May 28, 2025
rpcclient Enumeration
Domain enumeration is a critical step in network reconnaissance, especially in Windows environments. One powerful yet often overlooked tool for this task is rpcclient, a command-line utility that interacts with the Windows RPC service. In this post, we’ll explore how to use rpcclient to gather valuable domain information for security assessments.
First, let's connect to the target as the "dave" user.

querydominfo displays the domain name, numbers of users, groups and aliases on the target, and the server role.

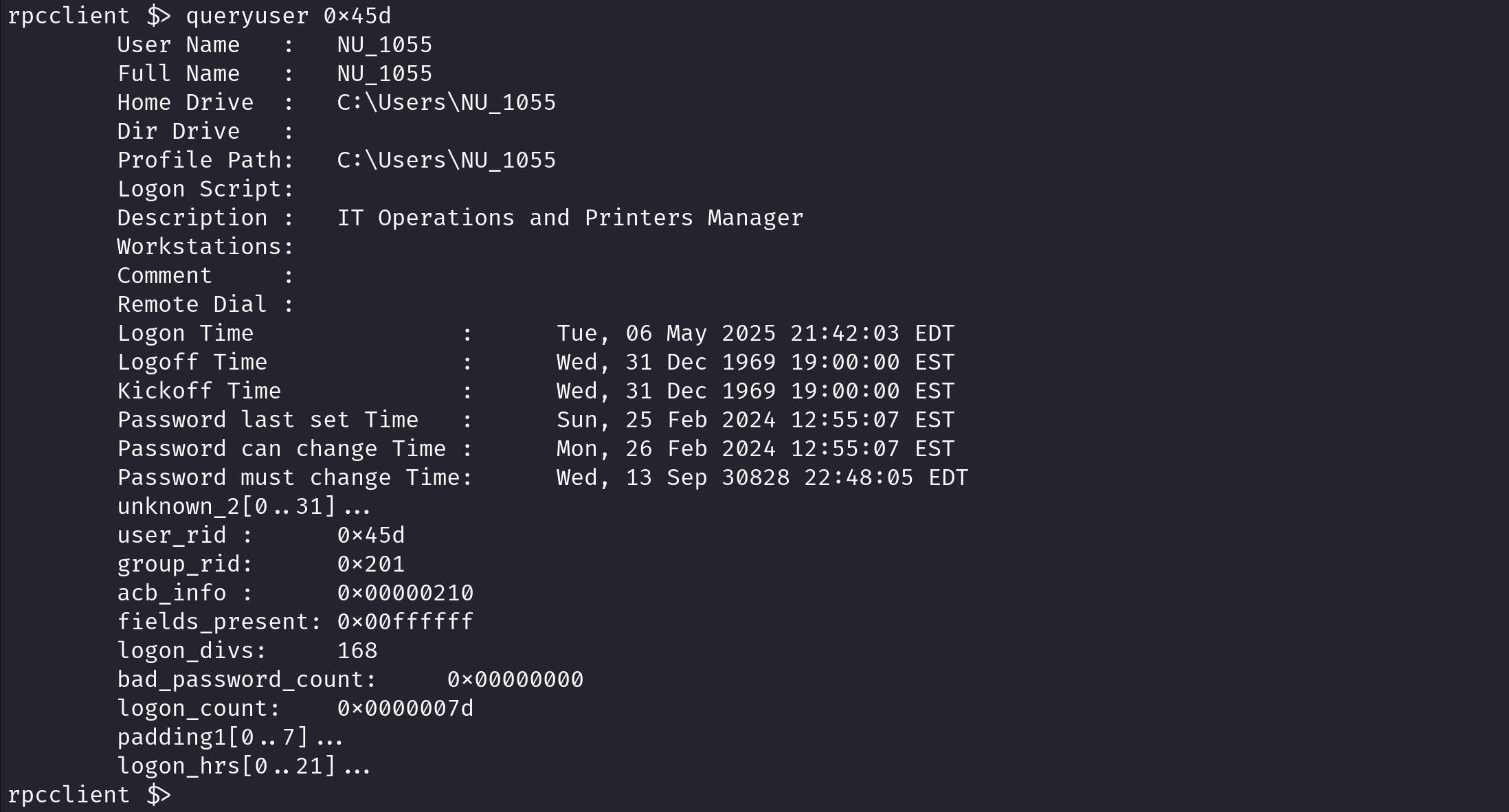
enumdomusers displays a list of users on the target and their RIDs.
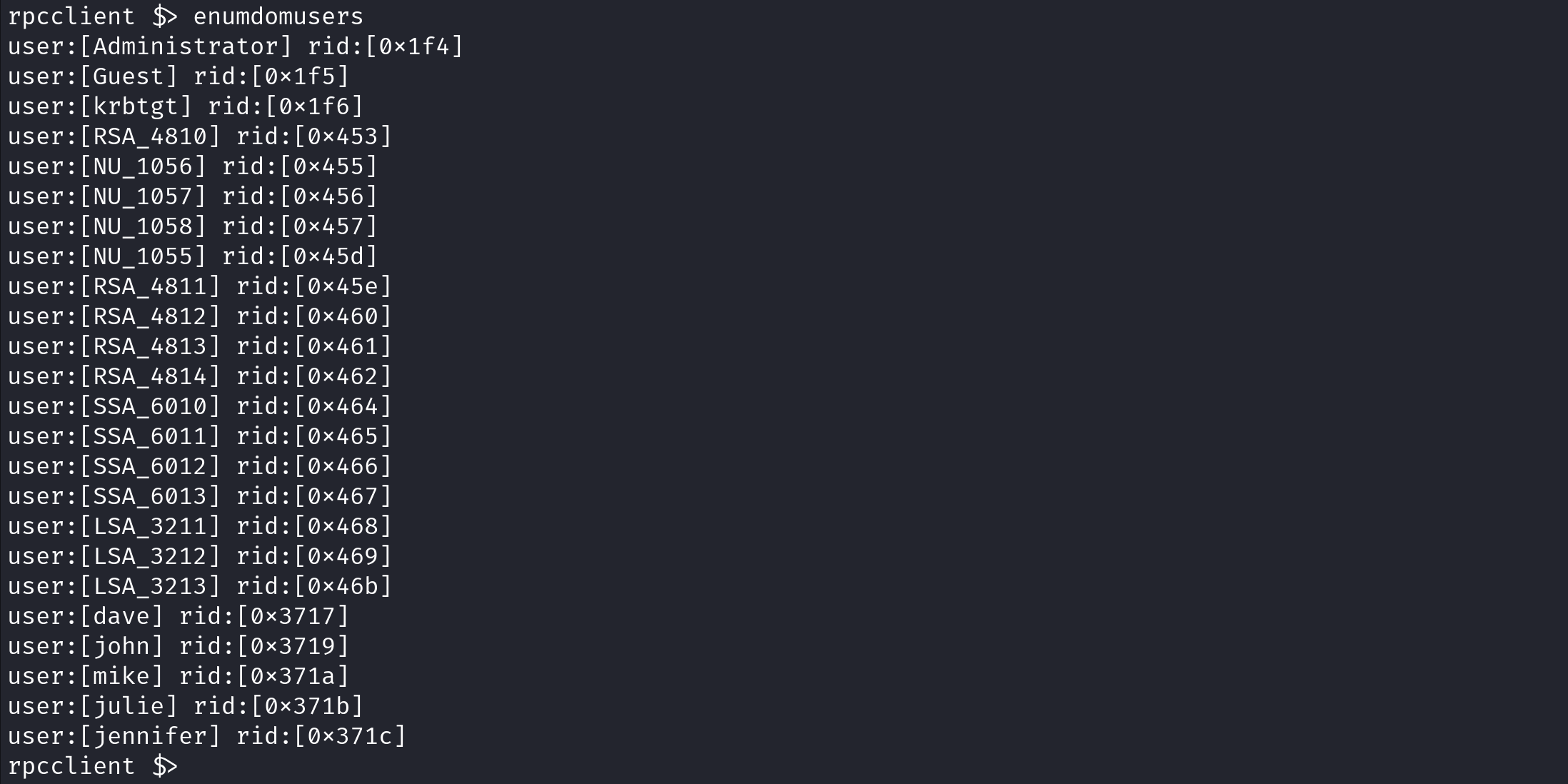
queryuser [RID] displays the home drive, description, logon time information, password information, user RID and the group RID.
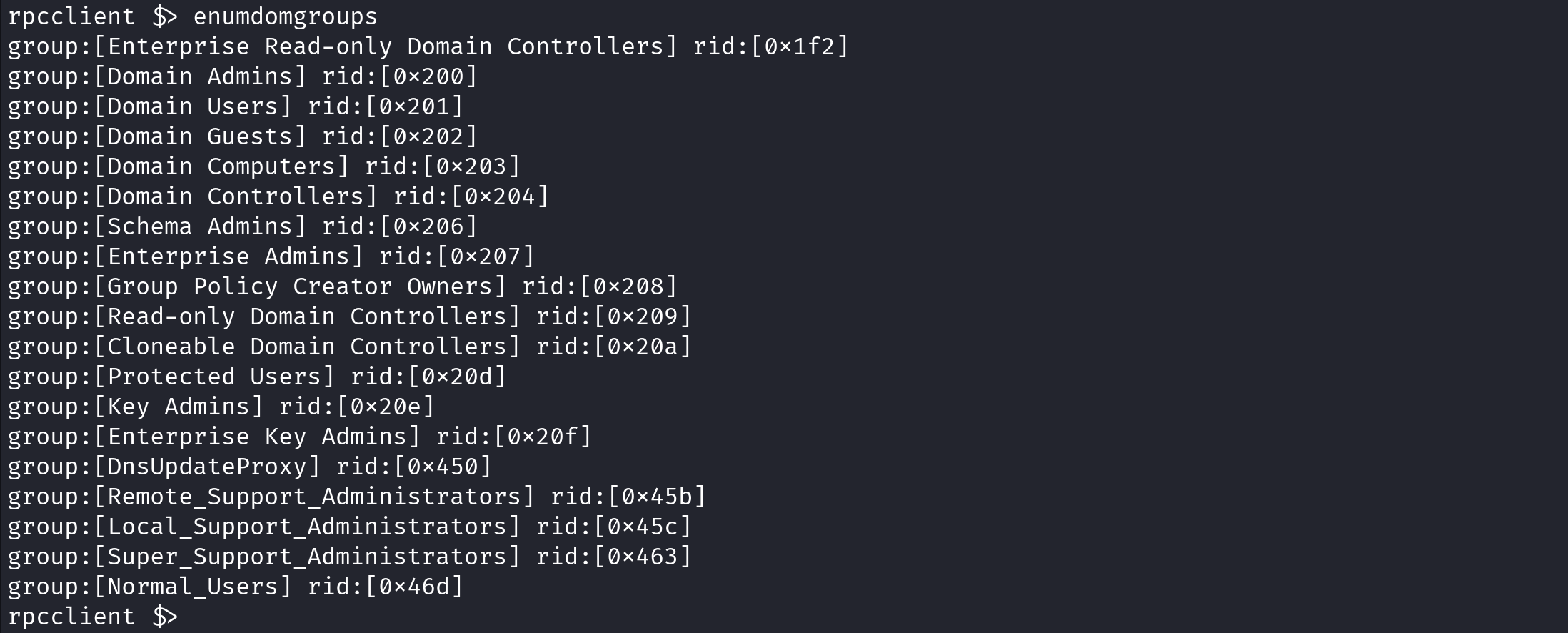
enumdomgroups displays a list of groups and their RIDs.
querygroup [RID] displays information about a particular group (in this case the Domain Users).

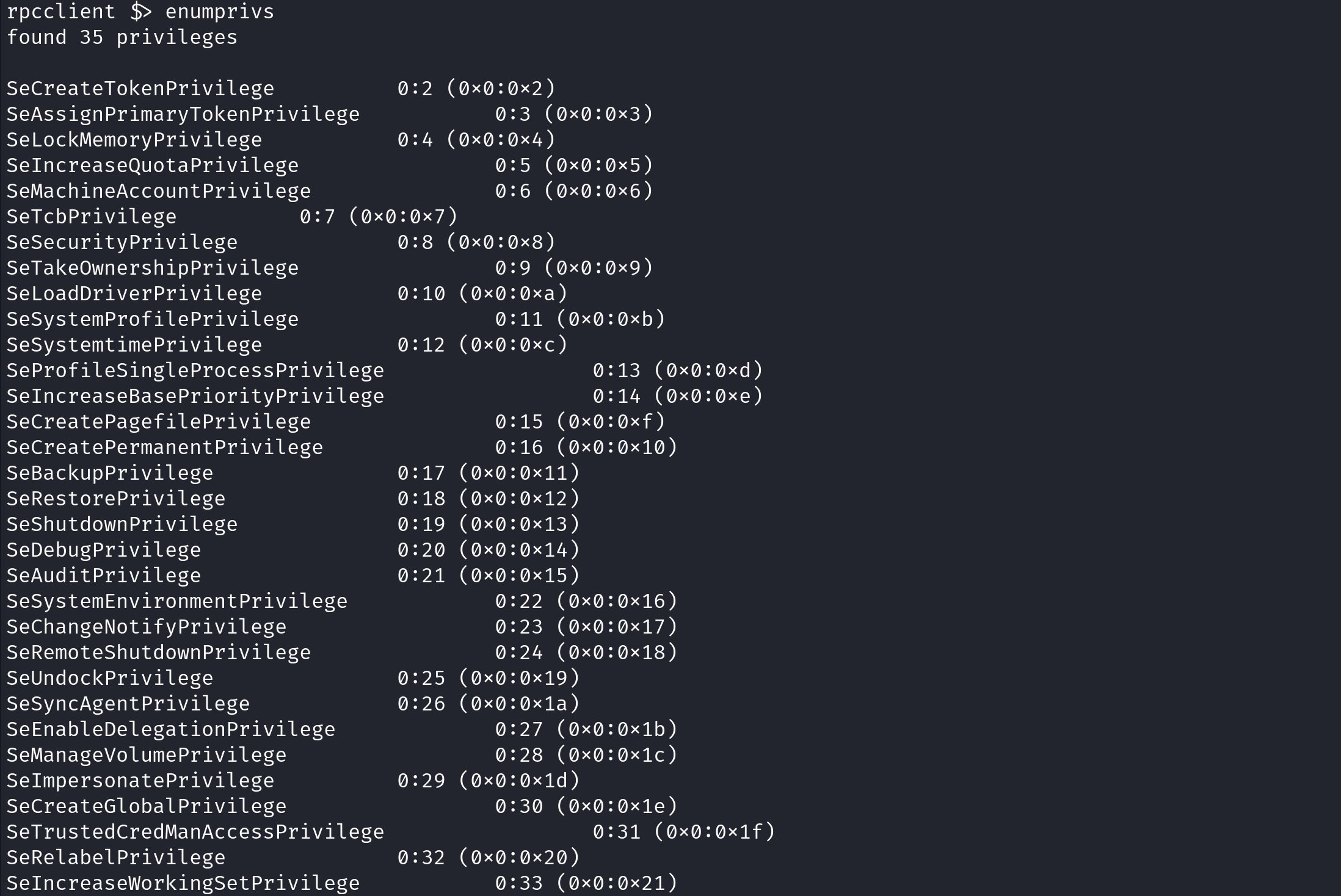
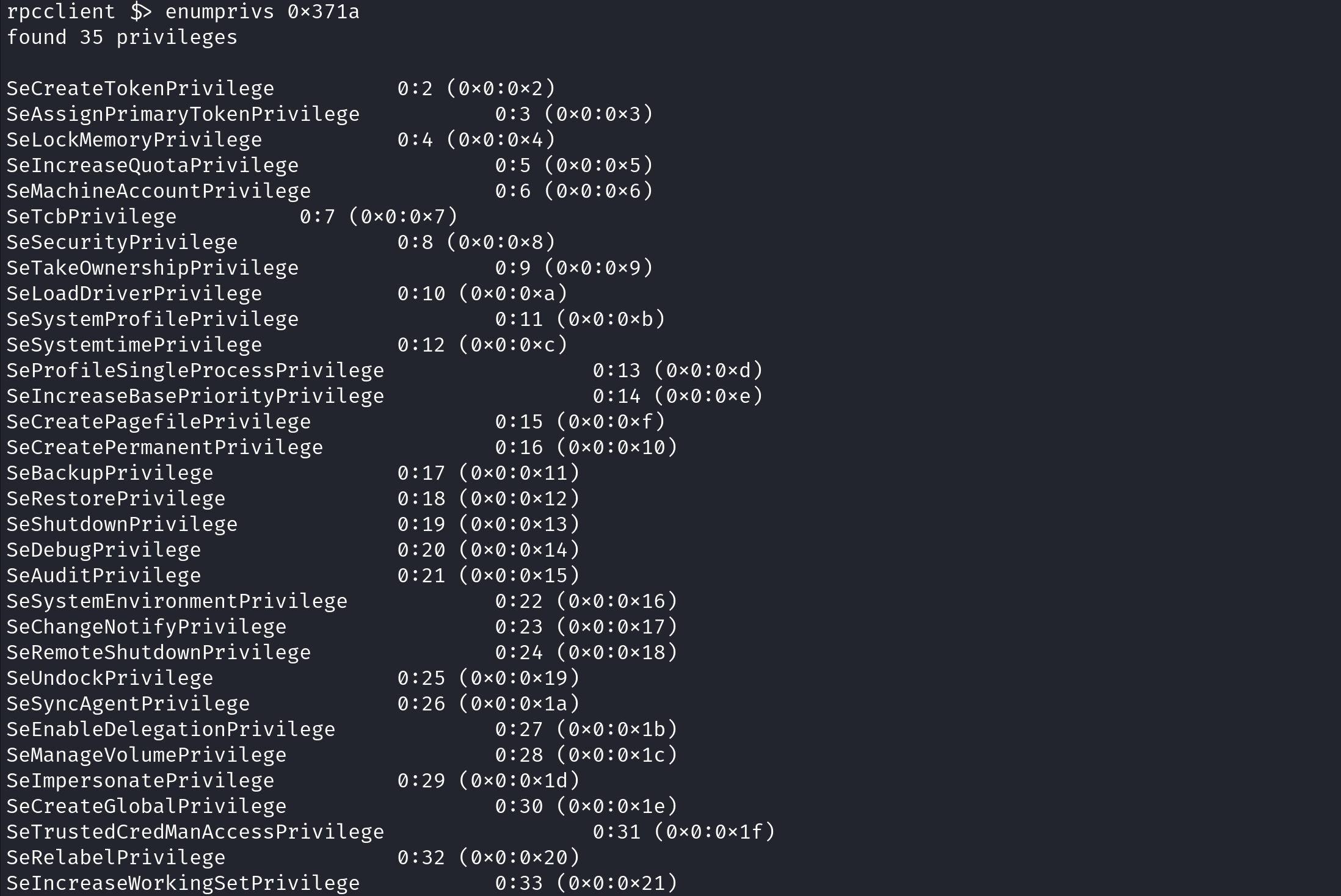
enumprivs displays a list of the current user's privileges.

enumprivs [RID] displays the privileges for a particular user. In this case, it is for the user "mike".
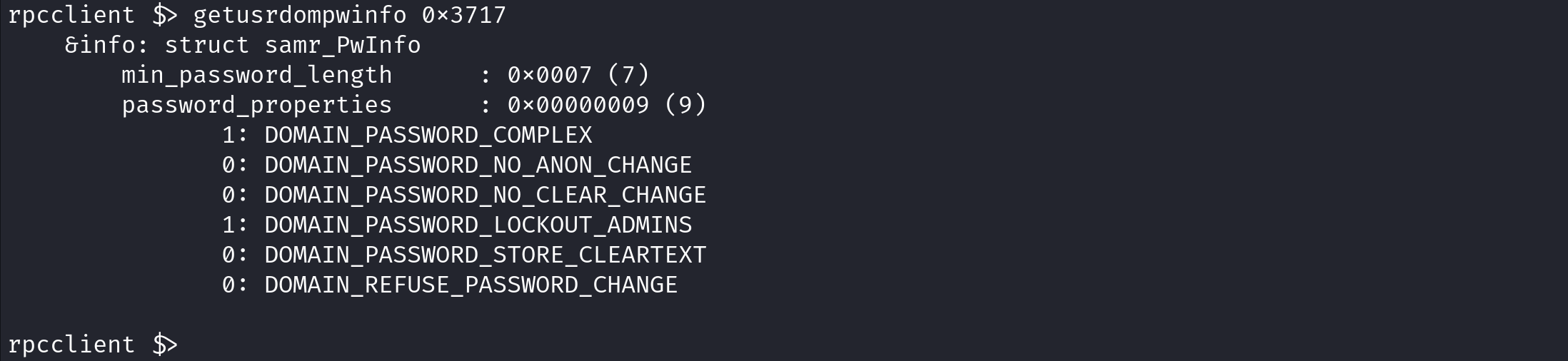
getdompwinfo queries and displays the domain password policy settings.

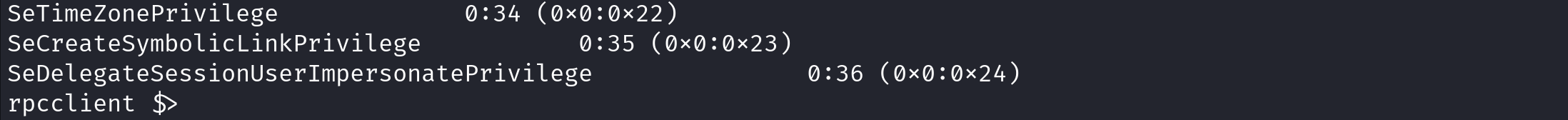
getusrdompwinfo provides a mix of information about the current user's password settings and domain-level policies relevant to that user.
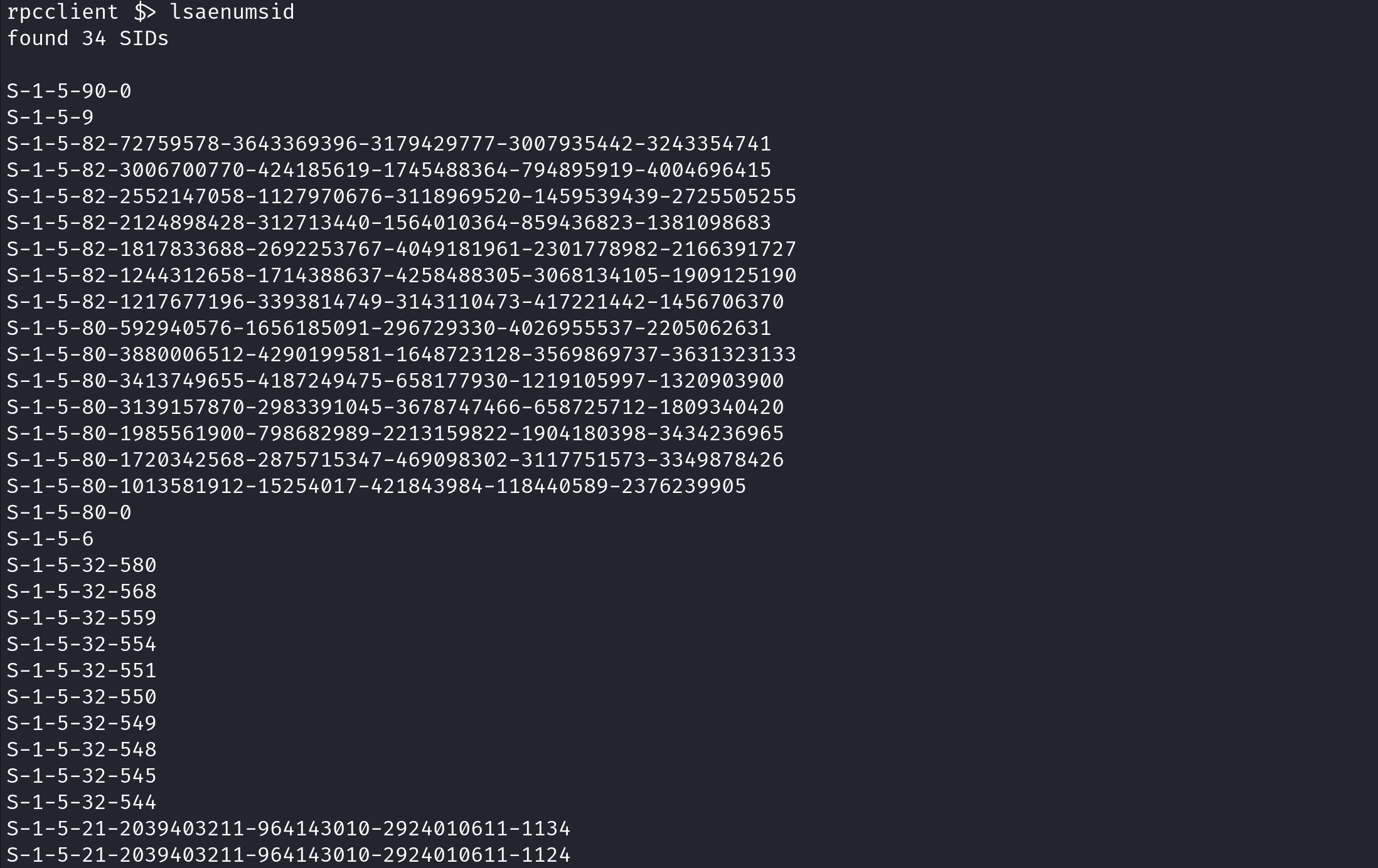
lsaenumsid enumerates the Security Identifiers (SIDs) stored in the Local Security Authority (LSA) of the target.

We can resolve these SIDs (Security Identifiers) using lookupsids.
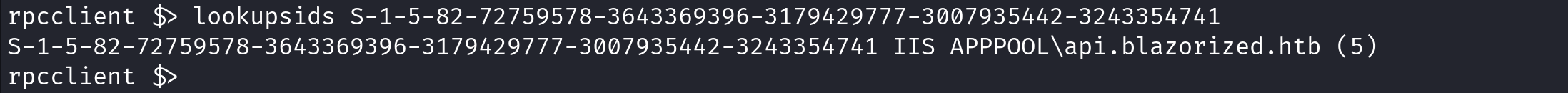
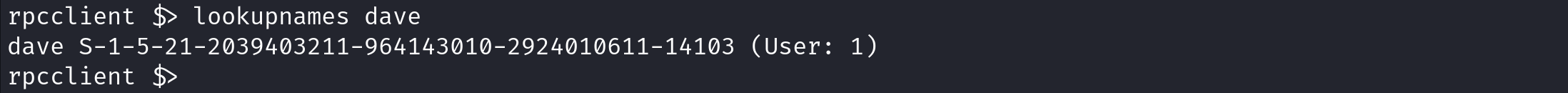
The lookupnames command is the reverse of lookupsids: it resolves account names to SIDs.
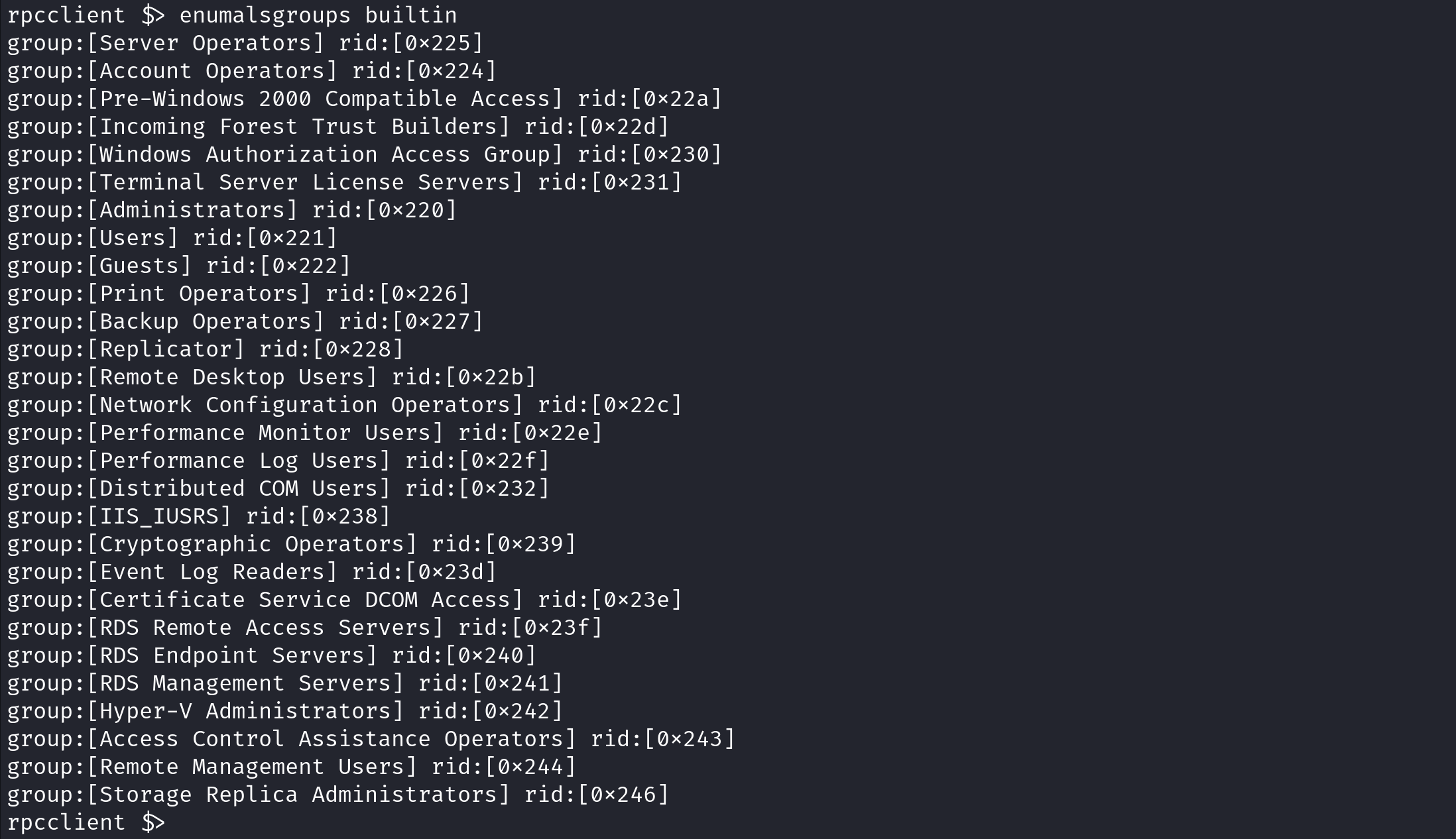
enumalsgroups is used to enumerate alias groups (also known as local groups) within a specified domain or policy handle.
enumdomains is used to enumerate domain names that are known to the Local Security Authority (LSA).

lookupdomain is used to resolve a domain name to its SID (Security Identifier).

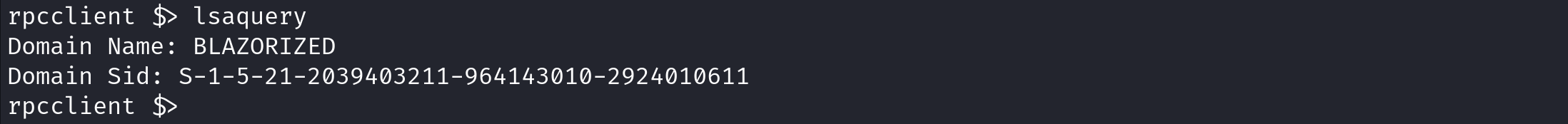
lsaquery displays the domain name and its SID.
samlookuprids is used to resolve Relative Identifiers (RIDs) within a domain to their corresponding user or group names and types.

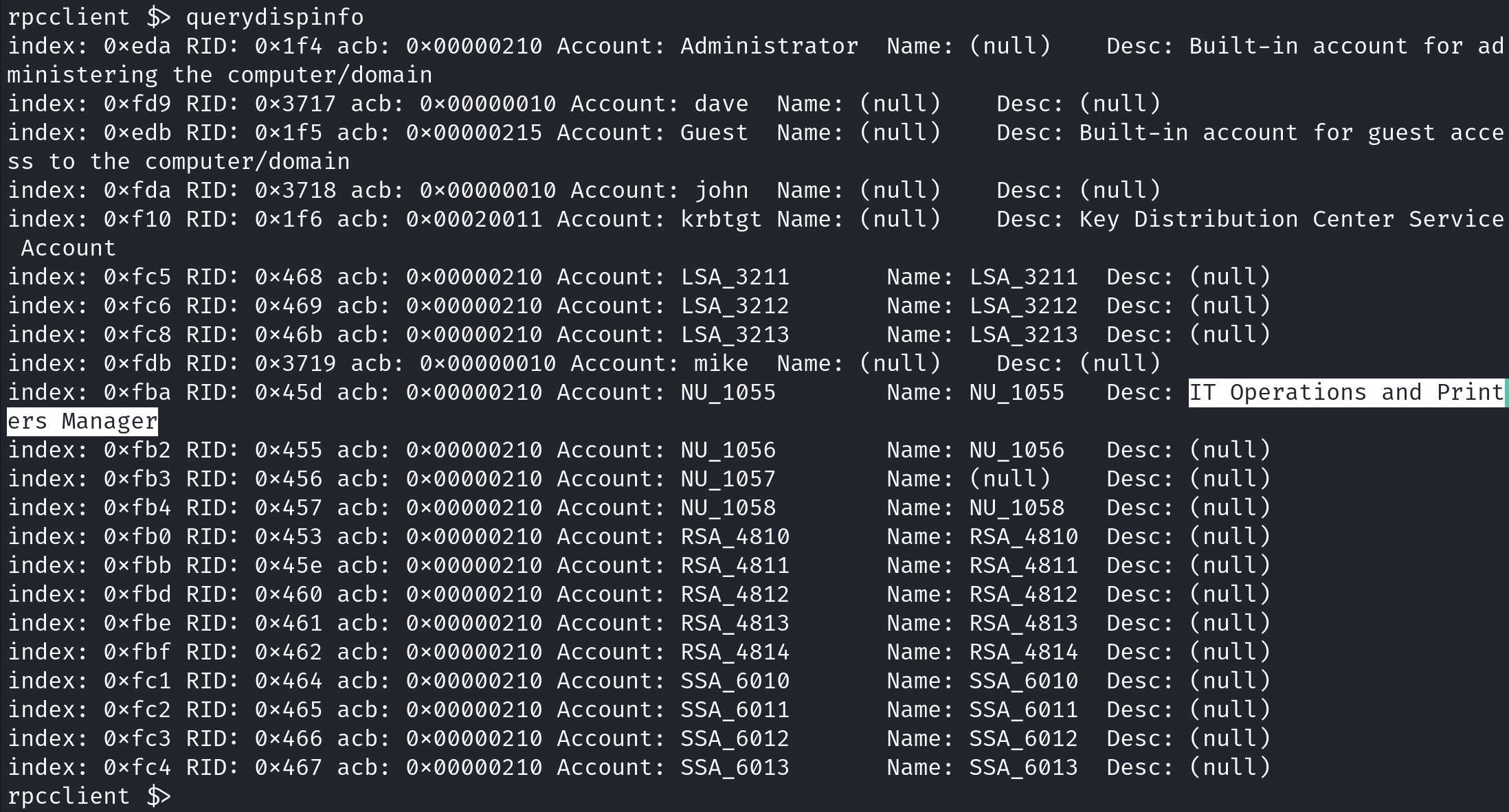
querydispinfo displays the RIDs, account names, full names, and the description for the users stored in the SAM (Security Account Manager) database.
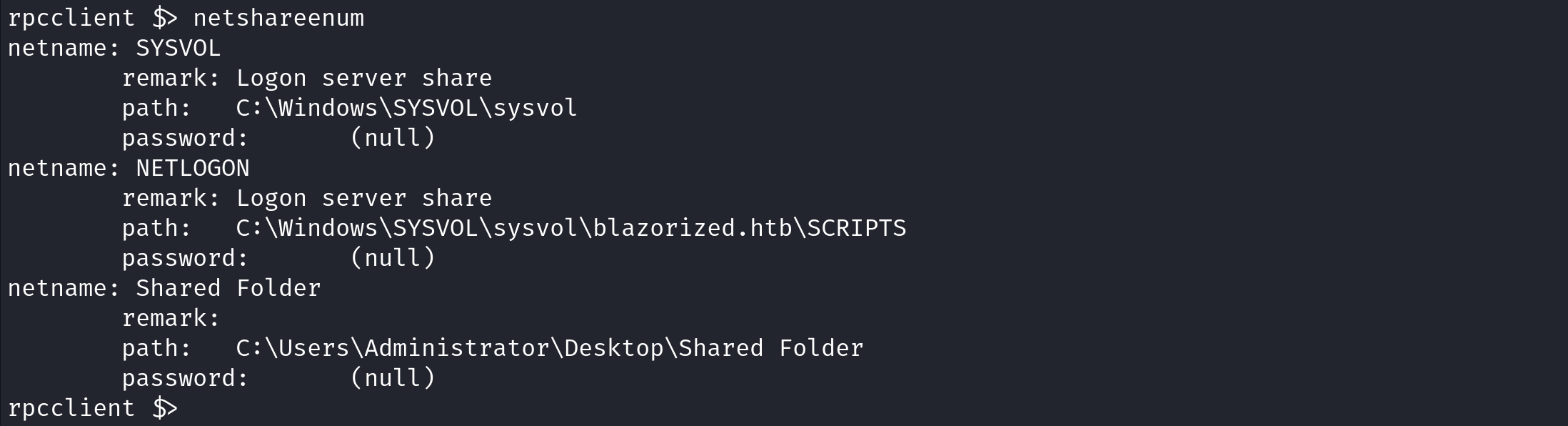
netshareenum lists the shared resources (network shares) available on the target.
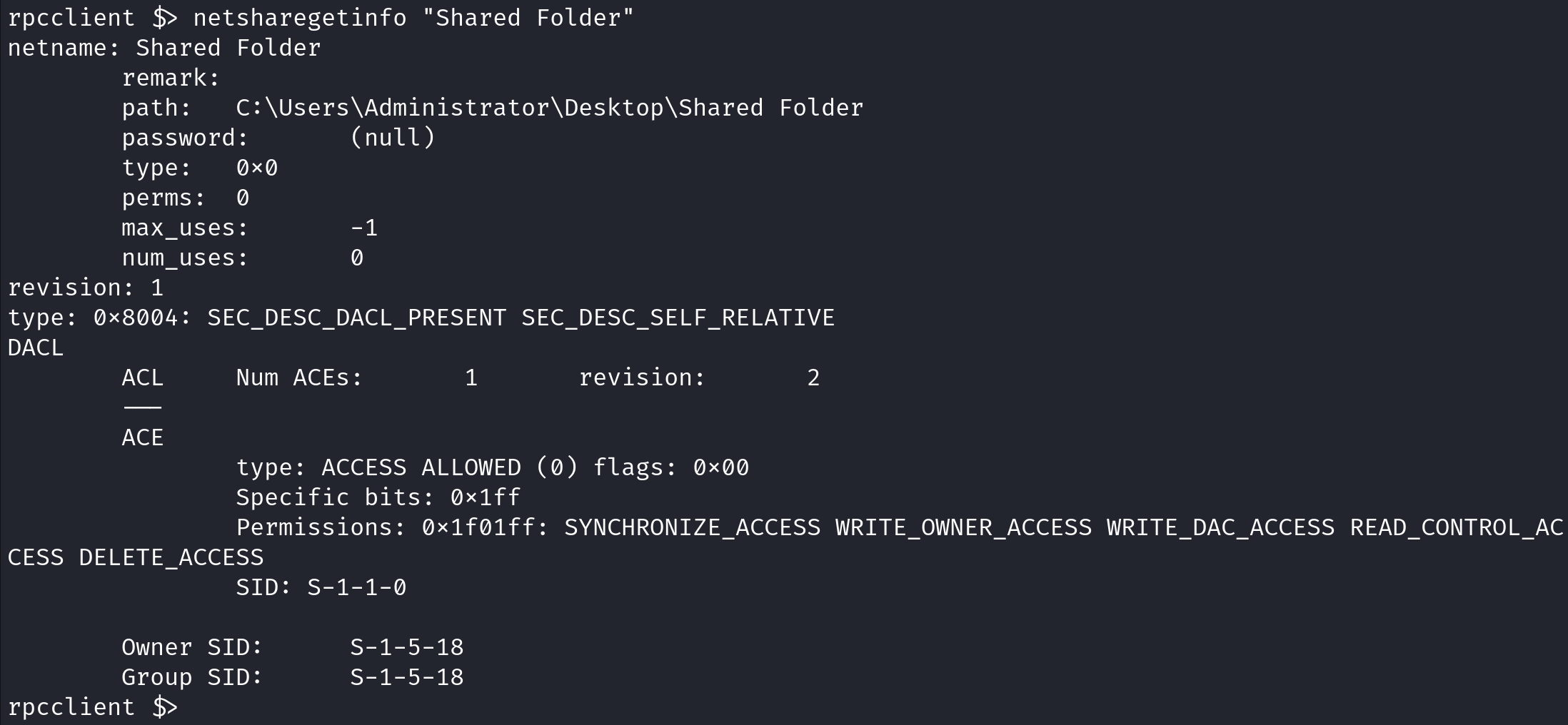
netsharegetinfo retrieves the share type, share description, permissions, and path to a particular share drive.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.