May 2, 2022
Server Side Template Injection (SSTI) - Example 2
In this tutorial, we will see how to perform a SSTI (Server-Side Template Injection) attack. The website allows us to register ourselves and provides us with a UUID that we can use with the password to login to the web application. Once logged in, we can buy furniture by adding it to the cart.
This is the main page of the website. It allows us to "Register" or "Login".
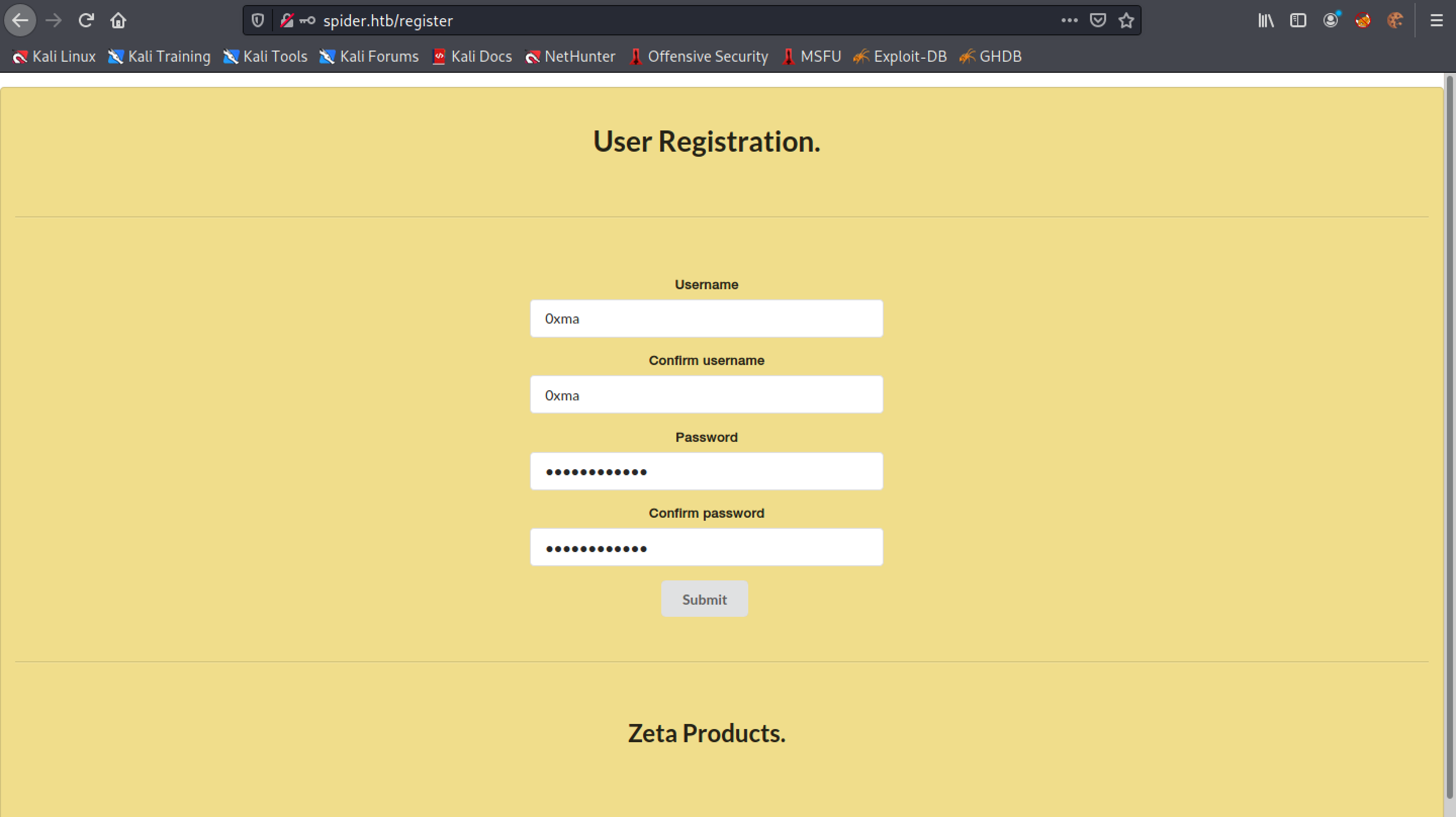
Let's register a user.
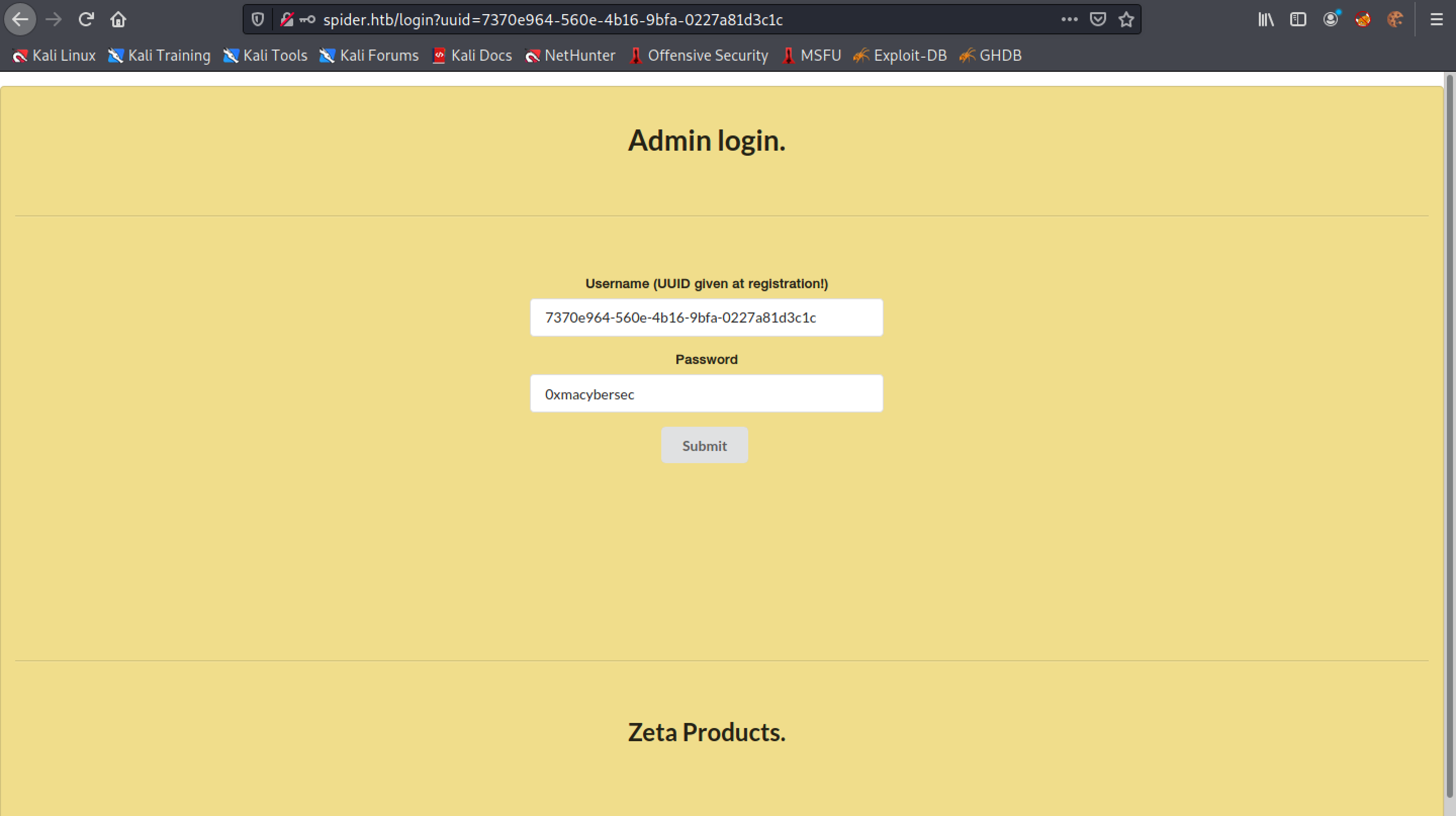
It returns a UUID which we can use to login to the website instead of using our username.
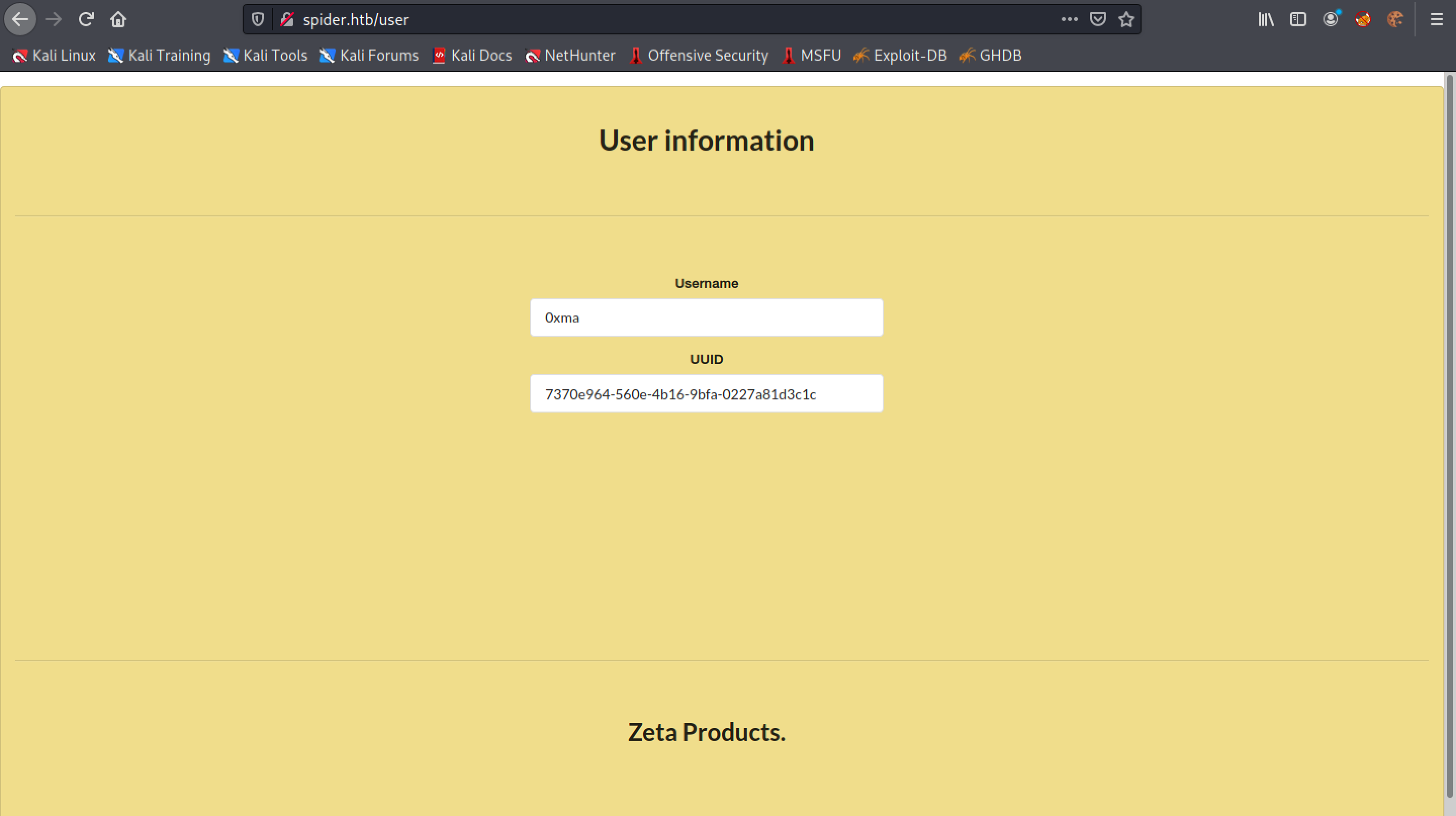
Once logged in we can purchase any furniture that we want by adding it to the cart. Let's click on "User Information" on the left panel to see what information it contains regarding the user.
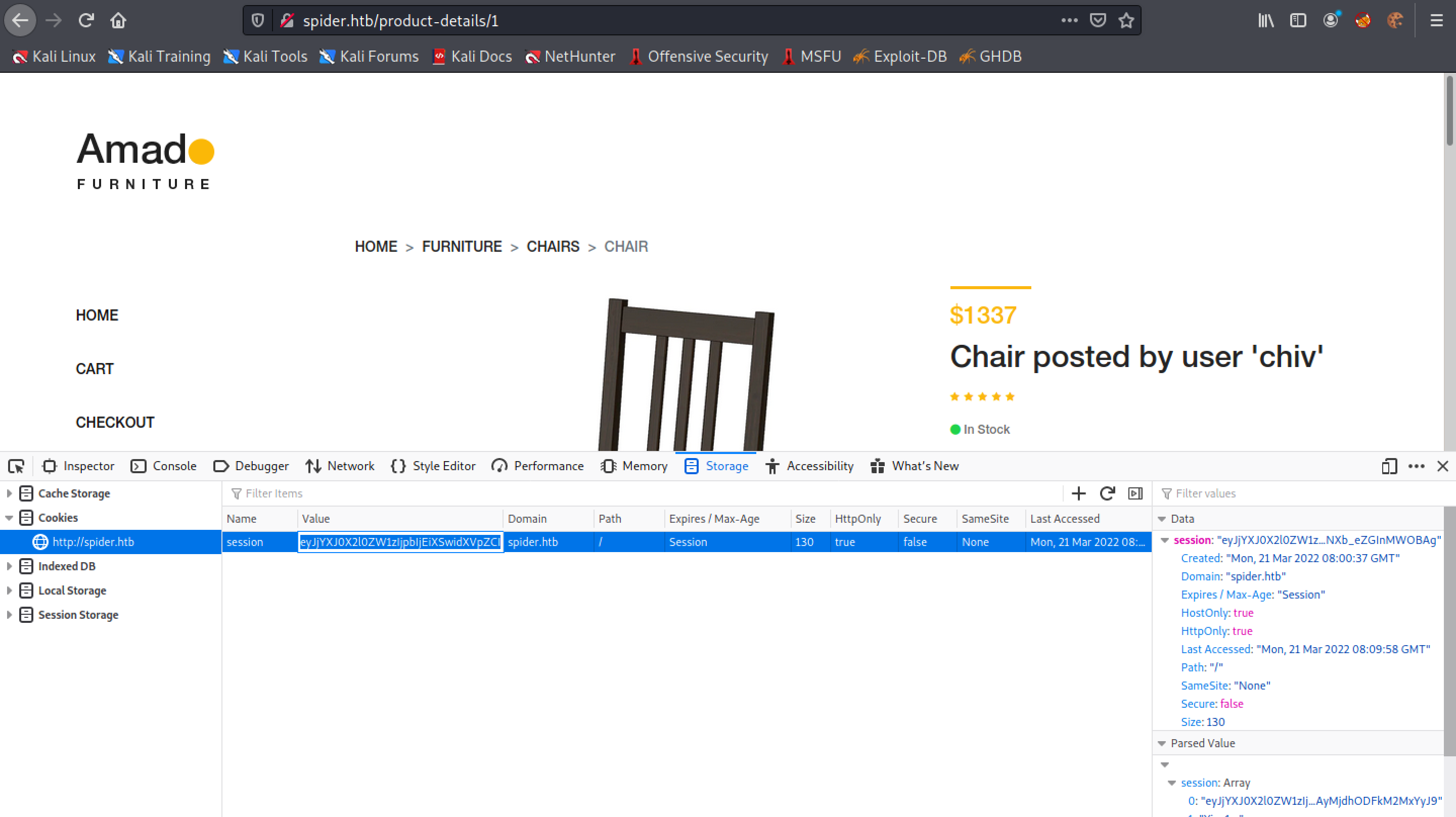
This page contains only the username and UUID.
Let's copy the cookie and decode it to see what it contains.
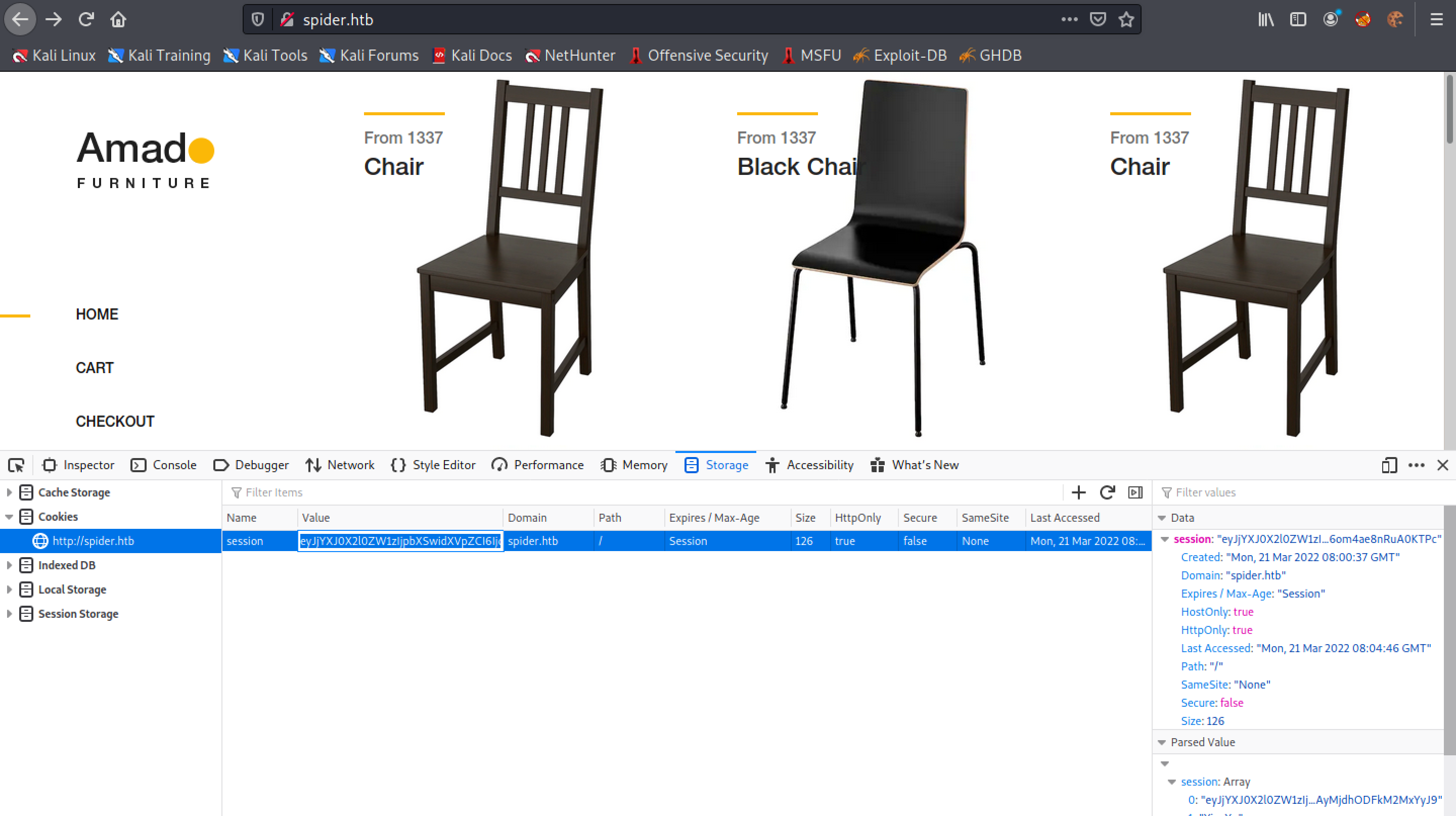
The last part of the cookie (after the dot (.)) can't be decoded. But the part that is decoded shows that it contains the UUID and the items that we have added to the cart.
Let's click on a chair and add it to the cart.
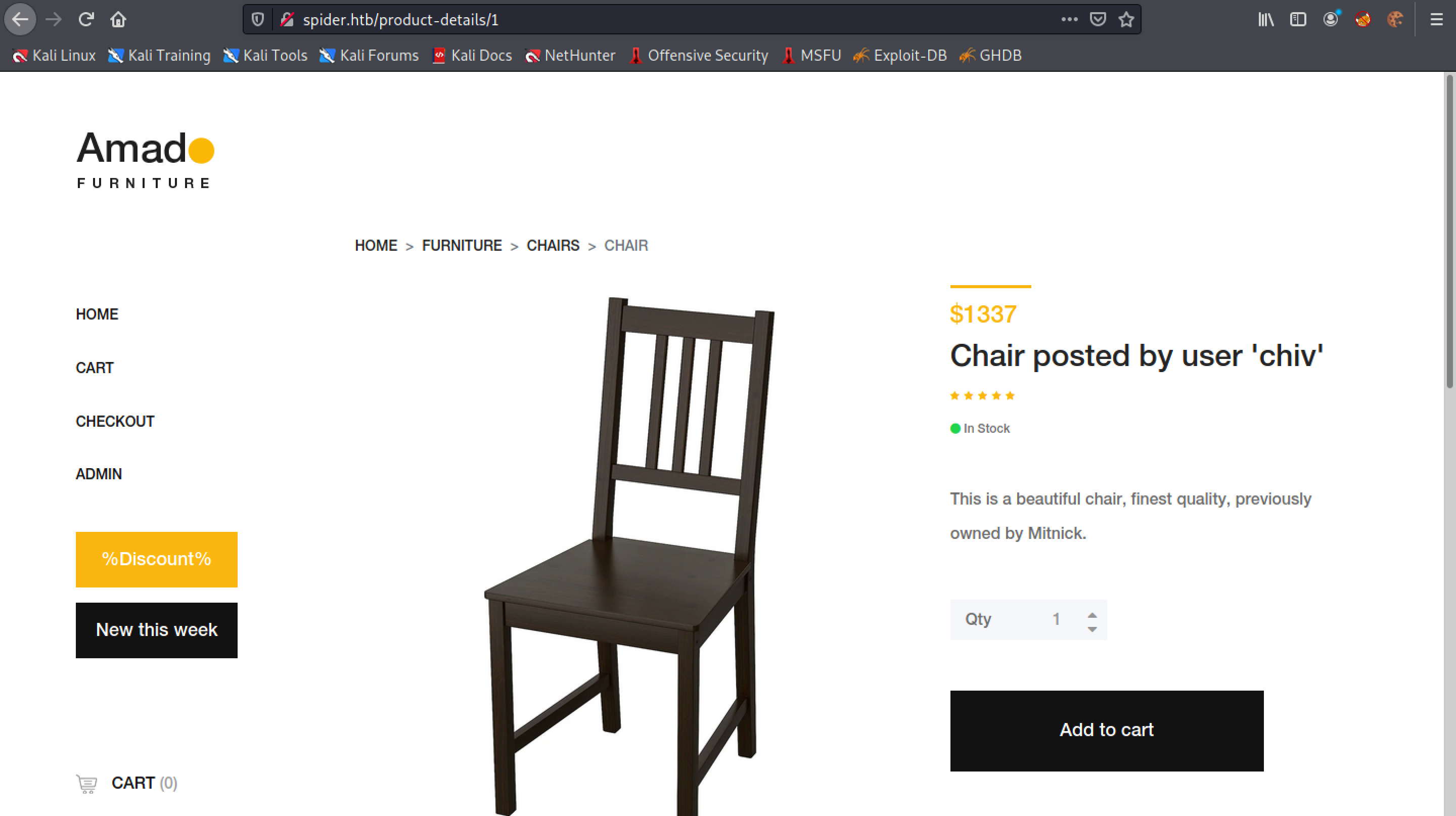
Copy the cookie.
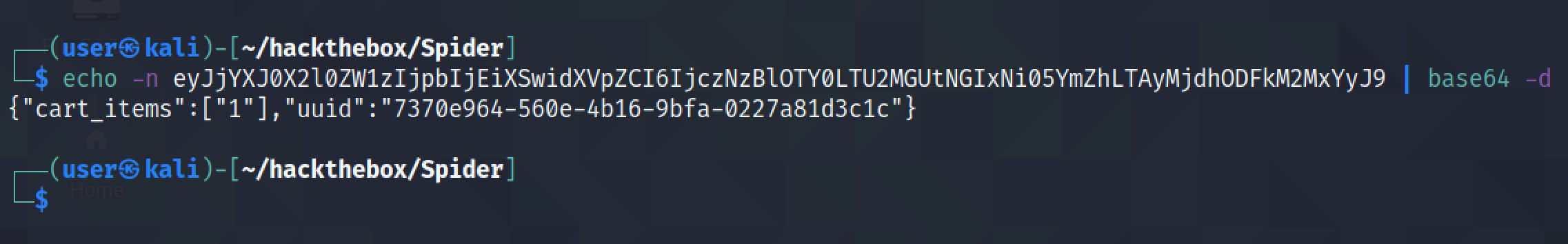
Base64 decoding the cookie shows that an item has been added to the cart. So this was a quick introduction to the functionality of the website.
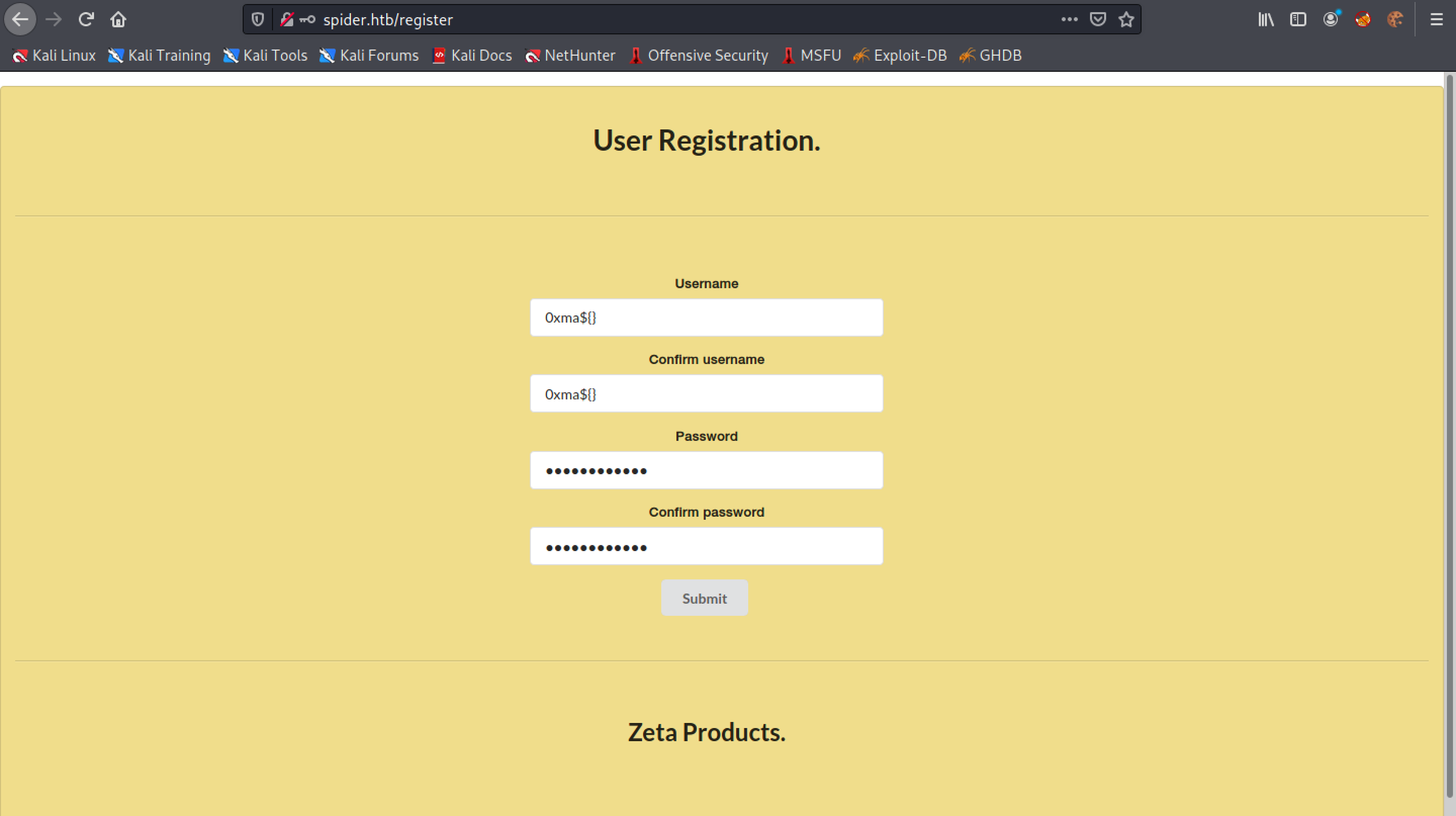
Let's attempt a SSTI attack while registering a user.
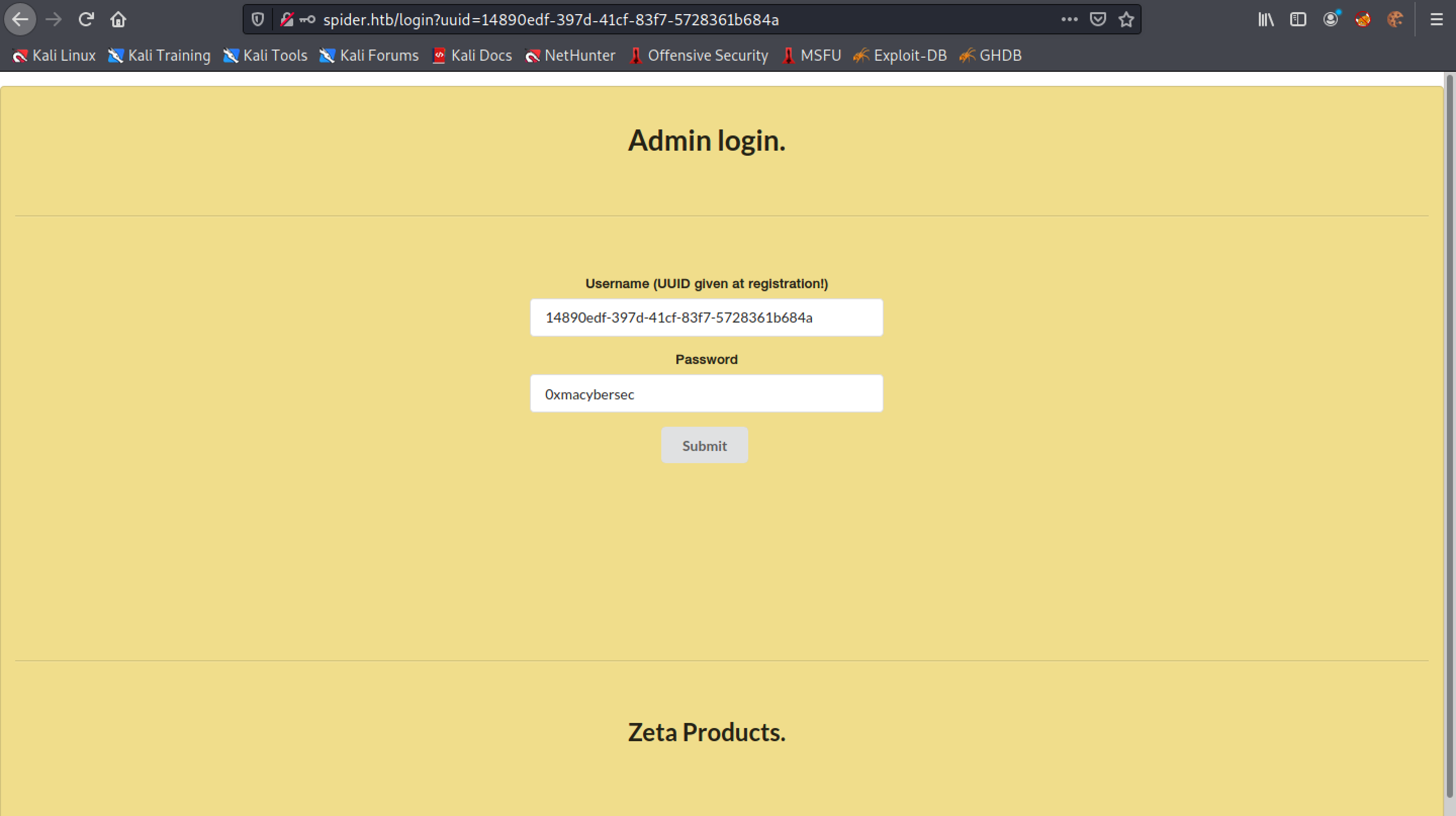
Login to the website using the UUID.
Click on "User Information".
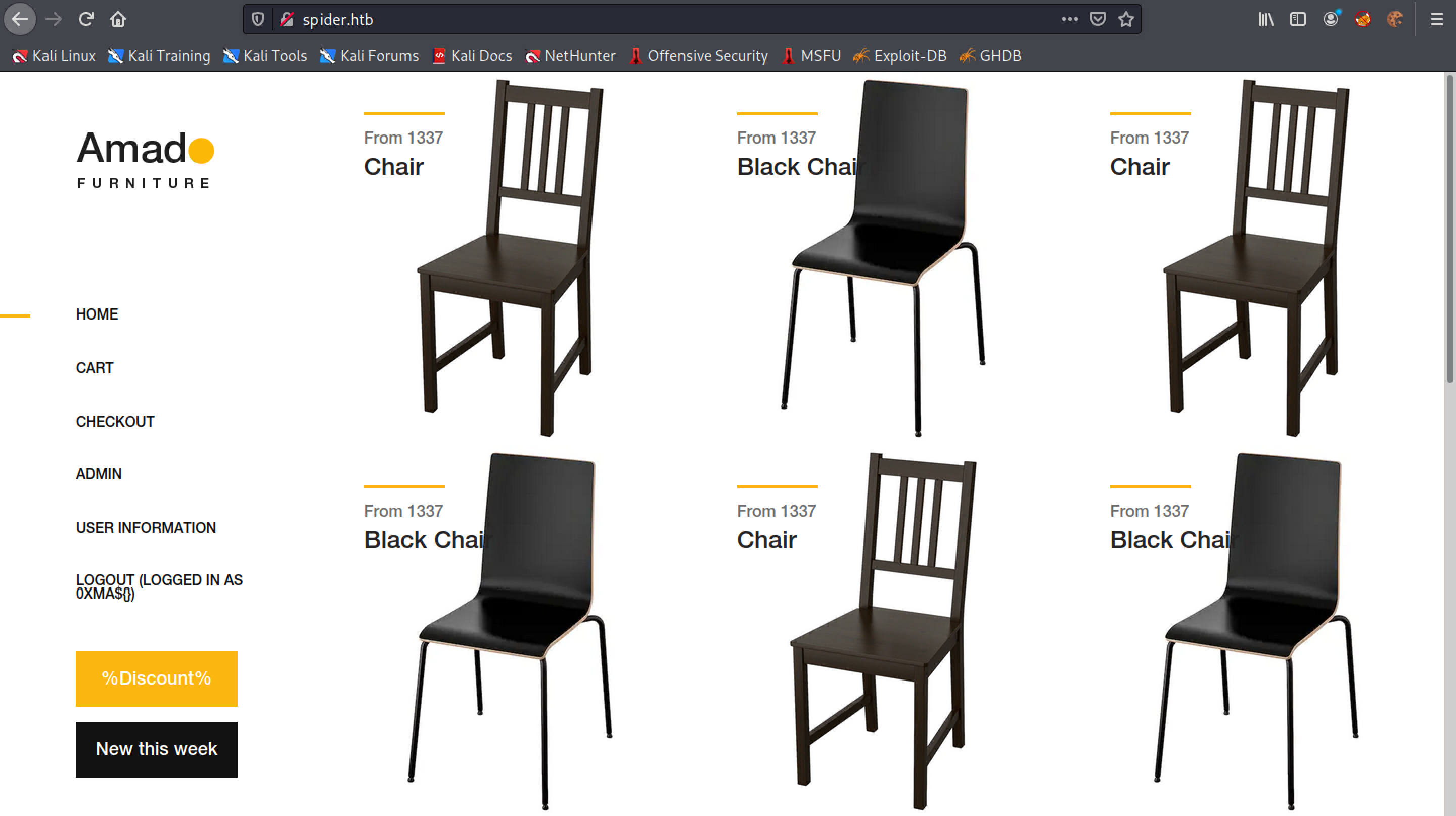
The username is displayed intact without any changes. And it doesn't crash the web application.
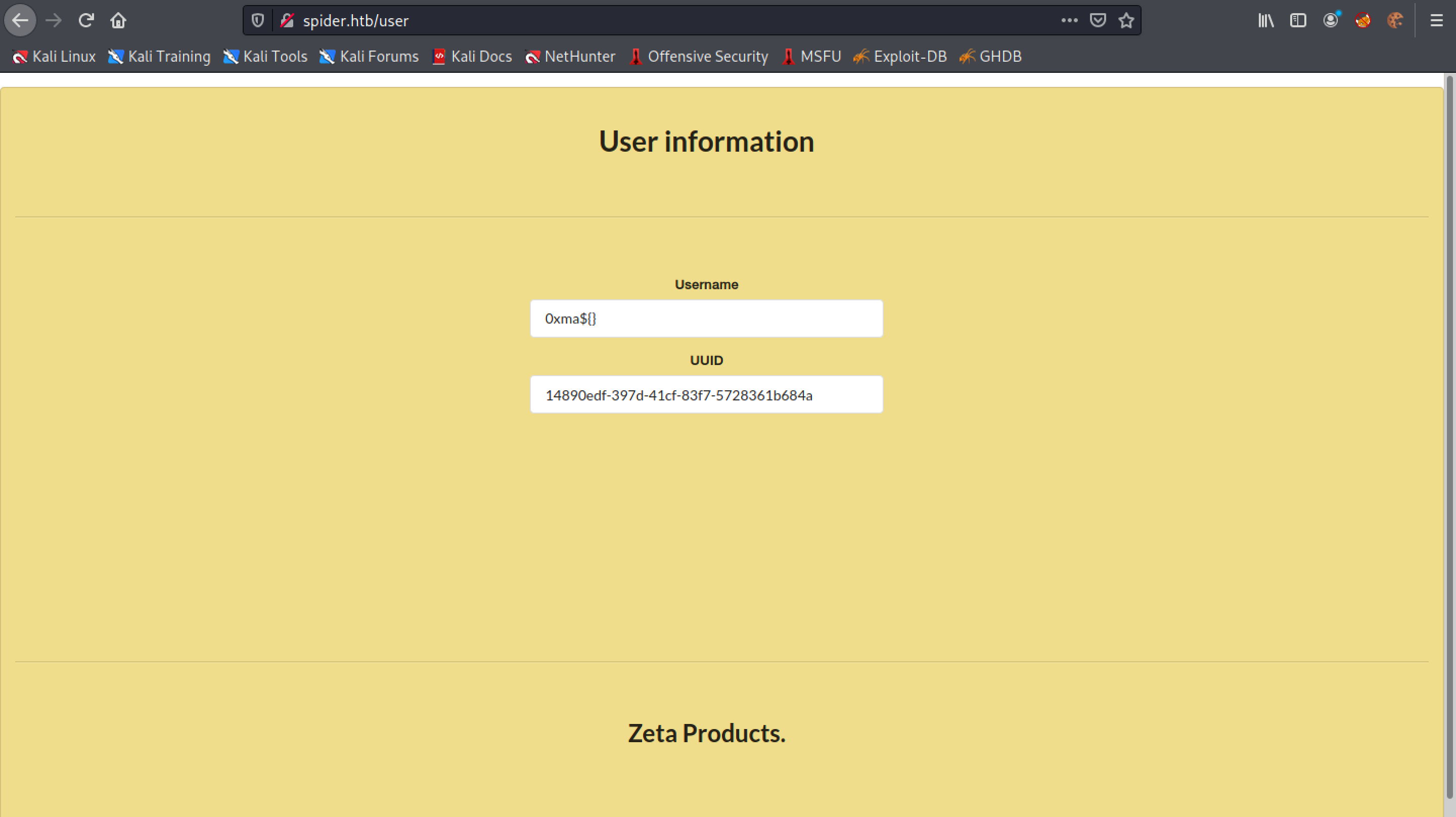
Register with a different payload in the username 0xma${7*7}. Login and click on "User Information".
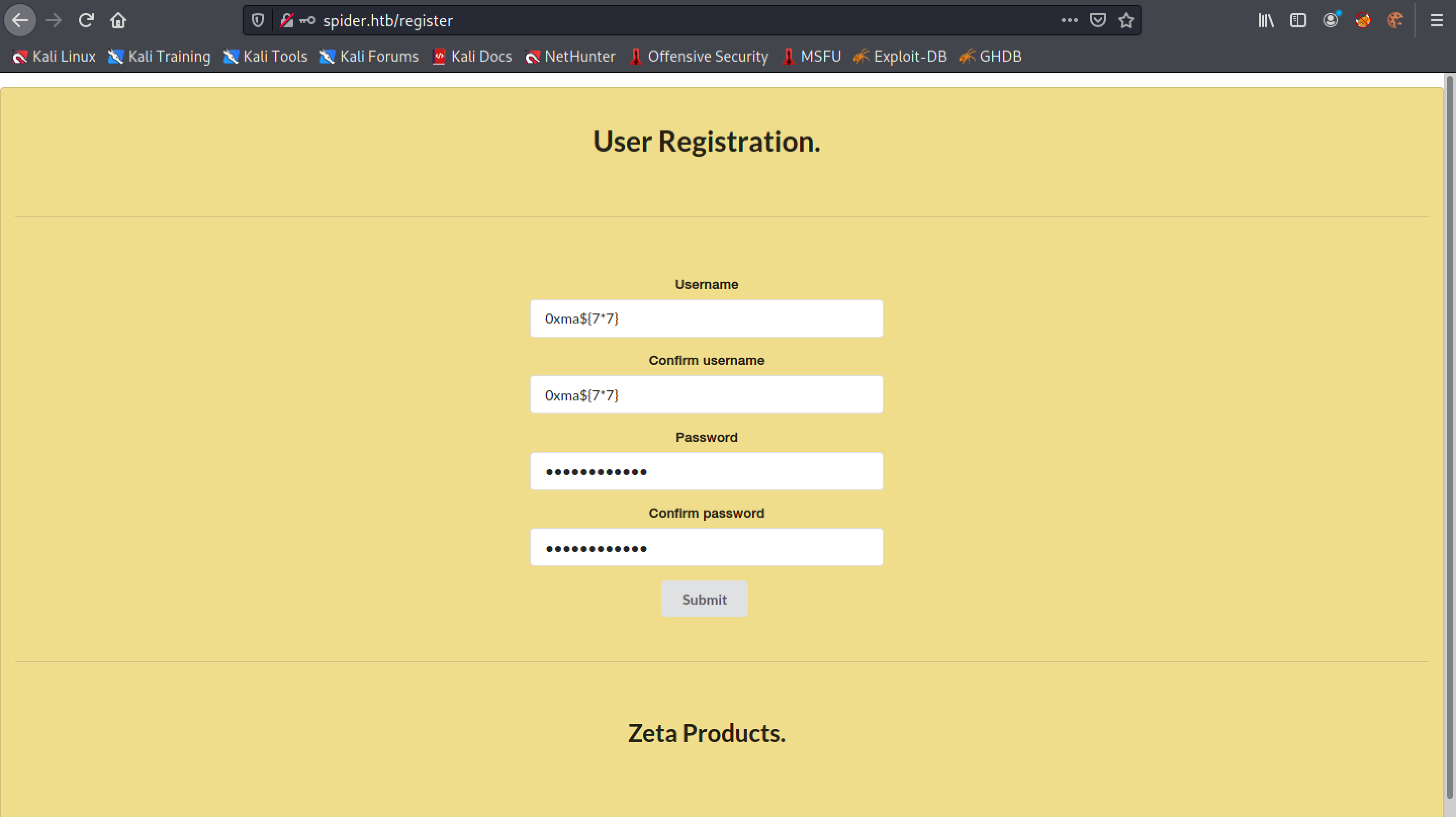
The username is displayed intact and there is no sign of SSTI yet.
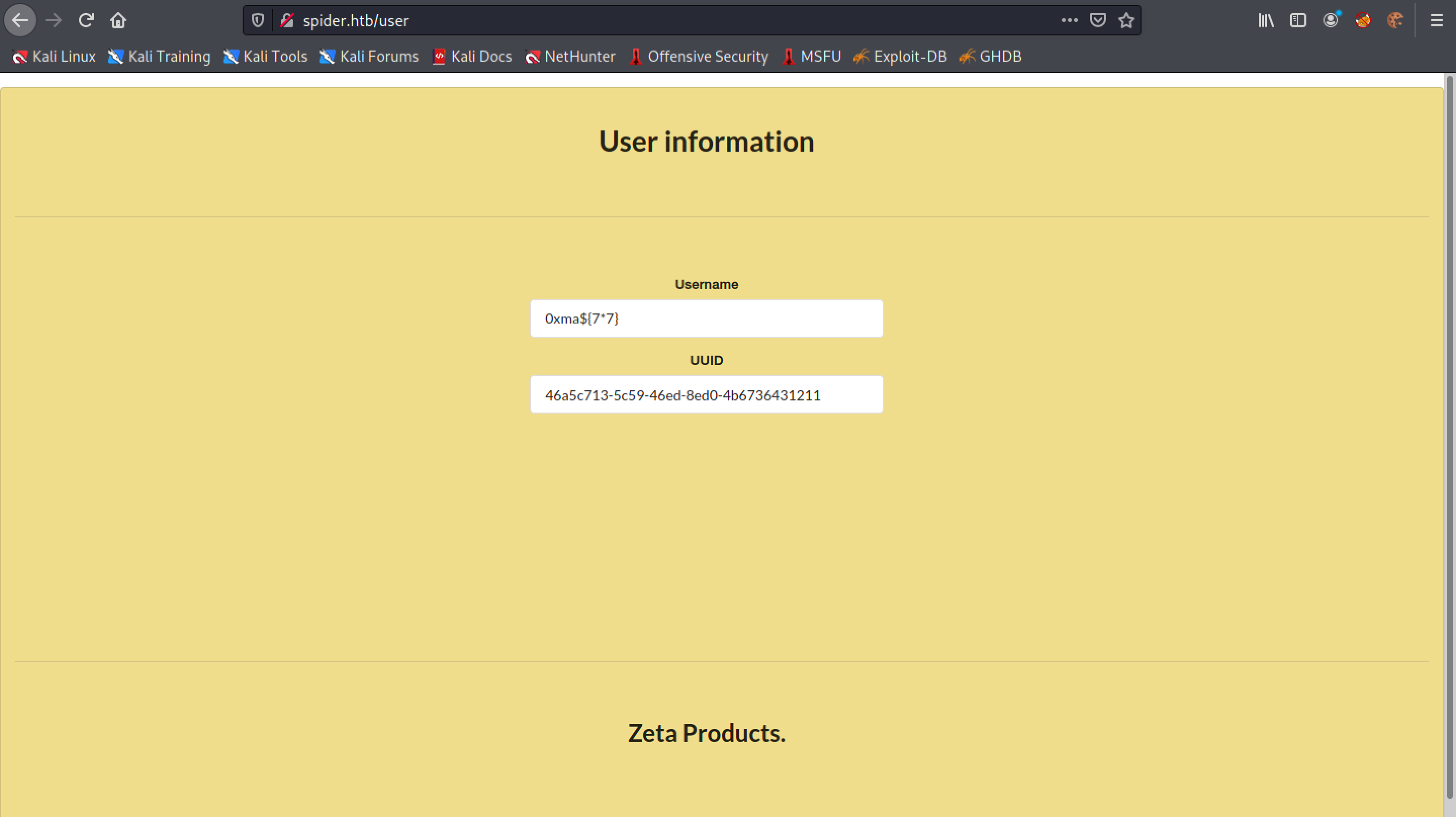
Let's add another set of curly braces to the username 0xma${{7*7}}.
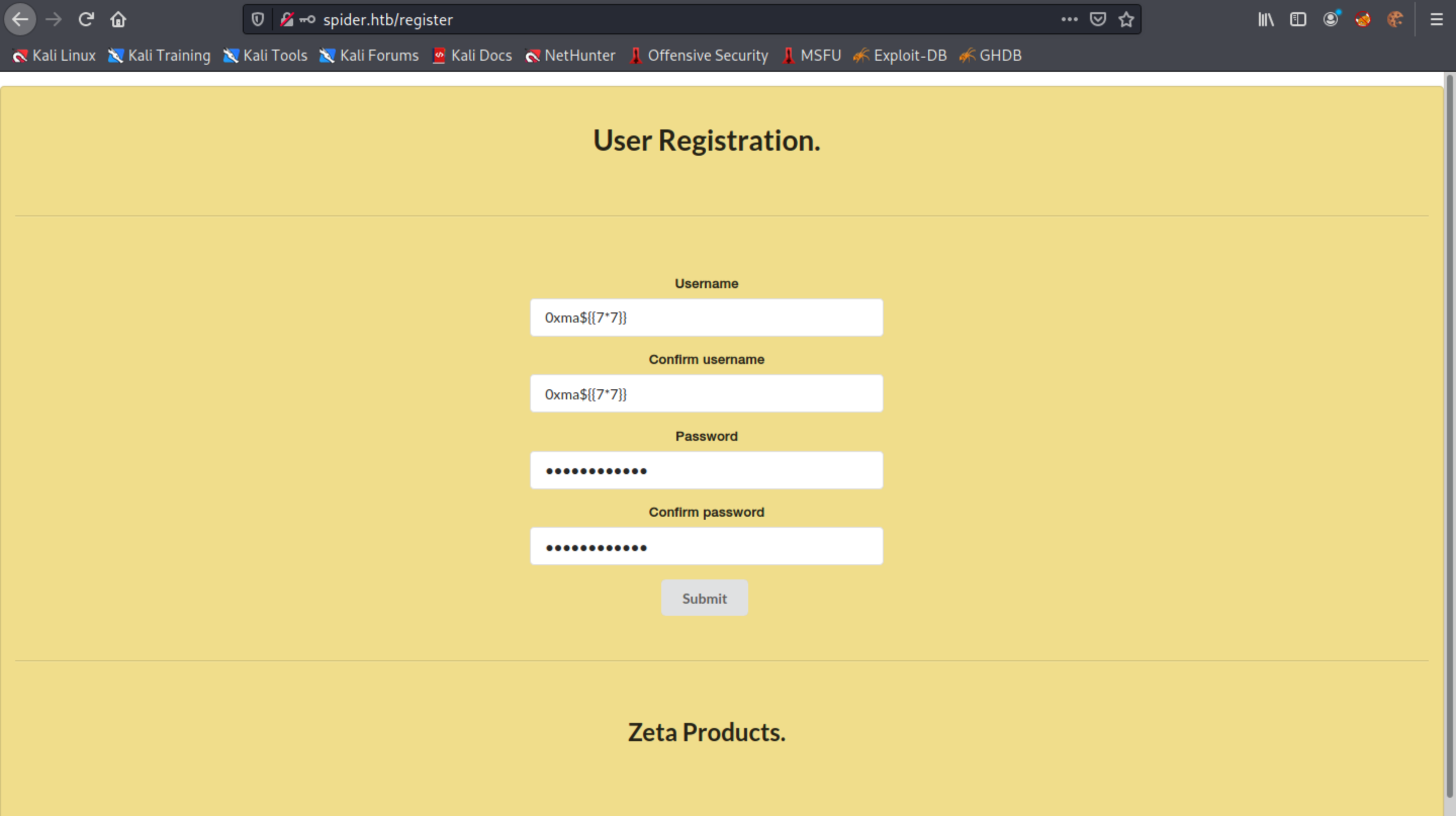
The web application responds with a message that the username cannot exceed 10 characters.
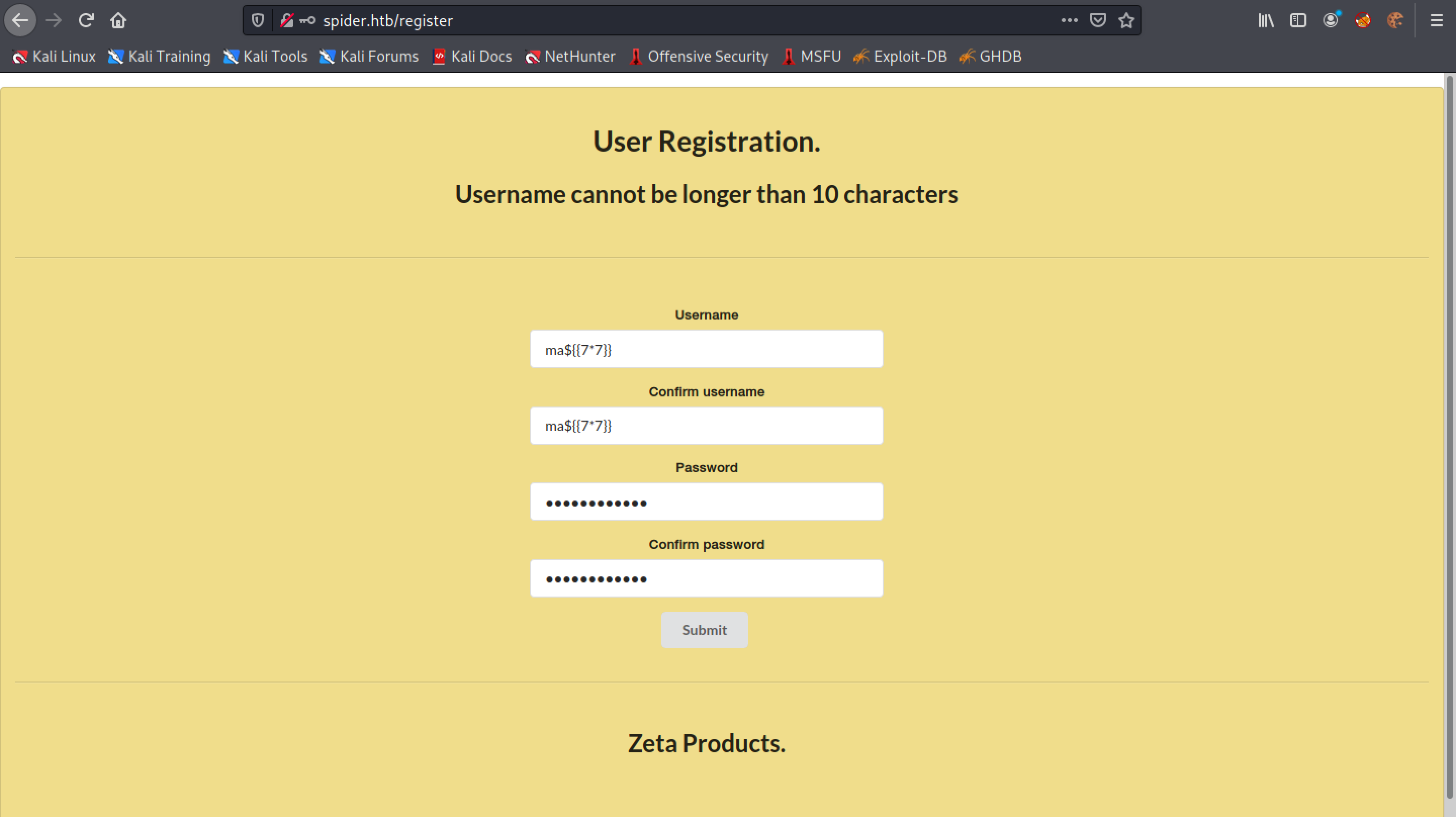
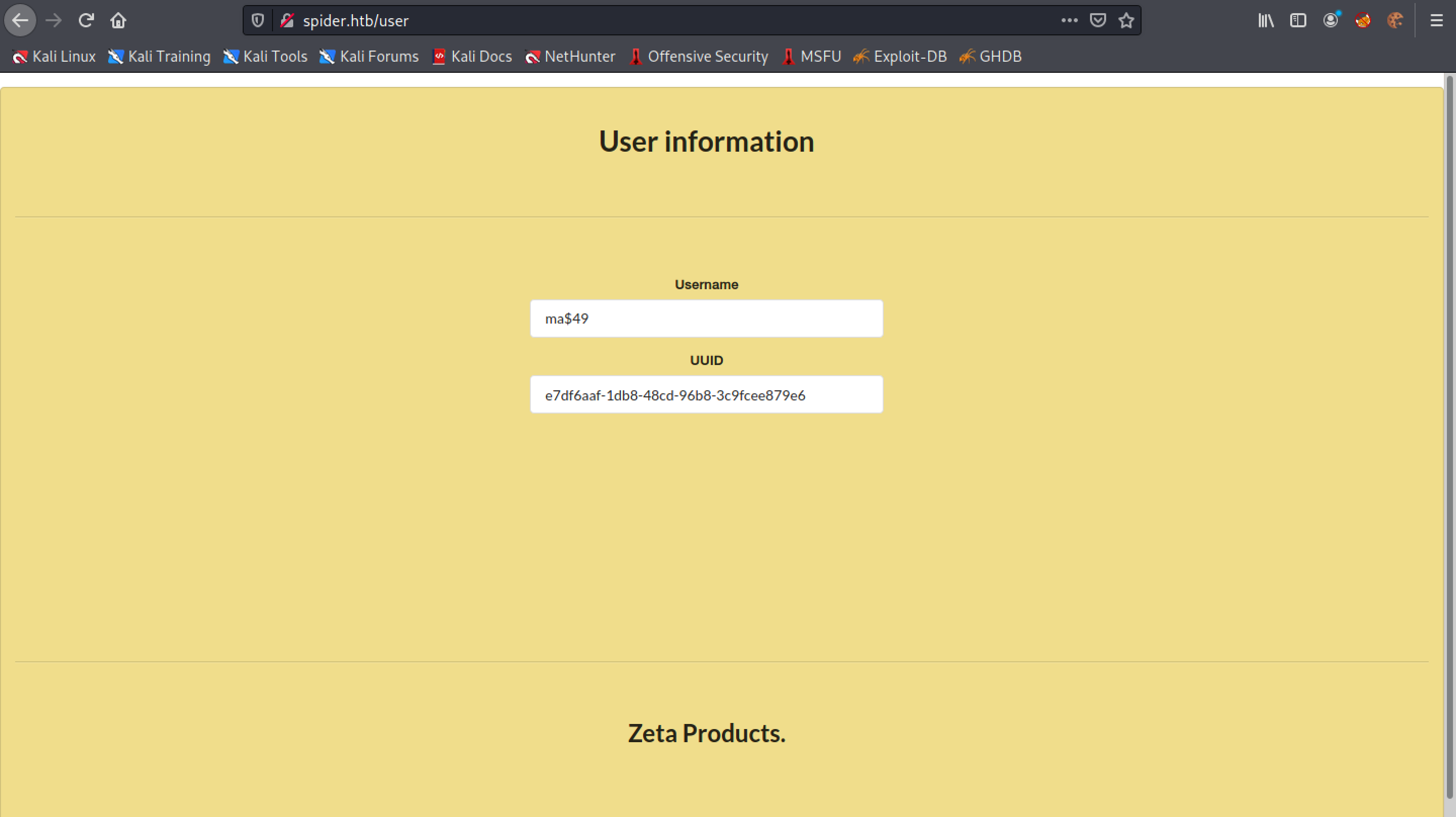
Let's reduce our username to 10 characters by registering ma${{7*7}}. Login to the website and click on "User Information".
Bingo. We get the result of the multiplication in the SSTI payload. This shows that SSTI attack is possible.
Let's try a Jinja payload to see if it works. This page contains more information about Jinja payloads.
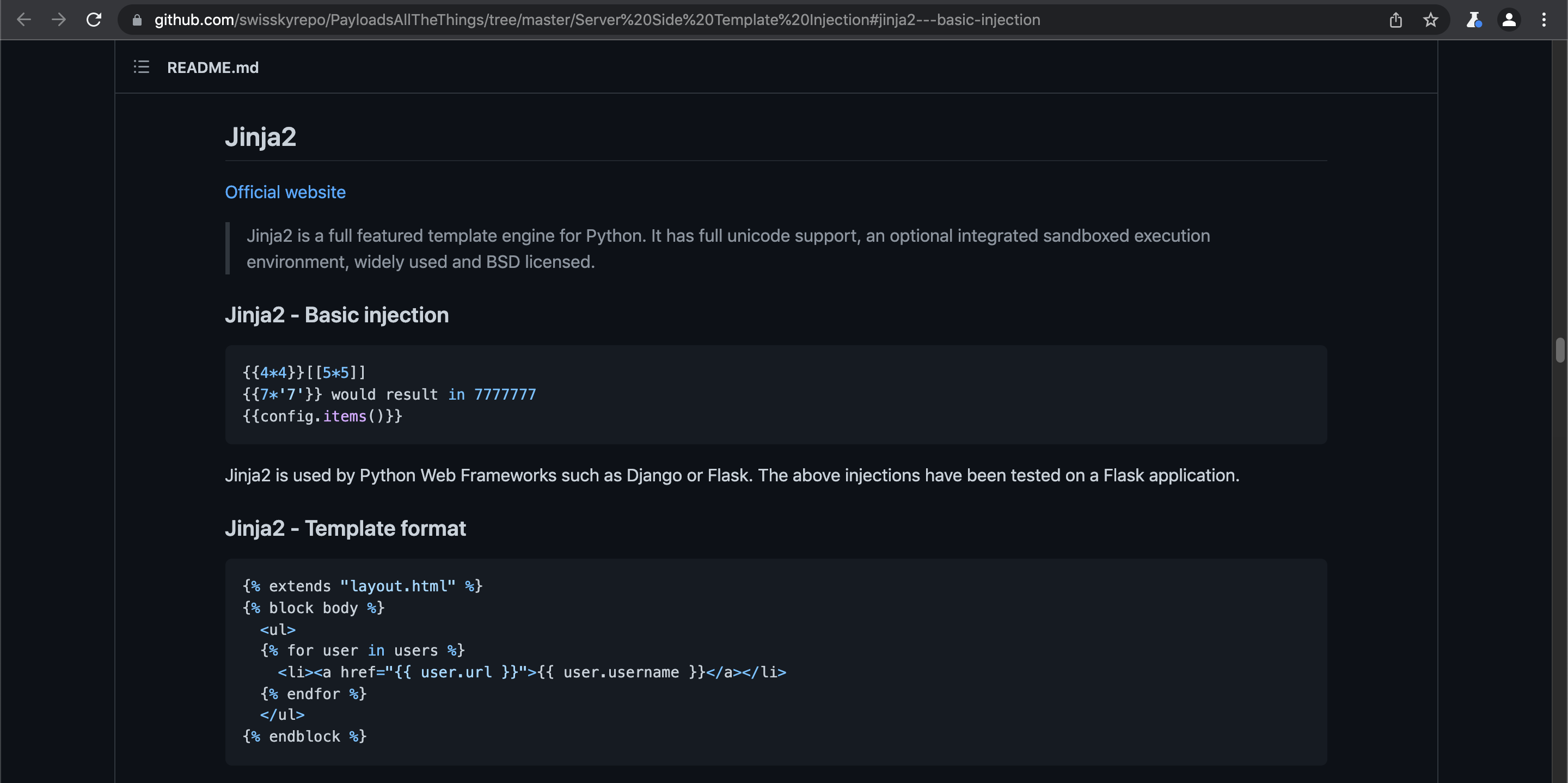
Since we are only restricted to 10 characters, we can only use config instead of config.items().
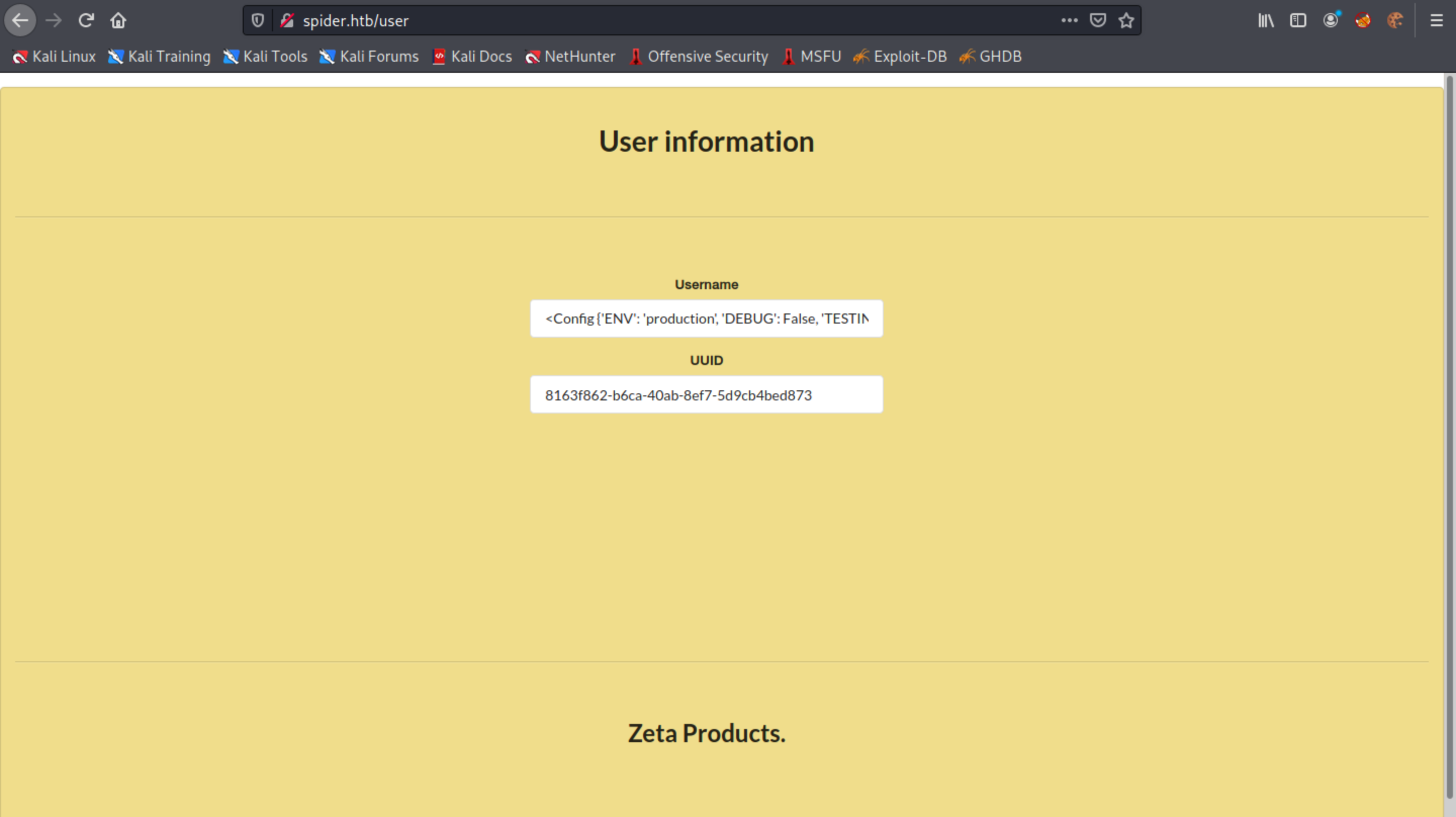
The "User Information" page now displays configuration information.
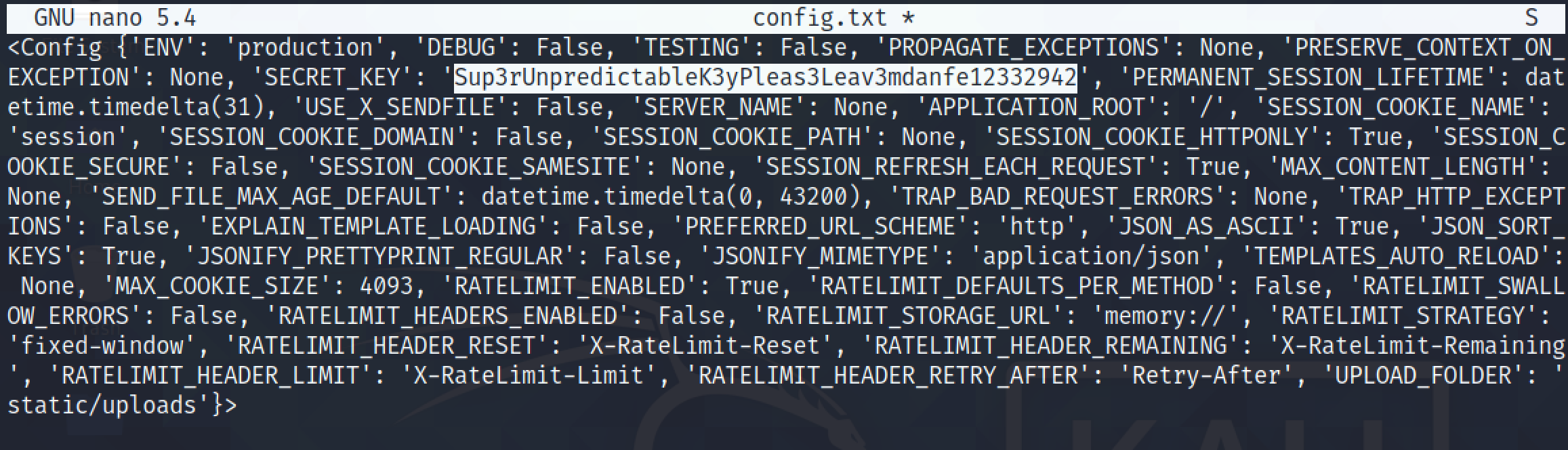
This shows the secret key that is used to encrypt the cookies. This tutorial shows how we can use this secret key to perform a SQL injection by injecting our payload in the cookie.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.