May 9, 2025
Username Enumeration using CrackMapExec, NetExec, enum4linux, rpcclient, kerbrute, and ldapsearch
In this tutorial, we'll see how to uncover valid usernames on a target system using tools like CrackMapExec, NetExec, enum4linux, rpcclient, Kerbrute, and ldapsearch. Enumerating usernames is a crucial step in the information-gathering phase of a penetration test.
crackmapexec can be used to enumerate usernames. After passing in the protocol (smb), the target IP address (10.10.11.202), the username (Ryan.Cooper) and the password (NuclearMosquito3), we have to use the --users option. It was able to find nine usernames.
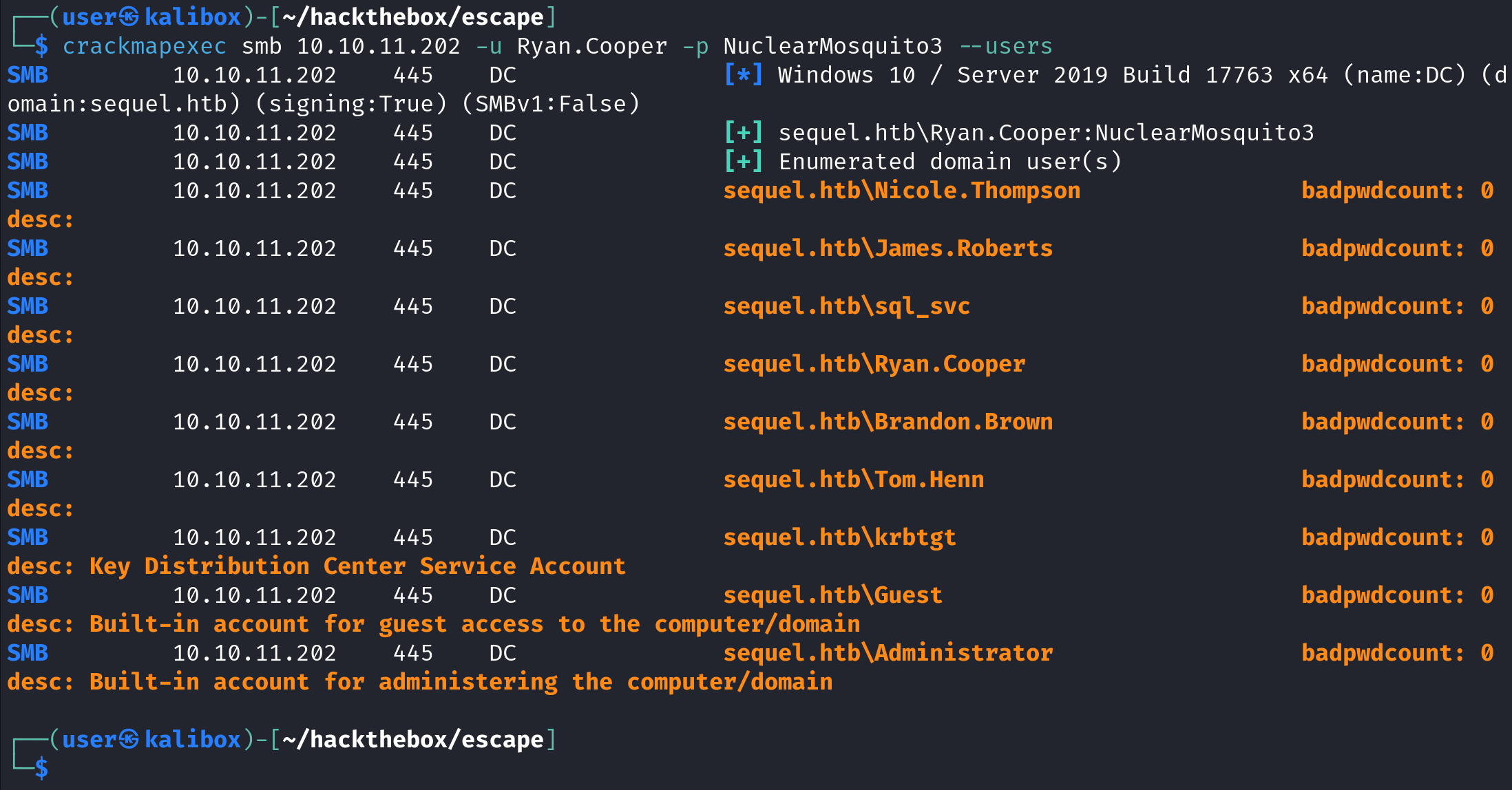
The same goes for netexec.
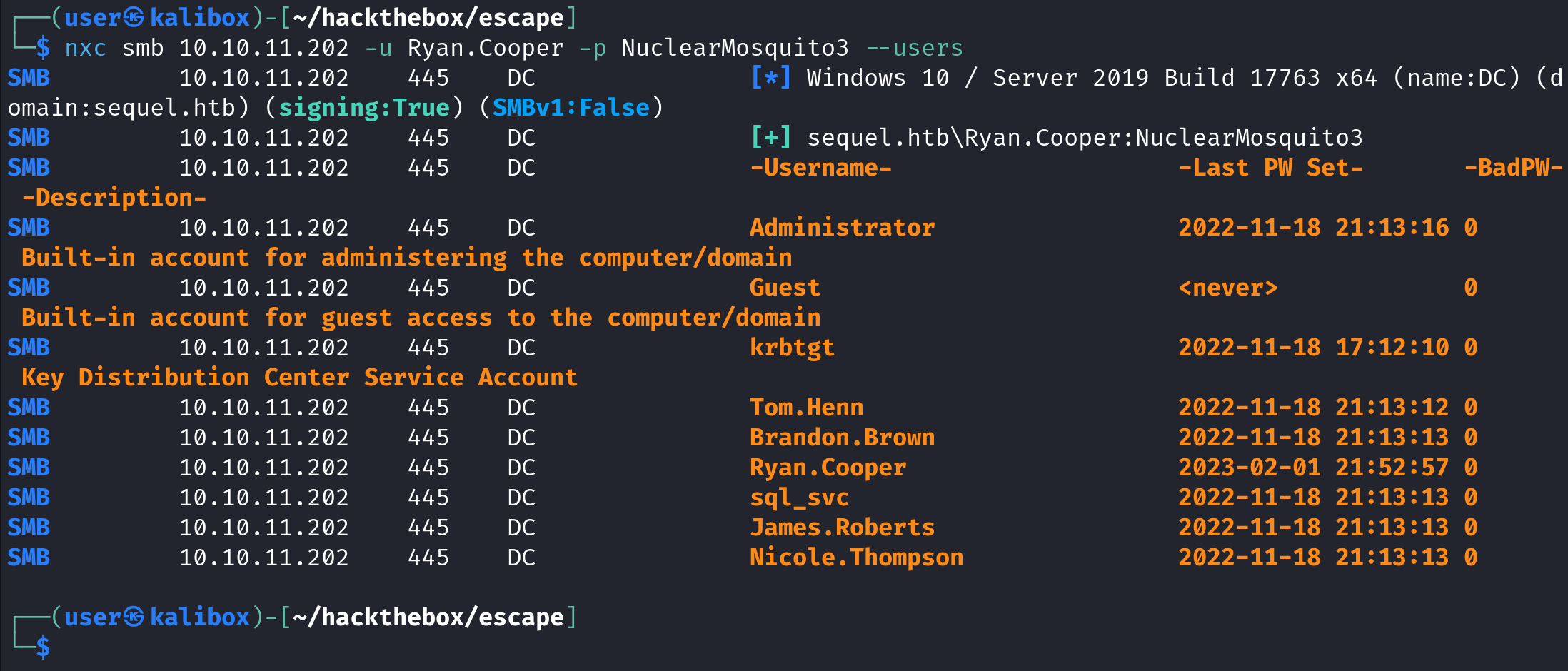
enum4linux-ng.py can display the usernames as well. It takes the target IP address (10.10.11.22), the username (dave) and the password (Password@123). However, enum4linux-ng produces a lot of output.
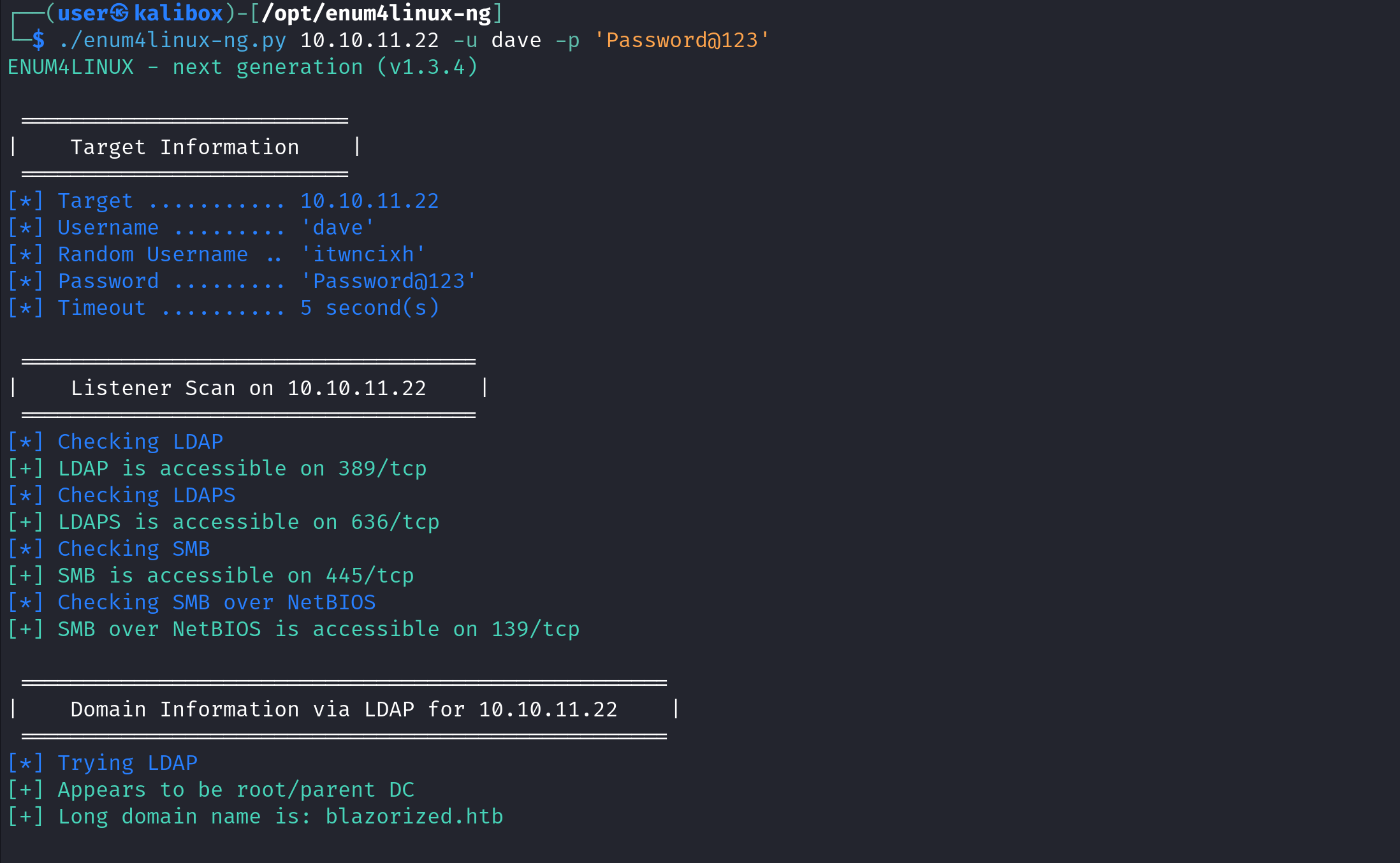
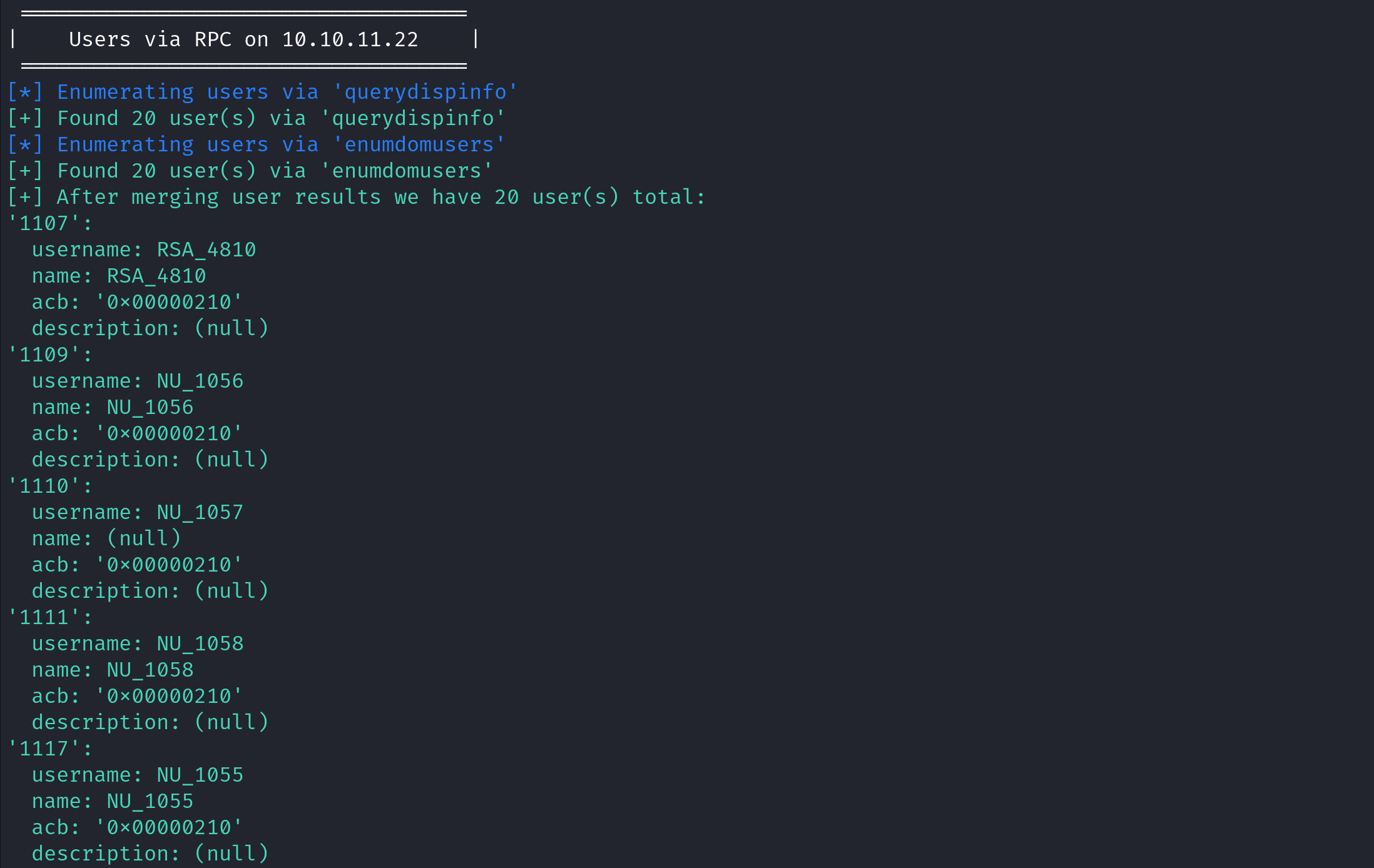
We can use grep to display the lines with the word "username:" in it.

And cut allows us to filter out the text "username:" and only display the actual usernames.
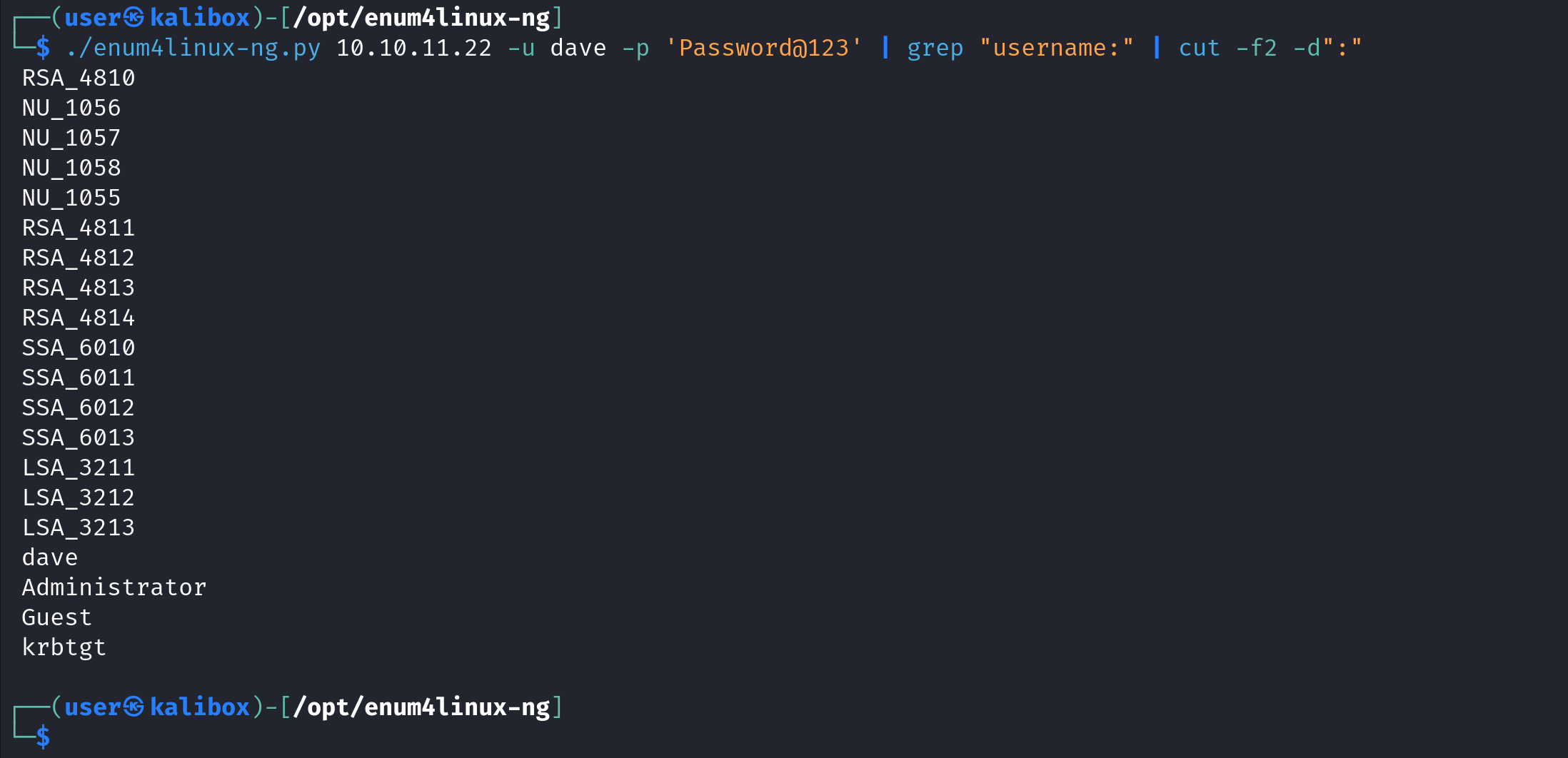
kerbrute has four modes in which it can operate. One of them is "userenum" which can enumerate usernames on the target. It takes a list of usernames (usernames.txt), the domain name (-d) and the domain controller's name or IP address (--dc) as options.
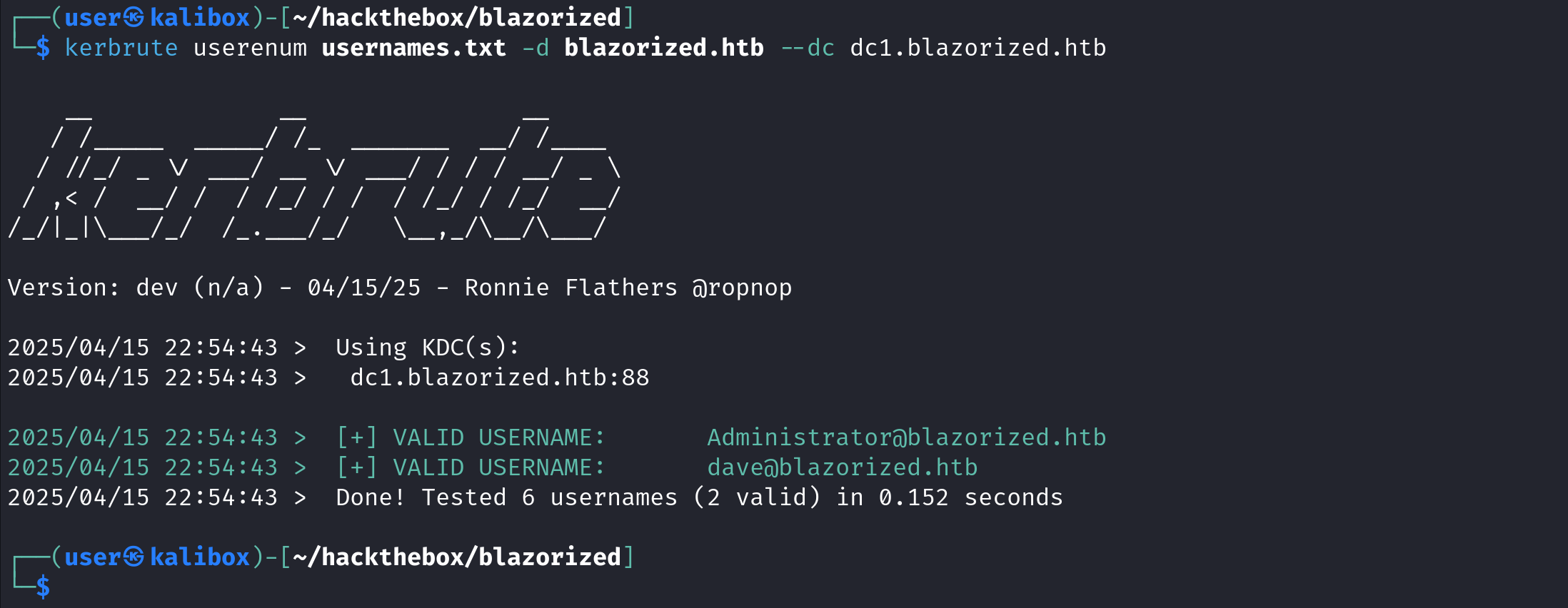
In order to enumerate users with rpcclient, we first have to connect to it. The querydominfo command displays the number of users, groups and aliases on the target.
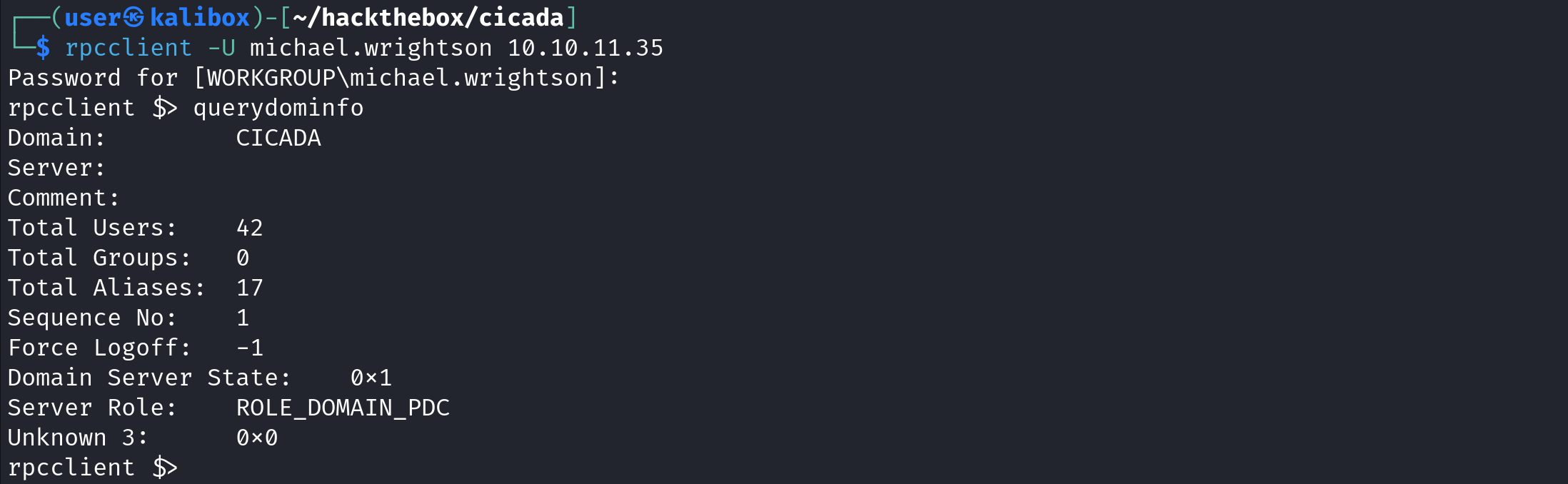
enumdomusers displays the usernames it was able to find.

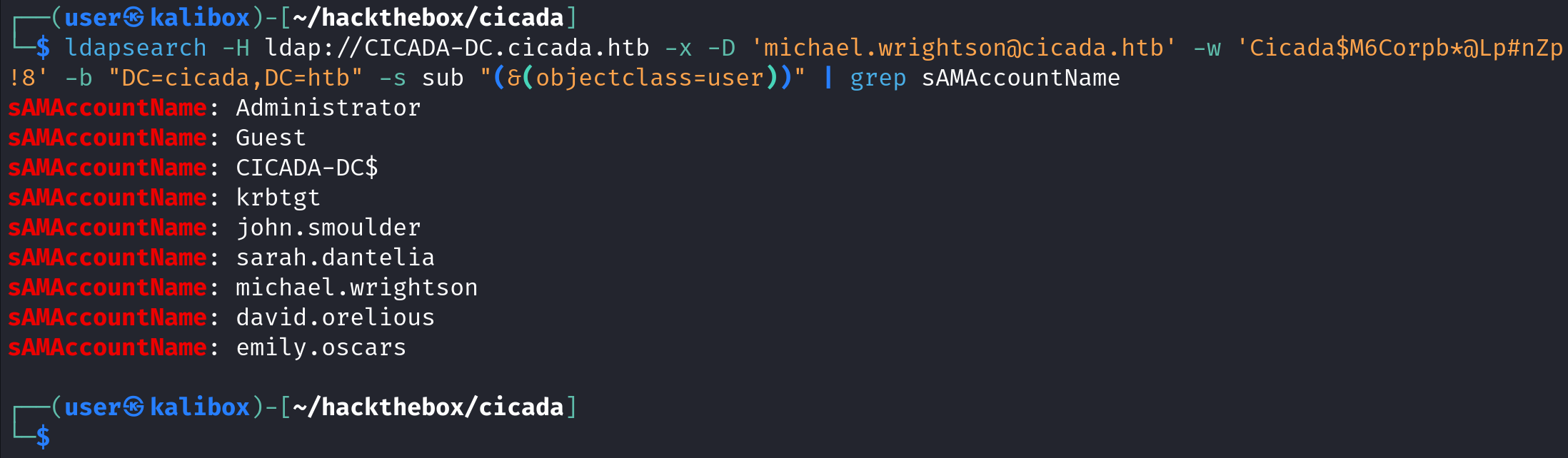
Let's take a look at ldapsearch to enumerate usernames. "-H" takes the target, "-x" is for simple authentication, "-D" takes the username, "-w" takes the password, "-b" takes the base DN. However, it outputs a lot of data. We can filter it by only printing the information related to the user object by using the "-s" option. We can filter further by only display the lines that has "sAMAccountName" in it.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.