May 3, 2025
Enumerating Password Policies
Understanding password policies is key to assessing an organization's security posture. In this tutorial, we explore how to enumerate these policies using powerful tools like CrackMapExec, NetExec, rpcclient, and ldapsearch. Whether you're a penetration tester or security enthusiast, this tutorial equips you with practical techniques to uncover critical password settings.
crackmapexec is no longer maintained but we can use it to enumerate password policies. It takes the protocol (SMB), the IP address (10.10.11.35), the username (michael.wrightson) and the password (Cicada$M6Corpb*@Lp#nZp!8) as arguments. And we also have to pass the --pass-pol option to enumerate the password policy.
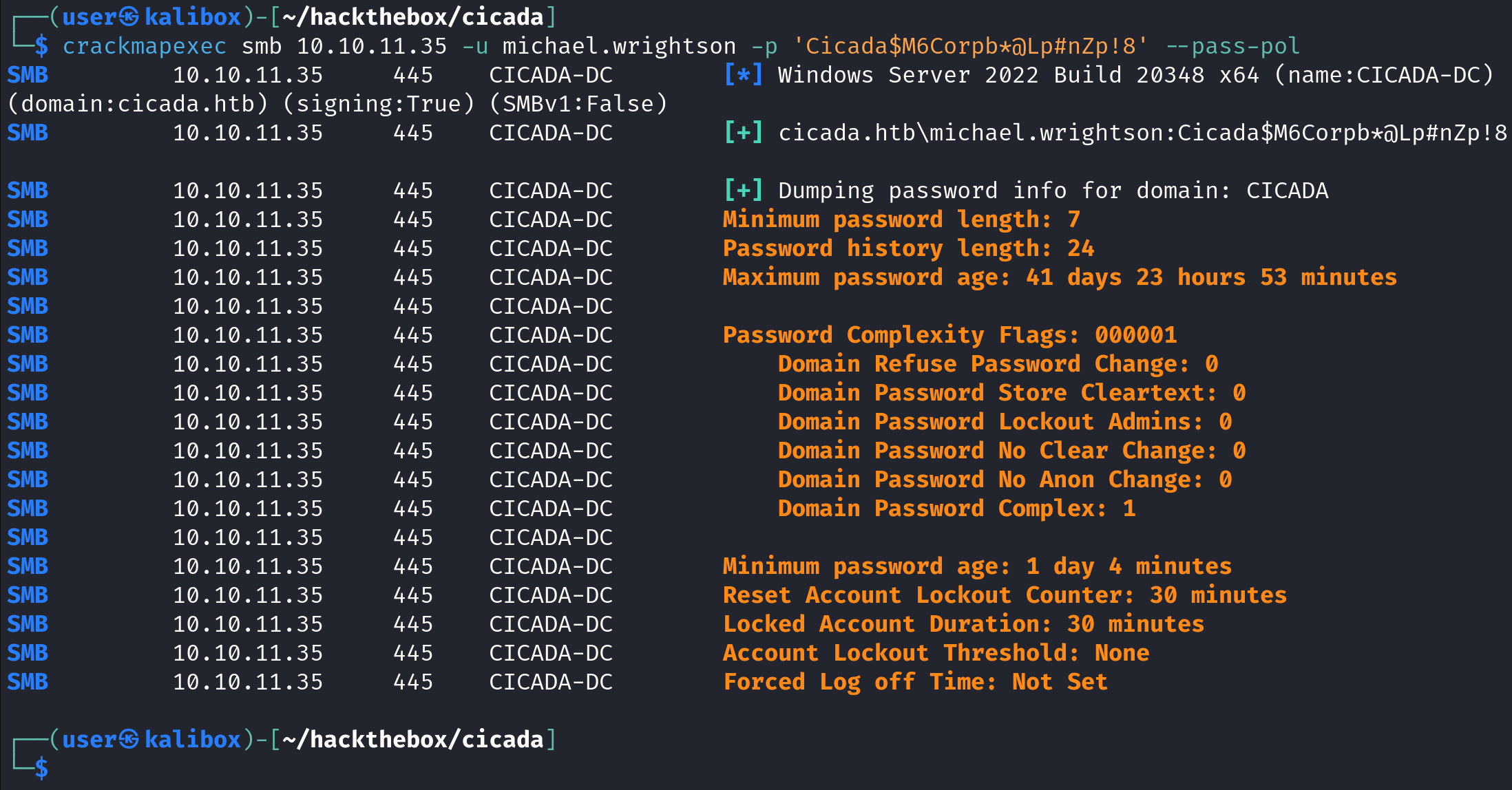
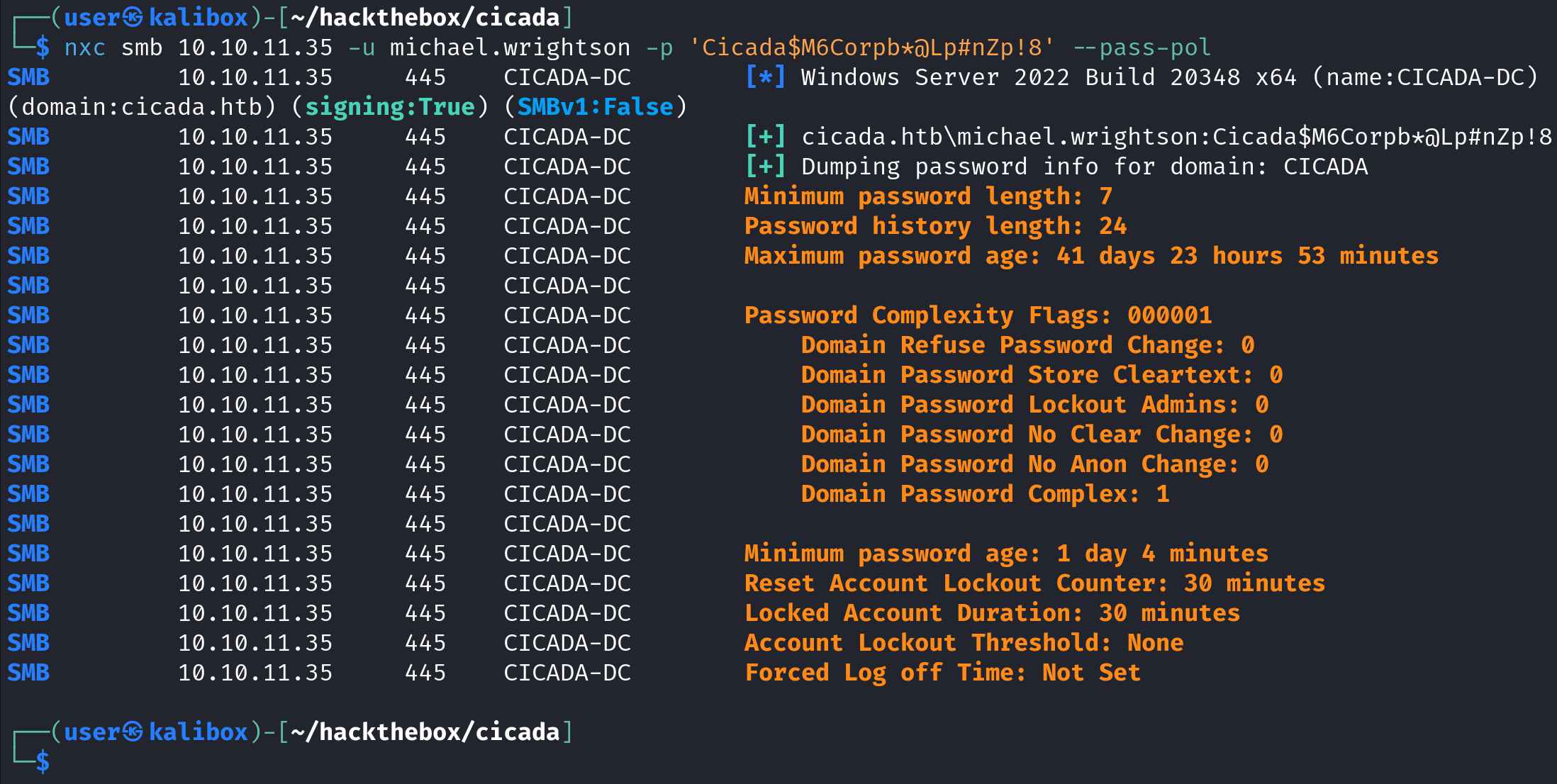
netexec is another useful tool that we can use to enumerate password policies. It takes the protocol (SMB), the IP address (10.10.11.35), the username (michael.wrightson) and the password (Cicada$M6Corpb*@Lp#nZp!8) as arguments. And we also have to pass the --pass-pol option to enumerate the password policy. It is the same as crackmapexec.
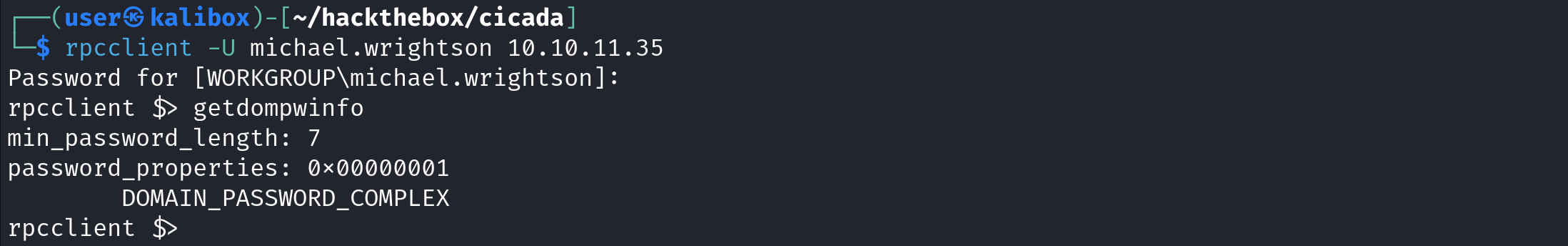
rpcclient is also capable of providing password policy information. However, it doesn't provide as much information as netexec.
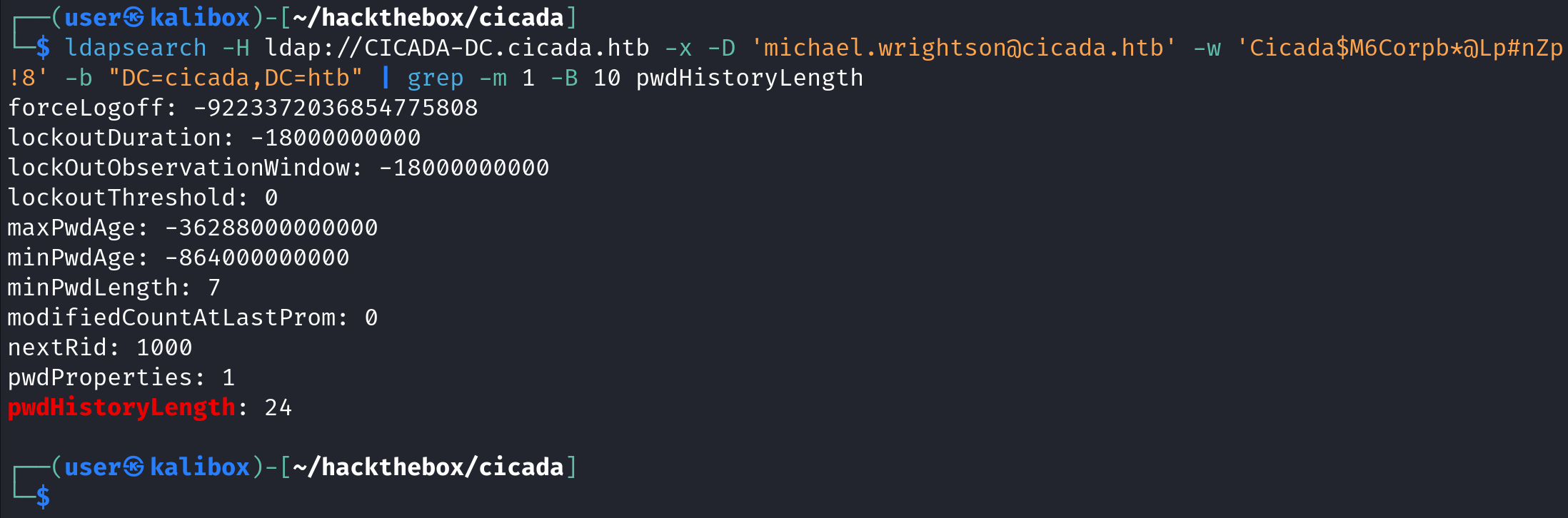
ldapsearch is another tool that can provide password policy information. "-H" takes the URI, "x" stands for simple authentication (username/password), "-D" takes the username, "-w" takes the password, and "-b" takes the base DN.
However, the output to this command is thousands of lines. That's why it's important to use grep. "-m 1" tells it to stop after the first match and "-B 10" tells it to display 10 lines before the matching line.
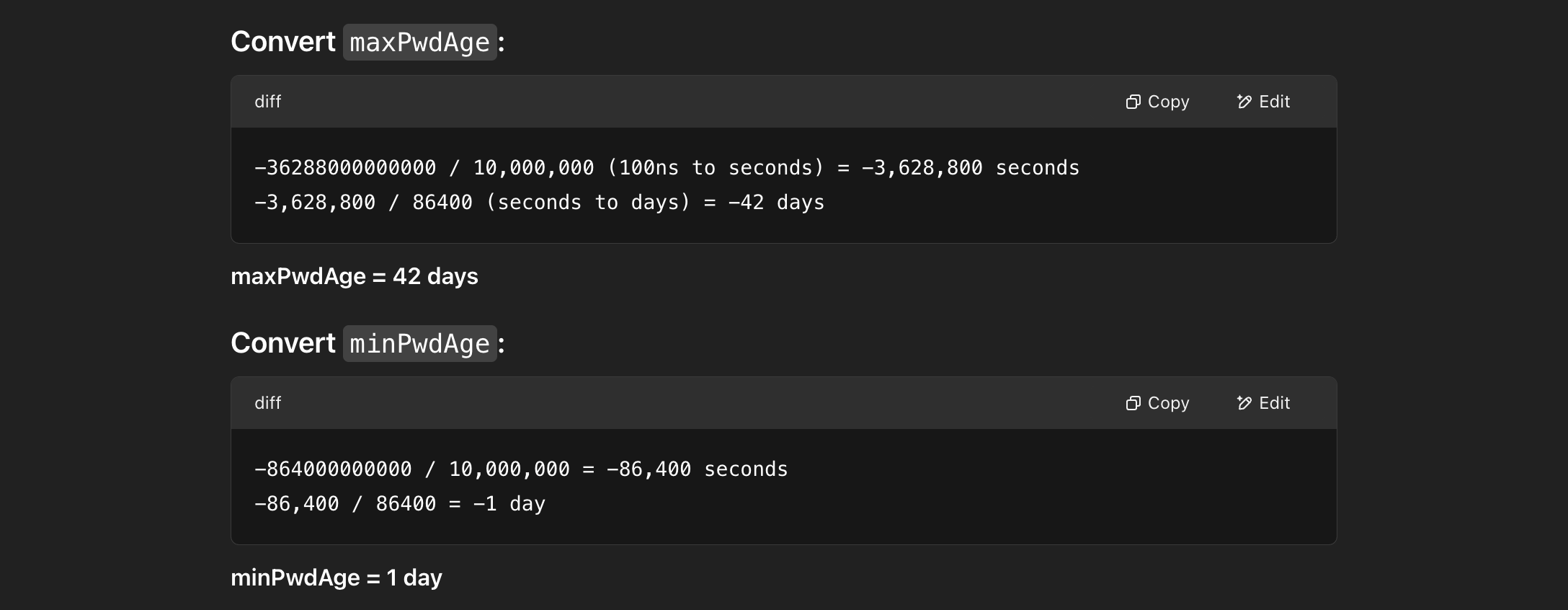
We can use the following formula shown below to convert the date and time. I have used ChatGPT, but we can do it using a calculator or a quick Bash or PowerShell script as well.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.